- Cisco Community
- Technology and Support
- Security
- Network Security
- Block access to Remote Access VPN by IP Address
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Block access to Remote Access VPN by IP Address
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2021 12:37 PM
I am running a couple of Cisco FTD 2110 managed with FMC and am looking for the best way to block access to our remote access VPN by IP. From doing some reading it looks like the best (and only?) way to do this is via a control plane ACL deployed via Flex Config. I saw another post that showed how this could be accomplished via geo but I am unsure on that syntax. I'm hoping someone could provide what syntax is used or point me towards some documentation for this?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2021 12:46 PM
No you cannot currently use Geolocation to block traffic "to" the FTD to filter VPN connections. Still an unresolved and open feature request...
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvs65322/?rfs=iqvred
Use flexconfig to apply a control plane ACL, or filter on the upstream router or place another FTD in front of the RAVPN FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2021 12:52 PM
Is there any documentation on what the control plane ACL would need to look like? Are we able to use a network object group along with it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2021 02:24 AM
here it will give you high level control plan ACL information : (HTH)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2021 09:38 PM
You should be able to use a normal extended ACL object (including network object group). Just add the parameter "control-plane" at the end of the access-group command which applies the ACL to the interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2021 03:13 AM
And how do I do this in FMC?
This is ridiculous, how do I block IP address from trying to establish a VPN connection? It is such a basic, fundamnetal request, for god sake.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2021 01:16 AM
For what it`s worth you could utilize an MFA solution (which you should have anyway) which allows GEO blocks (like DUO MFA).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 10:48 AM - edited 06-02-2021 10:52 AM
I just tested and confirmed this can be done in FMC.
Short steps:
1. Create an extended ACL object that denies the sources you want to block and allows all others.
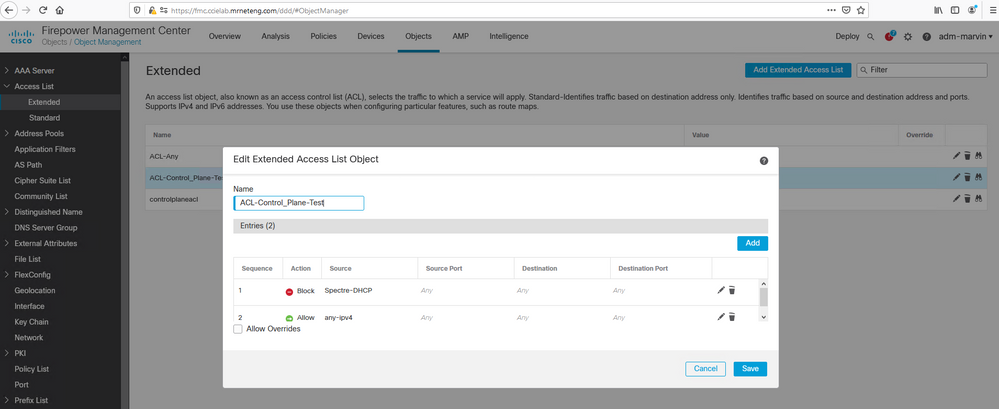
2.Create a Flexconfig object that defines a variable linked to the ACL you just created.
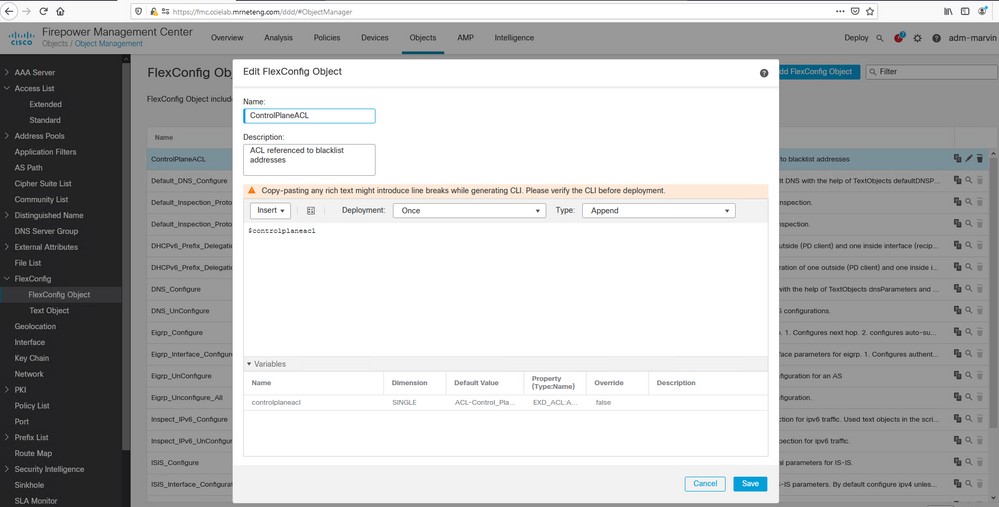
3. Create a second Flexconfig object that references the ACL variable and applies it to the desired interface including the "control-plane" keyword.
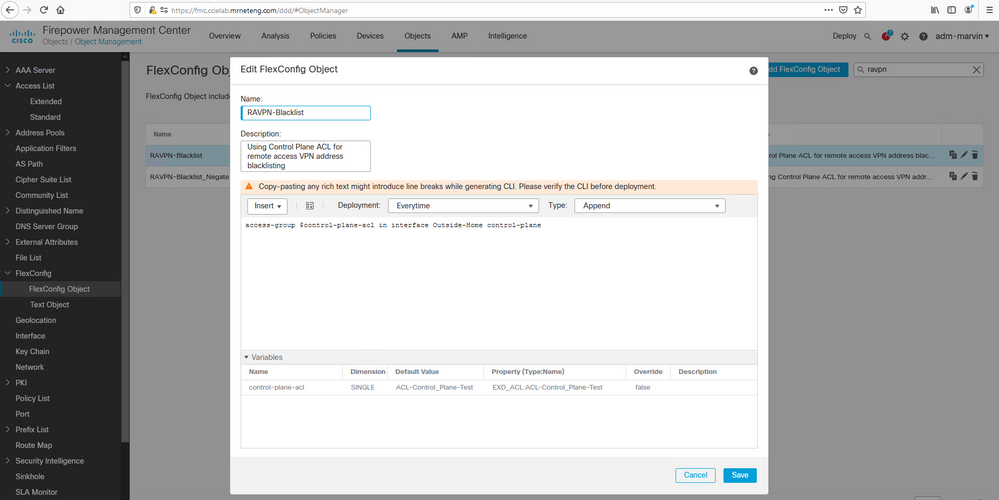
4. Create and deploy a Flexconfig policy to the target FTD device(s).
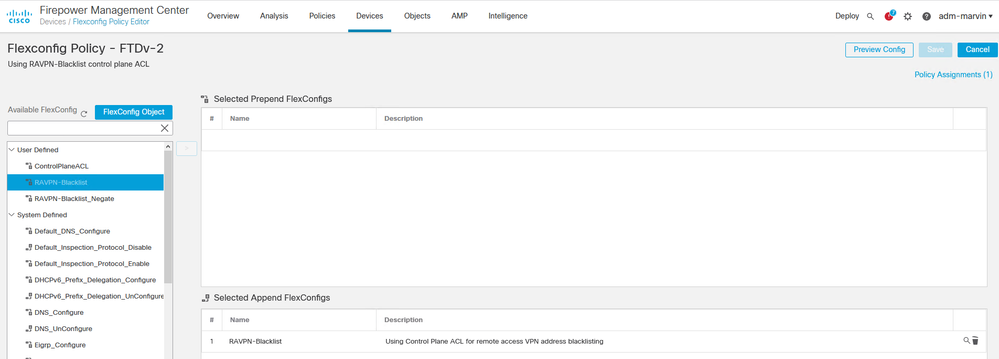
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 06:54 AM
Hi Marvin,
Can you clarify where the step 2 variable is being used?
Is it possible to just create one object, with one variable referencing the ACL?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 10:43 AM
The variable created in Step 2 is referenced by the object in Step 3.
I've not tried concatenating them - once I get something working using the Velocity language they use for that, I tend to leave it alone if I can.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 10:45 AM
Good to know. I'll give this a shot. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2023 07:38 PM - edited 10-31-2023 08:05 PM
Hi Marvin,
Sorry, this is a beginner-level question.
in step 3 you create a new FlexConfig object, what option do you choose to insert:
Or do I key it in?
For Step 2 I got it via Insert Policy Object --> Extended ACL Object
TIA for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2023 06:41 AM
@beIN SG Support it's a policy object in both cases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2022 08:01 PM
Will applying the extended ACL to the Outside interface not override the Access Control Policy defined within the FMC (under Policies>Access Control)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2022 12:18 AM
@jasond no, a control-plane ACL applied inbound on the outside interface will filter traffic "to" the FTD. The ACP controls traffic "through" the FTD.
The control-plane would permit or deny the VPN connection from being established, the ACP would control the communication if the VPN is established.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide