- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Block certain types of files on Firepower 1140 managed by FMC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 01:00 AM
Hello for everybody.
We need to block next file types:
- Block all portable executable files (exe, cpl, dll, ocx, sys, scr, drv, efi, fon, pif, etc.);
- Block additional file types that could be dangerous: .js files, rtf files, .scr files, .hlp files and .lnk files, .dll etc;
- .zip archive with password;
- Archive file containing the archive inside.
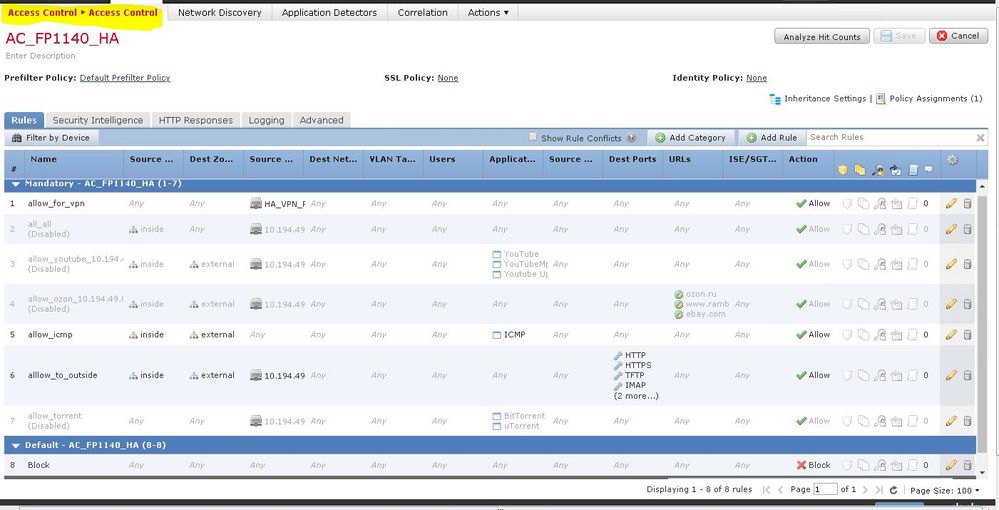
If i understand correctly, we can do this via malware policy or via access control (note that access-control is created for a test environment, so the rules may seem wrong - while everything is being checked).
But problem, that we couldn't find the specified file types in the specified policy. Maybe these files are blocked in another place/policy?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 05:39 AM - edited 06-15-2020 05:40 AM
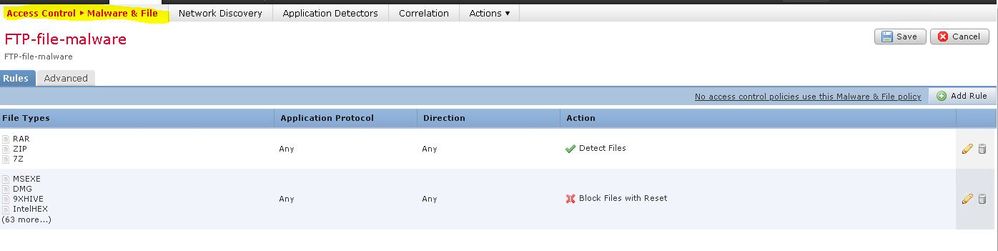
Not every file type can be specified in your File Policy - only supported ones. There are 96 supported file types as of Firepower 6.6 (current latest version). They do not currently include .js (JavaScript) or .dll (Dynamic Link Library) files. See below:
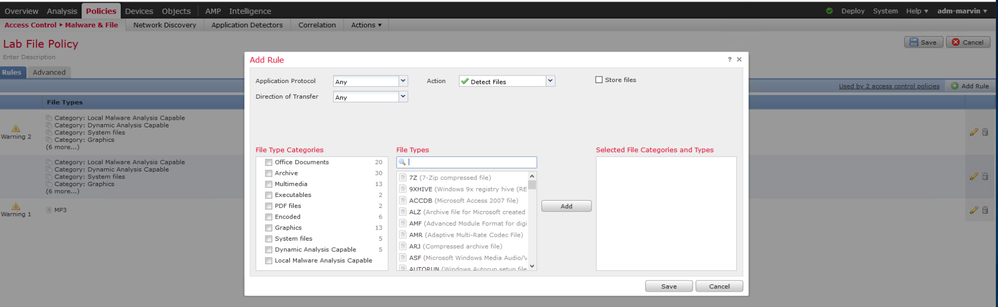
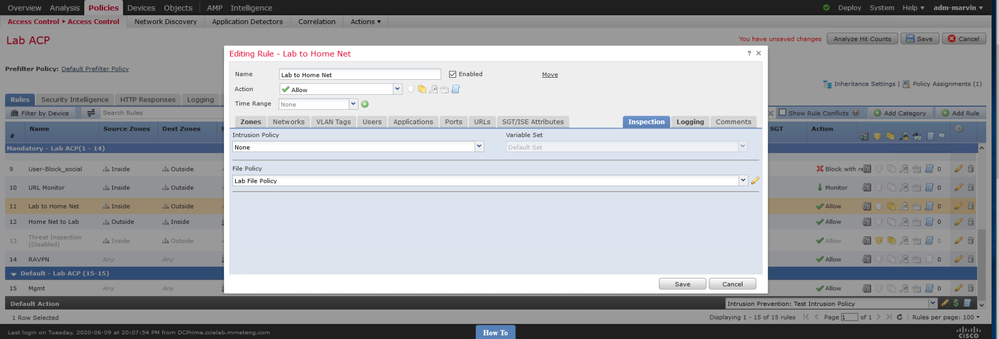
Once you have created a file policy, you need to associate it with the appropriate rule(s) in your access control policy via the inspection tab of the rule(s). When you have done so you can quickly see it by the presence of the icon on the right side of the ACP rule showing the files icon (looks like a sheaf of papers) highlighted as shown below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 03:52 AM
Hi,
I cannot tell from your screenshot, but are you referencing your File Policy under "inspection" tab of one of the relevant ACP rules?
This link demonstates how to configure the File Policy:- https://deconstructingsecurity.wordpress.com/firepower-example-config/
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 05:39 AM - edited 06-15-2020 05:40 AM
Not every file type can be specified in your File Policy - only supported ones. There are 96 supported file types as of Firepower 6.6 (current latest version). They do not currently include .js (JavaScript) or .dll (Dynamic Link Library) files. See below:

Once you have created a file policy, you need to associate it with the appropriate rule(s) in your access control policy via the inspection tab of the rule(s). When you have done so you can quickly see it by the presence of the icon on the right side of the ACP rule showing the files icon (looks like a sheaf of papers) highlighted as shown below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 07:44 AM
Thank everybody for answers.
Yes, i know, that to apply the malware policy, you must create it and apply it on access control policy. But in our current version 6.4.0.7 i couldn't find all the file types listed - for example, .rtf is present, but .dll and .hlp are not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 07:43 PM
The supported file types vary by release (and by product - i.e. AMP on Firepower supports different file types than AMP on ESA than AMP for Endpoints etc.).
Unfortunately Cisco doesn't document these very well - neither in the respective configuration guide or release notes. The only way to confirm what's supported on your release is to look the file file policy dialog as I shared earlier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 11:10 PM
Is it possible that the access policy settings differ from the software version and the firepower model?
Because also we need to block all traffic (deny all, permit none) by default rule and set "Monitor" status for this rule. But i can see, that its not possible - i can select either block or monitor action.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 11:23 PM - edited 06-15-2020 11:25 PM
Yes setting options available to you vary by the version of software, configuration and type of device. For instance, you cannot block if the device isn't inline. Time-based ACP rules and FQDNs in rules are only on later versions, etc.
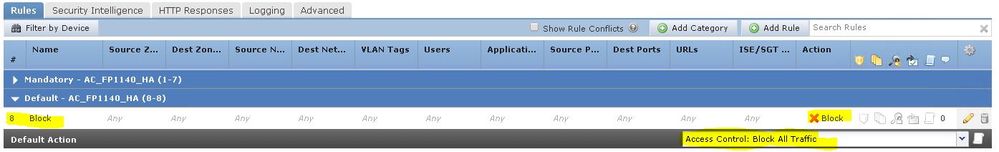
"Block" is roughly equivalent to "deny" on an ASA. They use that because there is also a "Block with Reset" action available which will not only block the traffic but also send a TCP RST packet to the initiator.
So your default section Rule #8 does that. You aren't logging that rule so it will silently drop the traffic.
Your Default Action for the policy will never be hit due to what you have in Rule #8 above it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 01:03 AM
But in this particular case only the traffic specified in the allowed rules in mandatory will be allowed. If there is no traffic in the allowed rules with this default rule (block any any), it will be discarded.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 05:52 AM
I think we are saying the same thing - your rule #8 (Mandatory Section) will operate independently of any earlier rules. Thus it will Block everything not previously acted upon in rules 1-7.
Since it does that, the Default Action ("Access Control: Block All Traffic") will never see any traffic.
I'm was also pointing out that you won't get any events as a result of rule #8 since the logging icon is greyed out. The logging that's enabled for the Default Action would not see any events.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide