- Cisco Community
- Technology and Support
- Security
- Network Security
- Welcome, all the time.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2016 08:43 AM - edited 03-12-2019 12:56 AM
I want to perform PBR in an ASA 5510 but this model can handle this?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2016 06:01 PM
Hi,
No, the ASA does not support PBR.
But Check this by Kureli Sankar
PBR on the router outside the firewall
With this method we can configure both the ISP links on the router outside the firewall. We can translate some traffic to use Primary ISP provided IP address and the rest of the traffic to use Secondary ISP provided IP address. Now, based on this source address that hits the router, we can configure the router to do policy based routing and route the traffic either via the Primary ISP or via the Secondary ISP.
Thanks to vote and Rank This Please.
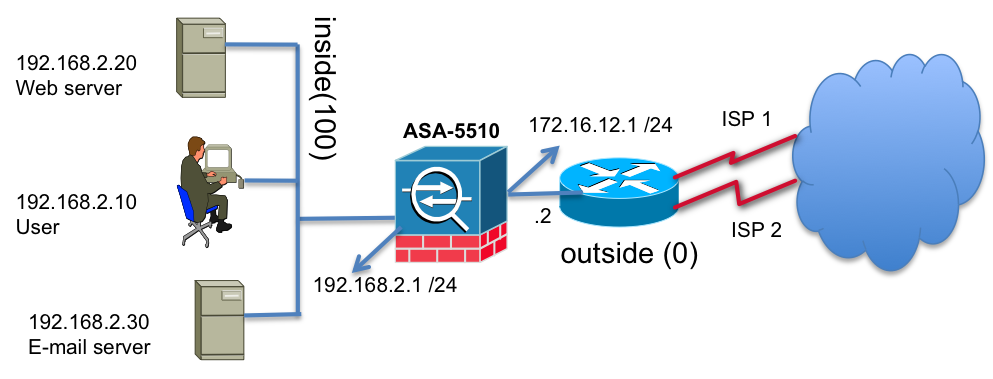
Let us assume the requirement as below:
1. We would like all the users traffic translated to the ISP1 provided address
2. We would like all the servers traffic translated to the ISP2 provided address
3. The router should look at the translated addresses and based on the address it should set the next hop address and route the traffic via the appropriate ISP.
ISP1 provided address block is 10.10.10.0/24 and ISP2 provided address block is 172.18.124.0/24. These are not routable addresses. For simplicity reasons we are using RFC 1918 address space.
ASA config:
Translation for all users to take ISP 1
nat (inside) 1 192.168.2.0 255.255.255.0
global (outside) 1 10.10.10.1
Translation for web and e-mail servers to take ISP2
static (inside,outside) 172.18.124.20 192.168.2.20 netmask 255.255.255.255
static (inside,outside) 172.18.124.30 192.168.2.30 netmask 255.255.255.255
route outside 0 0 172.16.12.2
Router config:
ip access-list ext isp1-addr
permit ip 10.10.10.0 0.0.0.255 any
ip access-list ext ips2-addr
permit ip 172.18.124.0 0.0.0.255 any
route-map ISP permit 10
match ip address isp1-addr
set ip next-hop 10.10.10.2
route-map ISP permit 20
match ip address isp2-addr
set ip next-hop 172.18.124.2
int f0/0
ip address 172.16.12.2 255.255.255.0
ip policy route-map ISP in
Allowing outbound via ISP1 and inbound via ISP2
Let us take the same example above. We can use one ISP1 for all outbound connections and use IPS2 for all inbound connections.
Translation for all outbound connections from users and servers to take ISP 1
nat (inside) 1 192.168.2.0 255.255.255.0
global (ISP1) 1 10.10.10.1
route ISP1 0 0 10.10.10.254
Here are the translations for inbound connections to the servers:
Translation for web and e-mail servers to take ISP2
static (inside,ISP2) 172.18.124.20 192.168.2.20 netmask 255.255.255.255
static (inside,ISP2) 172.18.124.30 192.168.2.30 netmask 255.255.255.255
In the previous case even the out bound connections made by the servers would take the ISP2 path but, in this example outbound connections from the web and e-mail servers will take ISP1. ONLY the INBOUND connections will come through ISP2 and will be responded back using ISP2.
Allowing internet access via ISP1 and L2L vpn via ISP2
The above example can also be used to allow internet access outbound and inbound via ISP1 with the default route pointing to ISP1 and VPN site to site tunnels can be terminated on the ISP2 interface by configuring specific routes to reach peer networks via IPS2.
Multiple context mode
The last option is to use multiple context mode where we can load balance on a per context basis. VPN is not supported in this mode and so are dynamic routing protocols. Please refer this link for the limitations:http://www.cisco.com/en/US/docs/security/asa/asa82/configuration/guide/contexts.html#wp1146747
Context-1 could use ISP1 link and Context-2 could use ISP2 link.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2016 06:01 PM
Hi,
No, the ASA does not support PBR.
But Check this by Kureli Sankar
PBR on the router outside the firewall
With this method we can configure both the ISP links on the router outside the firewall. We can translate some traffic to use Primary ISP provided IP address and the rest of the traffic to use Secondary ISP provided IP address. Now, based on this source address that hits the router, we can configure the router to do policy based routing and route the traffic either via the Primary ISP or via the Secondary ISP.
Thanks to vote and Rank This Please.

Let us assume the requirement as below:
1. We would like all the users traffic translated to the ISP1 provided address
2. We would like all the servers traffic translated to the ISP2 provided address
3. The router should look at the translated addresses and based on the address it should set the next hop address and route the traffic via the appropriate ISP.
ISP1 provided address block is 10.10.10.0/24 and ISP2 provided address block is 172.18.124.0/24. These are not routable addresses. For simplicity reasons we are using RFC 1918 address space.
ASA config:
Translation for all users to take ISP 1
nat (inside) 1 192.168.2.0 255.255.255.0
global (outside) 1 10.10.10.1
Translation for web and e-mail servers to take ISP2
static (inside,outside) 172.18.124.20 192.168.2.20 netmask 255.255.255.255
static (inside,outside) 172.18.124.30 192.168.2.30 netmask 255.255.255.255
route outside 0 0 172.16.12.2
Router config:
ip access-list ext isp1-addr
permit ip 10.10.10.0 0.0.0.255 any
ip access-list ext ips2-addr
permit ip 172.18.124.0 0.0.0.255 any
route-map ISP permit 10
match ip address isp1-addr
set ip next-hop 10.10.10.2
route-map ISP permit 20
match ip address isp2-addr
set ip next-hop 172.18.124.2
int f0/0
ip address 172.16.12.2 255.255.255.0
ip policy route-map ISP in
Allowing outbound via ISP1 and inbound via ISP2
Let us take the same example above. We can use one ISP1 for all outbound connections and use IPS2 for all inbound connections.
Translation for all outbound connections from users and servers to take ISP 1
nat (inside) 1 192.168.2.0 255.255.255.0
global (ISP1) 1 10.10.10.1
route ISP1 0 0 10.10.10.254
Here are the translations for inbound connections to the servers:
Translation for web and e-mail servers to take ISP2
static (inside,ISP2) 172.18.124.20 192.168.2.20 netmask 255.255.255.255
static (inside,ISP2) 172.18.124.30 192.168.2.30 netmask 255.255.255.255
In the previous case even the out bound connections made by the servers would take the ISP2 path but, in this example outbound connections from the web and e-mail servers will take ISP1. ONLY the INBOUND connections will come through ISP2 and will be responded back using ISP2.
Allowing internet access via ISP1 and L2L vpn via ISP2
The above example can also be used to allow internet access outbound and inbound via ISP1 with the default route pointing to ISP1 and VPN site to site tunnels can be terminated on the ISP2 interface by configuring specific routes to reach peer networks via IPS2.
Multiple context mode
The last option is to use multiple context mode where we can load balance on a per context basis. VPN is not supported in this mode and so are dynamic routing protocols. Please refer this link for the limitations:http://www.cisco.com/en/US/docs/security/asa/asa82/configuration/guide/contexts.html#wp1146747
Context-1 could use ISP1 link and Context-2 could use ISP2 link.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2016 10:11 AM
Thanks pretty much,
I did a lab with the solutions and works perfectly then I will apply it to production environment, thanks for the support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2016 03:08 PM
Welcome, all the time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2016 06:11 PM
Hi
You will not be able to do PBR on ASA5510. PBR is supported on 9.4 and up. ASA5510 cannot run 9.4 code.
http://www.cisco.com/c/en/us/td/docs/security/asa/asa94/release/notes/asarn94.html#ID-2172-00000128
http://www.cisco.com/c/en/us/td/docs/security/asa/compatibility/asamatrx.html#48552
Thanks
John
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
