- Cisco Community
- Technology and Support
- Security
- Network Security
- Can not access to DMZ Host from Inside Host
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can not access to DMZ Host from Inside Host
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2023 09:26 PM
Hi friends,
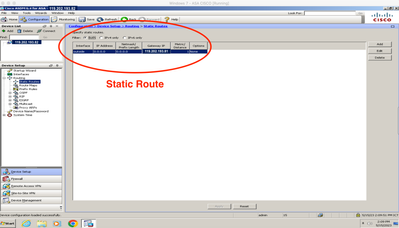
I have a Firewall 5520 with 3 interfaces: Inside (Host: 172.16.10.0/24 and GW: 172.16.10.2) Outside (119.202.193.81) and DMZ (182.16.10.1)
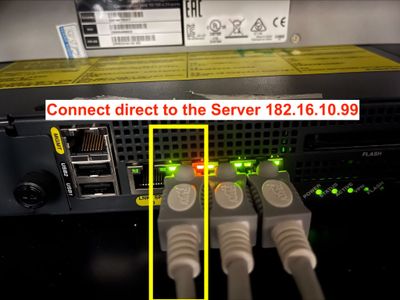
I did connect LAN cable on the Server (182.16.10.99) direct to GigabitEthernet0/2 on Firewall ASA 5520.
I have 2 questions:
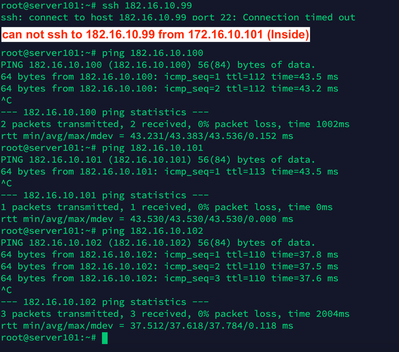
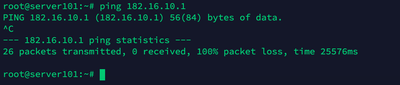
Can I connect direct with LAN cable 5e from a Server to the Firewall and the Led alert (Red) is correct? I can Ping to 182.16.10.99 from any hosts placed in the Inside interface. But the strange is Ping is successful to any IP starting with 182.16.10.x (but can not Ping to 182.16.10.1 is the IP of DMZ interface, and I only have one Server (182.16.10.99) connected direct to DMZ Port but the Ping replied successfully with any IP starting with 182.16.10.x (except 182.16.10.1)
I want any Host Inside access to Server 182.16.10.99 and versa (both way)
Any ideas, please help, tks a lot !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2023 01:47 AM - edited 05-25-2023 01:55 AM
Try this and test it this will solve this ping issue.
policy-map global_policy
class inspection_default
inspect icmp
exit
For SSH
ASA(config)# enable password system@123
Step 2: Create a username with password.
ASA(config)# username testme password cisco@123
Step 3: Configure this local username to authenticate with SSH.
ASA(config)# aaa authentication ssh console LOCAL
Step 4: Create RSA key pair.
ASA(config)# crypto key generate rsa modulus 1024
INFO: The name for the keys will be:
Keypair generation process begin. Please wait...
Step 5: Now specify only particular hosts or network to connect to the device using SSH.
ASA(config)# ssh 18.x.x.x.x 255.255.255.0 DMZ
ASA(config)# ssh 172.16.10.0 255.255.255.0 Inside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2023 09:17 PM - edited 05-25-2023 09:37 PM
Hi @Sheraz.Salim
Thank for your very quick support. The pictures that I show in this post give you more details info. I want both Inside host and DMZ host can communicate to each other in both ways, versa (like Ping or SSH).
First, I don't know why the Server99 in the DMZ (there's only one Server99 with IP: 182.16.10.99 connected directly to the DMZ port) But Server99 can not Ping to the DMZ Interface IP: 182.16.10.1,. I want to know why (related to the cable or any physical connector reason) or any Cisco Firewall policy that denied this. As I know, any host can Ping successfully to the IP of the Interface which is connected by default (such as Inside or DMZ cause they're in the same LAN Subnet)
Second, the goal is I want all hosts placed in Inside or DMZ can communicate to each other, in both ways (versa) with any services (Ping, SSH, Web,...). So the SSH commands you gave me above seem like just apply for the hosts can SSH to the Cisco ASA device (not the hosts in DMZ Interface), isn't it?
Thank @Sheraz.Salim again and waiting for your answer/reply in the soonest.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 01:23 AM - edited 05-26-2023 01:25 AM
In order to reach ping/etc from inside to dmz and from dmz to inside you need to make some changes on your firewall.
interface GigabitEthernet0/1
description inside network
nameif inside
security-level 50
!
interface GigabitEthernet0/2
description DMZ
nameif DMZ
security-level 50
!
same-security-traffic permit intra-interface (I noted you already have this command)
if you put inside and dmz in same security-level 50 they would be able to communicate to each-other.
For the DMZ server to Firewall Interface could you please show us the output of this command. "show interface GigabitEthernet0/1". curious have to change the cable? If you want the server to be at 100Mbps in that case change the speed settting on the firewall interface DMZ (or match them 100Mpbs at server and same on Firewall)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 04:18 AM
Hi @Sheraz.Salim the DMZ security level is already set is 40. You can take a look at the files name Cisco show run ...
One more thing, I don't know why the status of the DMZ Interface is Down, I did check DMZ Interface status is Enable in the ASDM -> Interface --> GigabitEthernet0/2 (DMZ): Enable
I also tried the command no shutdown to bring it UP but it seem no luck
no shutdown
write memory
show interface GigabitEthernet 0/2
Interface GigabitEthernet0/2 "DMZ", is down, line protocol is down
Any ideas? Thank @Sheraz.Salim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 04:36 AM
Yes DMZ is security level is 40 and Inside security level is 50. In order to communicate dmz to inside and Inside to dmz you need to set the same security values on both interface security level to 50.
interface GigabitEthernet0/1
description inside network
nameif inside
security-level 50
!
interface GigabitEthernet0/2
description DMZ
nameif DMZ
security-level 50
!
same-security-traffic permit intra-interface (I noted you already have this command)
Interface GigabitEthernet0/2 is showing down down mean either your server and Firewall have cable issue or the server nick card is not function properly. try to plug your laptop or computer to this dmz interface and configure the subnet on laptop/computer same as in firewall subnet. once done try to ping the default gw of the dmz interface.
Its seem more likely issue could be at your server end. however on the output of the DMZ interface there is nothing no noise of any packets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 05:02 AM
the DMZ interface show down, and the auto-duplex is not show half or full
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2023 02:46 AM
there is something in cable the color is Yellow blinking ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2023 02:49 AM
@MHM Cisco World I think is running half duplex instead of full duplex either cable issue or change the cable required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2023 02:53 AM
Yes that same in my mind.
I high suspect in duplex and speed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2023 09:24 PM
Hi @MHM Cisco World, thank for your support. Is it effect to the network or anything? Cause I only need them work with 100Mbps that's enough for me. What if it's Red blinking not Yellow blinking?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 01:25 AM - edited 05-26-2023 01:26 AM
hardcoded the speed in both side of link
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 01:27 AM
@MHM Cisco World Here is the link in case OP need it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 01:28 AM
Thanks, I hope @thedao take look.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2023 04:08 AM
Thanks @MHM Cisco World I will try to see how (maybe set 100Bmps for both of them Inside and DMZ Interface)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide