- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Changing ISE Certificate for EAP Auth Role
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Changing ISE Certificate for EAP Auth Role
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2022 11:20 AM
Hello All,
ISE v2.7
Currently, we are using a Certificate on ISE that is signed by our internal Windows CA server. This cert is used for "Admin, EAP Authentication, RADIUS DTLS, Portal".
We also use a certificate from Digicert for our Guest Portal.
The issue I'm running into is for our BYOD network. Since Android 10, these devices can no longer connect to a WPA2-Enterprise Wi-Fi network where the cert is not publicly signed, or by installing certs directly onto the Android devices (*which we prefer not to do).
I'm wondering what fallout could occur by beginning to use the Digicert, instead of the internally signed cert from our Windows CA server for the Roles described above?
When we had originally setup ISE, I believe we were going to use the CA Certificates for authentication. All of our company owned laptops/desktops have certs on them from the CA server. But, I don't believe we are using those Certs for auth any longer. Is there a way to tell in ISE if those Certs are being checked during authentication?
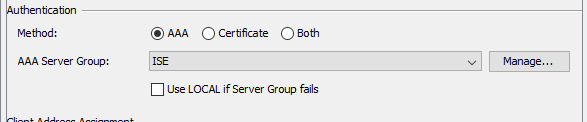
I know on our ASA, under the AnyConnect Connection Profile, for the Authentication Method we just have that configured for "AAA" and it points to our ISE server.
In ISE, would this be found in Policy Sets > Wired/Wireless > under the Conditions column? When looking at the Policy Sets, for Wired and Wireless. Our "Compliant" Policy Set just checks if the PC is in our AD, the location of the endpoint, and its Posture status.
Any help would be appreciated!
Thanks in Advance,
Matt
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2022 11:30 AM - edited 07-20-2022 11:36 AM
@Matthew Martin it's probably the EAP certifcate causing a problem with the Anrdoid devices, it's common to use a public CA to sign the EAP certificate nowadays.
Refer to this Cisco ISE certificates guide for more information https://community.cisco.com/t5/security-knowledge-base/how-to-implement-digital-certificates-in-ise/ta-p/3630897
For the Wired/Wireless authentication, what protocol are you using EAP-TLS or PEAP/MSCHAPv2? If using PEAP/MSCHAPv2 then the client would just need to trust the CA signing the ISE EAP certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2022 02:54 PM
Thanks for the reply Rob. I will check out that link.
We are using PEAP/MSCHAPv2. So if using a publicly signed Cert, like DigiCert, the clients should automatically trust this cert?
Thanks Again,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2022 02:59 PM
@Matthew Martin most devices will have the Digicert root certificate in their certificate store.
In regard to Windows devices in particular, check the authentication settings in the GPO configuration, in case you are explictly trusting only your internal CA, tick the box for the Digicert certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2022 11:53 AM
Thanks Rob!
I looked at my PC's Trusted Root Cert Authorities store and there is a couple of DigiCert root certificates in there.
I also looked in GPO Management for anything that would be only trusting our Windows CA cert. I found a few policies that are related to Certs and Authentication.
I found the following 3 GPOs (*I included screenshots below as well) :
1. 802.1x Authentication Enable - This policy enables the Wired Autoconfig service, sets "Computer only" auth, and sets the Auth Method to PEAP.
2. Machine Cert - This policy appears to enroll the PC with the CA Server, and renews the cert when it expires...
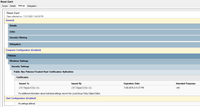
3. Root Cert - This might be what we're looking for, see screenshot... The setting under "Public Key Policies/Trusted Root Certification Authorities" shows my company name in the Issued To and Issued by fields. So I went into the full properties of the Policy and found the following in the attached screenshot, Root Cert Properties.

Thanks Again for the help!
-Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2022 12:05 PM
@Matthew Martin this is the section, if you are validating the certificate, then ensure you are trusting the new CA that is signing the certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2022 01:24 PM
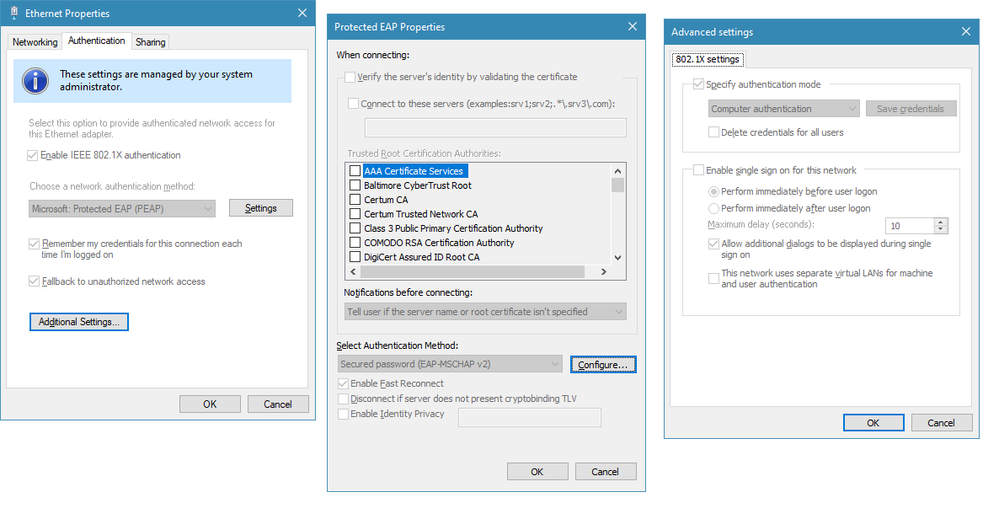
This is what my PC looks like for the Wired Adapter:
Since the Validate Server Certificate checkbox is not checked. Would it be safe to say that changing the Cert in ISE to the DigiCert for EAP Authentication shouldn't cause any auth issues? Do these settings also apply to the Wireless adapter?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2022 02:05 PM
@Matthew Martin yes, any certificate present to the client would be trusted.
Not secure though.
Yes you'd apply the same to the wireless adapter.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide