- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cisco AnyConnect Disconnect Internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 03:27 AM
Hello Cisco Community,
i have an issue with Cisco AnyConnect, when Connect to Anyconnect it disconnect my internet, i tried to configure split tunneling but same issue happened
Configuration Posted below,
Kindly Need Help
ASA Version 9.8(2)
!
hostname HorizonTechs
enable password $sha512$5000$mS2rtkhk40uzS4o+0isPPA==$X9qdaPGZBwI+DhdLvgcaIA== pbkdf2
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
ip local pool AnyConnectPool 10.0.0.10-10.0.0.100 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 41.33.245.131 255.255.255.248
!
interface GigabitEthernet1/2
bridge-group 1
nameif inside_1
security-level 100
!
interface GigabitEthernet1/3
nameif outside2
security-level 0
ip address 41.65.17.156 255.255.255.248
!
interface GigabitEthernet1/4
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/5
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/6
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/7
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/8
shutdown
bridge-group 1
no nameif
no security-level
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
boot system disk0:/asa991-1fbff-k8.spa
boot system disk0:/asa991-lfbff-k8.SPA
boot system disk0:/asdm-791.bin
boot system disk0:/asa952-lfbff-k8.SPA
ftp mode passive
clock timezone EEST 2
clock summer-time EEDT recurring last Fri Apr 0:00 last Fri Sep 0:00
dns domain-lookup outside
dns domain-lookup inside
dns server-group DefaultDNS
name-server 192.168.1.1 outside
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network NETWORK_OBJ_192.168.254.0_28
subnet 192.168.254.0 255.255.255.240
object network NETWORK_OBJ_10.0.0.0_24
subnet 10.0.0.0 255.255.255.0
object network NETWORK_OBJ_192.168.1.0_24
subnet 192.168.1.0 255.255.255.0
object network NETWORK_OBJ_10.10.10.0_25
subnet 10.10.10.0 255.255.255.128
object network NETWORK_OBJ_192.168.1.0_25
subnet 192.168.1.0 255.255.255.128
object network NETWORK_OBJ_10.0.0.0_25
subnet 10.0.0.0 255.255.255.128
access-list outside2_cryptomap extended permit ip host 41.65.17.156 host 91.231.48.157
access-list outside_access_in extended permit ip any any
access-list VPN-Remote_splitTunnelAcl standard permit 10.0.0.0 255.255.255.0
access-list outside_cryptomap extended permit ip host 41.33.245.131 host 91.231.48.157
access-list outside_cryptomap_1 extended permit ip host 41.33.245.131 host 91.231.48.157
access-list outside_cryptomap_3 extended permit ip host 41.65.17.156 host 91.231.48.157
access-list outside_cryptomap_2 extended permit ip host 41.33.245.131 host 91.231.48.157
access-list SPLIT_TUNNEL extended permit ip 192.168.1.0 255.255.255.0 any
access-list Internal-LAN standard permit host 0.0.0.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside_1 1500
mtu outside2 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit 192.168.1.0 255.255.255.0 outside
icmp permit any inside_1
icmp permit 10.0.0.0 255.255.255.0 inside
icmp permit 192.168.1.0 255.255.255.0 inside
icmp permit any inside
asdm image disk0:/asdm-782.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside_1,outside) source static any any destination static NETWORK_OBJ_10.10.10.0_25 NETWORK_OBJ_10.10.10.0_25 no-proxy-arp route-lookup
nat (inside_1,outside) source static any any destination static NETWORK_OBJ_192.168.1.0_25 NETWORK_OBJ_192.168.1.0_25 no-proxy-arp route-lookup
nat (inside_1,outside) source static any any destination static NETWORK_OBJ_10.0.0.0_25 NETWORK_OBJ_10.0.0.0_25 no-proxy-arp route-lookup
!
nat (inside_1,outside) after-auto source dynamic any interface
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 41.33.245.129 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
aaa authentication serial console LOCAL
aaa authentication telnet console LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 inside_1
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer 94.97.1.132
crypto map outside_map 1 set ikev1 transform-set ESP-AES-256-SHA
crypto map outside_map 3 match address outside_cryptomap_1
crypto map outside_map 3 set peer 94.97.1.132
crypto map outside_map 3 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 3 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 4 match address outside_cryptomap_3
crypto map outside_map 4 set peer 94.97.1.132
crypto map outside_map 4 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 4 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 5 match address outside_cryptomap_2
crypto map outside_map 5 set peer 94.97.1.132
crypto map outside_map 5 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 5 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto map outside2_map 1 match address outside2_cryptomap
crypto map outside2_map 1 set peer 94.97.1.132
crypto map outside2_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside2_map 1 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside2_map interface outside2
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment self
subject-name CN=ITDynamicsASA
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.1.1,CN=HorizonTechs
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpool policy
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 18dad19e267de8bb4a2158cdcc6b3b4a
308204d3 308203bb a0030201 02021018 dad19e26 7de8bb4a 2158cdcc 6b3b4a30
0d06092a 864886f7 0d010105 05003081 ca310b30 09060355 04061302 55533117
30150603 55040a13 0e566572 69536967 6e2c2049 6e632e31 1f301d06 0355040b
13165665 72695369 676e2054 72757374 204e6574 776f726b 313a3038 06035504
0b133128 63292032 30303620 56657269 5369676e 2c20496e 632e202d 20466f72
20617574 686f7269 7a656420 75736520 6f6e6c79 31453043 06035504 03133c56
65726953 69676e20 436c6173 73203320 5075626c 69632050 72696d61 72792043
65727469 66696361 74696f6e 20417574 686f7269 7479202d 20473530 1e170d30
36313130 38303030 3030305a 170d3336 30373136 32333539 35395a30 81ca310b
30090603 55040613 02555331 17301506 0355040a 130e5665 72695369 676e2c20
496e632e 311f301d 06035504 0b131656 65726953 69676e20 54727573 74204e65
74776f72 6b313a30 38060355 040b1331 28632920 32303036 20566572 69536967
6e2c2049 6e632e20 2d20466f 72206175 74686f72 697a6564 20757365 206f6e6c
79314530 43060355 0403133c 56657269 5369676e 20436c61 73732033 20507562
6c696320 5072696d 61727920 43657274 69666963 6174696f 6e204175 74686f72
69747920 2d204735 30820122 300d0609 2a864886 f70d0101 01050003 82010f00
3082010a 02820101 00af2408 08297a35 9e600caa e74b3b4e dc7cbc3c 451cbb2b
e0fe2902 f95708a3 64851527 f5f1adc8 31895d22 e82aaaa6 42b38ff8 b955b7b1
b74bb3fe 8f7e0757 ecef43db 66621561 cf600da4 d8def8e0 c362083d 5413eb49
ca595485 26e52b8f 1b9febf5 a191c233 49d84363 6a524bd2 8fe87051 4dd18969
7bc770f6 b3dc1274 db7b5d4b 56d396bf 1577a1b0 f4a225f2 af1c9267 18e5f406
04ef90b9 e400e4dd 3ab519ff 02baf43c eee08beb 378becf4 d7acf2f6 f03dafdd
75913319 1d1c40cb 74241921 93d914fe ac2a52c7 8fd50449 e48d6347 883c6983
cbfe47bd 2b7e4fc5 95ae0e9d d4d143c0 6773e314 087ee53f 9f73b833 0acf5d3f
3487968a ee53e825 15020301 0001a381 b23081af 300f0603 551d1301 01ff0405
30030101 ff300e06 03551d0f 0101ff04 04030201 06306d06 082b0601 05050701
0c046130 5fa15da0 5b305930 57305516 09696d61 67652f67 69663021 301f3007
06052b0e 03021a04 148fe5d3 1a86ac8d 8e6bc3cf 806ad448 182c7b19 2e302516
23687474 703a2f2f 6c6f676f 2e766572 69736967 6e2e636f 6d2f7673 6c6f676f
2e676966 301d0603 551d0e04 1604147f d365a7c2 ddecbbf0 3009f343 39fa02af
33313330 0d06092a 864886f7 0d010105 05000382 01010093 244a305f 62cfd81a
982f3dea dc992dbd 77f6a579 2238ecc4 a7a07812 ad620e45 7064c5e7 97662d98
097e5faf d6cc2865 f201aa08 1a47def9 f97c925a 0869200d d93e6d6e 3c0d6ed8
e6069140 18b9f8c1 eddfdb41 aae09620 c9cd6415 3881c994 eea28429 0b136f8e
db0cdd25 02dba48b 1944d241 7a05694a 584f60ca 7e826a0b 02aa2517 39b5db7f
e784652a 958abd86 de5e8116 832d10cc defda882 2a6d281f 0d0bc4e5 e71a2619
e1f4116f 10b595fc e7420532 dbce9d51 5e28b69e 85d35bef a57d4540 728eb70e
6b0e06fb 33354871 b89d278b c4655f0d 86769c44 7af6955c f65d3208 33a454b6
183f685c f2424a85 3854835f d1e82cf2 ac11d6a8 ed636a
quit
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate c5f33e5d
308202d6 308201be a0030201 020204c5 f33e5d30 0d06092a 864886f7 0d01010b
0500302d 31153013 06035504 03130c48 6f72697a 6f6e5465 63687331 14301206
03550403 130b3139 322e3136 382e312e 31301e17 0d313930 38303631 30313031
375a170d 32393038 30333130 31303137 5a302d31 15301306 03550403 130c486f
72697a6f 6e546563 68733114 30120603 55040313 0b313932 2e313638 2e312e31
30820122 300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101
009f9bc2 11615249 17c46a3e d879d1cd 9edf8984 9b1329b1 10e1d1e1 234c8589
fb0b33c9 627ae355 16782a64 df896840 139b249c f2cc11ee 6d9165e3 29f0c382
51a6d3e9 53065a22 30213c46 9543ff7f 4a7515da 60b44269 96f8c647 03153b92
25f57757 c0f7e3ce 36d4a3fc 0fdd19e7 d932bd52 eea11113 5a2008dc 4c3d6b5a
42742deb 38ec37f4 555ee4ec 2e60628f 1eb1c62d fff0c7f4 7cd604a7 7eb4fb96
07ade3ba d18b3b20 3b8885a6 b2741887 f1f220ad 378b1a11 26136bf9 5a96dee3
80315cde 51ee70ac 1896d3b0 ff98b889 e104346b 0b00e7a3 42a06300 bc5a0db6
c664528c d7aa72a5 7cc707d7 2c005c4d 87e4d70d 84d6b92b 2ae04634 4fc62a99
83020301 0001300d 06092a86 4886f70d 01010b05 00038201 01009ead b92a23f8
c2c12b1f a8545fcf d9e84a8d ab62d171 79bf1053 5e0032c1 d54c1a3e f6aae15d
14d5e371 6ffa1116 ef54e280 fafda078 2ca891cb 074c9c13 b7b6e3b5 a1ac0e7f
afe93ad1 04b52d2f ff414ae0 ec60aa1b 0b4b19c8 065a2c76 749b1667 622c35b5
6bfb74fa e773947d 78682e1b 9b5d5509 cd3d125a a3d7182e b6b7f315 212010a1
7ca50106 08869b1a 13cb832a 3a325aa6 0cd3f2a7 262fd515 f99c66b2 11f8af69
9527ad19 8f56031a 735b149d 52e732d0 a8fee502 183608e0 da043d70 6973ebb3
c30494c3 abb326aa c5a39d81 acdd8826 e849f01f fd0653a5 c746a377 10a12359
63a0eb7c 6d218734 6868af79 c75fb43d e36a57b7 9805c12b b19b
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_Launcher_Access_TrustPoint_0
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 policy 2
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 3600
crypto ikev1 policy 3
authentication rsa-sig
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 policy 4
authentication rsa-sig
encryption aes-256
hash sha
group 5
lifetime 3600
telnet timeout 5
no ssh stricthostkeycheck
ssh 41.33.245.128 255.255.255.248 outside
ssh 192.168.1.0 255.255.255.0 inside_1
ssh timeout 30
ssh version 2
ssh key-exchange group dh-group14-sha1
console timeout 0
vpdn username 2070069@tedata.net.eg password ***** store-local
dhcpd auto_config outside
!
dhcpd address 192.168.1.100-192.168.1.200 inside
dhcpd dns 8.8.8.8 8.8.8.8 interface inside
dhcpd auto_config outside interface inside
dhcpd option 150 ip 192.168.1.31 interface inside
dhcpd option 66 ip 192.168.1.31 interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl cipher default custom "AES256-SHA"
ssl cipher tlsv1 custom "AES256-SHA"
ssl cipher dtlsv1 custom "AES256-SHA"
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside_1
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside2
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside vpnlb-ip
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-3.1.14018-k9.pkg 1
anyconnect profiles HorizonTechs-VPN_client_profile disk0:/HorizonTechs-VPN_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
vpn-filter value outside_access_in
vpn-tunnel-protocol ikev1 ssl-client
group-policy GroupPolicy_HorizonTechs-VPN internal
group-policy GroupPolicy_HorizonTechs-VPN attributes
wins-server none
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol ssl-client
split-tunnel-policy excludespecified
split-tunnel-network-list value Internal-LAN
default-domain value cisco.com
webvpn
anyconnect profiles value HorizonTechs-VPN_client_profile type user
group-policy GroupPolicy_94.97.1.132 internal
group-policy GroupPolicy_94.97.1.132 attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol ikev1
dynamic-access-policy-record DfltAccessPolicy
username test password $sha512$5000$l0ve7YcrpY1/PwU6U6XYTg==$CZ8JaRHbCI2z0KoPPo+7Bg== pbkdf2 privilege 15
username moamen password $sha512$5000$c1m1Lay/mcwGFk8ZpX2AyA==$TqacU5kTPhYCgBHTIR/vog== pbkdf2 privilege 15
username admin password $sha512$5000$Kxd8bbPYlRTmK4U3wuE3vw==$xG/NyuxZq34+kYnNC/6MTA== pbkdf2 privilege 15
tunnel-group 94.97.1.132 type ipsec-l2l
tunnel-group 94.97.1.132 general-attributes
default-group-policy GroupPolicy_94.97.1.132
tunnel-group 94.97.1.132 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group HorizonTechs-VPN type remote-access
tunnel-group HorizonTechs-VPN general-attributes
address-pool AnyConnectPool
default-group-policy GroupPolicy_HorizonTechs-VPN
tunnel-group HorizonTechs-VPN webvpn-attributes
group-alias HorizonTechs-VPN enable
!
class-map global-class
match any
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class global-class
sfr fail-open
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
password encryption aes
Cryptochecksum:c45ab87dda7fdfc3b3dfbafe2483a3ac
: end
Solved! Go to Solution.
- Labels:
-
Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 05:22 PM
Hi, per the above configuration it looks like you are tunneling everything:
I would modify the lines below to match what is in bold
split-tunnel-policy excludespecified
-----> split-tunnel-policy tunnelspecified
split-tunnel-network-list value Internal-LAN
access-list Internal-LAN standard permit host 0.0.0.0
-----> access-list Internal-LAN standard permit 192.168.1.0 255.255.255.0
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 10:54 AM
Hi @Moamen Elsayed ,
Have a look at this diagram from the Cisco site. It may help understand the management access issue.
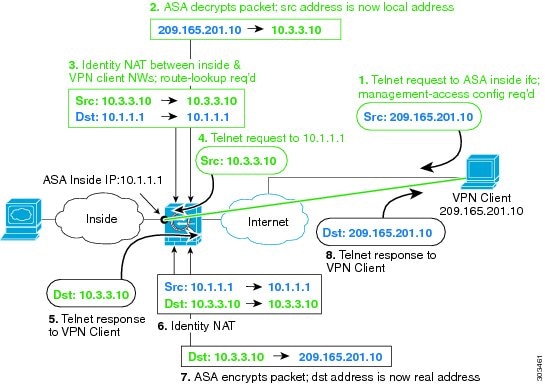
! Enable hairpin for non-split-tunneled VPN client traffic:
same-security-traffic permit intra-interface
! Enable management access on inside ifc:
management-access inside
! Identify local VPN network, & perform object interface PAT when going to Internet:
object network vpn_local subnet 10.3.3.0 255.255.255.0 nat (outside,outside) dynamic interface
! Identify inside network, & perform object interface PAT when going to Internet:
object network inside_nw subnet 10.1.1.0 255.255.255.0 nat (inside,outside) dynamic interface
! Use twice NAT to pass traffic between the inside network and the VPN client without
! address translation (identity NAT), w/route-lookup:
nat (outside,inside) source static vpn_local vpn_local destination static inside_nw inside_nw route-lookup
I have also tested the commands below in my lab, and verified ssh and ping access to inside interface when using Anyconnect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 05:22 PM
Hi, per the above configuration it looks like you are tunneling everything:
I would modify the lines below to match what is in bold
split-tunnel-policy excludespecified
-----> split-tunnel-policy tunnelspecified
split-tunnel-network-list value Internal-LAN
access-list Internal-LAN standard permit host 0.0.0.0
-----> access-list Internal-LAN standard permit 192.168.1.0 255.255.255.0
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 03:46 AM
Hello ALAN,
thanks for your support man, i wan to share another issue with you, i have made site to site VPN between posted ASA conf and another ASA on other country, i can make ssh to 91.231.48.157 from my lan behind my ASA, and i want to can ssh to same ip when i connect any connect vpn, how can i fix this??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 11:31 AM
Hi @Moamen Elsayed ,
The IP posted appears to be a public IP. When you tunnel in via Anyconnect, that IP would not be among the secured routes and thus you still would be able to ssh into it as long as the ssh access list allows it. i.e. ssh <public ip> <subnet mask> and <interface>. Have you tried this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 04:18 PM
Hello Alan,
this Ip allowed only for 192.168.1.0/24 (My LAN Network behind ASA), i configured any connect to be on same network to be able ssh on that IP, is that possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 11:18 AM
Hi @Moamen Elsayed ,
I see your Anyconnect network is configured as below:
ip local pool AnyConnectPool 10.0.0.10-10.0.0.100 mask 255.255.255.0
Maybe you can try to add this network to the ssh access list and see whether you are able to access the inside interface after connecting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 05:04 PM
i can not ping or ssh to asa ip i can only ping to other pc on network 192.168.1.170.
why i can not access to asa
note:
i add this nat (outside,any) source static vpn_pool_ip vpn_pool_ip destination static inside inside no-proxy-arp
but am still can not ssh or ping inside interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 06:12 PM
Hi @Moamen Elsayed ,
Let me run this in a lab and get back to you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 07:06 PM
In the meantime, you can also check this out:
https://www.petenetlive.com/KB/Article/0000984
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 10:54 AM
Hi @Moamen Elsayed ,
Have a look at this diagram from the Cisco site. It may help understand the management access issue.

! Enable hairpin for non-split-tunneled VPN client traffic:
same-security-traffic permit intra-interface
! Enable management access on inside ifc:
management-access inside
! Identify local VPN network, & perform object interface PAT when going to Internet:
object network vpn_local subnet 10.3.3.0 255.255.255.0 nat (outside,outside) dynamic interface
! Identify inside network, & perform object interface PAT when going to Internet:
object network inside_nw subnet 10.1.1.0 255.255.255.0 nat (inside,outside) dynamic interface
! Use twice NAT to pass traffic between the inside network and the VPN client without
! address translation (identity NAT), w/route-lookup:
nat (outside,inside) source static vpn_local vpn_local destination static inside_nw inside_nw route-lookup
I have also tested the commands below in my lab, and verified ssh and ping access to inside interface when using Anyconnect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 01:24 PM
unfortunately inside interface still unreachable ssh and ping
you can take a look to updated configuration below:
ASA Version 9.8(2)
!
hostname HorizonTechs
enable password $sha512$5000$mS2rtkhk40uzS4o+0isPPA==$X9qdaPGZBwI+DhdLvgcaIA== pbkdf2
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
ip local pool AnyConnectPool 10.0.0.10-10.0.0.100 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 41.33.245.131 255.255.255.248
!
interface GigabitEthernet1/2
bridge-group 1
nameif inside_1
security-level 100
!
interface GigabitEthernet1/3
nameif outside2
security-level 0
ip address 41.65.17.156 255.255.255.248
!
interface GigabitEthernet1/4
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/5
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/6
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/7
shutdown
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/8
shutdown
bridge-group 1
no nameif
no security-level
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
boot system disk0:/asa991-1fbff-k8.spa
boot system disk0:/asa991-lfbff-k8.SPA
boot system disk0:/asdm-791.bin
boot system disk0:/asa952-lfbff-k8.SPA
ftp mode passive
clock timezone EEST 2
clock summer-time EEDT recurring last Fri Apr 0:00 last Fri Sep 0:00
dns domain-lookup outside
dns domain-lookup inside
dns server-group DefaultDNS
name-server 192.168.1.1 outside
same-security-traffic permit intra-interface
object network NETWORK_OBJ_10.0.0.0_25
subnet 10.0.0.0 255.255.255.128
object network inside
object network inside_nw
subnet 192.168.1.0 255.255.255.0
access-list outside2_cryptomap extended permit ip host 41.65.17.156 host 91.231.48.157
access-list outside_access_in extended permit ip any any
access-list VPN-Remote_splitTunnelAcl standard permit 10.0.0.0 255.255.255.0
access-list outside_cryptomap extended permit ip host 41.33.245.131 host 91.231.48.157
access-list outside_cryptomap_1 extended permit ip host 41.33.245.131 host 91.231.48.157
access-list outside_cryptomap_3 extended permit ip host 41.65.17.156 host 91.231.48.157
access-list outside_cryptomap_2 extended permit ip host 41.33.245.131 host 91.231.48.157
access-list Internal-LAN standard permit host 0.0.0.0
access-list Internal-LAN standard permit 192.168.1.0 255.255.255.0
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside_1 1500
mtu outside2 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-782.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside_1,outside) source static any any destination static NETWORK_OBJ_10.0.0.0_25 NETWORK_OBJ_10.0.0.0_25 no-proxy-arp route-lookup
nat (inside_1,outside) source dynamic any interface
nat (outside,inside_1) source static NETWORK_OBJ_10.0.0.0_25 NETWORK_OBJ_10.0.0.0_25 destination static inside_nw inside_nw route-lookup
!
object network NETWORK_OBJ_10.0.0.0_25
nat (outside,outside) dynamic interface
object network inside_nw
nat (inside_1,outside) dynamic interface
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 41.33.245.129 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
aaa authentication serial console LOCAL
aaa authentication telnet console LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 inside_1
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer 94.97.1.132
crypto map outside_map 1 set ikev1 transform-set ESP-AES-256-SHA
crypto map outside_map 3 match address outside_cryptomap_1
crypto map outside_map 3 set peer 94.97.1.132
crypto map outside_map 3 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 3 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 4 match address outside_cryptomap_3
crypto map outside_map 4 set peer 94.97.1.132
crypto map outside_map 4 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 4 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 5 match address outside_cryptomap_2
crypto map outside_map 5 set peer 94.97.1.132
crypto map outside_map 5 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 5 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto map outside2_map 1 match address outside2_cryptomap
crypto map outside2_map 1 set peer 94.97.1.132
crypto map outside2_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside2_map 1 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside2_map interface outside2
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment self
subject-name CN=ITDynamicsASA
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.1.1,CN=HorizonTechs
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpool policy
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 18dad19e267de8bb4a2158cdcc6b3b4a
308204d3 308203bb a0030201 02021018 dad19e26 7de8bb4a 2158cdcc 6b3b4a30
0d06092a 864886f7 0d010105 05003081 ca310b30 09060355 04061302 55533117
30150603 55040a13 0e566572 69536967 6e2c2049 6e632e31 1f301d06 0355040b
13165665 72695369 676e2054 72757374 204e6574 776f726b 313a3038 06035504
0b133128 63292032 30303620 56657269 5369676e 2c20496e 632e202d 20466f72
20617574 686f7269 7a656420 75736520 6f6e6c79 31453043 06035504 03133c56
65726953 69676e20 436c6173 73203320 5075626c 69632050 72696d61 72792043
65727469 66696361 74696f6e 20417574 686f7269 7479202d 20473530 1e170d30
36313130 38303030 3030305a 170d3336 30373136 32333539 35395a30 81ca310b
30090603 55040613 02555331 17301506 0355040a 130e5665 72695369 676e2c20
496e632e 311f301d 06035504 0b131656 65726953 69676e20 54727573 74204e65
74776f72 6b313a30 38060355 040b1331 28632920 32303036 20566572 69536967
6e2c2049 6e632e20 2d20466f 72206175 74686f72 697a6564 20757365 206f6e6c
79314530 43060355 0403133c 56657269 5369676e 20436c61 73732033 20507562
6c696320 5072696d 61727920 43657274 69666963 6174696f 6e204175 74686f72
69747920 2d204735 30820122 300d0609 2a864886 f70d0101 01050003 82010f00
3082010a 02820101 00af2408 08297a35 9e600caa e74b3b4e dc7cbc3c 451cbb2b
e0fe2902 f95708a3 64851527 f5f1adc8 31895d22 e82aaaa6 42b38ff8 b955b7b1
b74bb3fe 8f7e0757 ecef43db 66621561 cf600da4 d8def8e0 c362083d 5413eb49
ca595485 26e52b8f 1b9febf5 a191c233 49d84363 6a524bd2 8fe87051 4dd18969
7bc770f6 b3dc1274 db7b5d4b 56d396bf 1577a1b0 f4a225f2 af1c9267 18e5f406
04ef90b9 e400e4dd 3ab519ff 02baf43c eee08beb 378becf4 d7acf2f6 f03dafdd
75913319 1d1c40cb 74241921 93d914fe ac2a52c7 8fd50449 e48d6347 883c6983
cbfe47bd 2b7e4fc5 95ae0e9d d4d143c0 6773e314 087ee53f 9f73b833 0acf5d3f
3487968a ee53e825 15020301 0001a381 b23081af 300f0603 551d1301 01ff0405
30030101 ff300e06 03551d0f 0101ff04 04030201 06306d06 082b0601 05050701
0c046130 5fa15da0 5b305930 57305516 09696d61 67652f67 69663021 301f3007
06052b0e 03021a04 148fe5d3 1a86ac8d 8e6bc3cf 806ad448 182c7b19 2e302516
23687474 703a2f2f 6c6f676f 2e766572 69736967 6e2e636f 6d2f7673 6c6f676f
2e676966 301d0603 551d0e04 1604147f d365a7c2 ddecbbf0 3009f343 39fa02af
33313330 0d06092a 864886f7 0d010105 05000382 01010093 244a305f 62cfd81a
982f3dea dc992dbd 77f6a579 2238ecc4 a7a07812 ad620e45 7064c5e7 97662d98
097e5faf d6cc2865 f201aa08 1a47def9 f97c925a 0869200d d93e6d6e 3c0d6ed8
e6069140 18b9f8c1 eddfdb41 aae09620 c9cd6415 3881c994 eea28429 0b136f8e
db0cdd25 02dba48b 1944d241 7a05694a 584f60ca 7e826a0b 02aa2517 39b5db7f
e784652a 958abd86 de5e8116 832d10cc defda882 2a6d281f 0d0bc4e5 e71a2619
e1f4116f 10b595fc e7420532 dbce9d51 5e28b69e 85d35bef a57d4540 728eb70e
6b0e06fb 33354871 b89d278b c4655f0d 86769c44 7af6955c f65d3208 33a454b6
183f685c f2424a85 3854835f d1e82cf2 ac11d6a8 ed636a
quit
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate c5f33e5d
308202d6 308201be a0030201 020204c5 f33e5d30 0d06092a 864886f7 0d01010b
0500302d 31153013 06035504 03130c48 6f72697a 6f6e5465 63687331 14301206
03550403 130b3139 322e3136 382e312e 31301e17 0d313930 38303631 30313031
375a170d 32393038 30333130 31303137 5a302d31 15301306 03550403 130c486f
72697a6f 6e546563 68733114 30120603 55040313 0b313932 2e313638 2e312e31
30820122 300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101
009f9bc2 11615249 17c46a3e d879d1cd 9edf8984 9b1329b1 10e1d1e1 234c8589
fb0b33c9 627ae355 16782a64 df896840 139b249c f2cc11ee 6d9165e3 29f0c382
51a6d3e9 53065a22 30213c46 9543ff7f 4a7515da 60b44269 96f8c647 03153b92
25f57757 c0f7e3ce 36d4a3fc 0fdd19e7 d932bd52 eea11113 5a2008dc 4c3d6b5a
42742deb 38ec37f4 555ee4ec 2e60628f 1eb1c62d fff0c7f4 7cd604a7 7eb4fb96
07ade3ba d18b3b20 3b8885a6 b2741887 f1f220ad 378b1a11 26136bf9 5a96dee3
80315cde 51ee70ac 1896d3b0 ff98b889 e104346b 0b00e7a3 42a06300 bc5a0db6
c664528c d7aa72a5 7cc707d7 2c005c4d 87e4d70d 84d6b92b 2ae04634 4fc62a99
83020301 0001300d 06092a86 4886f70d 01010b05 00038201 01009ead b92a23f8
c2c12b1f a8545fcf d9e84a8d ab62d171 79bf1053 5e0032c1 d54c1a3e f6aae15d
14d5e371 6ffa1116 ef54e280 fafda078 2ca891cb 074c9c13 b7b6e3b5 a1ac0e7f
afe93ad1 04b52d2f ff414ae0 ec60aa1b 0b4b19c8 065a2c76 749b1667 622c35b5
6bfb74fa e773947d 78682e1b 9b5d5509 cd3d125a a3d7182e b6b7f315 212010a1
7ca50106 08869b1a 13cb832a 3a325aa6 0cd3f2a7 262fd515 f99c66b2 11f8af69
9527ad19 8f56031a 735b149d 52e732d0 a8fee502 183608e0 da043d70 6973ebb3
c30494c3 abb326aa c5a39d81 acdd8826 e849f01f fd0653a5 c746a377 10a12359
63a0eb7c 6d218734 6868af79 c75fb43d e36a57b7 9805c12b b19b
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 remote-access trustpoint ASDM_Launcher_Access_TrustPoint_0
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 policy 2
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 3600
crypto ikev1 policy 3
authentication rsa-sig
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 policy 4
authentication rsa-sig
encryption aes-256
hash sha
group 5
lifetime 3600
telnet timeout 5
no ssh stricthostkeycheck
ssh 41.33.245.128 255.255.255.248 outside
ssh 10.0.0.0 255.255.255.0 outside
ssh 192.168.1.0 255.255.255.0 inside_1
ssh 10.0.0.0 255.255.255.0 inside_1
ssh timeout 30
ssh version 2
ssh key-exchange group dh-group14-sha1
console timeout 0
management-access inside_1
vpdn username 2070069@tedata.net.eg password ***** store-local
vpn-sessiondb max-anyconnect-premium-or-essentials-limit 20
dhcpd auto_config outside
!
dhcpd address 192.168.1.100-192.168.1.200 inside
dhcpd dns 8.8.8.8 8.8.8.8 interface inside
dhcpd auto_config outside interface inside
dhcpd option 150 ip 192.168.1.31 interface inside
dhcpd option 66 ip 192.168.1.31 interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl cipher default custom "AES256-SHA"
ssl cipher tlsv1 custom "AES256-SHA"
ssl cipher dtlsv1 custom "AES256-SHA"
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside_1
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 inside
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-3.1.14018-k9.pkg 1
anyconnect profiles HorizonTechs-VPN_client_profile disk0:/HorizonTechs-VPN_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
vpn-filter value outside_access_in
vpn-tunnel-protocol ikev1 ssl-client
group-policy GroupPolicy_HorizonTechs-VPN internal
group-policy GroupPolicy_HorizonTechs-VPN attributes
wins-server none
dns-server value 192.168.1.1
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Internal-LAN
default-domain value cisco.com
group-policy GroupPolicy_94.97.1.132 internal
group-policy GroupPolicy_94.97.1.132 attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol ikev1
dynamic-access-policy-record DfltAccessPolicy
username test password $sha512$5000$+aSSWB8pE4hpimi95DNmKw==$iUld6u8YtYnFGplNGutRaw== pbkdf2 privilege 15
username moamen password $sha512$5000$kd9VL51bwARHO/TBrSuTOQ==$Tdg02MRe1j+v0cQDxsRYrw== pbkdf2 privilege 15
username admin password $sha512$5000$np0GhBCd1qt5NzWqgxXqTQ==$Yao4Q7/aL/sWmF3CB4vEZA== pbkdf2 privilege 15
tunnel-group 94.97.1.132 type ipsec-l2l
tunnel-group 94.97.1.132 general-attributes
default-group-policy GroupPolicy_94.97.1.132
tunnel-group 94.97.1.132 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group HorizonTechs-VPN type remote-access
tunnel-group HorizonTechs-VPN general-attributes
address-pool AnyConnectPool
default-group-policy GroupPolicy_HorizonTechs-VPN
tunnel-group HorizonTechs-VPN webvpn-attributes
group-alias HorizonTechs-VPN enable
!
class-map global-class
match any
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class global-class
sfr fail-open
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
password encryption aes
Cryptochecksum:42b1acdf4fb159f7fada1958dab2e279
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2019 02:37 AM
Its worked and i can manage asa but am still can not ssh to this ip 91.231.48.157
From anyconnect but i can if am on lan behind asa, what do you think about that
Note: this ip tunnled with another asa on other country
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2019 06:33 PM
Thank you!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide