- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco FMC and SAML
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco FMC and SAML
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 12:15 AM - edited 09-30-2022 02:22 AM
Hello,
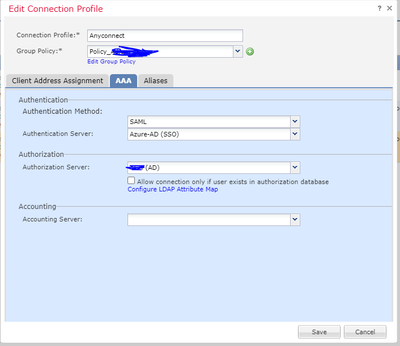
We have Cisco FMC\FTD (Version is 7.0.1) integrated with Azure SAML for Anyconnect MFA, also done integration with Active Directory for other purposes. Authentication works, I can connect to the Anyconnect. But now I need to also provide Authorization (For example, User1 must have access to some servers, but User2 doesn't). How I can do this?
When I add Authorization in Profile settings, then Authentication is failed.
How I can configure Azure SAML + Authorization by AD Groups?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 01:36 AM
Good question! I don't think AD can provide any type of authorization, I think you would need to use a RADIUS server to set those attributes. Do you have any RADIUS server in your environment?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 02:26 AM
Yes, I have Windows NPS Radius Server, which we use for WIFI-Authentication. Also we have Cisco ACS, but we use it just for TACACS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 02:32 AM
I would recommend using ACS, set up the authorization rules to match the users based on their AD group, or even usernames, and then associate the rules with dACLs where you can define their access level. I would also turn on CoA on the FTD and configure the ACS as the authorization server. Also, please keep in mind that you can actually use the ACS for both authentication and authorization, in that case the FTD will point to the ACS and then the ACS will check the users identities against the AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 02:42 AM
But If I use ACS also for authentication, then I need to integrate ACS with Azure-SAML, correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 03:05 AM
Yeah that's right, however, to keep things simple, you can leave the authentication as is and just use ACS for authorization.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 03:20 AM
Yes, as I see ACS doesn't support SAML.
I will try, thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 04:41 AM - edited 09-30-2022 04:41 AM
I didn't know that, thanks for sharing and you're welcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 09:40 AM
If you have a RADIUS server (NPS, ISE, old ACS etc.) you can use it for Authorization separately from the Azure AD you use for Authentication via the SAML method.
ISE TME Jason Maynard has created a YouTube video demonstrating the procedure step-by-step:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 12:13 PM
I will try dACL, as has suggested Aref Alsouqi, because I don't have ISE and unfortunatelly ACS doesn't has capavilities of ISE.
I'm not sure why FTD Anyconnect bypass traffic after SAML Authentication... But with dACL I can configure some kind of restricted accesses. But in this case I will lose NGFW capabilities of FTD (I mean, for example, IPS), am I correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2022 08:11 PM
ACS is capable of applying Authorization results based on a RADIUS authentication.
Even if you apply a dACL you still retain the ability to inspect traffic with the full capabilities of the FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2022 08:09 AM
Hello,
I have additional question:
I just will do authorization trough Cisco ACS for providing limited accesses (dACL) and then I will create one rule on FMC itself with "monitor" in Action field and apply, for example, IPS, correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 04:16 AM - edited 10-26-2022 05:07 AM
I configured our FMC in several ways:
1 - I configured Radius Server object on FMC, enable\disabled Dynamic Authentication, but nothing works. On Radius server itself I see next logs:
ACSVersion=acs-5.8.0.32-B.442.x86_64 : ConfigVersionId=140 : Device Port=61652 : RadiusPacketType=AccessRequest : Protocol=Radius : Called-Station-ID=95.*.*.246 : CVPN3000/ASA/PIX7.x-DAP-Tunnel-Group-Name=Anyconnect : AD-User-Candidate-Identities=irakli.gvishiani@*.com : StepData=9=Irakli.Gvishiani@*.com : StepData=10=*.com : StepData=11=*.com : StepData=13=STATUS_WRONG_PASSWORD,ERROR_INVALID_PASSWORD,irakli.gvishiani@*.com : Device IP Address=172.31.254.253
2 - I configured Radius Server object on FMC and enable just Authorization (Authorize only), but nothing works. On Radius server itself I see next logs:
ACSVersion=acs-5.8.0.32-B.442.x86_64 : ConfigVersionId=141 : Device Port=61652 : RadiusPacketType=AccessRequest : Protocol=Radius : Service-Type=Authorize Only : Called-Station-ID=95.*.*.246 : CVPN3000/ASA/PIX7.x-DAP-Tunnel-Group-Name=Anyconnect : DetailedInfo=UserName or Password is missing : Device IP Address=172.31.254.253
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 05:12 AM - edited 10-26-2022 05:18 AM
Also in Authentication I see that username appeared with domain postfix, can It be problem?
Because also I use Tacacs for User Authentication\Authorization for Device Access and there usernames are without domain postfix:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2022 03:47 AM - edited 10-28-2022 03:47 AM
Have anybody already done SAML + Authorization by AD Groups somehow?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide