- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: crypto key generate rsa signature command
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
crypto key generate rsa signature command
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2020 08:46 AM
Hi,
Can someone explain to me how does a router use the RSA signature key generated by the following command:
crypto key generate rsa signature
The command generates only one key as shown by the show crypto key mypubkey all command.
Does the router use this key to sign messages or certificates sent to remote peers?
Does the router sends this key to remote peers? If so, do remote peers use this key to send signed messages to the router?
In what context is this type of key used? IPsec? Diffie Hellman? IKE?
Please help me understand how this key is used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2020 11:14 PM
The key is used in securing ssh sessions. If the device also uses s a self-signed certificate the key may be used as the private key for the certificate (or you can optionally create and specify a separate key for use with your certificate). A device's certificate can be used for IKEv2 IPsec or for SSL/TLS sessions to the device's web UI (where such exists and is enabled).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2020 12:12 AM
@marvin gave you a very good explanation on the key. Just a small comment
on your command, the key word *signature* (at the end of the line) will
generate a key to be used for signing purpose only. It won't be used for
encrypting IKE VPN or WebUI. For a multi purpose key, you need to specify
the keyword *general-purpose* instead.
The key isn't sent to any peer. Instead it's used to sign messages (HMAC
hashing), signing certificates, etc. This is the concept of PKI that a
private key isn't sent. Only the public key in the certificate is
published.
You can read this.
https://www.digicert.com/blog/where-is-your-private-key/
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2020 05:02 AM
Ah thanks @Mohammed al Baqari for making that important distinction with the "signature" keyword.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2020 05:25 AM - edited 08-02-2020 06:30 AM
Thank you @Mohammed al Baqari for taking the time to try to answer my questions.
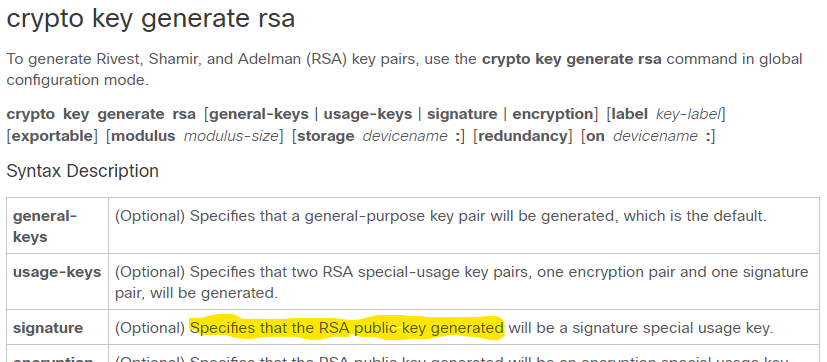
although I already know that the private key (not the public key) is used for signing a message or a certificate, I am surprised to know that this command produces a private key and not a public key. The reason for my confusion is the Cisco Command Reference Explanation! See the snapshot of it below!
I tend to think of it as a private key, as you said. The question now is how a peer receiving a message or a certificate, signed by this key, verify the integrity of the received message or certificate without the corresponding public key that is used to decrypt the signature?
The command generates only one key that is used for signature! Where is the corresponding public key?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2020 09:21 AM
The command generate both public and private key (keypair). To answer your
question, it depends on the use case. For example if you use IPsec
certificate authentication, the peers exchange their certs which include
the public key in messages 4 and 5 of Main Mode (IKEV1). This helps to
verify signatures. For webUI, the cert will be presented to the browser,
etc.
All subject to use case.
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2020 03:48 AM - edited 08-05-2020 03:50 AM
Thank you Mohammed.Things are clear now. What caused the confusion is that I did not notice that the show crypto key mypubkey all command shows only the public keys. Corresponding private keys are not shown.
@Mohammed al Baqari wrote:
Hi,
The command generate both public and private key (keypair). To answer your
question, it depends on the use case. For example if you use IPsec
certificate authentication, the peers exchange their certs which include
the public key in messages 4 and 5 of Main Mode (IKEV1). This helps to
verify signatures. For webUI, the cert will be presented to the browser,
etc.
All subject to use case.
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2020 04:07 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide