- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Deny Lan Access Anyconnect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Deny Lan Access Anyconnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 02:52 AM
Hello
We are on anyconnect 4.9 and ASA 5516.
When users are connected to VPN using anyconnect, we want to maintain split tunneling and deny access to their local Lan (or access to corporate laptop from local lan), is this possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 03:01 AM
@InTheJuniverse you should have a configuration similar to below
ciscoasa(config)#access-list Local_LAN_Access remark Client Local LAN Access
ciscoasa(config)#access-list Local_LAN_Access standard permit host 0.0.0.0
this is used for Local LAN access, if you do not wish to permit this access remove it.
Refer to this cisco guide on how to setup and do the opposite to unconfigure, the guide is CLI and ASDM so you should be able to work out the steps to remove that configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 03:11 AM
Thank you.
So, if 'Allow local Lan' access is removed, all traffic is tunnelled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 03:20 AM
@InTheJuniverse that configuration is in addition to your split tunnel configuration, so it depends on what the rest of your configuration. Provide the configuration if you wish it to be reviewed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 03:27 AM
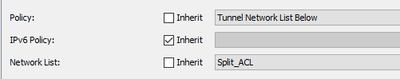
it's a simple split tunnel. In the ACL we added some corporate subnets.
group-policy SSLVPN internal
group-policy SSLVPN attributes
dns-server value 20.1.1.1
dhcp-network-scope 20.200.65.0
vpn-tunnel-protocol ssl-client
group-lock value SSLVPN
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_ACL
default-domain value xxxxxxxxxx
split-dns value xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
webvpn
anyconnect profiles value Anyconnect-SSLVPN type user
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 03:34 AM
@InTheJuniverse what is the configuration of "Split_ACL"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 03:39 AM - edited 03-16-2022 03:39 AM
access-list Split_ACL standard permit 20.0.0.0 255.0.0.0
access-list Split_ACL standard permit 141.127.0.0 255.255.0.0
access-list Split_ACL standard permit 172.19.0.0 255.255.0.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 05:14 AM
ASA(config-group-policy)#split-tunnel-policy excludespecified
ASA(config-group-policy)#split-tunnel-network-list value Local_LAN_Access
try this way instead of permit the Core LAN, deny the local LAN and make other go through tunnel.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide