- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD integration with Active Directory
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2015 07:26 PM - edited 03-11-2019 10:22 PM
Hi,
I recently having lab for ASA with FirePower integrated Microsoft AD deployment,
but I am wondering whether FirePower must install agent on AD server?
I installed agent on AD server and setting LDAP connection on FireSIGHT VDC server,
then it can fetch AD forest, and dashboard about source/destination user is all can display user information,
but I tried remove agent and stop service on AD, then the FireSIGHT VDC is still can settings LDAP connection,
so i am wondering whether FirePower must install agent on AD server,
If not, has different between both install or uninstall?
please help, thanks!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 07:12 AM
Just to cover all the bases...did you setup FireSIGHT to receive the user data?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 07:26 AM
i set the Identity Source, with IP of the user agent, i Setup a realm an download users..
And at the Access Policy i set selected User: MYDOMAIN/*
and at Advanced i set my identity policy
At the Identity Policy I import my Realm set to enabled with "passive Authentication"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 07:05 AM
I ran across an issue like this where it was caused by a Windows Server patch. Cisco has identified this bug as CSCva32331. Basically it required TLS? traffic to be a minimum of 1024-bit and so Windows Server wouldn't talk to Firesight. I had to create a registry key to lower the minimum bitrate to 512.
This was supposed to be fixed in Firepower 6.1 but I haven't installed it yet to verify.
So you can do 1 of 2 things.
#1: Uninstall KB3161606 from your Windows Server
#2: Go through steps below:
1. Click Start, click Run, type regedit in the Open box, and then click OK.
2. Locate and then click the following subkey in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\
3. On the edit Menu, point to new and click Key, name the new Key "Diffie-Hellman"
4. Navigate the the new Key created.
3. On the Edit menu, point to New, and then click DWORD Value.
4. Type ClientMinKeyBitLength for the name of the DWORD, and then press Enter.
5. Right-click ClientMinKeyBitLength, and then click Modify.
6. In the Value data box, type 00000200 (keep this in hexidecimal format), and then click OK.
After this is completed, you will need to restart the User Agent server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2016 08:36 AM
hm.. now it seams everything is available, but still nothing at "last reported"... it is really frustrating...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2016 09:40 AM
You need to verify that you have logon and logoff events enabled and that they're being logged.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2016 03:02 AM
Ok, i thought a DC would log logon and logoff events automaticly,
so i make an GPO for the whole domain with
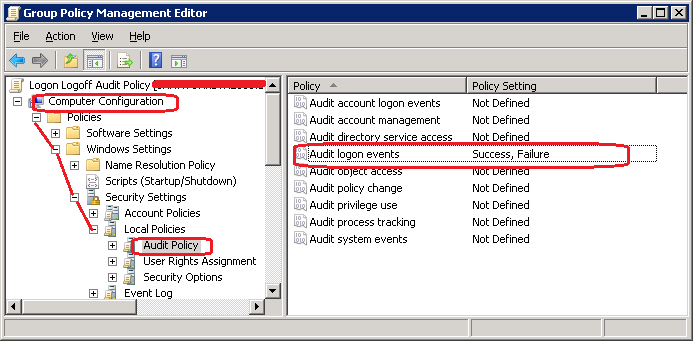
should it set for everybody and filtered for domain-users and domain-computers?
i've setted it for Domain-users yesterday and today nothing happened....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2016 07:22 AM
I have this set on the Default Domain Controllers Policy. The security filtering is set to Authenticated Users, Enterprise Admins, and SYSTEM (these were there before so I didn't adjust them).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2016 07:36 AM
yes, it was activated with my own gpo object, now i delete the old object and set it on Defaul DC Policy...
but for me it seems like, the user agent isnt working...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 11:57 PM
Do you got no idea, why it doesnt map Users?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2017 06:21 AM
Hi Marvin,
If my Firepower agent gets corrupted or for some issue it is not able to send logs to ASA, how would the access go? Would there be some issue in it?
What will happen to new connections?
Can we install the agent on a VM?
Also is there any software requirement for FMC? I know we need a VM with 256 GB memory , 8 gb memory , 4 cpu?
Is there any other thing which I need before I place my order.
Thanks in advance!!
Regards
Vaibhav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2017 10:47 PM
I have used User Agent 2.3 with good success on several installations. I try to install it locally on the DC(s) if possible. If it is not working it would only affect connections if your Access Control Policy used users or groups they belong to. Your reporting would also not be able to ascertain the username.
On the FMC you need at least those minimums. It doesn't help a lot but I usually try to double the RAM and vCPU allocation if the resources are available. Cisco does not allow you to change the allocated disk storage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2017 10:54 PM
Hi Marvin,
Thanks for this.
We are thinking of only making the policies based on user names and groups.
So if our agent fails, would the connection fail.
If we add a backup policy , for LAN--> internet http,https.. would it hit after agent fails.
I do not want to affect any normal traffic because of it being traffic dependent. Is it advisable to use multiple agents?
Thanks in advance!!
Regards
Vaibhav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2017 11:32 PM
Access Control Policy (ACP) rules are evaluated from the top down and the first match ends the rule processing. So if you have a catch all rule or set of rules at the bottom of the list they would be evaluated in the event that an earlier rule was not matched.
If you have ISE you can also use it as an alternative identity source. There is even a new lightweight ISE license type known as ISE PIC (Passive Identity Connector) that does not required a full blown 802.1x deployment of Network Access Control.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 06:11 AM
hi,
With FTD can we integrate Active Directory without Agent being installed in the environment. Like Agentless User-ID available in Palo Alto. thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 07:37 AM
If you are using ACP rules based on user then you need to have agent. But
if you are looking to import groups for role based access to FTD/FMC then
agent isn't required.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide






