- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Ensure NetBios traffic is not permitted to leave our network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ensure NetBios traffic is not permitted to leave our network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 01:55 PM - edited 02-21-2020 09:06 AM
Hello!
I've been asked to verify that NetBios traffic is not able to leave our network; specifically ports 445 and 139. My basic understanding makes me think that is the case but I'm not sure how to verify that. We are using ASA5525's in a HA configuration.
The request is to make sure NetBios traffic is blocked from leaving our network. Is that not already the default?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 06:32 PM
Hi,
Configure an access list on the firewall and you will be sure the traffic is not leaving the network.
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 06:32 AM
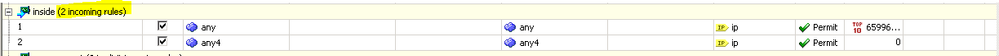
Just for understanding, this is a screen grab of my Firewall --> Access Rules. There are 2 rules, each allowing ANY/ANY. However, this ACL is labeled as "Incoming". Shouldn't I be seeing "Outgoing" somewhere?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 05:46 PM
Hi,
Incoming is correct. You need to deny the traffic inbound on the Inside interface.Create a rule on line 1 and only deny the ports you require.
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 07:11 PM
Like @johnd2310 said, we deny traffic incoming on the inside interface. That drops it as soon as it is received by the ASA and keeps it from being processed further (thus no need for an outbound ACL entry).
So add a new rule before the current line 1. Best is to create a service object group when building the rule to equal NetBIOS (tcp/445 and tcp/139). To do that, note that the GUI allows you to "add new group" when specifying the destination port(s)/service(s).
Also ensure you haven't allowed the traffic inbound from the Internet. That is the more high risk threat by far. I have seen customers allow all ports to a given Windows server thus exposing it to exploits and, by extension, compromising their entire internal network. Once you can "own" a given server from the outside you can usually use it to springboard to other resources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 07:15 PM
By default all traffic is allowed to transit from a higher security level (inside) to a lower security level (outside).
If there is an ACL applied to the inside interface, an implicit deny is then used for any traffic not specified.
You can always check an ASA firewall's handling of a given traffic flow using the packet tracer utility. for example:
packet-tracer input inside tcp <some inside address> 1025 <any outside address - e.g. 8.8.8.8> 445
...will check if tcp/445 is allowed outbound.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 06:16 AM - edited 05-07-2019 06:17 AM
Thanks Marvin,
I did the packet tracing and that traffic is certainly able to get out of our network. I started looking at creating an ACL to block Netbios but I'm struggling to figure that out. I'm not a CLI wizard by any stretch and mostly work from within the ASDM. When I go to ACL Manager I can create a new ACL but I don't see where I configure that ACL. All I can do is name it. Thoughts?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide