- Cisco Community
- Technology and Support
- Security
- Network Security
- external networks are not able to connect networks behind ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 09:56 AM
Hello all,
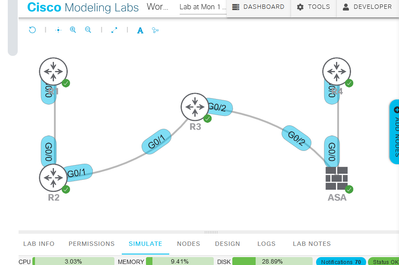
I am able to ping from R4(G0/0) to R1(G 0/0).But not from R4 to R1. Because R4 is behind ASA. I have copied the images and details for reference.
R1 -10.0.0.1/24
R4 -10.1.0.1/24
R1-R2 -10.0.0.0/24
R4-ASA -10.1.0.0/24
R2-R3 -20.0.0.0/30
R3-ASA - 21.0.0.0/30
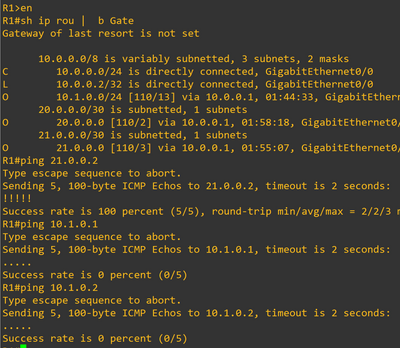
R1-availble routes
Ping is failed from R1 to R4. But R1 is able to ping outside interface(g0/2) of ASA
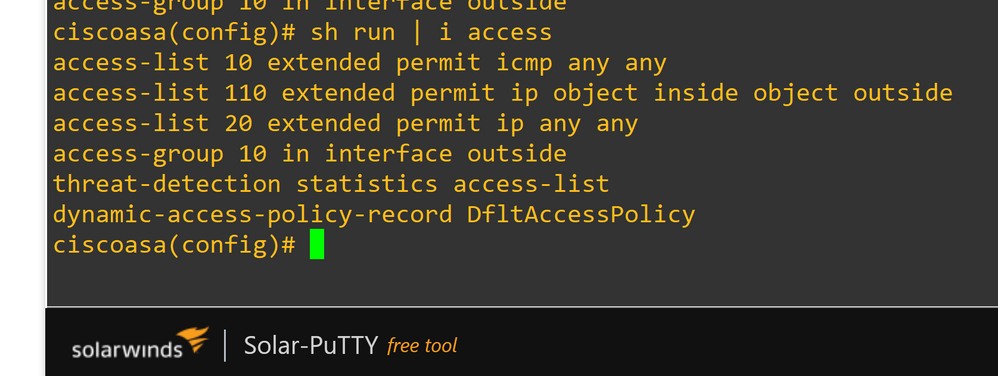
Configured access list 10 on asa outside interface to allow icmp traffic.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 12:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 10:19 AM
Hi @Cisconew
Is NAT configured on the ASA?
You'd never (by design) be able to ping the ASA inside interface IP address if you are connecting through the ASA via another interface (outside).
Can you run packet-tracer from the CLI and provide the output - "packet-tracer input outside 10.0.0.1 8 0 10.1.0.2"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 10:40 AM
Hi Rob Ingram,
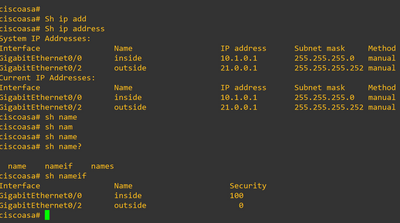
I have enabled NAT as given below.
The reason i am trying to connect from outside is i am configuring ipsec(IKEV2) VPN between ASA & R2.
ciscoasa(config)# sh run object
object network inside
subnet 10.1.0.0 255.255.255.0
object network outside
subnet 10.0.0.0 255.255.255.0
ciscoasa(config)# sh run nat
!
object network inside
nat (inside,outside) dynamic interface
ciscoasa(config)# packet-tracer input outside icmp 10.0.0.2 8 0 10.1.0.2
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 10.1.0.2 using egress ifc inside
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group 10 in interface outside
access-list 10 extended permit icmp any any
Additional Information:
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: QOS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 8
Type: VPN
Subtype: ipsec-tunnel-flow
Result: DROP
Config:
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x0000562a2f69cc06 flow (tunnel-pending)/snp_sp_action_cb:1748
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 10:45 AM
@Cisconew well the traffic is being dropped at the VPN phase, so what VPN configuration do you have configured?
If you are pinging between those networks, you'll need a NAT exemption rule to ensure traffic sent between the R1 and R4 networks is not unintentially translated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 11:03 AM
hI Rob Ingram,
Actually it didn't work, even before i apply vpn configurations to R2 & ASA.
So i will remove vpn configurations and check the connectivity and post the details.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 11:41 AM
Hi Rob,
I have reworked the lab and this time connectivity works before i apply vpn config.
Please find below the packet tarcer results:
ciscoasa# packet-tracer input outside icmp 10.0.0.2 8 0 10.1.0.2
Phase: 1
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 10.1.0.2 using egress ifc inside
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static inside inside destination static outside outside no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface inside
Untranslate 10.1.0.2/0 to 10.1.0.2/0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group 10 in interface outside
access-list 10 extended permit icmp any any
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static inside inside destination static outside outside no-proxy-arp route-lookup
Additional Information:
Static translate 10.0.0.2/0 to 10.0.0.2/0
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: QOS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: VPN
Subtype: ipsec-tunnel-flow
Result: DROP
Config:
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000055e6efbd4c06 flow (tunnel-pending)/snp_sp_action_cb:1748
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 11:49 AM
@Cisconew so you can ping between R1 and R4 if you remove the VPN configuration?
And the packet-tracer output above is when you add the VPN configuration back, which is still not working?
If so you need to troubleshoot why the VPN is not working.
What is the configuration on both ends?
Does ikev1/ikev2 sa establish?
Does IPSec SA establish?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 12:09 PM
@Cisconew so you can ping between R1 and R4 if you remove the VPN configuration?
- Yes, i was able to ping R1 &R4
And the packet-tracer output above is when you add the VPN configuration back, which is still not working?-Yes
If so you need to troubleshoot why the VPN is not working.
What is the configuration on both ends? - Attached as notepad
Does ikev1/ikev2 sa establish? -NO
Does IPSec SA establish?-NO
I have one doubt in encryption of IKEV2 Policies:
Router and ASA don't have same encryption options:
Router:(R2)
crypto ikev2 proposal PROP-SITE1
encryption aes-cbc-256
integrity sha1
group 14
ASA:
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 14
prf sha256
lifetime seconds 86400
R2#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
IPv6 Crypto ISAKMP SA
R2#sh crypto ipsec sa
interface: GigabitEthernet0/1
Crypto map tag: C-MAP, local addr 20.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.0.0.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.1.0.0/255.255.255.0/0/0)
current_peer 21.0.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 15, #recv errors 0
local crypto endpt.: 20.0.0.1, remote crypto endpt.: 21.0.0.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/1
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
R2#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 12:24 PM
Further, i have done ikev2 debugging.R2#debug crypto ikev2 error
IKEv2 error debugging is on
R2#
*Oct 18 19:20:39.715: IKEv2-ERROR:(SESSION ID = 1,SA ID = 1):: Received no proposal chosen notify
*Oct 18 19:20:39.717: IKEv2-ERROR:(SESSION ID = 1,SA ID = 1):Initial exchange failed: Initial exchange failed
R2#
*Oct 18 19:21:09.713: IKEv2-ERROR:(SESSION ID = 1,SA ID = 1):: Received no proposal chosen notify
*Oct 18 19:21:09.714: IKEv2-ERROR:(SESSION ID = 1,SA ID = 1):Initial exchange failed: Initial exchange failed
R2#
R2#
The results as below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 12:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 12:46 PM
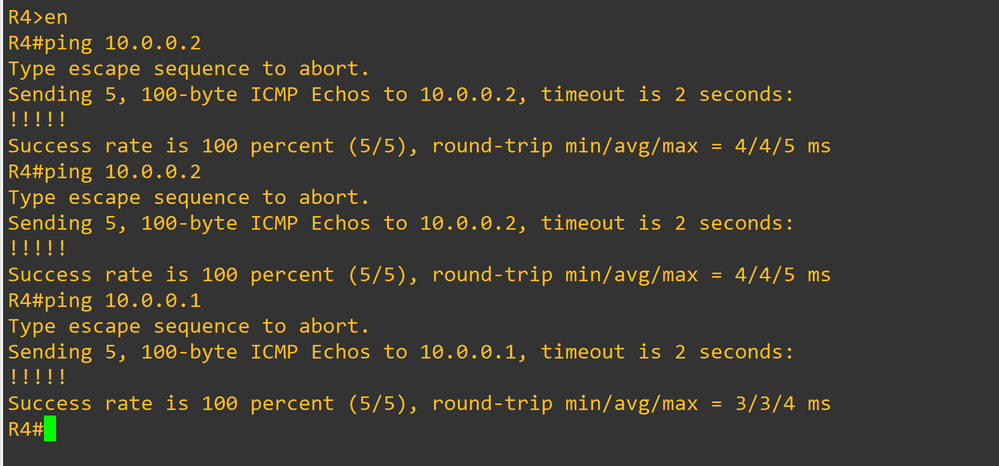
Thank you Rob Ingram!
It is working now.
R2#sh crypto ipsec sa
interface: GigabitEthernet0/1
Crypto map tag: C-MAP, local addr 20.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.0.0.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.1.0.0/255.255.255.0/0/0)
current_peer 21.0.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 20.0.0.1, remote crypto endpt.: 21.0.0.1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/1
current outbound spi: 0xE1ED2A16(3790416406)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xDCECF548(3706516808)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: C-MAP
sa timing: remaining key lifetime (k/sec): (4176233/3533)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2021 12:59 PM
Hi Rob,
One more doubt from same lab.
even though it is pinging, the packet tracer results shows as below:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (ipsec-spoof) IPSEC Spoof detected, Drop-location: frame 0x000055e6efbd5a3d flow (NA)/NA
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide