- Cisco Community
- Technology and Support
- Security
- Network Security
- FMC Default Logging and Default IPS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 09:22 PM - edited 02-21-2020 08:34 AM
Hi....I have a Firepower Management Center running 4110 in FTD. We are on version 6.2.3.4 on FMC.
I have about 50 Access Control Policy Rules...is there a way that I can turn on logging to the globally on all the ACP rules or do I have to go to each Access Control Policy and turn on each one.
The same goes for my IPS features. I have created an IPS policy but, do I need to go to each ACP rule and turn it on?
I see that there is a "Network and Analysis Intrusion Polices" where I can set my default network policy but, I did not see the policy I created
Thanks,
Dan
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 02:31 PM - edited 12-14-2018 02:32 PM
Hi Dan Hale,
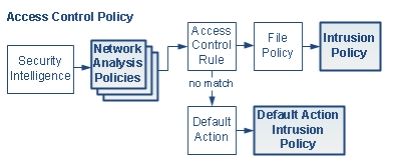
Network analysis and intrusion policies work together as part of the firepower intrusion detection and prevention feature.
Network analysis policy governs how traffic is decoded and preprocessed so that it can be further evaluated, especially for anomalous traffic that might signal an intrusion attempt.
An Intrusion policy uses intrusion and preprocessor rules (sometimes referred to collectively as intrusion rules) to examine the decoded packets for attacks based on patterns. Intrusion policies are paired with variable sets, which allow you to use named values to accurately reflect your network environment.
Below is the order of traffic analysis in an inline, intrusion prevention and advanced malware protection (AMP) deployment. It illustrates how the access control policy invokes other policies to examine traffic, and in which order those policies are invoked. The network analysis and intrusion policy selection phases are highlighted.
Thanks,
Abheesh
PS: Please don't forget to rate and select as validated answer if this answered your question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 11:08 PM - edited 12-13-2018 11:09 PM
Hi,
For logging and enabling IPS policy on ACP rules, you need to goto each and every rule to enable it. There is no global option for enabling.
For network analysis policy, go to Intrusion policy on top right corner you can see network analysis tab and click create a policy. Then goto ACP edit the policy Advanced setting select the Network analysis policy there.
Hope This Helps
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 08:57 AM
Thanks Abheesh,
So what is the real difference between the Network analysis policy and Intrusion Prevention Policy...I guess I thought they were the same.
Thanks,
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 10:03 AM
The Network Discovery policy relates to scanning the traffic and builds up
all the host profile intelligence attributes.
The Intrusion Policy relates to the Deep Packet Inspection for known
malware file signatures, vulnerability exploits etc. The IPS (SNORT) engine
provides the pass or block verdict.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 10:18 AM
As phil mentioned they are two different set of rules.
network discovery policy is a passive policy to gather the network information. however you must have to define a network discovery policy. by default its 0.0.0.0 and limit is 50,000.
IPS as phil mentioned.
you can also do a NAP for more specific network security to define your network parameter etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 02:31 PM - edited 12-14-2018 02:32 PM
Hi Dan Hale,
Network analysis and intrusion policies work together as part of the firepower intrusion detection and prevention feature.
Network analysis policy governs how traffic is decoded and preprocessed so that it can be further evaluated, especially for anomalous traffic that might signal an intrusion attempt.
An Intrusion policy uses intrusion and preprocessor rules (sometimes referred to collectively as intrusion rules) to examine the decoded packets for attacks based on patterns. Intrusion policies are paired with variable sets, which allow you to use named values to accurately reflect your network environment.
Below is the order of traffic analysis in an inline, intrusion prevention and advanced malware protection (AMP) deployment. It illustrates how the access control policy invokes other policies to examine traffic, and in which order those policies are invoked. The network analysis and intrusion policy selection phases are highlighted.
Thanks,
Abheesh
PS: Please don't forget to rate and select as validated answer if this answered your question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:02 PM
Looks like this thread has handled your Q.
Interested to know your use case for needing 50 rules in an ACL Policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2019 03:17 PM
Hi Evan,
I've worked on plenty of older firewalls PIX/ASA that have had far more then 50 ACL rules.
This particular firewall we converted from a Cisco ASA 5510. While we cleaned up the ACL's before we converted based on the ACL hitcounts there was ACL's still being used. Long term we will hopefully will clean up more that don't need to be used.
Thanks,
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 04:55 PM
Hi, I was referring to FIrepower ACL policy, not ASA.
Thanks for reply however.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2019 03:14 PM
Thank you everyone for the great info...cleared it up!
Thanks,
Dan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide