- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FMC - External Auth Using a Specific AD Group
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FMC - External Auth Using a Specific AD Group
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 01:37 PM
Hello All,
FMC v7.0.5
Very new to Firepower (*coming from ASA) and I'm setting up an External Auth using a MS Active Directory. Following a guide on youtube, I configured the LDAP server in order to allow a specific group in our AD to login to the FMC GUI. However, it's "sort of" working.
I'll post the configuration below... And a screenshot.
Firstly, just to confirm, I am able to login with my AD user (*BTW, my user is basically a global administrator user account). My user is also a member of this "Network Admins" group I created, along with a few other admins in the company. So, just to test that it was allowing me to login because I was in the Network Admins group, and not because my user is an Administrator user in AD, I created a test user in AD and put that regular user into the Network Admins group. However, this test user fails to login and fails the "Test" option during setup.
Primary Server: <primary-server-ip>
Port: 389
Secondary Server: <secondary-server-ip>
Port: 389
Base DN: dc=acme,dc=com
Base Filter: empty (*not sure if maybe this is what's missing...?)
User Name: <AD-main-admin-user>@acme.com
Password: ***********
Encryption: None
UI Access Attribute: sAMAccountName
CLI Access Attribute: sAMAccountName
Group Controlled Access Roles:
Administrator: CN=Network Admins,CN=Users,DC=acme,DC=com
*Copy and pasted the above from the Attribute Editor tab in AD for this group's "distinguished name"...
Group Member Attribute: member (*this is what they said to put in the guide I watched...)
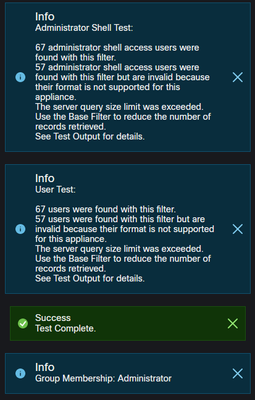
When I enter the test username and password I created into the Additional Test Parameters section and click the Test button, I get the following:
When I enter MY username and password here and click Test, I get:
Both my user and the test user I created are in the "Network Admins" group I put in the "Administrator" field under Group Controlled Access Roles, shown in the config above and attached.
Any help would be greatly appreciated!
Thanks in Advance,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 05:12 AM - edited 06-24-2023 05:13 AM
Based on the provided configuration, here are a few things to check and consider:
1. Base DN: Ensure that the Base DN is correctly set to the distinguished name of your Active Directory domain. In the given example, it is set to "dc=acme,dc=com," which should match your Active Directory structure.
2. Base Filter: The Base Filter field is left empty in your configuration. Normally, this field is used to specify additional filtering criteria if needed. If you don't require any additional filtering, leaving it empty should be fine.
3. Group Member Attribute: The Group Member Attribute is set to "member" in your configuration, which is the correct attribute for member-distinguished names in Active Directory.
4. Group Controlled Access Roles: Make sure the distinguished name (DN) for the "Network Admins" group is correct. You mentioned copying it from the Attribute Editor tab in AD, so ensure it matches the exact DN of the group.
5. Encryption: Currently, you have "None" selected for encryption. Depending on your security requirements and Active Directory configuration, you may want to consider using SSL/TLS encryption for secure communication between the FMC and Active Directory.
When testing the additional test parameters with the test username and password, ensure that the username and password are correctly entered. Double-check for any typos or misspellings.
If the test user continues to fail authentication and the test, it's important to verify that the test user has the necessary permissions and is a member of the "Network Admins" group in Active Directory. Additionally, check the logs on the Active Directory server and the FMC for any error messages or authentication-related issues that may provide more insights into the problem.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide