- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FMC FTD RA VPN Attribute Maps User in Multiple Groups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FMC FTD RA VPN Attribute Maps User in Multiple Groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2023 01:33 PM
Cisco Community,
[This is a duplicate post - I tried to re-post the original discussion, moving it from (VPN) to (Network Security) but...]
We have an FMC managing a set of FTD's serving as RA VPN concentrators. We are using LDAP Attribute Maps to apply policy to each user's Anyconnect VPN connection based on AD group MemberOf. Everything is good except we came across a situation where a user is now a MemberOf two different AD groups. Looking to solve the issue where this user's (and potentially others) VPN Group Policy will match more than one because of recent dual AD Group membership and the desired VPN GP is the one with less restrictive policy. One solution is removing the user from one of the AD Groups but this will not be possible in certain scenarios due to automated backend processes.
A main question is: Which VPN Group Policy will be applied to a User that matches two AD Groups in the LDAP Attribute Map?
A follow up question is: Under the Realm's LDAP Attribute Map, can we adjust the order of the LDAP Attribute Value Maps from Top - Down so that there is a hierarchical first match of the preferred VPN Group Policy for a User with dual membership?
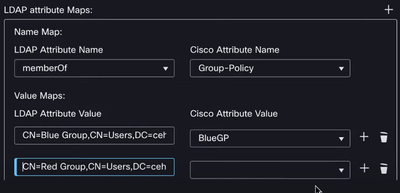
For example:
Let's say User-A is member of the top LDAP Attribute Map: IT-Operator --> Group Policy = IT-O (more restrictive) and is now also member of 2nd in line LDAP Attribute Map: IT-Superuser --> Group Policy = IT-S (less restrictive). If we switch the IT-Superuser to the be 1st in line, will User-A get this policy instead of the IT-Operator policy when they establish a RA VPN connection?
(using this image to illustrate - swapping Blue & Red so that Red is 1st in line)
FMC & FTD's are on 7.2.5.
P.S.
Hope it's OK, tagging some of the senior community members on this:
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2023 05:42 AM
If you move the IT-S Attribute Map to the top of the list, it should match first so that any user that is a member of that group will be assigned the privileges associated with that map. The matching is in a top down fashion.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2023 09:23 PM
Marius, thanks for the feedback! I reconfigured Attribute Maps in a top down fashion and it did not result in a first match as I hoped.
Testing showed that a group policy which was third in line from the top was applied to the user although the user was a memberOf the first/top group.
I cleared and rebuilt the configuration, leaving only the top attribute map and there was a match to the desired GP. However when I reintroduced the other LDAP Attribute Maps, the same authenticated user was mapped to the third GP again.
**BTW, someone (tvotna) provide some great information on the original post (in the VPN section) and mentioned a bug on ASA SW that specifically produces this undesirable behavior. I've heard 3 different sources confirm that it is supposed to be a top-down selection but it is not working.
DAP is mentioned as a workaround but not sure how to execute this.
Any intuitive support for a DAP newbie will be appreciated!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2023 07:33 AM
I think you can do that via AD not by arrange map in FMC.
Check link that include example same as your requirements.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2023 09:29 PM
Thanks MHM,
This is the guide I used to confirm that the LDAP Attribute Maps were built correctly, using the memberOf Attribute map.
The issue is that some users are going to have multi-group correlations.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide