- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FMC/FTD Snort Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FMC/FTD Snort Question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2021 12:17 PM
Hi
So received this info from and am wondering how I check we have received these on our FMC devices.???
Cisco Talos has released the following Snort SIDs to detect exploitation attempts targeting CVE-2021-44228: 58722 - 58739 and 300055 - 300057.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2021 04:40 PM
Hi,
in fmc go to Policies>Intrucion>"the policie that you have applied to your devices">rules, and in the filter put "Apache Log4j"
you will see all the "SID" from 58722 to 58739, and in the action you should see "a red x" thats mean "Drop and Generate Events"
From the range 300055 - 300057im not shure if its rigth or apply to FMC i cannot see any rule in that range maybe is only 2 0 instade of 3...
| 30057 | MALWARE-CNC Win.Trojan.Peronspy outbound system information disclosure |
| 30055 | MALWARE-CNC Win.Trojan.Deventiz CWD system information disclosure via FTP |
also maybe its obvius but you have to have internet acces in order to download the rule Update. i have
I hope it helps you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2021 12:12 AM
Hi Rafael,
Do you have info on how to make a report on this matter, so this info can be highlighted to the business.
Thanks
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2021 10:30 AM
Hi the easy way that i know is,
if you can see the event under the tab of "analysis" for example on Analisis>Intrusion>events> if you see any triggered ips firm you can click on the button "Report designer" and customise your report or you can play with the field of the filter serch, for example the field called "message" on the ips events
also this is a vulnerability and it will be used by an exploit or ransomware or so, for example conty is a ransomware that are using this vulnerability and as ransomware you will see in malware events, or file policies, and as the Leyend Marvin say if it is encrypted and you cannot unencript the trafic it will never trigger an event in the FMC(and you need a proper configuration of filepolicy and also malware protection license).
Also some version of FTD are vulnerables and other cisco devices so please take a look on this security advisor from Cisco
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-apache-log4j-qRuKNEbd
and a little meme for smile :3
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2021 12:04 PM
Hi Rafael,
Thanks for a great reply here..
So just to get one thing clarified.... You wrote :
also this is a vulnerability and it will be used by an exploit or ransomware or so, for example conty is a ransomware that are using this vulnerability and as ransomware you will see in malware events, or file policies, and as the Leyend Marvin say if it is encrypted and you cannot unencrypt the traffic it will never trigger an event in the FMC(and you need a proper configuration of filepolicy and also malware protection license).
Will this mean that traffic will not be detected by the FTD/FMC?? The reason why I am asking is that we can see that our FMC/FTD are not detecting any of the CVE for log4j, even do that snort2 is fully updated and should prevent this. But our MS Sentinel is telling us that we are been hit by it.... The IP we can see that are been used are also been noticed on github : Log4j IP Block List
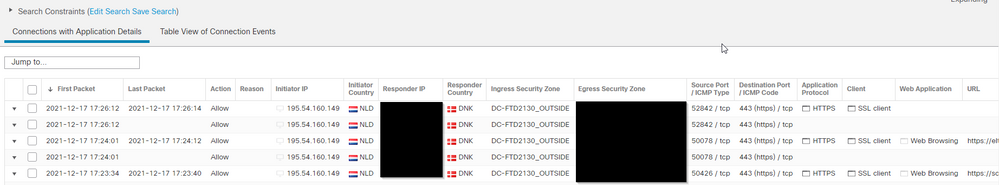
But my FMC just see these event as legal :
Can this be because it encrypted or, are we looking to something else here?
The IP are blocked now, but I would expect that our IPS and snort2 would block this? My FTD are running with AMP, Malware licens etc. so that should be OK.
So are we looking at FTD/FMC doing it wrong, or is this wrong info in Sentinel?
Frank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2021 05:56 PM
@Frank Osberg do your ACP Security Intelligence settings include the TALOS IP blacklist items?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2021 11:29 PM
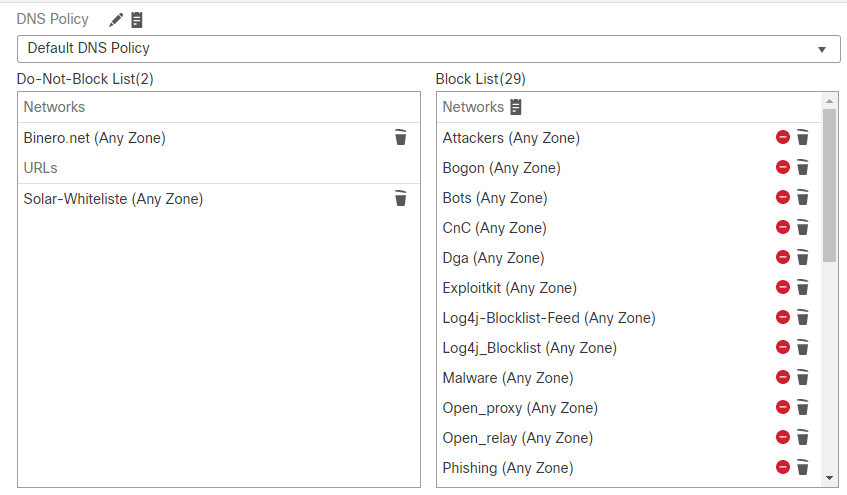
Where in my ACP should I see this? I have some in Security Intelligence today, but this might be missing
In my Object section:
But is there missing something here?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2021 04:26 AM
You would not see the blocks as intrusion events as I had noted unless the traffic is unencrypted (or decrypted and resigned via SSL policy). But if the SI categories you show are in your ACP you should get IP blocks as a result.
If a specific set of addresses seems to be missed then I would suggest raising a TAC case and they can refer it to TALOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 10:41 PM
Hi Rafael,
Is by updating the snort rule in the rule update will mitigate the vulnerability since i couldnt find any other resolution officially announce by cisco.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 11:07 PM
The Snort rule will block traffic transiting the firewall that matches the vulnerability - if it can be seen. If, for example, the traffic is encapsulated in an undecrypted TLS flow (for example, over https) it won't be seen and thus cannot be blocked.
Note also that the rule also only applies to traffic through the firewall. As of the time of this writing, Cisco is still evaluating the firewall software itself as to the impact of the Log4j vulnerability.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 12:15 AM
Hi Marvin,
Thanks for the explanation, so best case scenario for now is to only update the snort rule to latest once released since cisco is still evaluating the vulnerability.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide