- Cisco Community
- Technology and Support
- Security
- Network Security
- FPR1010 Port Forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 03:43 AM
Hi Guys,
Again new to the FirePower software, but been using the ASDM for years.
I am having trouble getting my head around the NAT setup.
Simply, let us say I have a web server (for test, it is actually a Fluke analyser) listening on port 80 on the inside of the network, with lets say IP=192.168.0.1
I need to map all requests arriving at port 8080 on the outside, with lets say IP=1.2.3.4 to that internal server.
For this deployment, I am trying to reduce the number of public IPs, and use only the external interface, single IP.
I seem to have tried every combination using FDM but as yet no joy.
I am port scanning the outside interface, and can see the https port open (which is providing FDM) but no other open ports. So, port 8080 as above doesn't seem to be mapped.
For testing, I have a cheeky 'allow all' rule in the Access Control screen - so the ACL shouldn't be coming in to play.
Source and destination are somewhat confusing terms... is this viewed as the internal device being the source? In my case, traffic will always be initiated from the outside.
Any help with this would be much appreciated!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 07:26 AM
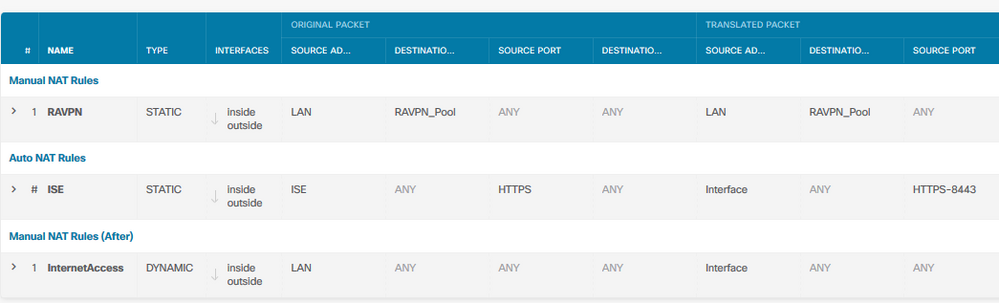
Right, so your Manual NAT rules need to be moved to the "after" section as per my example below.
When you create the rules select placement "After auto NAT rules".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 04:36 AM
Hi,
The NAT rule looks ok to me. Do you have a dynamic Manual NAT rule for outbound internet access above this Auto NAT rule? If so this is probably conflicting with your new rule. You would need to ensure your rule for Fluke is above the other rule
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 07:11 AM
Hi Rob,
I have the default rules that the device comes with, followed by my new rule as Auto NAT.
It does strike me as odd that each port seems to have its own dynamic NAT entry. I expected it to be more like ASA where the BVI group 'inside' usually has just one PAT entry as a sort of fall back for if no other rules apply. It doesn't seem to let me use the group 'inside' only specific named interfaces.
I didn't create those rules - should they be present?
I obviously need at least one, to do the dynamic PAT for any inside 'clients'. In my trivial config, I have a laptop in port 7 and my Fluke tester providing a web server in port 6. In production I will probably just use port 3 to link to a switch and therefore as far as the FPR sees it, everything will come from ge3.
Picture of NAT rules attached.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 07:26 AM
Right, so your Manual NAT rules need to be moved to the "after" section as per my example below.
When you create the rules select placement "After auto NAT rules".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 08:14 AM
Right... I have deleted all the built-in rules, and then added a new dynamic one right at the end.
I have had to assign the rule to a specific port, in my case the dynamic rule for internet access had to be assigned port 7 (in to which my laptop is plugged).
I had to assign the static NAT rule to port 6, in to which my Fluke analyser is plugged.
As soon as I did that, we have success!
I think the thing that has tripped me up here, is it appears you have to be specific as to the physical port.
With the ASAs I have used for years, it appears you can assign rules to inside or outside interfaces even though those may actually be groups of physical interfaces.
FDM won't let me select 'inside' as an interface, only the individual ports that make that up... That may come to be a problem as I did want to have an 'outside' group and have backup WAN connections available... I will come to that later.
I think we are there... I will tidy up my rules, do a screen print, update this post so it can be found as a reference for others, and mark this as the accepted solution.
Thanks for your help on this one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2020 12:37 PM
First sign of madness, replying to your own postings...
As mentioned above it was the order of NAT statements. No idea why the default setup gives rules that you apparently can't place your own rules in front of. You can't change the position before/after once the rule is created.
Also, as mentioned, the interface needs to be explicitly defined eg. inside_6 if you are plugged in to port 6. In ASA days, I believe you could simply specify 'inside' if the physical interfaces were part of a BVI group.
So, in case it helps others, please find attached some screen prints of a working setup.
First we have the NAT screen showing the order of statements... our special rule must be before the general 'internet' PAT rule.
Note in this special case, that ports 6 and 7 are used... This is simply as my 'lab' setup didn't have a separate switch so I was using the individual ports on the FPR1010. In the more general case these will probably both be inside_2 which then connect to a switch.
Second screen print shows the correct configuration for the NAT rule. Note (in my opinion) source and destination are confusing... Source is the inside, which in my case contains the Fluke analyser (web server).... in my view that isn't really the source as requests actually come in from the outside. No matter once you get your head around it.
For reference, the third print shows a sample Access Rule, that then allows the mapped traffic to flow.
I hope this helps someone in the future, and thanks again to Rob for leading me to this solution.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide