- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Hairpin NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2013 08:50 AM - edited 03-11-2019 07:08 PM
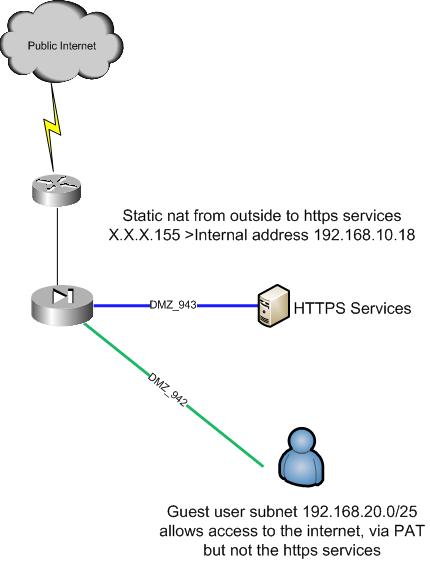
Hi all I’m having a problem getting hairpin nat to work on my ASA5524X Code 8.6
I have some services sitting in DMZ_943 these are https services and are accessible from outside the network on a public ip address x.x.x.155 all works fine.
We have a set of guest internet access clients sitting in another DMZ_942 and can access the internet fine, however when these clients need to access the HTTPS server on the public address x.x.x.155 it fails.
Both DMZ are connected to the same ASA
Does anyone know what the correct HAIRPIN NAT statement would be for this?
Other post have suggested the following:
nat (ouside,ouside)
or
nat (inside,inside) source dynamic interface destination static PUBLICIP INTERNAL_WEB_SERVER
Should it b:
nat (dmz_942,dmz_943)…………..?
Cheers
Paul
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2013 09:00 AM
Hi,
You wouldnt be doing Hairpin NAT as the hosts are behind different interfaces. Hairpin NAT would be when both hosts were behind the same interface.
To me it would seem that you simply need to NAT the DMZ_943 server towards the DMZ_942 interface with the public IP address.
Naturally what you have to take into consideration is that if you have some hosts on the DMZ_942 that HAVE TO HAVE access to the server with its real IP address then the above NAT configuration suggestion wouldnt work. In that case you might have to resort to a Static Policy NAT configuration in the new software NAT format.
If you are configuring the Static NAT for the DMZ server with a simple Network Object NAT like below then it would be easy to do it for the other interfaces too
Static NAT for DMZ -> WAN
object network SERVER
host x.x.x.x
nat (DMZ_943,outside) static x.x.x.115
Static NAT for DMZ -> DMZ
object network SERVER-TO-DMZ_942
host x.x.x.x
nat (DMZ_943,DMZ_942) static x.x.x.115
I am not sure how big your current configuration is but probably the easiest way to determine the correct NAT configuration for you would be to see the current configuration
Hope this helps
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2013 09:47 AM
Hi Jouni - thanks for your reply.
All the clients will need to access the server via it's public URL and IP this is because it's tied in with the SSL certificate and chain.
I assumed I would need hairpin NAT because the connections are going out to the internet resolving for DNS and then returning back in the same interface (outside) thus requiring the command same-security-traffic permit intra-interface, and a matching U-turn NAT statement?
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2013 09:56 AM
Hi,
You cant configure the ASA to act so that a connection would first go out its "outside" interface and then enter the "outside" interface.
What you would simply need to do is NAT the DMZ server towards the other DMZ interface to its public IP address just like you have done towards the "outside" currently.
If the ACL rules permit the traffic then the connections should work just fine.
Without seeing the current configuration I naturally cant give you an exact answer on what the NAT configurations should look like.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2013 06:27 AM
Hi Jouni
Thanks again for your reply.
The following twice NAT got it working:
nat (dmz99,any) source static NET_DMZ99 NET_DMZ99 destination static PUBLICIP_19x.x.x.156 MAIL_INTERFACE service HTTPS HTTPS
Thanks
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


