- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: How to restrict access to FTD management interface.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to restrict access to FTD management interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 09:12 AM
Hi,
I am trying to restrict SSH access to the management interface of the FTD device.
Can someone share the correct procedure?
Platform settings apply only to the data interfaces and the management interface is still accessible.
I tried applying ssh access list from CLISH but that did not work either and the device is still accessible from any IP.
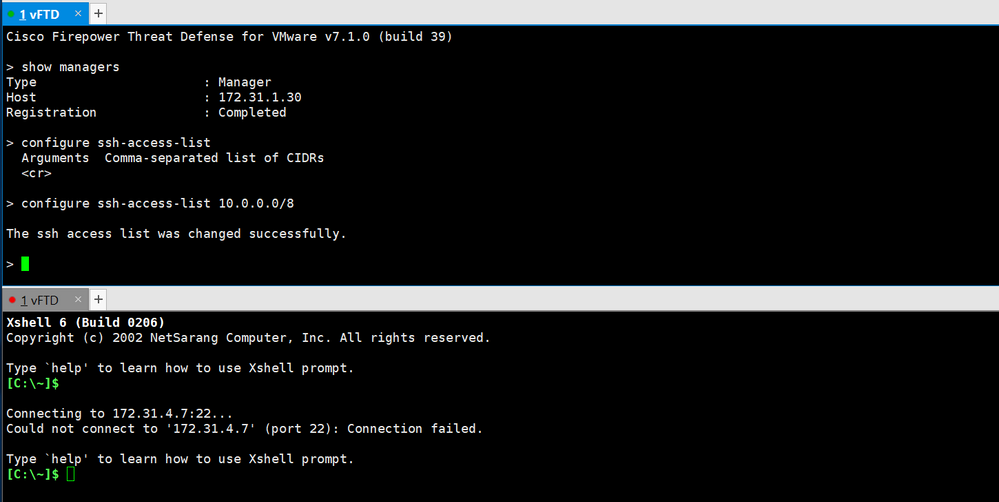
> configure ssh-access-list 10.0.0.0/8
We are running FXOS version 6.7 on FTD 2110 managed by FMC on version 7.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 10:36 AM
That's the proper command. There was a bug with it back in 6.2.x but that should be fixed on 6.7 and 7.0
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCve55973/?rfs=iqvred
I tested it on my device and it appears to work as expected (prevented me from accessing the device from a non-10.0.0.0/8 address):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 12:27 PM - edited 09-21-2021 12:30 PM
Hi Marvin,
Thank you for your reply.
I just did some more checks and can see that my ACL is applied. However, I have two permit any any statements at the beginning and the end of ACL. Please see redacted entries below.
show ssh-access-list
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
ACCEPT tcp -- ---- anywhere state NEW tcp dpt:ssh
ACCEPT tcp -- --- anywhere state NEW tcp dpt:ssh
ACCEPT tcp -- --- anywhere state NEW tcp dpt:ssh
ACCEPT tcp -- ---- anywhere state NEW tcp dpt:ssh
ACCEPT tcp anywhere anywhere state NEW tcp dpt:ssh
How can I modify it to get rid of the any any statements?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 01:03 PM - edited 09-21-2021 01:03 PM
You should be able to enter a replacement with just the networks you want:
configure ssh-access-list <entry_1>,<entry_2>,<entry_n>
That will replace the existing entries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 02:37 PM
I configured acl in the format
Configure ssh-access-list 10.1.1.0/24,10.2.0.0/24,172.16.0.0/16
Unfortunately, permit any any entries are still retained.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2021 05:38 AM
I tested on my system it worked as I described. See my output below:
> configure ssh-access-list 10.0.0.0/8 The ssh access list was changed successfully. > show ssh-access-list ACCEPT tcp -- 10.0.0.0/8 anywhere state NEW tcp dpt:ssh > > configure ssh-access-list 10.0.0.0/8,172.16.0.0/12 The ssh access list was changed successfully. > show ssh-access-list ACCEPT tcp -- 10.0.0.0/8 anywhere state NEW tcp dpt:ssh ACCEPT tcp -- 172.16.0.0/12 anywhere state NEW tcp dpt:ssh > > configure ssh-access-list 172.16.0.0/12 The ssh access list was changed successfully. > show ssh-access-list ACCEPT tcp -- 172.16.0.0/12 anywhere state NEW tcp dpt:ssh >
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2021 05:47 AM - edited 09-22-2021 05:48 AM
Thanks, Marvin
It does not work for me in production.
It works fine in the lab but I am using a different version there.
When I configure ACL it does not remove entries but just duplicates them and add to the bottom of the ACL
Another thing is I cannot even disable ssh access completely.
After issuing configure disable-ssh-access access is still there and ACL is not being removed.
It disappears from the config and ssh access is restricted as expected when I test in LAB.
I must be hitting some bug and will raise that with cisco.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2021 02:34 AM
Hi,
I thought I will share the update for anyone who has the same issue.
Basically, we were hitting the below bug.
CSCvx71156 - access list is not working on 6.7
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvx71156
Cisco TAC came up with a workaround involving logging in to expert mode, a manual edition of iptables and iptables service restart afterwards.
This fixed the problem and we were able to restrict access as required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2021 11:43 AM
Thanks for the update - I hadn't encountered that bug before.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide