- Cisco Community
- Technology and Support
- Security
- Network Security
- Integrating FMC with ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 05:25 AM - edited 02-21-2020 07:27 AM
Hi;
I have a test lab and want to integrate FMC 6.2.2.81 with ISE 2.2 (patch 5). Also I have an Internal MS CA server and have imported the CA root certificate into ISE and FMC already.
Now I want to generate CSR of FMC to get a FMC Server Certificate from my internal CA server. There is no option to do it on FMC web GUI and I searched the Internet to see how it is and found very strange posts explaining complex procedures, like obtaining an open source software (OpenSSL) and generating CSR with it..!!
I don't understand while we are able to create CSR for ISE just by using its GUI, why there is no such basic thing on a FMC? Isn't it weird?
I didn't managed to find any simple guide explaining how to use OpenSSL to generate CSR, and actually I'm not sure if I need to dig into OpenSSL documents, Linux, etc to find just bunch of commands to generate a simple CSR!!
I will appreciate any help on this. because I don't know where to start and basically if it is needed or if there are other reasonable and simpler ways to do that. Again I don't know why Cisco has not implemented such basic thing on its "Next Generation" devices, as it did on ISE?! confused!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2018 08:00 AM
WebGUI location: Objects > PKI > Trusted CAs > Internal Certs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 05:35 AM
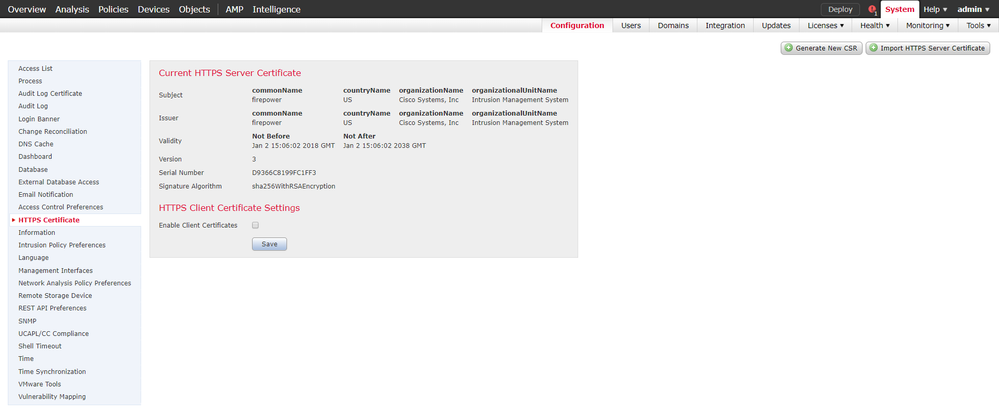
You can generate a CSR via the web gui. Look at the top right corner of the picture below:
I also use a GUI based tool called xca (opensource) that does a bunch of certificate operations in a simplified way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 04:34 PM
Hi.
Do I need to create a HTTPS CSR, as you said, for pxgrid?
I found a doc which said we need to establish SSH to the FMC and use openssl to generate private key and csr. If this was the case, what should be set as DN or Common Name for the csr? I don't think using the hostname of the FMC as DN was correct. I created a realm and the directory and was able to download the users and groups onto FMC. I'm a little bit confused on this and not sure if this means joining FMC to the domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 11:06 AM
This Cisco doc has instructions on how to create a CSR using openssl or without using a CSR. The doc is for signing the certificate using the Internal ISE 2.2 CA, but if you use the openssl method you can just sign this using an external CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 04:55 PM
Thanks for your reply @Rob Ingram.
Would you clarify me on the second part of the question? I've created realm and directory on FMC and downloaded users and groups from AD onto it. Is it the same as joining it to the domain? If not, what should be written as Common Name (DN) for the FMC while generating a csr?
regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2018 10:04 AM
I've have configured FMC/ISE pxgrid integration though. You would need to create a CSR if you are using pxgrid to exchange user/ip and SGT bindings from ISE to FMC. pxgrid could be used if you wish to quarantine an endpoint, by sending a CoA from ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2018 04:03 PM
I found this document in which it explained the procedure. Assuming that the pxGrid client is FMC in this document, I started to enter commands on FMC CLI but it needed root CA certificate name to generate CSR. I had uploaded root CA certificate before through FMC GUI: Object Management > PKI > Trusted CAs, but this command didn't accept its name with the following warming:
admin@firepower:~$ openssl pkcs12 -export -out firepower.p12 -inkey firepower.key -in pxGridClient.csr -chain -CAfile xinmix-root-ca-certificate.cer unable to load certificates
There is no such file on FMC:
admin@firepower:~$ dir firepower.key firepower.p12 pxGridClient.csr
any idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2018 03:44 AM
openssl genrsa -out fmc.key 2048
openssl req -new -key fmc.key -out fmc.csr
- Copy those files (fmc.key and fmc.csr) off the FMC
- Sign the CSR request from Internal CA
- Download the Root Cert and Intermediate Root (if you have one)
- Upload the Root + Int Root to FMC
- Upload the signed certificate
- Complete the ISE configuration and test
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2018 05:05 AM
dHi.
I found This document on Cisco communities and started to follow the procedures as mentioned, but I stuck where we should use "openssl" command on FMC to generate pkcs12 package. It needs root CA's certificate name which I was unable to find a way to copy it onto FMC. This is what I got:
admin@firepower:~$ openssl pkcs12 -export -out firepower.p12 -inkey firepower.key -in pxGridClient.csr -chain -CAfile xinmix-root-ca-certificate.cer unable to load certificates
So; how I can upload my root CA certificate onto FMC with CLI? I read on cisco site that CLI access is restricted. so is there any way?
From Cisco website:
"You cannot use the CLI on the Firepower Management Center. The Firepower Management Center supports Linux shell access, and only under Cisco Technical Assistance Center (TAC) supervision."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2018 08:00 AM
WebGUI location: Objects > PKI > Trusted CAs > Internal Certs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2018 05:16 AM
@Rob Ingram wrote:
Those 2 commands I previously gave you to create a private key and csr are the only commands you need to run on the cli. The import of the Root certs aswell as the signed cert will be done on the WebGUI.
WebGUI location: Objects > PKI > Trusted CAs > Internal Certs
Hi;
Thank you. I managed to copy certificates onto FMC and run "openssl" and get a certificate from my internal CA server for FMC.
But now I stuck at the next step, where I created Realm on FMC and managed to download user and groups onto it. then on ISE 2.2 patch 5, I created a separate CSR and signed it with certificate template created specially for pxgrid integration and after getting that certificate on ISE and bound it to CSR with "pxgrid"usage (not as "admin"usage, because I have another certificate for admin usage and don't want to replace that one). Finally I got back to FMC and on System > Integration > Identity Sources page, i got this logs stating that connection to Primary Host has Failed:
Primary host: test: ISE connection. Preparing ISE Connection objects... Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: pxgrid connection init done successfully Preparing subscription objects... Connecting to ISE server... Beginning to connect to ISE server... Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: _reconnection_thread starts Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: connecting to host 10.1.204.168 ....... Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: stream opened Starting SSL Handshake, SSL state:before/connect initialization Completed SSL Handshake, SSL state: SSL negotiation finished successfully Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: EXTERNAL authentication complete Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: authenticated successfully (sasl mechanism: EXTERNAL) Captured Jabberwerx log:2018-03-08T12:42:26 [ INFO]: pxgrid_connection_connect: Connected. host=10.1.204.168 Captured Jabberwerx log:2018-03-08T12:42:27 [ INFO]: Controller version: 1.0.4.20 Captured Jabberwerx log:2018-03-08T12:42:27 [ INFO]: Account pending ...timed out trying to form connection to ISE server. Unable to connect to ISE server at host: '10.1.204.168'. disconnecting pxgrid Connection to ISE server failed because of time out
I think it has something to do with certificates. what did I do wrong?
Besides, ISE and FMC can ping each others IP address and FQDN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2018 05:50 AM
From this error message above I would guess you need to approve the FMC account in ISE. Go to Administration > pxGrid Services > Clients locate the FMC and select "Approve". You could also go to Administration > pxGrid Services > Settings and automatically approve new accounts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2018 06:54 AM
@Rob Ingram wrote:
"Captured Jabberwerx log:2018-03-08T12:42:27 [ INFO]: Account pending"
From this error message above I would guess you need to approve the FMC account in ISE. Go to Administration > pxGrid Services > Clients locate the FMC and select "Approve". You could also go to Administration > pxGrid Services > Settings and automatically approve new accounts.
You really rock. It worked. Thank you for your time :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2018 03:00 AM
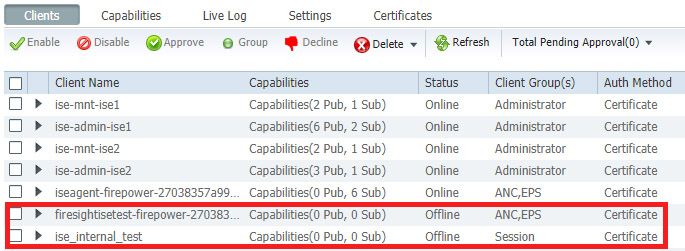
Under "Status" title it shows "Offline" for FMC. Is it normal or I should change them to be online manually?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2018 04:35 AM
I believed the ise_internal_test should always remain "Online" as long as connectivity between FMC and ISE exists.
For testing, on the FMC confirm you can see user/host information sent from ISE. You could also go back to the ISE integration page on FMC and hit test again to confirm it can still communicate with ISE.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide