- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Intrusion Events
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2022 09:55 AM
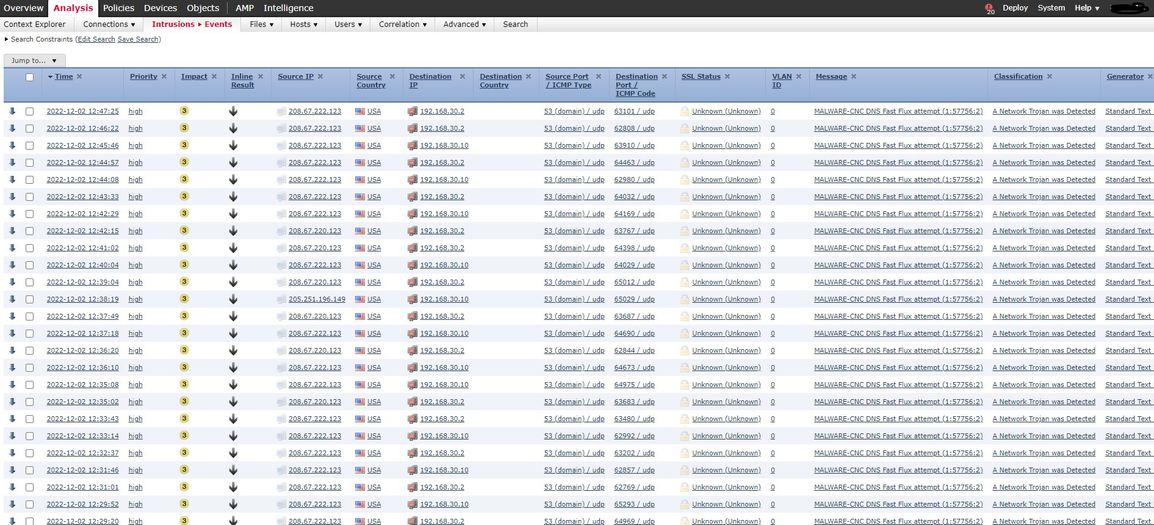
Hey all I am getting intrusion events as shown in the below screenshot. These are known DNS servers and trusted. Can anyone tell me what is going on here and how I should try to remediate this??? I am at a loss
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 04:34 AM
Rather than disable the rule altogether, I would suggest whitelisting the Umbrella public DNS servers that are seen in the events you are showing. I highly doubt Umbrella is sending intrusion attempts into the private network via DNS replies. Instead, it is probably triggered by one of the fields in the DNS responses (such as TTL) having a low value for legitimate reasons.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2022 09:24 PM
SID - 57756 - MALWARE-CNC DNS Fast Flux attempt
alert udp $EXTERNAL_NET 53 -> $HOME_NET any (msg:"MALWARE-CNC DNS Fast Flux attempt"; flow:to_client; content:"|00 01|"; depth:2; offset:4; byte_test:2,>,1,0,relative; byte_test:1,=,1,2,bitmask 0x80; content:"|00 01 00 01|"; distance:6; content:"|00 01 00 01 00 00 00 05|"; distance:0; metadata:policy max-detect-ips drop, service dns; reference:url,attack.mitre.org/techniques/T1568/001/; classtype:trojan-activity; sid:57756; rev:2; gid:1; )
After reviewing the syntax and the connection events that you attached, the traffic does match the rule.
To remediate this, the intrusion rule (with SID 57756) needs to be disabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 04:34 AM
Rather than disable the rule altogether, I would suggest whitelisting the Umbrella public DNS servers that are seen in the events you are showing. I highly doubt Umbrella is sending intrusion attempts into the private network via DNS replies. Instead, it is probably triggered by one of the fields in the DNS responses (such as TTL) having a low value for legitimate reasons.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide