- Cisco Community
- Technology and Support
- Security
- Network Security
- NAT Translation in Cisco FMC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 08:35 AM
Hello all,
I'm using cisco FMC 4600 to manage FTD cluster and I need to get NAT statistics and events. As which internal IPs have been translated to a certain NAT IP address.
Is there a way to do that in FMC?
Thank you,
Hadeel
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 12:49 AM
as @Marvin Rhoads mentioned employing the Secure Network Analytics but not everyone can have Netflow tool in place. but to give you some visibility from FMC and see the connection events you can go to "Analysis"-->"Unified-Events" this will bring you the live connection feed what FMC receving from the FTD. on the search bar you can put in your FTD name and it will filter all the connection passing through from your firewall. here you can filter/fine tune what you want to see.
again as said it will not give you exctaly what you looking for but it will give you some insight of the connection. or the otherway you can do it from "Analysis"---"Connection-Event"--->"Edit-Search"-->Connection-Event-->Device(here you put your device name) and it will display the history of connection event. Also here agian you can right click one of the tab and narrow down what you want to see.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 01:54 AM
Definitely look at Unified Events. I had forgotten we can select the NAT IP (Source or destination) from among the displayed columns - it's not enabled by default but can be added. You can then drag the column to be next to the original source IP (among other customizations). Once you have a filtered view that suits you you can even download the events as a csv. See the following screen shot:
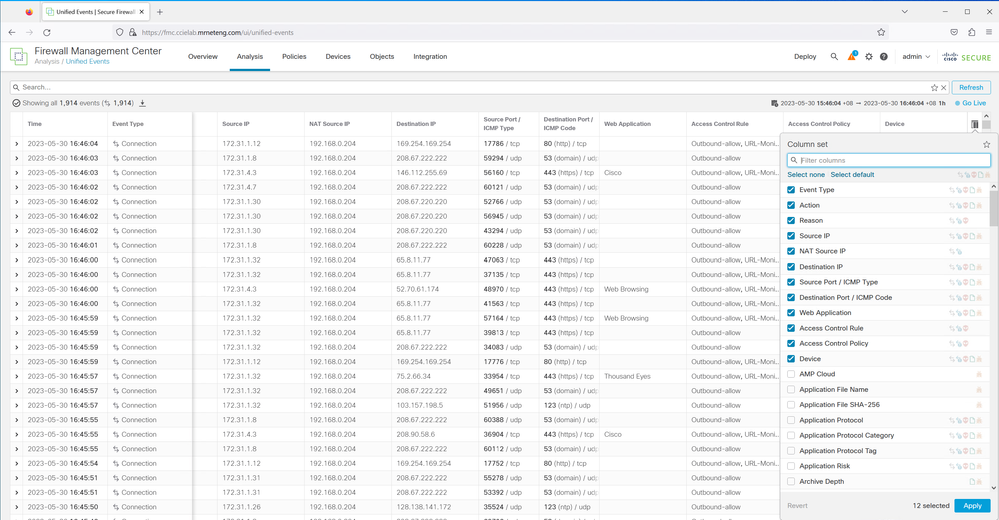
The only downside is that you are limited to the FMC's event storage capacity. Depending on your FMC and how many events it is logging that can be as little as less than 1 day. You can see the capacity in the Health Monitor as shown below - my lab FMCv has 19 days capacity but it is very lightly used.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 09:47 AM
Unfortunately that information is not stored within FMC. It can be retrieved in real time from the cluster members using "show xlate".
If that information is required for forensic or historical purposes, the only way I know to get it is to setup Netflow export to a collector (Such as Cisco Secure Network Analytics, formerly known as Stealthwatch). Cisco firewalls use NSEL (Netflow Secure event Logging) which captures both the original and translated address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 09:50 AM
Thank you so much @Marvin Rhoads .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 12:49 AM
as @Marvin Rhoads mentioned employing the Secure Network Analytics but not everyone can have Netflow tool in place. but to give you some visibility from FMC and see the connection events you can go to "Analysis"-->"Unified-Events" this will bring you the live connection feed what FMC receving from the FTD. on the search bar you can put in your FTD name and it will filter all the connection passing through from your firewall. here you can filter/fine tune what you want to see.
again as said it will not give you exctaly what you looking for but it will give you some insight of the connection. or the otherway you can do it from "Analysis"---"Connection-Event"--->"Edit-Search"-->Connection-Event-->Device(here you put your device name) and it will display the history of connection event. Also here agian you can right click one of the tab and narrow down what you want to see.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 01:54 AM
Definitely look at Unified Events. I had forgotten we can select the NAT IP (Source or destination) from among the displayed columns - it's not enabled by default but can be added. You can then drag the column to be next to the original source IP (among other customizations). Once you have a filtered view that suits you you can even download the events as a csv. See the following screen shot:

The only downside is that you are limited to the FMC's event storage capacity. Depending on your FMC and how many events it is logging that can be as little as less than 1 day. You can see the capacity in the Health Monitor as shown below - my lab FMCv has 19 days capacity but it is very lightly used.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 02:02 AM
@Marvin Rhoads exactly, this is what I used in production network. Stealthwatch pricing was quite high and we were not able to match it so yes, this is what I am doing/using this for long time. @hadeelOth81 if you have budget go for netflow stealthwatch. but if you like me then this is only solution to keep us running unless we able to manage the big guys so spent more money on the tool we love.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 10:14 AM
I will check this feature update you today
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 04:14 AM
NO need more comment other answer You perfectly
thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 02:02 AM
Yes, there is a way to obtain NAT statistics and events in Cisco FMC (Firepower Management Center) for your FTD (Firepower Threat Defense) cluster. To view the NAT translations and associated events, you can follow these steps:
- Log in to your Cisco FMC web interface.
- Navigate to the "Analysis" tab in the top menu.
- Select "Events" from the drop-down menu.
- In the left-hand panel, under "Event Types," expand the "Network" section and choose "NAT Events."
- This will display the NAT events in the main window, showing the source IP, destination IP, and translated IP addresses involved in the NAT process.
To obtain specific information about internal IPs translated to a particular NAT IP address, you can use the search and filter options in Cisco FMC:
- On the "Events" page, use the search bar at the top to enter the desired NAT IP address.
- Press Enter or click the search icon.
- The search results will display the events where the specified NAT IP address is involved.
By analyzing the NAT events and associated data, you can determine which internal IPs have been translated to a certain NAT IP address within your FTD cluster.
Please note that the exact steps and options may vary slightly depending on the version of Cisco FMC you are using.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 06:31 AM
Thank you all, your solutions saved me for now, the only downside as Marvin mentioned FMC can save up to 2 days 6 hours 32 min
Much appreciate your help!!
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 07:20 AM
You can config the syslog and offload to external server.
Go to ACP--->select your interested policy--->Logging---->Default Syslog settings:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 09:26 AM
Thank you @Sheraz.Salim . I already configured external syslog server.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide






