- Cisco Community
- Technology and Support
- Security
- Network Security
- NATting an External IP to an Internal IP on an ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NATting an External IP to an Internal IP on an ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 09:26 AM - edited 03-11-2019 05:58 PM
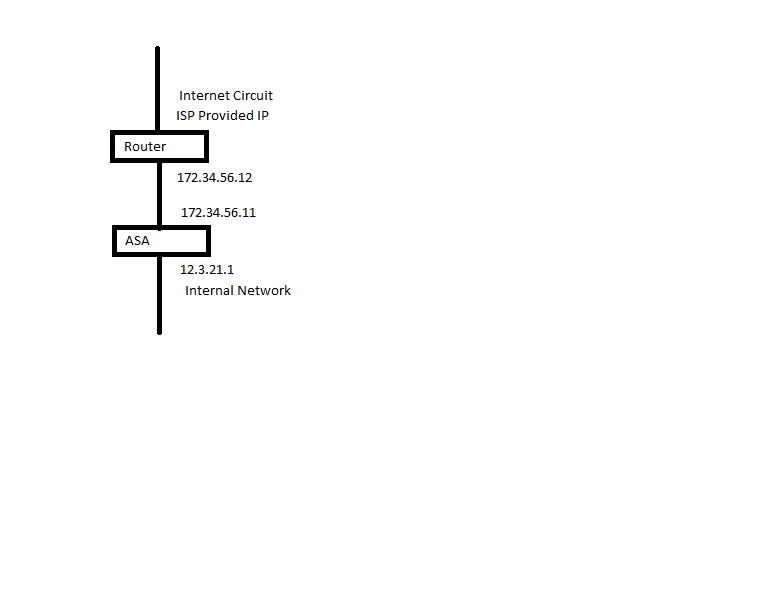
I have a router that sits on the front end of the network and has a public IP configured on the interface that connects to my ASA. Another interface on the router is configured with a public IP that connects to my ISP for Internet access. The ASA has an interface on my internal network. I would like to NAT the public IP of the router interface that connects to my ASA to an IP on my internal network. So, lets say the router public IP is 172.34.56.12. I want to NAT this IP to 12.3.21.2, which is an IP on my internal network. So then that way I can manage the router from my internal network using the internal IP. See the attached image. Is this possible and how?
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 09:34 AM
Hi,
Are you saying that your router has the following things
- Small public subnet/link network between the WAN interface and the ISP gateway
- Small public subnet/link network between the LAN interface and the ASA
If the above is true then why would you want to NAT the Routers IP address to an internal IP address just for management purposes? Dont you already have a Dynamic PAT configured for all traffic heading to the Internet (and the WAN router) that uses the ASA outside IP address? Should be no problem managing the router that way too?
What type of router do you have by the way?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 09:42 AM
Yes, that is correct. The router and ASA are located in one state and the management server is located in another state. If I have the mangement server manage the router using 172.34.56.12, the management traffic (snmp, tftp, etc.) is sent out over the Internet to get to the router. I want to be able to manage the router using an internal IP that can send the traffic over the VPN I have between the two locations. The router is a 3925E and the ASA is a 5540.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 09:49 AM
Hi,
Didnt see a mention of the VPN connection in the original post.
Do you have a L2L VPN / Site to Site / Lan to Lan VPN between the ASA and some other device at the location where the management server is? Can you clarify the VPN setup abit.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 09:57 AM
The VPN is a site to site VPN. So any traffic destined for the internal network of the other location goes over the VPN. The VPN is between two ASA's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 10:17 AM
Hi,
Seems kinda special setup if you ask me
What software does the ASA have? (At the site where the router is located) This ofcourse decides which kind of NAT configurations we can even try. And possibly if the setup you are asking for is even possible
If the WAN Router has an extra free interface I would possinbly consider the following
- Configure a VRF on the WAN Router
- Attach the free WAN Router port to that VRF
- Configure the interface with a free LAN IP Address
- Configure VRF default route towards the LAN networks default gateway
- Connect the interface to the LAN switch
- Use the L2L VPN to connect to the LAN IP address configured on the WAN Router interface
I cant personally say are there some serious security risks with this kind of setup but considering that the WAN Router interface would be in a VRF it would atleast be away from the Global Routing Table of the WAN Router. It would also be normally reachable through the L2L VPN
Naturally this totally depends if you even have a free interface on the WAN Router for this purpose (Some other similiar setup might be possible also)
A quick look for the Cisco 3925E model would suggest that there is 2 SFP Slots and 2 GigabitEthernet Ports? Or are there 4 GigabitEthernet ports with 2 additional SFP slots?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 10:25 AM
I don't want to use an interface on the router. The ASA is running 8.4.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2013 10:34 AM
Hi,
Not if this would work but the only thing I can think of would be
object network ROUTER-REAL
host 172.34.56.12
object network ROUTER-MAPPED
host 12.3.21.2
object network REMOTE-SITE
subnet 10.10.10.0 255.255.255.0
same-security-traffic permit intra-interface (unless already configured)
nat (outside,outside) 1 source static ROUTER-REAL ROUTER-MAPPED destination static REMOTE-SITE REMOTE-SITE
Where
- ROUTER-REAL = defines the actual interface IP address of the WAN Router
- ROUTER-MAPPED = defines the NAT address on the L2L VPN connection
- REMOTE-SITE = defines the L2L VPN Remote network
- same-security-traffic permit intra-interface = permits traffic to enter and leave through the same interface on the ASA (outside in this case)
- NAT Configuration = Does NAT between the same "outside" interface where ROUTER-REAL is translated to ROUTER-MAPPED when the destination is REMOTE-SITE
Naturally there might be some other considerations too like
- ROUTER-MAPPED IP address would need to be something that will be forwarded to the L2L VPN connection according to its "crypto map
- WAN Router would need to have a router for the REMOTE-SITE network
- If you are going to initiate some connections from the WAN Router you would need to allow the traffic on the local ASAs "outside" interface ACL
- Possibly something else?
Cant be sure if it will work
- Jouni
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


