- Cisco Community
- Technology and Support
- Security
- Network Security
- New to Firepower
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
New to Firepower
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 01:03 AM - edited 02-21-2020 09:18 AM
Hello,
I've inherited a couple of Cisco ASAs in active/passive mode that have Firepower installed. It seems there is also a VM appliance that I have access too.
Can anyone provide some handy commands to check how it's configure and what is being utilised?
Also I can't see what interfaces are being monitored.
Anything to give me a head start would be great then I can do some proper reading.
Thanks
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 02:35 AM
If FirePower is already configured you can use ASDM and it will scan Firepower module also. There you can access configuration -> ASA FirePower Module -> Device -> Interfaces. There you can see what interfaces are being placed in Zones and at Access Policy Rules you can see what Zones are placed in Source and Destination. At ASA configuration you can verify Firewall -> Inspect Policy -> global-map (or any other name) -> Check what traffic is passed to firepower for inspection and if it is monitor only or actualy inspecting the traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 03:34 AM - edited 07-17-2019 03:47 AM
All I can find in the ASDM is under Configurations > Firewall > Service Policy Rules
Here there is a policy called global-class with a tab called 'ASA FirePOWER Inspection' which is enabled and permits traffic.
I can't see any:
configuration -> ASA FirePower Module -> Device -> Interfaces or Firewall -> Inspect Policy
I do see the ASA FirePOWER Status tab under home and shows as 'Up' for status and application status
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 05:20 AM
From the ASA cli "show module sfr detail". If it is managed by the Firepower Management center (FMC, formerly known as Defense center or DC) that will be indicated in the output. If the module has been setup, similar info will show up on the Firepower section of the ASDM main page (down at the bottom center).
If the module is FMC-managed then all policies and settings are done on that server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 07:19 AM - edited 07-17-2019 07:29 AM
Hello,
Yes there is a FMC server, but I have no idea how the ASA servers data to it or how the ASA chooses what interface to monitor, all very confusing :). Seems there is no FirePower section on the ASDM apart from the tab on the home screen.
This is what I see:
en/act# show module sfr detail
Getting details from the Service Module, please wait...
Card Type: FirePOWER Services Software Module
Model: ASA5516
Hardware version: N/A
Serial Number: JADx
Firmware version: N/A
Software version: 6.2.2.1-73
MAC Address Range: 005d.xe.x7 to 005d.xe.x7
App. name: ASA FirePOWER
App. Status: Up
App. Status Desc: Normal Operation
App. version: 6.2.2.1-73
Data Plane Status: Up
Console session: Ready
Status: Up
DC addr: 172.x.x.5
Mgmt IP addr: 172.x.x.7
Mgmt Network mask: 255.255.255.0
Mgmt Gateway: 172.x.x.254
Mgmt web ports: 443
Mgmt TLS enabled: true
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 07:56 AM
Correct. When the Firepower service module is managed by FMC ("DC addr: 172.x.x.5") the the management of the module is not done at all via ASDM not can you see anything about it other than it's presence, software version, the fact that it is up and remotely managed.
The module inspects traffic that is sent to it via the ASA backplane according to the class-map/policy-map/service policy construct on the ASA config. Typically we send all traffic to the module (maybe excepting some that we don't want to inspect like for instance encrypted traffic that passes through the ASA). How the module inspects and what it does is completely configured on and reported to the FMC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 09:16 AM
Would you be kind enough to point me in the right direction to where there policies would be on the FMC?
I will check on the ASA at that global service policy as it must list the FMC IP somewhere?
Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 08:08 PM
The ASA service policy pushes traffic to the internal Firepower module. The module interacts with the FMC to both receive configuration and send events.
In an FMC, the policies primarily are under an Access Control policy (ACP). The most common is the ACP itself but can also include Intrusion, Network Discovery, SSL and File polices as well as other elements like Security Intelligence and QoS.
There are several books as well as numerous free Cisco Live presentations that cover these in much more detail if you're interested in learning more.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2019 10:50 PM
I just need to first enable or remove an interface and wondered how I do that in FMC?
Kind regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 06:01 AM
All interface configuration is done from the ASA. FMC only configures policies and related settings for the Firepower service module.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 06:04 AM
Where on the ASA is this configured? We have many interfaces and I need to see which ones are being monitored.
I can't seem to locate this on the ASDM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 08:19 AM
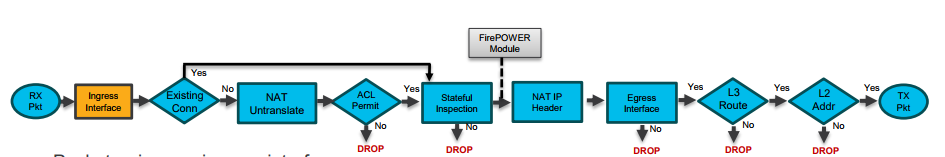
A Firepower service module (or, by extension, FMC) doesn't monitor ASA interfaces per se. It monitors traffic sent to is by the ASA class-map which is referenced in a policy-map and applied via a service policy (usually global). The class-map can say monitor all traffic or only traffic that matches an ACL. Whatever it scoops up is sent to the service module - irrespective of ASA interfaces.
Perhaps this flowchart will help explain it:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 07:37 AM - edited 07-19-2019 07:41 AM
hi,
there are two ways to manage the ASA with FirePower (FP): locally via ASDM or via a central FMC.
do you want to learn how your current ASA talks to FMC? or are you removing the active/passive pair from FMC and do your own lab?
try to locate for the ASA policy-map and/or firepower ACL (if any).
you can refer to this helpful link to learn about ASA FP, ASDM and FMC:
http://wannabecybersecurity.blogspot.com/2019/01/cisco-asa-firepower-traffic-redirection.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 08:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 06:27 PM - edited 07-19-2019 06:28 PM
hi,
the FP module on the ASA talks to FMC via the global policy map (and ACL) traffic redirection and registering the managed device/sensor (ASA FP) to the FMC.
you configure the security zones which the ASA interfaces are associated and then apply the FMC access control policy (ACP).
see helpful link:
http://wannabecybersecurity.blogspot.com/2019/06/configuring-cisco-fmc-objects-and.html
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide