Open Firewall Ports
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 09:52 AM
I am a firewall newbie so please excuse my ignorance. I need to open some firewall ports to setup a Barracuda web filter. Do I open ports under NAT Rules in ASDM 7.9 or some other place? Thanks for any guidance, I really appreciate it.
Here are the ports I need to open:
Port Direction Protocol Description
| 22 | In/Out | TCP | Remote diagnostics |
| 25 | Out | TCP | Email and email bounces |
| 53 | Out | TCP/UDP | DNS (Domain Name Server) |
| 80 | Out | TCP | Virus, spyware, category definition updates, and firmware updates |
| 123 | In/Out | UDP | NTP (Network Time Protocol) |
| 8000 | In/Out | TCP | To access web interface. |
8002 | In/Out | TCP | Synchronization between linked systems. |
| 23557 | In/Out | TCP |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 09:58 AM
They are access control rules that will need adding to your access control list, I presume the firewall is already configured and has ACLs you can add those rules to ? See the link below, remember to be specific and only allow the ports required to the source / destinations required. If you don't usually do it it's probably worth doing it with someone or getting someone to peer review if possible ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 10:36 AM - edited 05-29-2020 11:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 11:48 AM
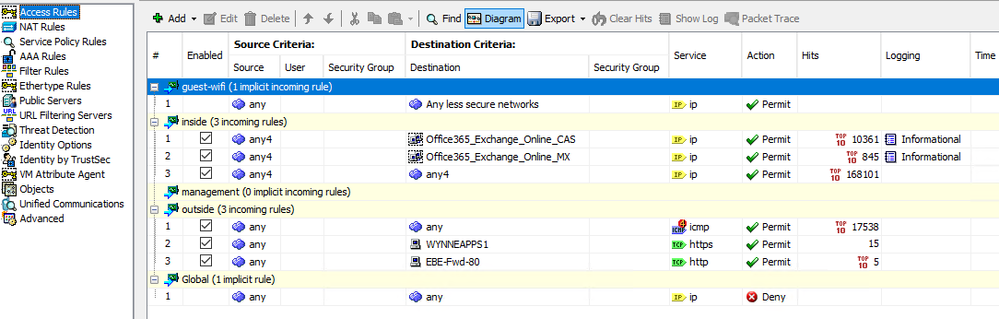
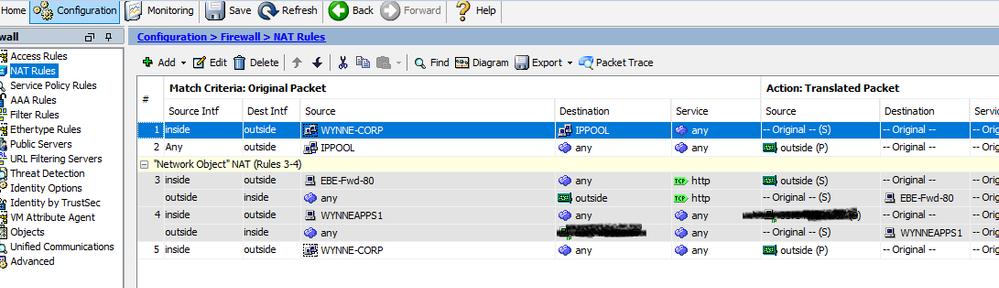
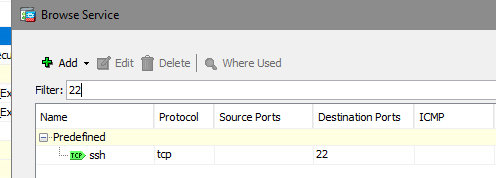
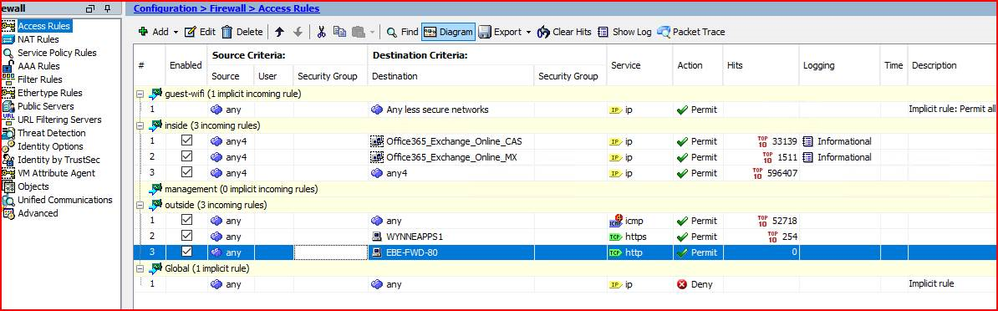
I have created both Access and NAT Rules. (see screenshot). I get confused when on the direct; some ports are Out and the other ports are In/Out. Also, for example, when I try to do Port 22, it comes up as SSH instead of TCP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2020 12:32 AM
Your ACL from traffic inside to outside is permitting "any" from inside to outside, so you shouldn't explicitly need to permit any outbound traffic.
Why do you need to permit the traffic "in" for NTP, SSH, access to the web interface, sync etc? Is this system being remotely managed from outside the firewall? If not I don't see why you should need these rules. The firewall is stateful, so any traffic you permit outbound will automatically be permitted back in.
SSH uses TCP protocol port 22.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 05:30 AM
I believe I setup the Access and NAT correctly. How does it know that I want port 80 to go to 81? Do I have to enter 81 somewhere?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 05:33 AM
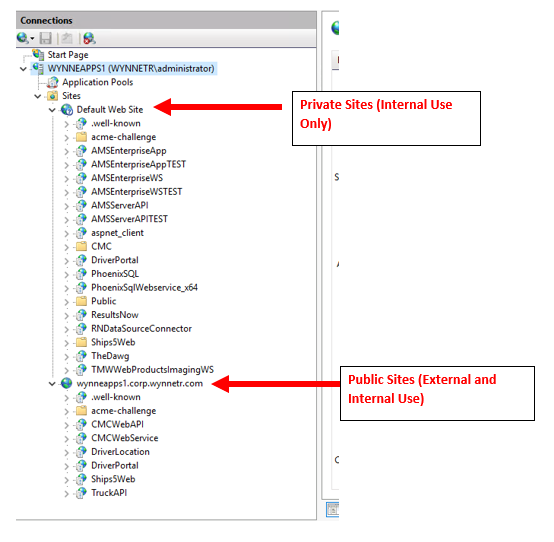
I have several sites on my web server in IIS. Some I want public and some I need private (internal use only).
The private sites use port 80 and 443. The public sites use 81 and 444. I need to ensure that traffic from WAN to LAN is forwarded from 80 to 81, and 443 to 444.While keeping 80/443 hidden or internal only. Hope this makes sense. Thanks for all the help!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 10:17 AM
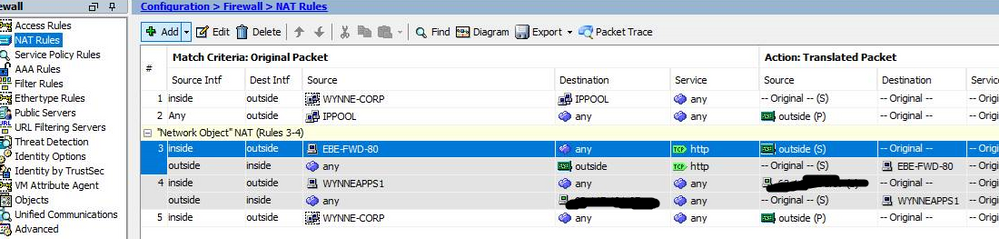
If the sites you want exposed to the public only listen on ports 81 & 444 then you could to this with a static NAT & just allow those ports through the firewall from the WAN to LAN ? Slightly less common ports so will prevent a little bit of sniffing. Is that feasible or do you need to ensure WAN traffic uses an existing connection string that you can't modify ?
From a security perspective I'd advise you use a different web server for internal and external sites. I'd also be concerned by the IPv4 any - outside being permitted but that will take some time and effort now a few services will be relying on it. One to resolve over time.
For the TCP/22 showing as SSH, it's just a known port so the ASA does it automatically as per HTTP/S. You can also create port objects and call them what you like.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 10:37 AM
I have all my Private Sites setup separately from Public Sites. See screenshot below.