- Cisco Community
- Technology and Support
- Security
- Network Security
- Ping from outside to outside interface Firepower 1150
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ping from outside to outside interface Firepower 1150
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2023 01:31 PM
Hello everyone,
I'm unable to ping the outside interface's public IP from the outside. I have ICMP inspection enabled as well as the ACL "icmp permit any outside." I can ping through the device without issue. Looking at the log, it is showing:
- "ICMP error packets were dropped by the ASA because the ICMP error messages are not related to any session already established in the ASA."
I should note, this is one of our VPN servers and the outside interface IP I'm trying to ping is the headend to many ezvpn tunnels. Could that be causing an issue with the way it handles unencrypted traffic on that interface, or is something else goofy going on?
Thanks!
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 03:05 AM
My first question is where are you pinging from? You might already know this, but you can only ping the ingress interface of the firewall, you will not be able to ping a firewall IP that is not the ingress IP.
The EZVPN should not be causing issues. It is quite normal having both VPN and normal data traffic on the same "outside" interface.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 03:18 AM
The issue you are encountering may be caused by the way the Firepower 1150 handles ICMP traffic on the outside interface.
When you are trying to ping the outside interface's public IP, the device is likely dropping the ICMP packets because it does not have an established session for the ICMP traffic. This can happen because ICMP traffic, like ping, is stateless and does not initiate a new session, thus the ASA doesn't know how to handle the ICMP packets.
Here are a few things you can try to resolve the issue:
Create a static NAT rule for the outside interface's public IP, this will allow the ASA to create a session for the ICMP traffic and allow it to pass through.
Create an access rule that allows ICMP traffic from the outside to the outside interface's public IP.
Make sure that the ASA has the feature of ICMP inspection enabled and that the correct ICMP types are allowed.
Make sure that the firewall's inside interface is not blocking the ICMP traffic.
Make sure that the VPN service is not blocking the ICMP traffic.
It's also worth noting that, if the VPN server is handling many ezVPN tunnels, it could be possible that the VPN traffic is taking up resources or filling up connection tables on the firewall and causing issues with handling the ICMP traffic.
You can check the resource usage on the Firepower device by using the command:
show resource usageIf you are still experiencing issues after trying these steps, you may want to contact Cisco TAC for further assistance.
Please rate this and mark as solution/answer, if this resolved your issue
All the best,
AK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 05:34 AM
Hi @Colin B ,
Can you add the following command and try again.
same-security-traffic permit inter-interface
Regards,
Harold Ritter, CCIE #4168 (EI, SP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 05:44 AM
isn't that command meant to be same-security-traffic intra-interface ?
inter-interface is for traffic between interfaces with the same security level. But this is for "through-the-box" traffic so I do not believe it will affect ICMP to the box.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 05:58 AM
Hi @Marius Gunnerud ,
It looks like I misread the OP. I thought he was trying to ping between to devices to two interfaces at the same security level.
Regards,
Harold Ritter, CCIE #4168 (EI, SP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2023 09:56 AM
If you are coming from an address downstream of the outside interface of a Cisco Secure Firewall Threat Defense (FTD) and trying to ping the interface address, you need to allow icmp to the interface.
This has nothing to do with NAT and Access Control Policies but is a platform setting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 01:48 AM
Hi Colin,
You can enable ICMP access for your outside interface on FMC(Firepower Management Center) under Devices > Platform Setting > select ICMP Access > Click Add button on ICMP access page and set action permit, set ICMP services, set Network to get access of outside interface and select a Zone of your outside interface. Please find below screenshot for your reference


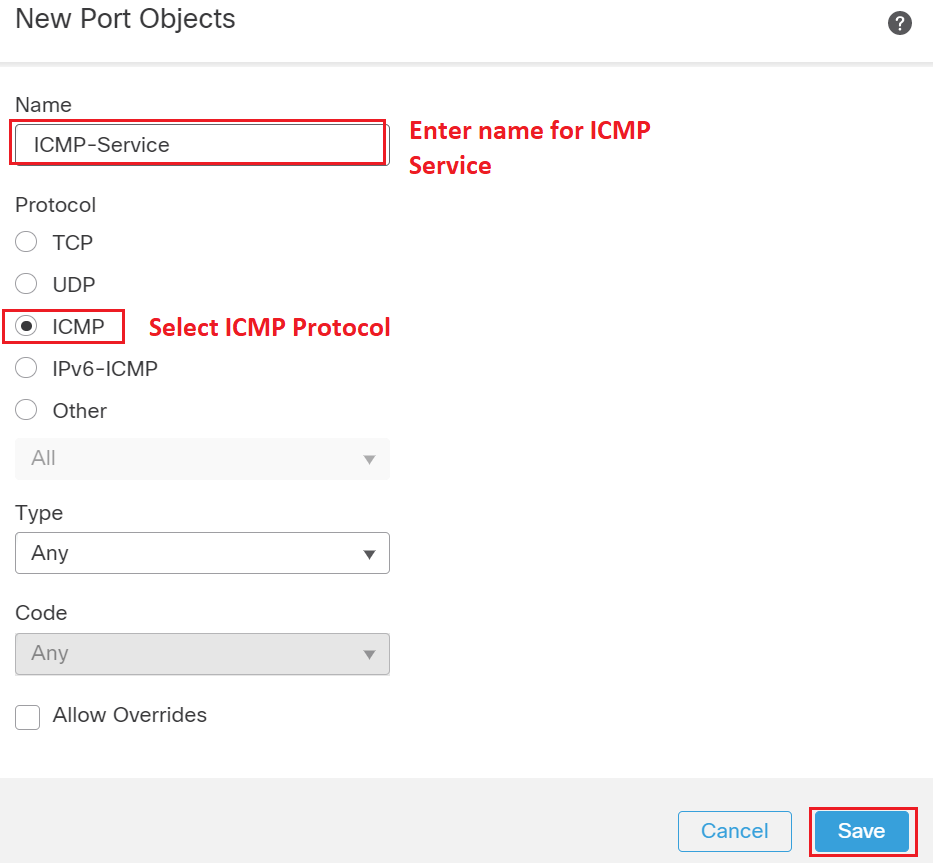


Hope above steps will help you on pinging your outside interface from outside
-----------------------------------------
If you find my reply solved your question or issue, kindly click the 'Accept as Solution' button and vote it as helpful.
You can also learn more about Secure Firewall (formerly known as NGFW) through our live Ask the Experts (ATXs) session. Check out Cisco Network Security ATXs Resources [https://community.cisco.com/t5/security-knowledge-base/cisco-network-security-ask-the-experts-resources/ta-p/4416493] to view the latest schedule for upcoming sessions, as well as the useful references, e.g. online guides, FAQs.
-----------------------------------------
Regards
Arunkumar
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide






