- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Possible to send IoC events from FMC to SNMP/Email?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Possible to send IoC events from FMC to SNMP/Email?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 01:47 AM
Hello,
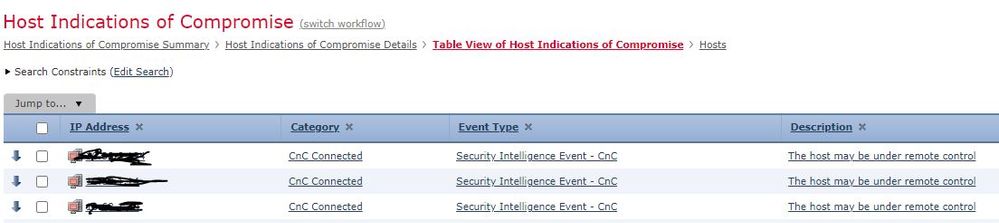
We are running FMC 7.2 and on the summery dashboard on the Threats TAB, there is a list called "Indication of Compromise by Host" where we can see hosts that have downloaded malware and are CnC connected. It looks like this:
We would like to get an email or/and a SNMP alert whenever this happens, but I cannot find where I can configure this.
I've looked under Policys->Actions->Alerts->Advanced Malware Protection Alerts, but I am not sure this is exactly the same alerts?
Thanks
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 12:21 AM - edited 02-09-2023 12:33 AM
Did some more invistagation into this and the IoC events we see in the Threat TAB in the dashboard comes from the Analysis->Hosts->Indications of Compromise page. Is it possible to get emaill alerts for those events?
Thanks
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 01:13 AM - edited 02-09-2023 01:17 AM
You could look into Monitor Alerts, there you can create alerts for Security intelligence on the FMC.
Another option, and perhaps a better option, is to integrate your FMC with SecureX, there you should be able to create playbooks based on events and those events trigger actions like sending an email.
https://blogs.cisco.com/security/automate-your-way-to-success-with-cisco-securex
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 05:03 AM - edited 02-09-2023 05:17 AM
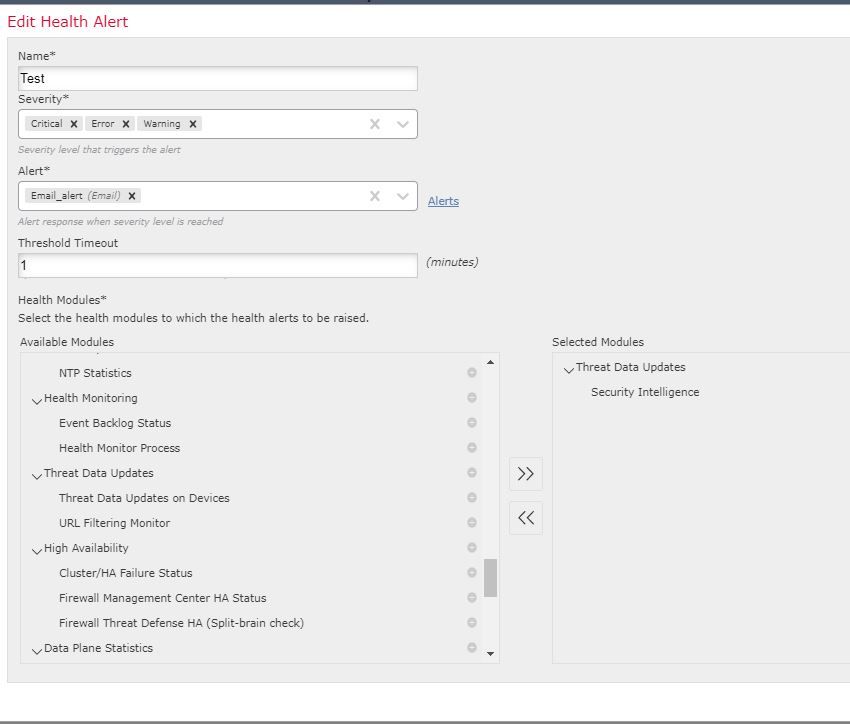
Thanks Marius. I will have a look at that.
Edit. Is this the correct one? This was the only one I found related to Security Intelligence, but it seems more like an update alert?
Best regards
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2024 06:17 AM - edited 09-11-2024 06:54 AM
Same question here. IoC is an interesting event to receive in both mail alert and SNMP trap from FMC.
However I also feel the need to differentiate on type of IoC:
Outside in: blocked and happens all the time: not that much interested in
Inside out: that looks like we have a host with a CnC infection: very interesting to know and investigate further
Inside to inside host: same as above.
I am starting to test with a rule under Policies - Correlation - Rule Management and use as connections event with an IOC Tag for certain networks. After that under Policy Management connect new Rule to the SNMP settings to that rule. Hope that works as expected.
Cheers /Ruud
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide