- Cisco Community
- Technology and Support
- Security
- Network Security
- PPTP Traffic Not Passing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PPTP Traffic Not Passing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 01:38 AM - edited 03-12-2019 12:13 AM
Hello,
i have issue in my network , as part of the work we need to connect to outside PPTP server but its always fail , works only if we connect directly to the gateway router.
back behind the ASA the client cant connect , what is driving me crazy is when i do packet tracer with ASDM its show everything working fine ,
the below configuration is all i need to connect from client to outside server . also i have tried connect wireless and wired , but nothing
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect pptp
service-policy global_policy global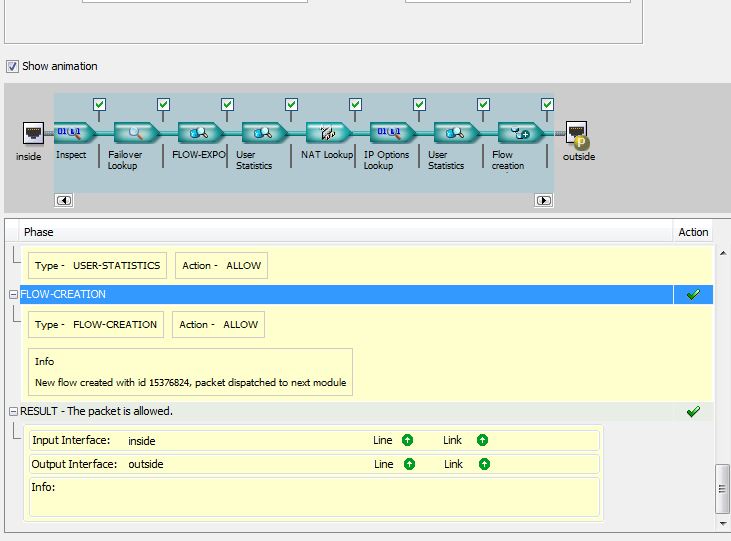
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 02:44 AM
That should work. Is it definitely using PPTP and not L2TP over IPSec (aka, is the client VPN configuration left on automatic and you have assumed it is PPTP)?
Using the ASDM log when trying to connect do you see anything being blocked or any warnings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 02:50 AM

this is the debug from the asa for two connection try , its always fail after the unknown -message show up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 03:01 AM
What version of software are you using on your ASA?
I meant just the normal ASDM logging, not debugging (although the above is interesting to see). Are any packets getting dropped?
The above makes it looks like the workstation is doing the disconnect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 03:10 AM
we are working with Version 9.4(2) 5545 with firepower module what is driving me crazy that when i do packet tracer on the ASDM it show success for all steps and its working fine if i connect from anywhere and direct to the router , but not the ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 03:23 AM
I'm not really a fan of the 9.4(x) train, as I have had other issues with it.
I don't think it is likely to fix it, but I would be tempted to go to 9.5(2)200. That train has been working well for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2016 03:29 AM
i will keep looking and let you know the final result , thank you for the advice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 01:49 AM
I have a same problems.How did you solve it ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 02:07 AM
i didn't solve it yet , i also found a line to go with
: SFR requested to drop GRE packet from outside , this was message from the syslog server that the ASA send log to it , so now i know where is the issue
but it was totally hidden as no alarm on IPS or blocked by any rules
i will tell you in details when i get it to work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2016 06:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2016 07:46 AM
thank you for this advice , but i have tried this before and didn't solve the case 😄
i think i have another issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2016 10:56 AM
i am sorry for my late reply, i found the solve.
i am using SSL Inspection , we has to remove the SSL Policy from the access policy after that its working, for now the TAC didn`t respond why that issue happen as its up-normal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2016 05:25 AM
Hi
I have the same problem.
Can you be more specific when you says .. :
"...we has to remove the SSL Policy from the access policy after that its working".
Remove SSL Policy .. ?? Where ??
I have tried to do a Global Inspection specific that make the GRE pass.
After another inspection that redirect to SFR.
Same problem.....
Thanks for help...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2016 05:38 AM
Please tell me what version of FireSIGHt do u have, and i will try to explain based on it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2016 05:40 AM
Hi
Thanks for the answer
I have 6.0.0-1005
Thanks again
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
