- Cisco Community
- Technology and Support
- Security
- Network Security
- Problems when I put a server in the dmz
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problems when I put a server in the dmz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2012 02:53 PM - edited 03-11-2019 05:06 PM
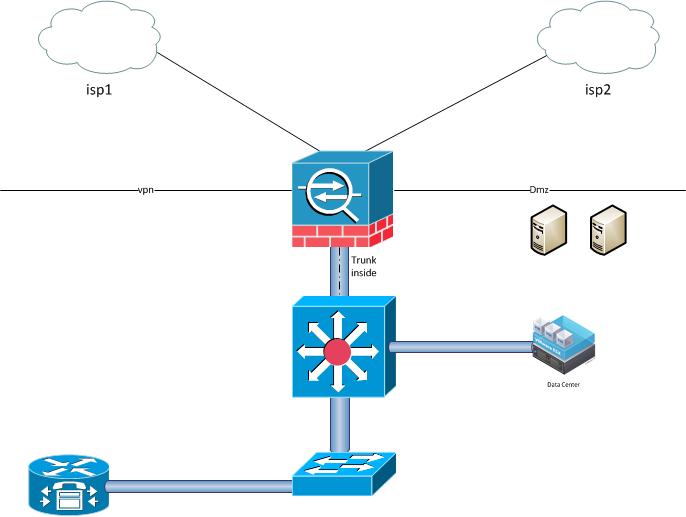
I have a asa5505, with this software:
Cisco Adaptive Security Appliance Software Version 8.4(4)1
Device Manager Version 6.4(7).
Im using vlans interface. I have the following vlan interfaces configured:
outside (called isp1),inside,dmz.
The asa is connected to a switch via trunk. There are several ESXi servers with VMs connected to the same switch.
The isp1 vlan interface is asociated with the e0/0.
I have a problem, when I start any (linux or windows) server in the dmz, all the internal networks lose the internet connection (via isp1).
There is a static nat X.X.X.61 <-> 192.168.111.61 beetwen the test server and the outside.
There are dynamic nat (pat) between the internal networks and the public ip on the outside interface x.x.x.64.
After several attempts (with whatismyip.com) I get verify that the public ip is x.x.x.61
What is wrong?...
attached the most relevant config.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2012 03:44 PM
Hi,
Have you tried to check on the ASA in realtime what happens to the connections attempts throught it when you start up a server?
Do you mean that for the LAN to work normally you wont have any servers up and running on the DMZ? Seems abit odd.
You sure there isnt somekind of loop with the server platform and switches that chokes the whole network including ASA?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2012 08:07 AM
Hello Jouni,
checking the realtime log, only nomal Build and TearDown messages, no deny msg.
Yes. in the moment the server in dmz try to access the internet , for example http, or dns all the internet goes down for all the internal networks.
I did a test putting the ASA alone. Also I assingned dmz and inside IP´s to the fisical ports, connected one pc in the inside interface, another pc in the dmz interface.
The pc in the iside interface is able to access internet until I plug the (dmz) cable in the pc. Exactly when the pc try to access the dns servers or I open the http browser.
Im stucked because I need start the dmz for several servers.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2012 01:02 PM
Hello,
Please share the show run NAT
Regards,
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2012 01:11 PM
show run nat:
!
object network PCoIP-host
nat (dmz,isp1) static 190.147.134.61
object network web-mail-host
nat (dmz,isp1) static 190.147.134.48
object network smtp-host
nat (dmz1,isp2) static interface service tcp smtp smtp
object network www-host
nat (dmz1,isp2) static interface service tcp www www
object network pop3s-host
nat (dmz1,isp2) static interface service tcp 995 995
object network dns-tcp-host
nat (dmz1,isp2) static interface service tcp domain domain
object network dns-udp-host
nat (dmz1,isp2) static interface service udp domain domain
object network 172.16.1.x-190.147.134.64-PAT-network
nat (inside,isp1) dynamic interface
object network 172.16.1.x-200.116.11.57-PAT-network
nat (inside,isp2) dynamic interface
object network dvr-udp-host
nat (dmz,isp3) static interface service udp 8080 8080
object network dvr-tcp-host
nat (dmz,isp3) static interface service tcp 8080 8080
object network 10.10.10.x-190.147.134.64-PAT-network
nat (inside,isp1) dynamic interface
object network 10.10.10.x-200.116.11.57-PAT-network
nat (inside,isp2) dynamic interface
object network 172.16.1.48-190.147.134.64-PAT-network
nat (inside,isp1) dynamic interface
object network 172.16.1.48-200.116.11.57-PAT-network
nat (inside,isp1) dynamic interface
object network 192.168.x.x-200.116.11.57-PAT-network
nat (inside,isp2) dynamic interface
object network 192.168.10.x-190.147.134.64-PAT-network
nat (inside,isp1) static interface
object network 192.168.100.x-190.147.134.64-PAT-network
nat (inside,isp1) static interface
object network 192.168.15.x-190.147.134.64-PAT-network
nat (inside,isp1) static interface
object network 192.168.50.x-190.147.134.64-PAT-network
nat (inside,isp1) static interface
#show run object:
object network PCoIP-host
host 192.168.111.61
....
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2012 01:33 PM
Hello Rafael,
do the following:
packet-tracer input inside tcp 172.16.1.100 1025 4.2.2.2 80
Regards,
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2012 01:40 PM
packet-tracer input inside tcp 172.16.1.100 1025 4.2.2.2 80
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 0.0.0.0 0.0.0.0 isp1
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
object network 172.16.1.x-190.147.134.64-PAT-network
nat (inside,isp1) dynamic interface
Additional Information:
Dynamic translate 172.16.1.100/1025 to 190.147.134.64/1025
Phase: 5
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 61570, packet dispatched to next module
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: isp1
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2012 01:43 PM
Hello Rafael,
Okay so the packet-tracer shows the inside network gets Natted to the ISP1 interface. Configuration looks good.
Basically what you are saying is as soon as you have the DMZ servers all of the internal users are unable to go to the internet correct?
I would say the best way to handle this would be creating captures at the time you have the DMZ server on, what do you think?
Regards,
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2012 08:32 PM
My friends,
I think that is a proxy arp issue. But I don't have a solution yet.
I need some help with this.
Thank.s
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2012 09:13 PM
Hello Rafael,
Can you do some captures when the server is in place?
From an inside host, so we can determine if there is a problem with the ASA,
Regards,
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 04:04 AM
Hello Julio,
I did some changes to test. I just put the e0/0 and e0/1 in the outside vlan (isp).
The e0/2 is in the dmz vlan and the e0/3 is in the inside vlan.
internet in the isp vlan interface (E0/0) works fine alone. When I plug another pc in the E0/1 port, or if I plug a pc in the E0/2, all the traffic goin from the inside to internet (isp) goes down.
Also I just take off the ASA and put back a Cisco RV042 that was working before the ASA, I have the same problem.
the internet on the isp is ok. a Pc connecte alone in the modem works fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 09:40 AM
Hello Rafael,
Okay here is what I want you to do:
put the e0/0 and e0/1 in the outside vlan (isp).
The e0/2 is in the dmz vlan and the e0/3 is in the inside vlan.
Then connect a PC to the inside vlan
capture capin interface inside match icmp any host 4.2.2.2
capture capout interface outside match icmp any host 4.2.2.2
Then try to ping from the inside host to 4.2.2.2 and afterwards provide
show cap capin
show cap capout
Regards
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2012 03:34 AM
Hi Julio,
After try everything, I decided do a wireshark capture. Everything looks fine, I just was curiously about a "IP checksum offload" message, doing some research with google, I saw the light. All the problems starts when the virtual machines migrated (due to drs) to one of the servers that have Gigabits NIC with TOE (Broadcom NetXtreme II 5709 Dual Port Ethernet PCIe Card with TOE and iSCSI Offload).
I just disabled the tso (tcp segmentation offload) for the affected OS. Now everything is fine.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2012 09:37 AM
Rafael,
Great to hear that,
Some kudos for you,
Please mark the question as answered,
Regards
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


