- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: "Blocked by File Process" with Verdict as BLOCK
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
"Blocked by File Process" with Verdict as BLOCK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2020 09:36 AM
There is a Firewall Rule from 10.1.1.29 to 10.7.3.220 on tcp 445 port. When Checked from FMC GUI Log it does not show any log from 10.1.1.29 to 10.7.3.220 on 445 port. Rather we see traffic from 10.1.1.29 to 10.7.3.220 on port 135 from FMC GUI.
However If I check same traffic log from CLI as per below it shows , by File Policy there are some block saying "Blocked by File Process" with Verdict as BLOCK. It is also true that sometimes from CLI I see Verdict is Pass but that does not reflect at FMC GUI Log.
Is this is something blocked by File Policy ?
10.7.3.220-445 - 10.1.1.29-64152 6 Packet: TCP, ACK, seq 3562632589, ack 892842533
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 ShmDBLookupFile returned 0
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature cache query returned Cache Miss for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with disposition Cache Miss, spero Cache Miss, severity 0, and transmit Not Sent
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 Archive Inspection query returned Cache Miss for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with disposition Cache Miss
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature reserved file data of 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 for arc insp with flags 0x0061DB00 and status Smaller than Min Filesize
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature reserved file data of 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with flags 0x0061DB00 and status Smaller than Min Filesize
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature verdict Pending and flags 0x0061DB00 for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 of instance 511341060
10.7.3.220-445 - 10.1.1.29-64152 6 File Process: malware detected, gid 147, sid 1, drop
10.7.3.220-445 - 10.1.1.29-64152 6 AppID: service NetBIOS-ssn (SMB) (755), application unknown (0), out-of-order
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 Rule Id (0) passed in pkt header is no longer valid
10.1.1.29-64152 > 10.7.3.220-445 6 Firewall: allow rule, 'SharePoint_Web_R17', allow
10.1.1.29-64152 > 10.7.3.220-445 6 Snort: processed decoder alerts or actions queue, drop
10.1.1.29-64152 > 10.7.3.220-445 6 Snort id 21, NAP id 7, IPS id 5, Verdict BLOCK
10.1.1.29-64152 > 10.7.3.220-445 6 ===> Blocked by File Process
Verdict reason is sent to DAQ
10.7.3.220-445 - 10.1.1.29-64152 6 Packet: TCP, ACK, seq 3562632589, ack 892842533
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 ShmDBLookupFile returned 0
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature cache query returned Cache Miss for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with disposition Cache Miss, spero Cache Miss, severity 0, and transmit Not Sent
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 Archive Inspection query returned Cache Miss for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with disposition Cache Miss
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature reserved file data of 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 for arc insp with flags 0x0061DB00 and status Smaller than Min Filesize
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature reserved file data of 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with flags 0x0061DB00 and status Smaller than Min Filesize
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature verdict Pending and flags 0x0061DB00 for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 of instance 511341060
10.7.3.220-445 - 10.1.1.29-64152 6 File Process: malware detected, gid 147, sid 1, drop
10.7.3.220-445 - 10.1.1.29-64152 6 AppID: service NetBIOS-ssn (SMB) (755), application unknown (0), out-of-order
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 Rule Id (0) passed in pkt header is no longer valid
10.1.1.29-64152 > 10.7.3.220-445 6 Firewall: allow rule, 'SharePoint_Web_R17', allow
10.1.1.29-64152 > 10.7.3.220-445 6 Snort: processed decoder alerts or actions queue, drop
10.1.1.29-64152 > 10.7.3.220-445 6 Snort id 21, NAP id 7, IPS id 5, Verdict BLOCK
10.1.1.29-64152 > 10.7.3.220-445 6 ===> Blocked by File Process
Verdict reason is sent to DAQ
10.7.3.220-445 - 10.1.1.29-64152 6 Packet: TCP, ACK, seq 3562632589, ack 892842533
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 ShmDBLookupFile returned 0
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature cache query returned Neutral for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with disposition Neutral, spero Cache Miss, severity 0, and transmit Not Sent
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 Archive Inspection query returned Cache Miss for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with disposition Neutral
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature reserved file data of 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 for arc insp with flags 0x0061DB00 and status Smaller than Min Filesize
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature reserved file data of 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 with flags 0x0061DB00 and status Smaller than Min Filesize
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 File signature verdict Log and flags 0x0061DB00 for 275842bcd62a6ba116c1086bef4c96585482b818cbff465def315f5e423430b9 of instance 511341060
10.7.3.220-445 - 10.1.1.29-64152 6 AppID: service NetBIOS-ssn (SMB) (755), application unknown (0), out-of-order
10.1.1.29-64152 > 10.7.3.220-445 6 AS 1 I 21 Rule Id (0) passed in pkt header is no longer valid
10.1.1.29-64152 > 10.7.3.220-445 6 Firewall: allow rule, 'SharePoint_Web_R17', allow
10.1.1.29-64152 > 10.7.3.220-445 6 Snort id 21, NAP id 7, IPS id 5, Verdict PASS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2020 06:28 PM
What is your current policy? Are you doing a malware cloud lookup?
Looks like the system is taking some time before the verdict of "Neutral" shows up for the file sha. Until that time, the firewall keeps blocking the file. Once the disposition is known, we see that the attempt is successfully passed. This is an expected behaviour.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2020 11:35 AM
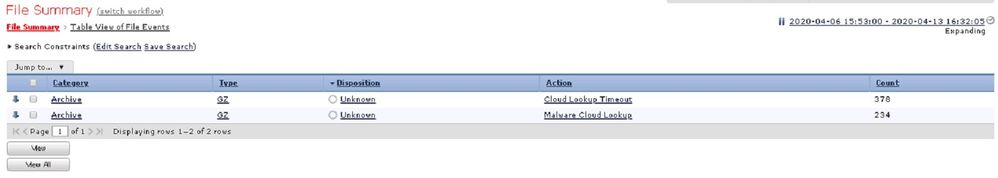
I see Logs shown Disposition as Unknown.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2020 01:05 PM
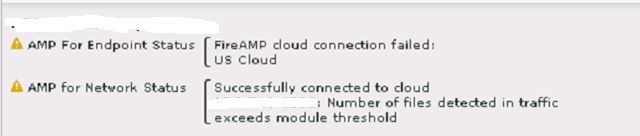
Additional question is why does it show "Cloud Lookup Failed" and 2nd set showing "Malware Cloud Lookup". It does not seem "Cloud Lookup Failed" is normal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2020 06:27 PM
cloud failed or the cloud couldn't analyze the file (for example password
encrypted file, etc). Ensure that your FTD can connect to the Talos cloud.
If its good, then I think the cloud isn't able to analyze the files because
they are compressed ones (GZ files).
Malware lookup indicate that its sending the query to the cloud because the
FMC doesn't know the hash of the file. But most of these queries are timing
out as per the other log (cloud lookup timeout)
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 08:23 AM
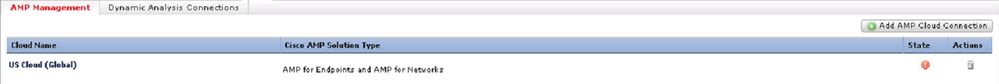
How to verify FMC to TALOS Connectivity ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 05:20 PM
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Reference_a_wrapper_Chapter_topic_here.html#id_97785
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2020 01:54 PM
I see AMP for Endpoints and Networks is most of the time intermittently broken. Any suggestions to fix it ? I believe when this is broken I see "CLOUD LOOKUP TIMEOUT"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2020 05:15 PM
1. Check if you are able to reach internet from your FMC - Pings to any internet IP.
2. Check if there is a working DNS configured - Ping a domain name
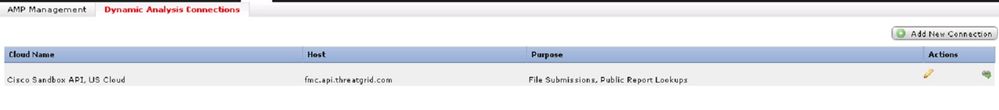
3. Check if you are able to reach the threadgrid host mentioned in the above screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2020 01:32 PM
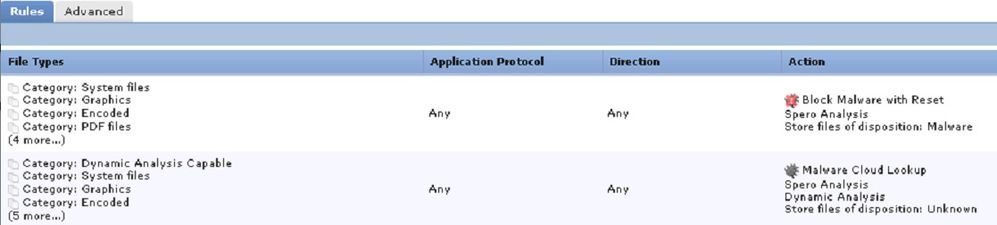
Yes I am using Malware Cloud LookUp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2020 11:57 PM
First your connection is dropped by snort because of malware matched using
fie policy scan. From your logs
10.7.3.220-445 - 10.1.1.29-64152 6 File Process: malware detected, *gid
147, sid 1,* drop
GID/SID details
https://snort.org/rule_docs/1-147
To have the logs reflected in FMC, you need to make sure that your IPS and
File rules matched in the ACP have logging enabled. From the logs, this
drop is triggered by rule named *SharePoint_Web_R17*
Ensure that logging is enabled for this rule (at the end of the
connection). If you have it at beginning of the connection, this drop won't
reflect.
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2020 11:30 AM
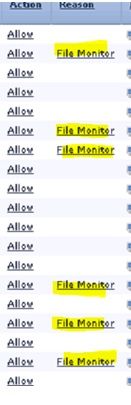
Logging is enabled with Logg at the end of the connection set. I see Log from FMC as per attached one ( File_Monitor_1.jpg )
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide