- Cisco Community
- Technology and Support
- Security
- Network Security
- Routing accross Cisco ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Routing accross Cisco ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2018 05:02 AM - edited 02-21-2020 08:21 AM
This is an accidental duplicate of: https://community.cisco.com/t5/firewalls/routing-across-asa-nat/m-p/3724964
Hi,
I have searched high and low over the last few days and couldn't find exact answer that would work in my case. I have the following setup:
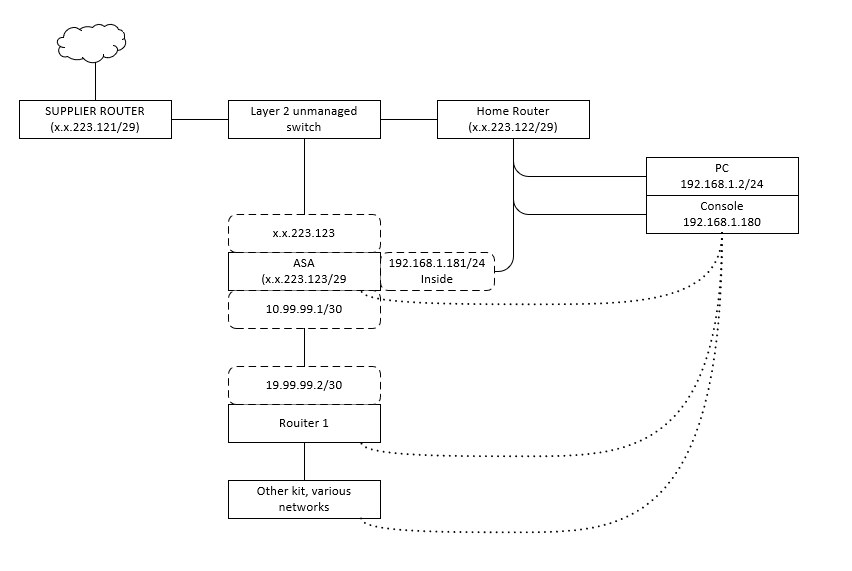
Essentially the network connectivity to my home is presented via 'business line' router that offers a modem mode that negotiates a GRE tunnel presenting a /29 network with a gateway marked on the leftmost router.
Onwards connectivity is provided via Layer 2 unmanaged switch that has a regular run of the mill router dishing out addresses in 192.168.1.0/24 and doing what I assume is basic NAT, as the DHCP dishes out gateway of x.x.223.121. It by itself as a public IP address of .122. Also, there's ASA connected to that switch that takes an address .123:
- Cisco Adaptive Security Appliance Software Version 9.1(7)13 - suggest the 'new style' NAT that I use below
- Device Manager Version 7.9(2)152
Behind the ASA sits my home lab (I'm currently training for CCNA, so ASA seemed a bit deep jump to go for, but I could get one very cheaply) defined on a DMZ interface. The ASA has two other interfaces - outside with the public address and inside with a 192.168.1.181/24 address. Lastly, there's a console server build on old 2511 that sits on 192.168.1.180/24. What I am aiming to achieve is to telnet/ssh through the ASA to the ingress router to my lab (SSH) or to the Console (telnet, I know.... doesn't support SSH).
I have broadly followed this guide to a certain degree of success, based on its latter part.
The relevant bits of config on ASA:
Configuration on interfaces:
interface Ethernet0/0 speed 1000 nameif outside security-level 0 ip address x.x.223.123 255.255.255.248 ! interface Ethernet0/1 nameif dmz security-level 50 ip address 10.99.99.1 255.255.255.252 ! interface Ethernet0/2 nameif inside security-level 100 ip address 192.168.1.181 255.255.255.0 !
There are network objects configured, with static NAT:
object network console host 192.168.1.180 nat (inside,outside) static x.x.223.124 object network R1 host 10.99.99.2 nat (inside,outside) static x.x.223.125
And there is also the access list that's applied as a single group to the outside interface
access-list inbound extended permit tcp any host 192.168.1.180 access-list inbound extended permit tcp any host 10.99.99.2 access-group inbound in interface outside
When I run packet tracer it all looks reasonable when simulating access from the outside to the object in question, same result on both - the other omitted for brevity, using packet-tracer from 8.8.8.8 to the public address, with tcp over port 22
Phase: 1 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 2 Type: UN-NAT Subtype: static Result: ALLOW Config: object network console nat (inside,outside) static x.x.223.124 Additional Information: NAT divert to egress interface inside Untranslate x.x.223.124/22 to 192.168.1.180/22 Phase: 3 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group inbound in interface outside access-list inbound extended permit tcp any host 192.168.1.180 Additional Information: Phase: 4 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 5 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 6 Type: NAT Subtype: rpf-check Result: ALLOW Config: object network console nat (inside,outside) static x.x.223.124 Additional Information: Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 2958, packet dispatched to next module Result: input-interface: outside input-status: up input-line-status: up output-interface: inside output-status: up output-line-status: up Action: allow
However, when I perform external ping (ping allowed on all interfaces of ASA) or try to check the port 22 - I get failures, despite the ASA external interface being happy:
--- PING x.x.223.123 (x.x.223.123) 56(84) bytes of data. --- 64 bytes from x.x.223.123: icmp_seq=1 ttl=244 time=37.8 ms 64 bytes from x.x.223.123: icmp_seq=2 ttl=244 time=38.1 ms 64 bytes from x.x.223.123: icmp_seq=3 ttl=244 time=36.8 ms 64 bytes from x.x.223.123: icmp_seq=4 ttl=244 time=38.1 ms --- x.x.223.123 ping statistics --- packets transmitted 4 received 4 packet loss 0 % time 3005 ms --- Round Trip Time (rtt) --- min 36.880 ms avg 37.753 ms max 38.171 ms mdev 0.518 ms
But neither of the NAT'ed devices:
--- PING x.x.223.124 (x.x.223.124) 56(84) bytes of data. --- --- x.x.223.124 ping statistics --- packets transmitted 9 received 0 packet loss 100 % time 8316 ms
When I check the NAT statistics I can see successful hits, but nothing comes back:
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static R1 x.x.223.125
translate_hits = 0, untranslate_hits = 122
2 (inside) to (outside) source static console x.x.223.124
translate_hits = 0, untranslate_hits = 236
On the flipside, when pinging out from R1 - no translate hist, but this isn't the case for the console (although in various attempts I had seen a hit of two on R1 as well):
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static R1 x.x.223.125
translate_hits = 0, untranslate_hits = 127
2 (inside) to (outside) source static console x.x.223.124
translate_hits = 5, untranslate_hits = 246
What this makes me think is that somehow the route back is not working from the external devices to ASA, via respectively the default gateway on the console (no routing enabled) or via the default route on R1
R1 - static route configured to point back to 10.99.99.1 (and rest either directly connected or learned via egirp). However, I cannot ping anything externally. All well in all the other networks.
Gateway of last resort is 10.99.99.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.99.99.1
10.0.0.0/8 is variably subnetted, 12 subnets, 3 masks
C 10.0.10.0/30 is directly connected, Serial0/1/0
L 10.0.10.1/32 is directly connected, Serial0/1/0
D 10.0.20.0/30 [90/2681856] via 10.0.30.2, 00:51:39, Multilink1
[90/2681856] via 10.0.10.2, 00:51:39, Serial0/1/0
C 10.0.30.0/30 is directly connected, Multilink1
L 10.0.30.1/32 is directly connected, Multilink1
C 10.0.30.2/32 is directly connected, Multilink1
C 10.5.1.0/24 is directly connected, Loopback1
L 10.5.1.1/32 is directly connected, Loopback1
D 10.5.2.0/24 [90/2297856] via 10.0.10.2, 00:51:39, Serial0/1/0
D 10.5.3.0/24 [90/1468928] via 10.0.30.2, 00:51:39, Multilink1
C 10.99.99.0/30 is directly connected, FastEthernet0/1
L 10.99.99.2/32 is directly connected, FastEthernet0/1
D 192.168.1.0/24 [90/30720] via 10.99.99.1, 00:51:39, FastEthernet0/1
The console has default gateway back to the ASA interface as well:
Default gateway is 192.168.1.181 Host Gateway Last Use Total Uses Interface ICMP redirect cache is empty
Lastly, I can ping to the respective endpoint from the ASA - outside, internal and DMZ. I have a feeling that I am missing something self-evident, but after a considerable amount of googling and researching I can't come up with a sensible answer. I tried to point the routes/gateways to the external addresses on the devices, but this didn't yield any positive results and didn't feel 'right' as ASA should be separating these networks.
While it's not the core of my study, with CCNA being the main focus I was hoping to have remote access to the lab as I can control it's power remotely and could well log in and practice while remote. Any help appreciated - I can also provide further detail or troubleshooting as needed while continuing my search for the answer to this particular problem.
I did check the packets stats on interfaces on both console and router but can't usefully determine whether they receive the few test packets from the out given the external traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 05:06 AM
Hi,
Your NAT for R1 specifies it is on the inside interface, it is on the DMZ interface so the NAT statement needs to reflect this i.e. nat (dmz,outside) static x.x.x.x
object network R1 host 10.99.99.2 nat (inside,outside) static x.x.223.125
Can you provide a packet-tracer for R1 for SSH?
Joel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 05:15 AM
Hi Joel,
just a quick note - this post is a duplicate and most answers I a had are there: https://community.cisco.com/t5/firewalls/routing-across-asa-nat/m-p/3724964
However, your observation is valid - and the mistake was there. I'll post an answer in a moment; just re-doing the config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 05:24 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide