- Cisco Community
- Technology and Support
- Security
- Network Security
- Routing traffic and setting rules 101
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 08:57 AM - edited 03-11-2019 02:06 PM
I have been at this for days and still can not seem to grasp why it will not work for me. First things first...
Layout of my network:
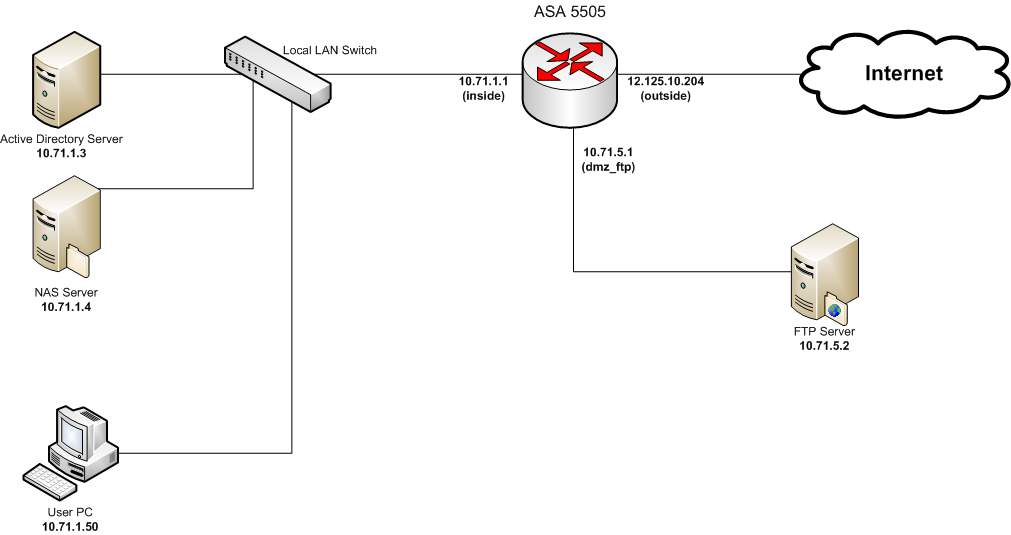
Current Config:
ASA Version 7.2(4)
!
hostname ACS-000-ROU2
domain-name ACS-ATLANTA.LOCAL
enable password xxxxxxxxxxxxxxxx encrypted
passwd xxxxxxxxxxxxxxxxx encrypted
names
name 10.71.1.3 ACS-000-ADS1
name 10.71.5.2 ACS-000-FTP1
name 10.71.1.0 ACS_Atlanta_LAN
name 10.71.5.0 ACS_FTP_DMZ
name 12.125.10.192 Public_Internet_Subnet
name 10.71.5.1 Router_FTP_DMZ_IP
name 12.125.10.206 PublicFTPIP
name 12.125.10.204 PublicRouterIP
name 10.71.1.1 Router_ACS_LAN_IP
!
interface Vlan1
description ACS Atlanta LAN
nameif inside
security-level 100
ip address Router_ACS_LAN_IP 255.255.255.0
ospf cost 10
!
interface Vlan11
description Outside - Public internet
nameif outside
security-level 0
ip address PublicRouterIP 255.255.255.224
ospf cost 10
!
interface Vlan21
description ACS Atlanta FTP DMZ
nameif dmz_ftp
security-level 100
ip address Router_FTP_DMZ_IP 255.255.255.0
ospf cost 10
!
interface Ethernet0/0
switchport access vlan 11
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 21
!
interface Ethernet0/3
switchport access vlan 31
shutdown
!
interface Ethernet0/4
switchport access vlan 31
shutdown
!
interface Ethernet0/5
switchport access vlan 31
shutdown
!
interface Ethernet0/6
switchport access vlan 31
shutdown
!
interface Ethernet0/7
switchport access vlan 31
shutdown
!
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns domain-lookup inside
dns domain-lookup dmz_ftp
dns server-group DefaultDNS
name-server ACS-000-ADS1
domain-name ACS-ATLANTA.LOCAL
object-group icmp-type debug_network
description Pings, Traceroutes, Etc...
icmp-object echo
icmp-object echo-reply
icmp-object time-exceeded
icmp-object traceroute
icmp-object unreachable
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_TCP_1 tcp
port-object eq domain
port-object eq www
object-group service rdp tcp
description Remote Desktop Protocall
port-object eq 3389
access-list dmz_ftp_access_in extended permit icmp any any
access-list dmz_ftp_access_in extended permit icmp any any object-group debug_netwrk
access-list dmz_ftp_access_in extended permit ip any any
access-list dmz_ftp_access_in extended permit tcp ACS_FTP_DMZ 255.255.255.0 host Ruter_FTP_DMZ_IP eq domain inactive
access-list inside_access_in extended permit icmp any any
access-list inside_access_in extended permit icmp any any object-group debug_netwok
access-list inside_access_in extended permit ip any any
access-list inside_access_in extended permit object-group TCPUDP ACS_Atlanta_LAN 25.255.255.0 any eq www
access-list inside_access_in extended permit object-group TCPUDP ACS_Atlanta_LAN 25.255.255.0 any eq domain
access-list inside_access_in extended permit icmp ACS_Atlanta_LAN 255.255.255.0 an object-group debug_network inactive
access-list outside_access_in remark new - ftp access to dmz
access-list outside_access_in extended permit tcp any host PublicFTPIP eq ftp inacive
access-list outside_access_in remark new - Remote Desktop Access
access-list outside_access_in extended permit tcp any host PublicFTPIP object-grou rdp inactive
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu dmz_ftp 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-524.bin
no asdm history enable
arp timeout 14400
global (inside) 1 interface
global (outside) 1 interface
nat (inside) 1 ACS_Atlanta_LAN 255.255.255.0
static (inside,dmz_ftp) ACS_Atlanta_LAN ACS_Atlanta_LAN netmask 255.255.255.0
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
access-group dmz_ftp_access_in in interface dmz_ftp
route outside 0.0.0.0 0.0.0.0 12.125.10.193 1
!
router rip
passive-interface outside
version 2
no auto-summary
!
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
aaa authentication ssh console LOCAL
http server enable
http ACS_Atlanta_LAN 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
telnet timeout 5
ssh scopy enable
ssh ACS_Atlanta_LAN 255.255.255.0 inside
ssh timeout 60
console timeout 0
username Administrator password xxxxxxxxxxxx encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
: end
Issue:
I'm currently trying to get my DMZed FTP server to be able to talk to the Local LAN (inside) allowing just IMCP (pinging). I have tried many many configs and nothing I do seems to be working. I think it has something to do with the NAT rules but not 100% positive. Any ideas?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 08:23 PM
Since your inside and dmz interfaces are set for the same security level, wouldn't you need to run the 'same-security-traffic permit inter-interface' command to allow the traffic to pass?
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 09:09 AM
Hi Arvo,
You would need the following:
static (inside,dmz_ftp)
nat (dmz_ftp) 2 0.0.0.0 0.0.0.0
global (inside) 2 interface
if this still doesn't work then, take th output of :
packet-tracer input dmz_ftp icmp
also you would need a route :
route inside 0.0.0.0 0.0.0.0
Hope this helps,
Thanks,
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 09:19 AM
Varun
static (inside,dmz_ftp)
that is actually in there, the config is just using names in the static.
route inside 0.0.0.0 0.0.0.0
the 10.71.1.x is directly connected so it wouldn't need a route
nat (dmz_ftp) 2 0.0.0.0 0.0.0.0
global (inside) 2 interface
can you explain this for my clarification because as i asked in the other thread, why do you need this as you don't need to nat internet addresses coming in from outside to either a dmz or the inside.
Many thanks
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 09:52 AM
Jon,
Was that a question for Varun?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 09:53 AM
Arvo
Yes it was.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 08:23 PM
Since your inside and dmz interfaces are set for the same security level, wouldn't you need to run the 'same-security-traffic permit inter-interface' command to allow the traffic to pass?
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 09:39 AM
Opps!!! I didn't mean for the dmz_ftp to be security level 100
I ment to have it at 50... But I was trying to avoid depending on any of the security levels for rules... The ASDM removed the rules allowing the interfaces to talk to the lower security interfaces as soon as I set up my first rule anyway... :/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 09:44 AM
Creggerd wrote:Since your inside and dmz interfaces are set for the same security level, wouldn't you need to run the 'same-security-traffic permit inter-interface' command to allow the traffic to pass?
Sent from Cisco Technical Support iPad App
Credderd,
When I add that rule though I now get a new deny message...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 02:23 PM
Ok so an update... I got all of the issues above worked out thanks to creggerd's comment.
I found out that if both the inside and dmz are the same security level then you MUST use...
"same-security-traffic permit inter-interface"
...to allow the traffic to flow from the interfaces. In my case I ended up NOT using that setting and simply setting the dmz vlan to security level 50 and keeping the inside at 100. That along with the nat rule...
static (inside,dmz_ftp) 10.71.1.0 10.71.1.0 netmask 255.255.255.0
...My traffic started flowing nicely!
Now on to something else... Same config but I have an issue with my security rules... I have NO rules at all in the security policy area yet I can go strait through the router with my FTP server (10.71.5.2) and browse a share on my AD Server (10.71.1.3). The funny thing is I can control traceroutes, pings, dns, http (or so it seems at least) traffic by creating rules to allow that type of traffic. When I delete those rules the traffic is no longer aloud through (this is what I expect). But for some reason it lets windows domain shares have all the traffic it wants...
Ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 02:32 PM
Actually I found out that problem too LOL... I had other interfaces on those two machines allowing me to remote connect without issues while I was configuring my router remotely...
Everything seems to be working as it should now. Thanks for all your help guys!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 06:41 PM
Glad I was able to help!
Sent from Cisco Technical Support iPhone App
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
