- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: send alarm cisco asa 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
send alarm cisco asa 5510
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2011 04:05 AM - edited 03-11-2019 01:20 PM
Hi,
I have a cisco asa 5510.
I am doing attack a my firewall, using namp. I am seeing in the log the attack but i like that firewall send only alarm of attack by email or nagios. I have active email with warning and i received very much email.....
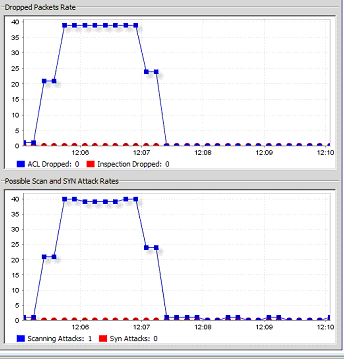
I observed that graph show attack, but not ip of attacker, is possible that cisco asa show the ip too ?
The log show scanning with nmap but not shunning IP and not send alarm. How i can send alarm ?
![]()
The graph no show ip, it's possible show it
threat-detection scanning-threat shun except ip-address X.X.X.X 255.255.255.0
threat-detection scanning-threat shun duration 3600
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2011 04:37 AM
Hi Emilio,
If you could show me your logging configuration, then i can tell you the exact commands that need to be configured.
However, primarily, you need to see to it that the syslog 401002 is in the logging list. By default the syslog is logged at level 4.
Here is the description for syslog 401002:
Error Message %ASA-4-401002: Shun added: IP_address IP_address port port
Explanation A shun command was entered, where the first IP address is the shunned host. The other addresses and ports are optional and are used to terminate the connection if available.
Hope this helps.
-Shrikant
P.S.: Please mark the question as answered if it has been resolved. Do rate helpful posts. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2011 11:29 PM
Hi,
Logging configuration
logging enable
logging timestamp
logging list errores level errors
logging buffer-size 32768
logging buffered warnings
logging trap warnings
logging asdm warnings
logging from-address xxxxx@xxxxxx
logging recipient-address xxxxx@jxxxxxx level errors
logging host Interface-outside 10.xx.xx.xx
logging message 605004 level warnings
The firewall no shunning host, only detect scanning, and
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2011 02:17 PM
Hi,
Do you need more information about my service request?
I am looking forward for you reply
Regards
Emilio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2011 12:22 PM
Hi Emilio,
I was wrong with the syslog I mentioned earlier. That syslog was for when "shun
The syslog you should be looking out for is 733102
Error Message %ASA-4-733102:Threat-detection adds host %I to shun list
Explanation This message indicates that a host has been shunned by the threat detection engine. When the threat-detection scanning-threat shun command is configured, the attacking hosts will be shunned by the threat detection engine.
Now, as to why the host is not being shunned, you can check the following:
Do "show run all | in scanning" to get the scanning threat rate parameters set on the ASA.
Enable "threat-detection statistics host".
Note: this command can effect the performance of the ASA in a high load environment. So make sure you disable it once you are done with it.
Let the ASA collect statistics for the attacking host for some time.
You can now view the statistics for the attacker by doing: "show threat-detection statistics host
host exceed the scanning threat rate parameters or not. Unless it exceeds that it won't be shunned.
You can go ahead and tweak the parameters for the scanning rate with the command:
threat-detection rate scanning-threat rate-interval (Burst-rate duration is 1/30th of the rate-interval)
(Make sure you remove the earlier configured scanned rates, just in case)
If the ASA shuns the attacker, you can view it under "show threat-detection shun".
Hope this helps.
-Shrikant
P.S.: Please mark the question as answered, if it ha been resolved. Do rate helpful posts. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2011 01:10 PM
Hi,
The steps which you explain before have been made by me.
I need send an email or trap when an attack happens. How to get it? Could you explain to me what steps I have to make, please?
Do you need the configuration file of my firewall?
Regards
Emilio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2011 01:23 PM
Hi Emilio,
Try the following:
logging message 733102 level 0
logging mail 0
logging from-address aaaa@bbbb.com
logging recipient-address xxxx@yyyy.com level 0
smtp-server
This way you will get alerts on xxxx@yyyy.com whenever the syslog 733102 is generated. The from address in the email will be aaaa@bbbb.com
Hope this helps.
-Shrikant
P.S.: Please mark the question as answered if it has been resolved. Do rate helpful posts. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2011 02:17 AM
I tested your configuration and it doesn’t work properly
I attach you the configuration file and loggin.

logging enable
logging timestamp
logging list errores level errors
logging buffer-size 32768
logging buffered informational
logging trap warnings
logging asdm warnings
logging mail emergencies
logging from-address xxxx@xxxx
logging recipient-address xxxxx@xxxxx level emergencies
logging host AAAA X.X.X.X
logging message 733102 level emergencies
logging message 605004 level warnings
smtp-server X.X.X.X
Launch nmap (Scanning)

Do you need more information about my service request?
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2011 06:17 AM
Hi Emilio,
I thought you needed an email alert when a host was shunned.
If you need an alert whenever [Scanning] drop rate-l is exceeded, then please add the following command:
logging message 733100 level 0
On the ASDM, you will be able to see the syslog id for all logs that are generated. So any log you want to be alerted by email, do: logging message
Hope this helps.
-Shrikant
P.S.: Please mark the question as answered if it has been resolved. Do rate helpful posts. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2011 02:04 AM
That's right, thank you very much, but how can i know the ip of attacker?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2011 02:40 PM
Hi,
Do you need more information about my service request?
I am looking forward for you reply
Regards
Emilio
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
