- Cisco Community
- Technology and Support
- Security
- Network Security
- SSH & HTTPS issue on Firepower 4100 chassis management interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2019 12:31 PM - edited 02-21-2020 09:42 AM
Hello,
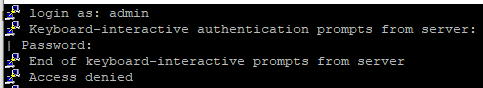
I am facing an issue with SSH/HTTPS management access on a Firepower 4100. After un-boxing the device, I consoled in and ran through the initial setup. I assigned the IP, subnet, hostname, default gateway, and IP blocks on the interface. I am able to ping the chassis mgmt interface from a laptop on the same subnet. From my laptop, I use putty to SSH in, I get a response, but using the same credentials that work for console access, it says access denied. I can confirm that my IP is in the IP block list on the private subnet of: 10.200.1.x/24.
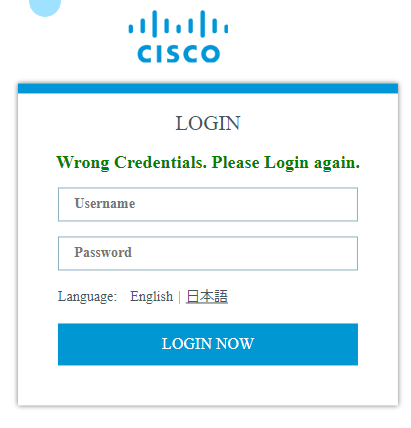
When I attempt to access the 4100 via https, I get the login page, but my credentials that work for console access, do not work for web access:
The only network connectivity that I have to the appliance is to the chassis mgmt port. I simply want SSH and/or HTTPS access. I tried creating a 2nd admin user. I have the same issue with that account.
Is there something simple that I am missing to SSH/HTTPS into the chassis management port? I'm on version 2.4(1.101). I have followed the Cisco Firepower 4100 Quick Start Guide. According to the doc, after the initial configuration, one should be able to SSH in to the appliance.
Many thanks for your assistance.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 05:29 AM - edited 02-10-2021 05:29 AM
Earlier in the same document you will find the detailed procedure on how to start from the very beginning again with the chassis - erasing the entire configuration from the console only access and build it all new, including the admin user password.
Reference:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 06:45 AM
Did you go through the guide starting with the erase-config section and including the out-of-box setup?
That should result in a "fresh" web interface. If it doesn't, you might try opening it in an incognito/private browser session.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 07:01 AM
Hello marvin
Thank you for your return
I applied an erase configuration after reboot I came on the basic configuration page I entered all the information requested after I save
As soon as I finish I have access to the HTTPS but the username and password intered show me is wrong I dont know why !!! and after few seconds the access is down.
I try with private access same problem.
Possible to connect to my equipment remotely to perform a check on my problem ?
Regards.
after a few rehearsals I lose access to the portal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 07:06 AM
Hello marvin
This is what I have to solve for the ftd application to be run
ftd-A /ssa/slot* # sh app
Application Instance:
App Name Admin State Oper State Running Version Startup Version Clus
ter State Cluster Role
---------- ----------- ---------------- --------------- --------------- ----
----------- ------------
ftd Disabled Offline 6.2.2.81 6.2.2.81 Not
ftd-A /ssa/slot/app-instance* # enable
ftd-A /ssa/slot/app-instance* # commit-buffer
Error: Update failed: [App Instance cannot be started. Please provision LogicalDevice before starting application.]
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 08:53 AM
You might want to contact TAC since they are equipped to do a WebEx session with you r to resolve your issue in real time.
If you get the Firepower Chassis manager issue resolved it is 10x easier to provision the logical device in the GUI and go fro there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 12:06 PM
Hello Marvin
Thank you for your return and information.
I know about the graphical interface it's very easy but as I told you already impossible to access the interface it works just at the start of the equipment then I lose access, How to check if an access list is blocking access ? Not option ip blocking because its empty
Another question is the physical interface of the chassis Mgmt, which is used for the firepower manager center access.
Thanks again Marvin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2021 12:30 AM
When you go through a fresh setup, as the guide notes, you will see this section:
Firepower Chassis Manager cannot be accessed if HTTPS Mgmt Access is not configured. Do you want to configure HTTPS Mgmt Access? (yes/no) [y]: y HTTPS Mgmt Access host/network address (IPv4/IPv6): 10.0.0.0 HTTPS Mgmt Access IPv4 netmask: 255.0.0.0
Be sure select "yes" and allow your relevant internal subnet(s) for https access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2021 02:36 AM
Hello Marvin
The model I'm working on is 4110, I don't have this option.
But I was able to solve the access problem by adding this command at the scope seystem/services level.
/system/services # enter ip-block 0.0.0.0 0 https
Thank you very much Marvin for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2021 05:15 AM
Hello Marvin
Others information
I was able to solve the problem of logical drive provisionning through the https interface.
now the ftd is up.
Just I specify an element for the future people that I hope will not have this problem, the message displayed under the CLI it had a relationship with the assignment of the interface of MGMT Ftd it was not properly specified I was able to resolve the problem under the graphic interface of the chassis.
Thank you all and good luck.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide