- Cisco Community
- Technology and Support
- Security
- Network Security
- SSH Terrapin Prefix Truncation Weakness
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSH Terrapin Prefix Truncation Weakness
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 05:56 AM
Good Day All,
I found a vulnerability on my 4321 router regarding this:
"The remote SSH server is vulnerable to a man-in-the-middle prefix truncation weakness known as Terrapin. This can allow a remote, man-in-the-middle attacker to bypass integrity checks and downgrade the connection's security."
Anyone information on how to resolve this is greatly appreciated.
-Alfred
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 06:00 AM
@dacruzer1 use unaffected algorithms such as AES-GCM
ip ssh server algorithm encryption aes256-gcm aes128-gcm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2024 08:21 PM
Hi Rob, We have received SSH Terrapin Prefix Truncation Weakness (CVE-2023-48795) vulnerability on AIR-CT5508-K9 IOS version AireOS 8.5.140.0. This vulnerability is associated with bug CSCwi61646. Please advise if we can ignore this vulnerability as on below link it says workaround is Not Available or Not Applicable. Or kindly suggest for the FIX.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 06:50 AM
adding to other comment check also below CVE :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 06:52 AM
HI Rob,
I configured that line and now I am getting this error when I tried to SSH:
couldn't agree a client-to-server cipher (available: aes256-gcm, aes128-gcm)
I am using putty to ssh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:01 AM
@dacruzer1 where do you receive this error on the device when configuring or in putty when connecting? If in putty then putty might not support GCM, what version of putty? And what ciphers does it support?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:09 AM
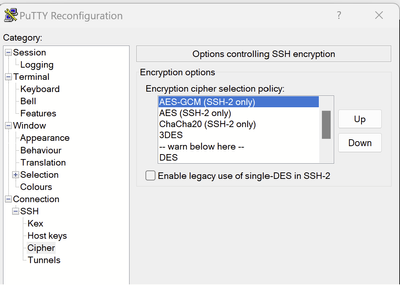
Hi Rob,
In putty, when connecting. Putty release version 0.70
It supports: AES (SSH-2 only), ChaCHa20 (SSH-2 only), Blowfish, 3DES
Is there an SSH tool that support GCM ?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:13 AM
@dacruzer1 0.70 is very old, 0.80 is the latest, download - https://www.chiark.greenend.org.uk/~sgtatham/putty/releases/0.80.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:21 AM
Hi Rob,
Downloaded and installed the latest version of putty, but still not connecting.
Putty Fatal Error:
"Selected client-to-server cipher "aes256-gcm, aes128-gcm" does not correspond to any supported algorithm"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:59 AM
Hi Rob,
It did not work, the same error...
I will need to console in and remove that line that I configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 01:39 PM
Can you post the show logging and your show ssh output ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 01:47 PM
2024-01-12 13:46:07 Looking up host "204.62.69.1" for SSH connection
2024-01-12 13:46:07 Connecting to 204.62.69.1 port 22
2024-01-12 13:46:07 We claim version: SSH-2.0-PuTTY_Release_0.80
2024-01-12 13:46:07 Connected to 204.62.69.1
2024-01-12 13:46:07 Remote version: SSH-2.0-Cisco-1.25
2024-01-12 13:46:07 We believe remote version has SSH-1 ignore bug
2024-01-12 13:46:07 We believe remote version needs a plain SSH-1 password
2024-01-12 13:46:07 We believe remote version can't handle SSH-1 RSA authentication
2024-01-12 13:46:07 Using SSH protocol version 2
2024-01-12 13:46:07 No GSSAPI security context available
2024-01-12 13:46:07 Selected client-to-server cipher "aes256-gcm,aes128-gcm" does not correspond to any supported algorithm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 07:12 AM
try latest putty 0.80 and check
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2024 03:24 PM
Hi everyone,
I ran into the same issue as @dacruzer1 has with trying to SSH to the switch after using unaffected algorithms that @Rob Ingram listed above, even with the latest version of Putty 0.80. I was able to fix that issue by using the following on the switch:
ip ssh server algorithm encryption aes256-gcm@openssh.com aes128-gcm@openssh.comI still needed to use Putty 0.80 even after I did the change.
Please let me know if what I did is the correct way or not.
Thank you,
Manwar
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide