- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: TACACS+ for Console ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 11:29 AM - edited 02-21-2020 07:25 AM
Hello all,
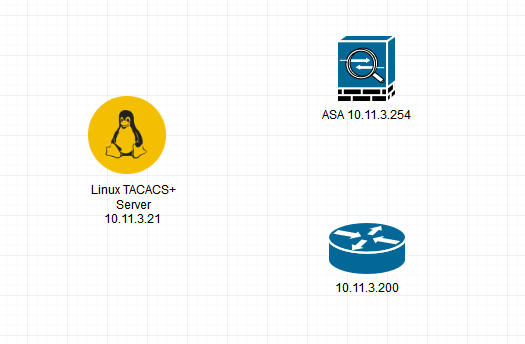
I am trying to use TACACS for authentication / authorization. My setup is shown below.
On the Router, everything works really well.
For the ASA, I can ssh, telnet and http with no issues and I am going straight to privilege level 15 (example below is ssh)
ciscoasa# show curpriv Username : theo Current privilege level : 15 Current Mode/ s : P_PRIV
but when I use the console, after logging I am in user-mode
ciscoasa> show curpriv Username : theo Current privilege level : 1 Current Mode/ s : P_UNPR
I can enter the enable password, but after that I cannot access anything, not even the show commands.
ciscoasa> enable 15 Password : ******* ciscoasa# conf t Command authorization failed
Cisco IOS
R1#show running-config | include aaa aaa new-model aaa authentication login REMOTE-LOGIN group tacacs+ local aaa authorization exec REMOTE-AUTHOR group tacacs+ local aaa authorization commands 15 REMOTE-EXEC-AUTHOR group tacacs+ local
R1#show run | include tacacs-server tacacs-server host 10.11.3.21 key Cisco123 tacacs-server key Cisco123
R1#show run | section vty line vty 0 4 authorization commands 15 REMOTE-EXEC-AUTHOR authorization exec REMOTE-AUTHOR login authentication REMOTE-LOGIN line vty 5 935 authorization commands 15 REMOTE-EXEC-AUTHOR authorization exec REMOTE-AUTHOR login authentication REMOTE-LOGIN
Cisco ASA
ciscoasa# show running-config aaa aaa authentication telnet console TACACS-Servers LOCAL aaa authentication http console TACACS-Servers LOCAL aaa authentication serial console TACACS-Servers LOCAL aaa authentication ssh console TACACS-Servers LOCAL aaa authorization command TACACS-Servers LOCAL aaa authorization exec authentication-server auto-enable aaa authentication login-history
ciscoasa# show run aaa-server aaa-server TACACS-Servers protocol tacacs+ aaa-server TACACS-Servers (Inside) host 10.11.3.21
key *****
Linux /etc/tac_plus.conf
group = network-admin {
default service = permit
login = PAM
service = exec {
priv-lvl = 15
}
user = theo {
login = PAM
member = network-admin
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 05:40 PM
Hi
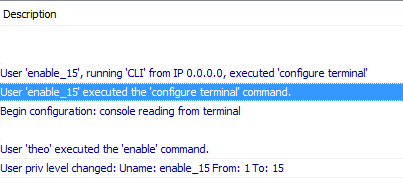
This is because you need to configure a user called enable_15 on your tacacs server.
If you take a look on your logs, you should see an authorization failed coming from that user enable_15
Thanks
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 05:40 PM
Hi
This is because you need to configure a user called enable_15 on your tacacs server.
If you take a look on your logs, you should see an authorization failed coming from that user enable_15
Thanks
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2018 01:55 AM
Perfect! That worked.
user = enable_15 {
default service = permit
service = exec {
priv-lvl = 15
}
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2018 03:17 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide