- Cisco Community
- Technology and Support
- Security
- Network Security
- Two VPN Site-to-Site Tunnels, One as a Backup to the Other
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2015 06:03 PM - edited 03-11-2019 11:39 PM
I have an ASA 5510 configured with two site-to-site tunnels: one to a main facility and the other as an alternate path to a DR site. What's the best mechanism for having one tunnel be the primary path and the second being a failover/redundant path? In this particular scenario we are NOT using dynamic routing locally as this is a stub site. So all routes identified in crypto maps take the tunnels, everything else is either directly connected or goes out to the internet. So how do I make one site preferred over the other since the crypto maps will identify the same remote networks via either path?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2015 12:34 PM
If you use backup LAN-to-LAN feature (i. e. originate-only and two peer addresses in the crypto map line) the ASA keeps only the primary tunnel up as long as Site 1 is reachable. Originate-only setting ensures that Site 2 cannot establish the tunnel until the firewall decides to activate the backup peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2015 09:07 PM
Hi Scott ,
If the VPNs are applied to a different interfaces, you can use IP SLA to track the VPN status. If they are applied on the same interface you can use the Backup LAN-to-LAN feature of the ASA.
Examples below:
IP SLA
http://www.networkgalaxy.org/2013/06/ipsec-vpn-as-backup-for-point-to-point.html
https://sites.google.com/site/amitsciscozone/home/ipsec/ha-for-ipsec-vpn-using-ip-sla
LAN-to-LAN
http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/command/reference/cmd_ref/c5.html#wp2238363
Otherwise crypto maps with the same interesting traffic on the same interface is not supported.
hope it helps
-Randy-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2015 06:42 AM
Randy -
The information you provided does help get me going in the right direction, but I'd like to clarify a couple of things.
The situation is an ASA with a single interface on a single internet connection, and I'm wondering if the IP SLA command can be used to track the availability of the public IP address of the peer? No sense in having the tunnel being used if the peer is down. If so, I'm not sure I understand how the firewall would fail over to using the second Site-to-Site VPN connection if the sla monitor detects a failure? The example given is overly simplistic with a single route statement. I cannot do that as my networks are not summarized. Would I then have to supply individual route statements with the track command? That would be pretty ugly.
As for the backup LAN-to-LAN scenario, I would make the primary link bi-directional. But I don't understand how configuring the link to the other site as originate-only helps at all since the availability of the connection to the backup site is independent of the availability of the connection to the primary site. In other words, this backup should kick in only when the connection to the primary site is down due to issues at the primary site directly. If you configure one side as originate-only, the other site would be able to answer regardless if the primary site is down. So wouldn't that bring the tunnel up and we'd have both operating simultaneously? With a single internet connection at the site with two S2S VPNs, if that goes down no backup is going to work anyways. I've attached a simple diagram of the network.
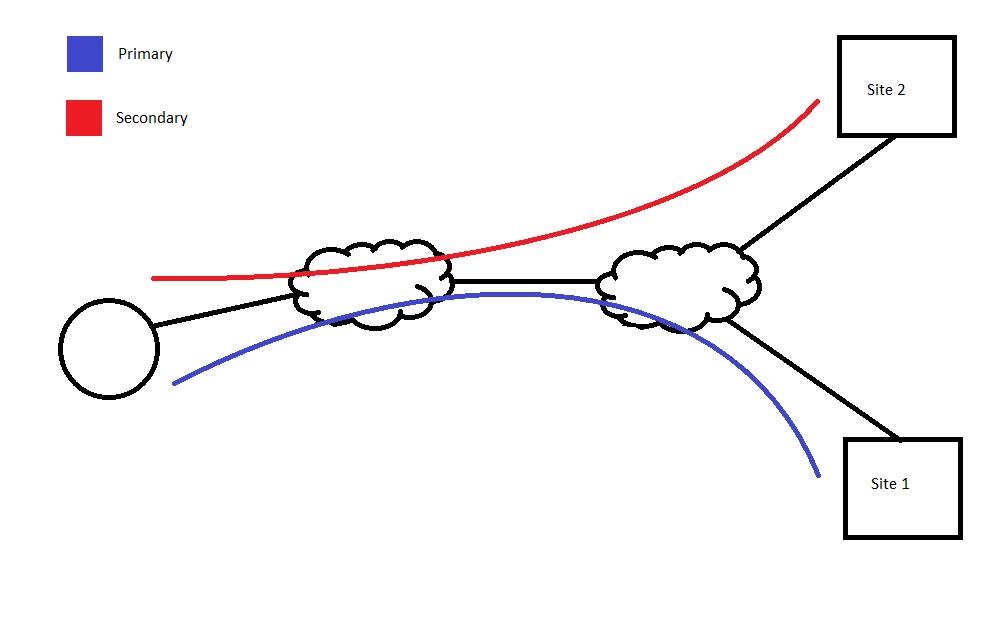
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2015 12:34 PM
If you use backup LAN-to-LAN feature (i. e. originate-only and two peer addresses in the crypto map line) the ASA keeps only the primary tunnel up as long as Site 1 is reachable. Originate-only setting ensures that Site 2 cannot establish the tunnel until the firewall decides to activate the backup peer.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
