- Cisco Community
- Technology and Support
- Security
- Network Security
- UDP Port forward on ASA 5510 9.0 (4) causes "ERROR: NAT unable to reserve ports."
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2014 05:28 PM - edited 03-11-2019 09:56 PM
I am trying for forward UDP port 43139 to an IP on the inside, but whenever I do the forward, I get the error "ERROR: NAT unable to reserve ports."
The commands I enter are as follows:-
object network AQUEEB_UTORRENT_UDP_43139
host 10.55.17.2
nat (inside,outside) static interface service udp 43139 43139
As soon as I hit enter on the above nat statement, I get "ERROR: NAT unable to reserve ports." Copy and paste of the way I enter commands is:-
ASA-5510-FW-02(config)# object network AQUEEB_UTORRENT_UDP_43139
ASA-5510-FW-02(config-network-object)# host 10.55.17.2
ASA-5510-FW-02(config-network-object)# nat (inside,outside) static interface service udp 43139 43139
ERROR: NAT unable to reserve ports.
My show ver :-
ASA-5510-FW-02(config-network-object)# show ver
Cisco Adaptive Security Appliance Software Version 9.0(4)
Device Manager Version 7.3(1)
Compiled on Wed 04-Dec-13 08:33 by builders
System image file is "disk0:/asa904-k8.bin"
Config file at boot was "startup-config"
ASA-5510-FW-02 up 2 days 17 hours
Hardware: ASA5510, 1280 MB RAM, CPU Pentium 4 Celeron 1600 MHz,
Internal ATA Compact Flash, 256MB
BIOS Flash AT49LW080 @ 0xfff00000, 1024KB
Any help is appreciated. My config below.
ASA-5510-FW-02# show run
: Saved
:
ASA Version 9.0(4)
!
terminal width 200
hostname ASA-5510-FW-02
enable password XXXXXXXXXXXXXX
passwd XXXXXXXXXXXXXXX encrypted
names
ip local pool 10.55.17.180-199_POOL 10.55.17.180-10.55.17.199 mask 255.255.255.0
!
interface Ethernet0/0
nameif outside
security-level 0
ip address dhcp setroute
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 10.55.17.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 172.16.16.6 255.255.255.0
!
banner motd
banner motd
banner motd *********************************************************
banner motd * This system is for authorized personnel ONLY. *
banner motd * Only specifically authorized personnel *
banner motd * may log into and use this system. *
banner motd *********************************************************
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns domain-lookup outside
dns server-group DefaultDNS
name-server 8.8.8.8
name-server 8.8.4.4
same-security-traffic permit intra-interface
object network vpn_nat
range 10.55.17.180 10.55.17.199
object network AQUEEB_UTORRENT_UDP_43139
host 10.55.17.2
object-group network HOME-NETWORKS
description THIS GROUP DEFINES ALL NETWORKS THAT ARE AT HOME
network-object 10.55.17.0 255.255.255.0
object-group network DC-NETWORKS
description THIS GROUP DEFINES ALL NETWORKS THAT I WANT TO ACCESS AT THE DC
network-object 10.55.151.0 255.255.255.128
network-object 10.55.151.128 255.255.255.128
network-object 10.55.24.0 255.255.255.0
network-object 10.55.12.128 255.255.255.128
network-object 10.55.12.0 255.255.255.128
network-object 10.16.32.0 255.255.255.0
network-object 10.55.10.30 255.255.255.255
network-object 10.55.10.0 255.255.255.248
network-object 10.55.16.0 255.255.255.0
object-group service TCP_54325 tcp
description THIS DEFINES TCP PORT FOR VNC FORWARDING
port-object eq 54325
access-list CRYPTOMAP-ACL-MATCH-FROM-HOME-TO-DC extended permit ip object-group HOME-NETWORKS object-group DC-NETWORKS
access-list inside_nat0_outbound extended permit ip object-group HOME-NETWORKS object-group DC-NETWORKS
access-list HOME_WIRED_NETWORK_ACL standard permit 10.55.17.0 255.255.255.0
access-list HOME_WIRED_NETWORK_ACL standard permit host 10.55.151.140
access-list HOME_WIRED_NETWORK_ACL standard permit host 192.186.208.231
access-list outside_in extended permit tcp any host 10.55.17.2 eq 43139 log
access-list outside_in extended permit udp any host 10.55.17.2 eq 43139 log
access-list outside_in extended permit tcp any host 10.55.17.2 eq 54325 log
pager lines 24
logging enable
logging buffer-size 65550
logging buffered debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,any) source static HOME-NETWORKS HOME-NETWORKS destination static DC-NETWORKS DC-NETWORKS
nat (inside,outside) source dynamic HOME-NETWORKS interface description Nat ONLY INSIDE IP's
nat (inside,outside) source static HOME-NETWORKS HOME-NETWORKS destination static HOME-NETWORKS HOME-NETWORKS no-proxy-arp route-lookup
!
object network vpn_nat
nat (outside,outside) dynamic interface
access-group outside_in in interface outside
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 172.16.16.0 255.255.255.0 management
http 10.55.17.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CRYPTOMAP-MAP-TO-CREATE-TUNNEL-TO-DC 1 match address CRYPTOMAP-ACL-MATCH-FROM-HOME-TO-DC
crypto map CRYPTOMAP-MAP-TO-CREATE-TUNNEL-TO-DC 1 set peer PUBLIC_IP
crypto map CRYPTOMAP-MAP-TO-CREATE-TUNNEL-TO-DC 1 set ikev1 phase1-mode aggressive
crypto map CRYPTOMAP-MAP-TO-CREATE-TUNNEL-TO-DC 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map CRYPTOMAP-MAP-TO-CREATE-TUNNEL-TO-DC interface outside
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
subject-name CN=172.16.16.6,CN=ASA-5510-FW-02
crl configure
crypto ca trustpoint AnyConnect_Trustpoint_CA
enrollment self
subject-name CN=ASA_5510_FW02,OU=HOME,C=CA,St=ON,L=MISSISSAUGA,EA=MYEMAIL@gmail.com
keypair RSA_2048_KeyPairName
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate e52f123e
DELETED
quit
crypto ca certificate chain AnyConnect_Trustpoint_CA
certificate a8abf253
DELETED
quit
crypto isakmp identity address
crypto ikev1 enable outside
crypto ikev1 am-disable
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh 192.168.0.0 255.255.255.0 inside
ssh 10.55.17.0 255.255.255.0 inside
ssh timeout 60
console timeout 0
management-access inside
dhcp-client client-id interface outside
dhcpd option 150 ip 10.55.151.140
!
dhcpd address 10.55.17.200-10.55.17.254 inside
dhcpd dns 8.8.8.8 8.8.4.4 interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 206.108.0.131 source outside prefer
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 management
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 management vpnlb-ip
webvpn
enable outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-3.1.05178-k9.pkg 1
anyconnect enable
group-policy AQUEEB_GROUP_POLICY internal
group-policy AQUEEB_GROUP_POLICY attributes
wins-server none
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value HOME_WIRED_NETWORK_ACL
default-domain none
address-pools value 10.55.17.180-199_POOL
username aqueeb password XXXXXXXX encrypted privilege 15
username aqueeb attributes
vpn-group-policy AQUEEB_GROUP_POLICY
tunnel-group PUBLIC_IP type ipsec-l2l
tunnel-group PUBLIC_IP ipsec-attributes
ikev1 pre-shared-key *****
isakmp keepalive threshold 10 retry 3
tunnel-group AQUEEB_TUNNEL_GROUP type remote-access
tunnel-group AQUEEB_TUNNEL_GROUP general-attributes
default-group-policy AQUEEB_GROUP_POLICY
tunnel-group AQUEEB_TUNNEL_GROUP webvpn-attributes
group-alias AQUEEB_TUNNEL_GROUP_ALIAS enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:6d17588980876334558e568c0dde3ba7
: end
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2014 09:29 PM
Hi,
You don't have any port forwarding configured on the ASA device at this moment but this NAT statement might be using this port(43139) on the Interface Ip for traffic going to the internet using the NAT statement:-
nat (inside,outside) source dynamic HOME-NETWORKS interface description Nat ONLY INSIDE IP's
If you check:-
show xlate global <IP Address of Outside interface>
You would see an entry present for this port(43139).
To use the Static PAT , you would have to clear the Xlate first and then apply this NAT.
Thanks and Regards,
Vibhor Amrodia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2014 07:14 PM
Hi,
It seems that there is already a connection built on this port and that's why the you are not able to port forward this port.
You can check that using:-
show conn port 43139-43140
Also , is there any specific reason why we are forwarding this port ?
Thanks and Regards,
Vibhor Amrodia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2014 08:17 PM
Hi Vibhor,
Thank you for your reply. You are right, I just checked and there are connections to port 43139. Can you please tell me in which part of my config I have configured port forwarding???
Thank you very much!
Kind regards,
Aqueeb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2014 09:29 PM
Hi,
You don't have any port forwarding configured on the ASA device at this moment but this NAT statement might be using this port(43139) on the Interface Ip for traffic going to the internet using the NAT statement:-
nat (inside,outside) source dynamic HOME-NETWORKS interface description Nat ONLY INSIDE IP's
If you check:-
show xlate global <IP Address of Outside interface>
You would see an entry present for this port(43139).
To use the Static PAT , you would have to clear the Xlate first and then apply this NAT.
Thanks and Regards,
Vibhor Amrodia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2014 03:43 AM
Hi Vibhor,
Again, you nailed the issue. I am able to enter the NAT statement now, I just have to be a little quick about it. As soon as I do the clear xlate command I need to enter the nat statement.
But port forwarding is still not working, attached screenshot.
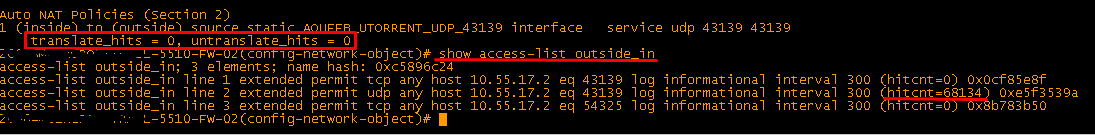
Any ideas?
Kind regards,
Aqueeb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2014 04:58 AM
Hi,
So , you have the rule on the ASA device that you need to get the traffic working ?
If yes , check the packet tracer if you see the flow as per the requirement.
If yes , move to capturing the real time traffic.
Thanks and Regards,
Vibhor Amrodia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2014 01:19 PM
The rule that I have on the ASA device to get the traffic working is the access-list applied to the interface outside. Basically the following two lines.
access-group outside_in in interface outside
access-list outside_in extended permit udp any host 10.55.17.2 eq 43139 log
How do I check the packet tracer??
If I capture data in real time what do I check for?
Thanks once again!
Aqueeb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2014 03:49 AM
Hi,
You can try this packet Tracer:-
packet input outside udp <External Source Ip on the internet> 45657 <Outside interface IP> 43139 det
For the captures , you just need to verify that the ASA device is passing the traffic through as this is UDP traffic , we would not be able to find much.
For more information on captures:-
https://supportforums.cisco.com/document/69281/asa-using-packet-capture-troubleshoot-asa-firewall-configuration-and-scenarios
Let me know if you have any further queries.
Thanks and Regards,
Vibhor Amrodia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2014 08:36 AM
Thanks again for all your help.
The reason why port forwarding was not working was because my dynamic nat rule for my inside network was in Section 1. I moved it to section 3 and port forwarding started working.
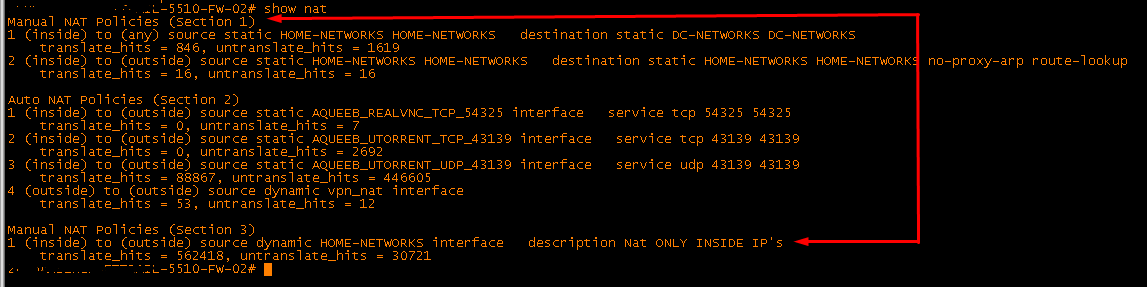
Aqueeb
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
