- Cisco Community
- Technology and Support
- Security
- Network Security
- Unable to access(Ping, http/s) to some google IPs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2019 01:18 AM - edited 02-21-2020 09:03 AM
Hi all
we use G Suite for work. We have Cisco ASA with firepower, We can access some google services, but we cant access the google services on 172.217.170.0 range, we can only access services on google 216.58.223.0 range. i checked the dns and its correct.. i checked the firewall rules and firepower, nothing is blocked. ISP says they are not blocking anything either. any idea what could be blocking the 172.217.170.0 range? Please assist
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2019 08:35 AM
dst ip/id=172.0.0.0, mask=255.0.0.0
You have 172.0.0.0/8 under LOCAL_LANS, causing it to go through your VPN. You might want to change that to at least a 172.16.0.0/12.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2019 03:11 AM
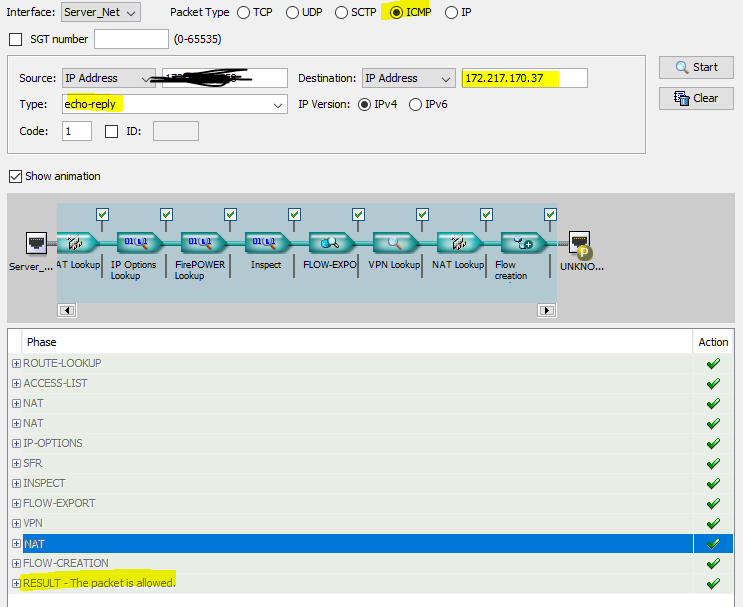
can you run this command and share the output from the cli
packet tracer input Server_Net icmp 192.168.1.1 8 0 172.217.170.37 detail
from your earlier output the packet is going out and seem that ASA is showing its working.
could you please make sure this is setup properly
policy-map global_policy
inspect icmp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2019 08:00 AM
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 45.140.4.40 using egress ifc outside
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group Server_Net_access_in in interface Server_Net
access-list Server_Net_access_in remark inside whitelist
access-list Server_Net_access_in extended permit ip object-group inside_mpls_whitelist_blanket any
object-group network inside_mpls_whitelist_blanket
network-object 192.168.40.0 255.255.255.0
network-object 172.31.0.0 255.255.255.0
network-object 192.168.45.32 255.255.255.224
network-object object OBJ-172.31.40.0-24
network-object object VLAN_110
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac8b29390, priority=13, domain=permit, deny=false
hits=55911369, user_data=0x2aaabdb03a40, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.40.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=any
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (Server_Net,outside) source static LOCAL_LANS LOCAL_LANS destination static LOCAL_LANS LOCAL_LANS no-proxy-arp route-lookup
Additional Information:
Static translate 192.168.40.39/0 to 192.168.40.39/0
Forward Flow based lookup yields rule:
in id=0x2aaac89f3cd0, priority=6, domain=nat, deny=false
hits=11300731, user_data=0x2aaac89aad40, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.40.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=172.0.0.0, mask=255.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=outside
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac77ec9d0, priority=0, domain=nat-per-session, deny=true
hits=8118746480, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac84d1fc0, priority=0, domain=inspect-ip-options, deny=true
hits=8003902666, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=any
Phase: 6
Type: SFR
Subtype:
Result: ALLOW
Config:
class-map sfr
match access-list sfr_redirect
policy-map global_policy
class sfr
sfr fail-open
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac9873920, priority=71, domain=sfr, deny=false
hits=280884612, user_data=0x2aaac99ed250, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=any
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac84d17d0, priority=66, domain=inspect-icmp-error, deny=false
hits=3565155285, user_data=0x2aaac84d1480, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=any
Phase: 8
Type: FLOW-EXPORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac99f1100, priority=18, domain=flow-export, deny=false
hits=3833965363, user_data=0x2aaac9e76820, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=any
Phase: 9
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac98d6c70, priority=13, domain=ipsec-tunnel-flow, deny=true
hits=3817482473, user_data=0x0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=any
Phase: 10
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (Server_Net,outside) source static LOCAL_LANS LOCAL_LANS destination static LOCAL_LANS LOCAL_LANS no-proxy-arp route-lookup
Additional Information:
Forward Flow based lookup yields rule:
out id=0x2aaac89f61f0, priority=6, domain=nat-reverse, deny=false
hits=8797542, user_data=0x2aaac8976190, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.40.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=172.0.0.0, mask=255.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=Server_Net, output_ifc=outside
Phase: 11
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 4096940090, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_sfr
snp_fp_inspect_icmp
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
Result:
input-interface: Server_Net
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2019 08:35 AM
dst ip/id=172.0.0.0, mask=255.0.0.0
You have 172.0.0.0/8 under LOCAL_LANS, causing it to go through your VPN. You might want to change that to at least a 172.16.0.0/12.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2019 10:08 AM
We changed 172.0.0.0/8 to 172.0.0.0/16. Now it works 😊
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide