- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Unable to import server certificate to FMC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unable to import server certificate to FMC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 01:12 AM - edited 02-21-2020 06:41 AM
hi
I'm trying to import server certifacate issued by our corporate CA to FMC, but i always get error "Unable to verify certificate."
In /var/log/httpd/httpsd_error_log i see errors:
[Thu Nov 09 08:59:37.040550 2017] [cgi:error] [pid 27221] [client 10.12.91.238:33111] AH01215: No such file or directory:/etc/sf/crl.conf at /usr/local/sf/lib/perl/5.10.1/SF/X509Certificates.pm line 919.: /usr/local/sf/htdocs/admin/https_cert.cgi, referer: https://fmc.isd.lamoda.tech/admin/https_cert.cgi [Thu Nov 09 08:59:37.040652 2017] [cgi:error] [pid 27221] [client 10.12.91.238:33111] AH01215: (Unable to verify certificate.) in /usr/local/sf/htdocs/admin/https_cert.cgi:163 at /usr/local/sf/lib/perl/5.10.1/SF.pm line 120.: /usr/local/sf/htdocs/admin/https_cert.cgi, referer: https://fmc.isd.lamoda.tech/admin/https_cert.cgi
I checked directory /etc/sf/ and there is no crl.conf in it.
What might be a reason?
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 06:05 AM
Which version is the FMC running ?
You might be hitting the bug CSCvf42713
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 06:50 AM
Perhaps... buy it has fixed status in 6.2.2.1 version
and i upgrade my fmc to 6.2.2.1 and this problem still exists
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2017 02:42 PM
I currently have a tac open on this myself. I too am at 6.2.2.1-73
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2018 04:07 PM
I'm running 6.2.2.1 and I am getting this error as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2018 06:43 PM
6.2.2.1 is still affected by the bug. You will need to import the certificate using the CLI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2018 07:31 AM
Thanks. I do have a ticket open with TAC but still waiting for assistance. I'm running the Threat Defense image. Is it safe to use the cli for this operation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2018 10:01 AM
Yes it is safe to perform on the CLI. I have performed on multiple customer environments without any issues.
But, if one were to arise, the certificate itself can be regenerated or set to the default and then start over.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 07:57 AM
The openssl method from the cli works. Now we are encountering an issue in that modern browsers are ignoring the common name in the cert and instead are using the subject alternative name. By default the Microsoft CA server doesn't issue certs with the san attribute set do we are trying to figure out how to accomplish this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 12:49 PM
if you need san in your cert just add it to the Attributes field when requesting the cert from Microsoft CA.
san:dns=FQN
this will add the subject alternative name
As for the cert problem all's i did was create my own key and csr using openssl got a new cert, logged into the FMC sudo to root and replaced the server.key and server.crt in the /etc/ssl directory and then restarted, this fixed the problem for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 07:25 AM
Thanks for the tip. I was able add the new cert by using this and copying the new cert over the server.crt file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2017 10:00 PM
Cisco bug CSCvg28901 matches this:
Symptom:
Certificate with Basic Constraints extension not critical will not be imported on FMC or sensor with error:
Unable to install certificate
I modified the extensions in my "server_cert" block, and changed to look like this:
#basicConstraints = CA:FALSE
basicConstraints = critical, CA:FALSE
I again signed the certificate, and this time was able to import it.
This link provides a good explanation as to why this is needed, but it seems to be related to signing with an intermediate CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 01:53 AM
How do you make basic constraints critical? Could you please explain a bit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 01:37 AM - edited 12-07-2017 01:38 AM
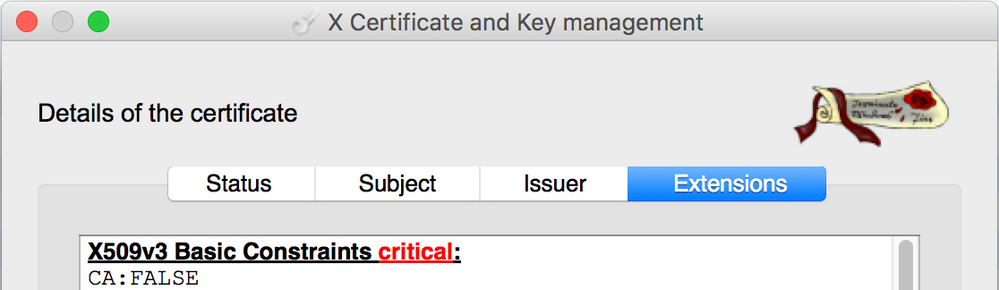
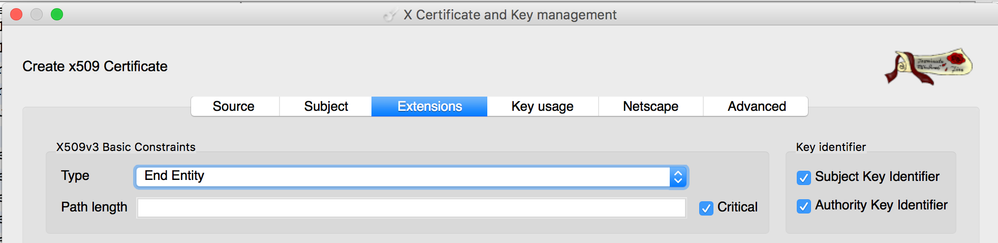
It all depends what do you use for issuing certificates. You can open your certificate in XCA, it's a free tool which allows you to work on certificates and see all the properties in graphical form.
When you import your certificate there, you can see if Basic Constraints critical or not (here, the attribute is present):
You can also right-click, then go Transform>Similar Certificate>Extensions and under Basic Constraints at the top, you will see Critical button:
This must be selected on the CA for the certificates you want to issue.
Regards,
Radek
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 10:25 AM
I'm using OpenSSL for this. In OpenSSL, I have a config file:
/root/ca/intermediate/openssl.cnf
This file has the following extension block, in which I find basicConstraints:
[ server_cert ]
# Extensions for server certificates (`man x509v3_config`).
#basicConstraints = CA:FALSE
basicConstraints = critical, CA:FALSE
nsCertType = server
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
crlDistributionPoints = <REMOVED>
authorityInfoAccess = OCSP;URI:<REMOVED>
I prepended "critical," and save the file.
When signing the CSR with OpenSSL, I used this command:
openssl ca -config intermediate/openssl.cnf -extensions server_cert -days 375 -notext -md sha256 -in intermediate/csr/fmc.mydomain.net.csr.pem -out intermediate/certs/fmc.mydomain.net.cert.pem
I was then able to import the certificate.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide