- Cisco Community
- Technology and Support
- Security
- Network Security
- Zone based firewall / IPsec VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2011 06:30 AM - edited 03-11-2019 12:29 PM
Hello,
I've remote vpn running on a 2801, now i decide to use ZBF to have some firewall feature on cisco router but, after deploy ZBF on my 2801 box i can connect but no traffic cross my internal lan.
Topology:
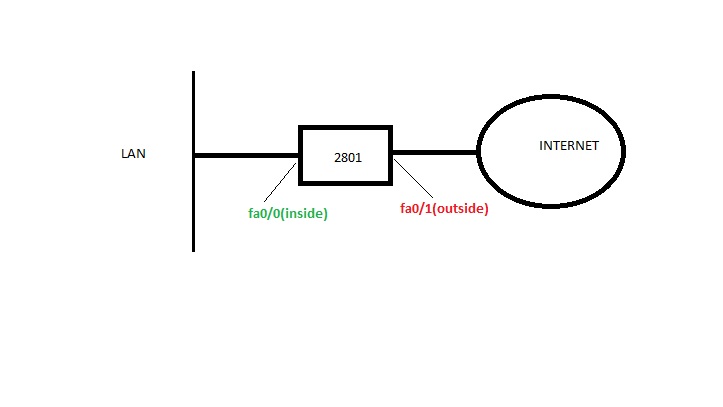
ZBF config.:
class-map type inspect match-any CHAP-1
match protocol tcp
match protocol icmp
match protocol udp
!
!
policy-map type inspect PMAP-1
class type inspect CHAP-1
inspect
police rate 8000 burst 1000
class class-default
!
zone security inside
zone security outside
zone-pair security inside-to-outside source inside destination outside
service-policy type inspect PMAP-1
*****************************************************************
interface FastEthernet0/0.32
description **** INSIDE INTERFACE ****
encapsulation dot1Q 32
ip address XX.XX.XX.XX XXX.XXX.XXX.XXX
ip access-group NON-MANAGEMENT-INSIDE_ETH in
ip nat inside
ip virtual-reassembly
zone-member security inside
no ip route-cache
interface FastEthernet0/1.10
description **** OUTSIDE INTERFACE ****
encapsulation dot1Q 110
ip address XX.XX.XXX.XX XXX.XXX.XXX.XXX
ip access-group ACL-INFRASTRUCTURE-IN in
no ip redirects
no ip unreachables
no ip proxy-arp
ip flow ingress
ip nat outside
ip virtual-reassembly
zone-member security outside
no cdp enable
*************************************************************
ROUTES
ip route 0.0.0.0 0.0.0.0 64.30.XXX.XX
ip route 1X.1X.0.0 25X.25X.XXX.0 FastEthernet0/0.32
ip route 1X.1X.2X.0 25X.25X.XXX.0 FastEthernet0/0.32
ip route 1X.1X.1X.0 25X.25X.XXX.0 FastEthernet0/0.32
********************************************************
VPN ACL
ip access-list extended IT-VPN-ACL
permit ip 1X.1X.X0.0 0.0.X.255 17X.1X.2XX.0 0.0.0.255
permit ip 1Y.1Y.Y0.0 0.0.X.255 17X.1X.2XX.0 0.0.0.255
permit ip 1Z.1Z.Z.0 0.0.X.255 172.16.255.0 0.0.0.255
PLEASE HELP!!!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2011 03:48 PM
Once you assign an interface into a zone, you would need to configure policy map for traffic in all direction where you initiate the traffic from.
Currently you have the following:
zone-pair security inside-to-outside source inside destination outside
service-policy type inspect PMAP-1
This will only allow traffic to be initiated from source: inside to destination: outside
For VPN traffic after it's being decrypted, the traffic would be initiated from source: outside to destination: inside. Hence, you would need to configure zone-pair for source: outside to destination: inside which allow the VPN traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2011 03:48 PM
Once you assign an interface into a zone, you would need to configure policy map for traffic in all direction where you initiate the traffic from.
Currently you have the following:
zone-pair security inside-to-outside source inside destination outside
service-policy type inspect PMAP-1
This will only allow traffic to be initiated from source: inside to destination: outside
For VPN traffic after it's being decrypted, the traffic would be initiated from source: outside to destination: inside. Hence, you would need to configure zone-pair for source: outside to destination: inside which allow the VPN traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2011 08:20 AM
HI Jennifer, Thanks for your response
i made the changes below but the same issue
and what u meen by permit VPN traffic is the match access-group in class-map?
class-map type inspect match-any safe-vpn-cmap
match protocol icmp
match protocol tcp
match protocol udp
match access-group name IT-VPN-ACL
!
!
policy-map type inspect safe-vpn-pmap
class type inspect safe-vpn-cmap
inspect
class class-default
!
zone security inside
zone security outside
zone-pair security safe-internalLAN-vpn source outside destination inside
service-policy type inspect safe-vpn-pmap
zone-pair security safe-vpn-internalLAN source inside destination outside
service-policy type inspect safe-vpn-pmap
!
best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2011 08:27 AM
after applying the virtual template to ouside security zone all start working
thanks!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


