- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Zone-Based Policy Firewall configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Zone-Based Policy Firewall configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 12:22 PM - edited 03-11-2019 01:34 PM
Hey folks. I need some help with my configs (I think). I have two 1811's connected in a lab using a ipsec vpn tunnel (using a switch to simulate an internet connection between them).
I am trying to configure one of the routers as a ZBPF just to allow a remote windows login (DC on the firewalled side, workstations on the other side).
I'm trying to verify that the zbpf is working, but it doesn't seem to stop anything. I had match icmp added to the class-map, but took it out to test if icmp would fail. It didn't. Basically, I don't think the firewall is working at all. Any thoughts on how I can configure this so that the policies will work between zone-pairs?
Any help would be greatly appreciated!
Here's an quick drawing:
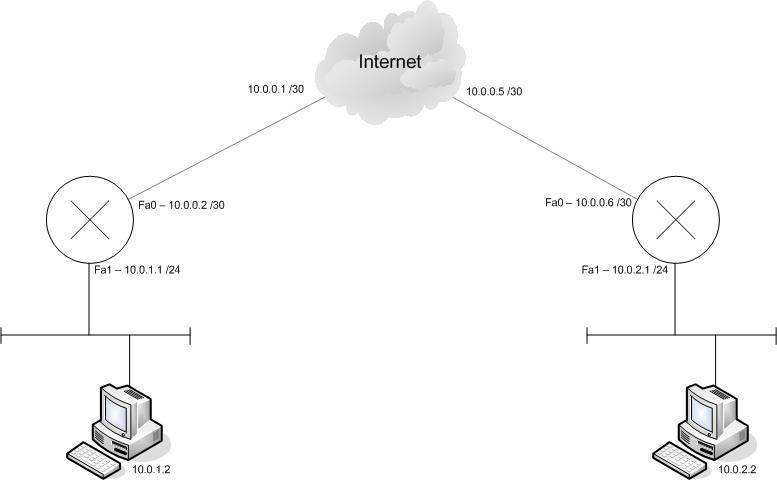
Here are the configurations:
Local router:
hostname sdc-1811-LocalLab
!
boot-start-marker
boot-end-marker
!
no aaa new-model
!
resource policy
!
ip cef
!
no ip domain lookup
!
class-map type inspect match-any Remote_VPN
match access-group 101
match protocol ldap
match protocol http
match protocol kerberos
match protocol netbios-ns
match protocol dns
!
!
policy-map type inspect zbpf_policy
class type inspect Remote_VPN
inspect
class class-default
!
zone security private
zone security internet
zone security dmz
zone-pair security dmz-to-internet source dmz destination internet
zone-pair security internet-to-dmz source internet destination dmz
service-policy type inspect zbpf_policy
!
!
crypto isakmp policy 5
encr aes
hash md5
authentication pre-share
group 2
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp policy 15
encr aes 256
authentication pre-share
group 2
!
crypto isakmp policy 20
encr 3des
authentication pre-share
group 2
!
crypto isakmp policy 30
encr aes
authentication pre-share
group 2
crypto isakmp key <crypto key> address 10.0.0.6
!
!
crypto ipsec transform-set ESP_3DES_MD5_HMAC esp-3des esp-md5-hmac
crypto ipsec transform-set ESP_3DES_SHA_HMAC esp-3des esp-sha-hmac
crypto ipsec transform-set ESP_AES_SHA_HMAC esp-aes esp-sha-hmac
crypto ipsec transform-set ESP_AES_MD5_HMAC esp-aes esp-md5-hmac
crypto ipsec transform-set ESP_AES256_SHA_HMAC esp-aes 256 esp-sha-hmac
!
crypto map Extranets 10 ipsec-isakmp
set peer 10.0.0.6
set transform-set ESP_3DES_MD5_HMAC
match address Remote_VPN
!
!
!
!
interface FastEthernet0
description "Internet" connection - 3750-Port48
ip address 10.0.0.2 255.255.255.252
zone-member security internet
duplex auto
speed auto
crypto map Extranets
!
interface FastEthernet1
description Local DMZ
ip address 10.0.1.1 255.255.255.0
zone-member security dmz
duplex auto
speed auto
!
interface Vlan1
no ip address
!
interface Async1
no ip address
encapsulation slip
!
ip route 10.0.0.4 255.255.255.252 10.0.0.1
ip route 10.0.2.0 255.255.255.0 10.0.0.6
!
no ip http server
no ip http secure-server
!
ip access-list extended Remote_VPN
permit ip any any
!
control-plane
!
line con 0
line 1
line aux 0
line vty 0 4
!
end
Remote router:
hostname sdc-1811-RemoteLab
!
boot-start-marker
boot-end-marker
!
no aaa new-model
!
resource policy
!
ip cef
!
no ip domain lookup
!
crypto isakmp policy 5
encr aes
hash md5
authentication pre-share
group 2
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp policy 15
encr aes 256
authentication pre-share
group 2
!
crypto isakmp policy 20
encr 3des
authentication pre-share
group 2
!
crypto isakmp policy 30
encr aes
authentication pre-share
group 2
crypto isakmp key <crypto key> address 10.0.0.2
!
crypto ipsec transform-set ESP_3DES_MD5_HMAC esp-3des esp-md5-hmac
crypto ipsec transform-set ESP_3DES_SHA_HMAC esp-3des esp-sha-hmac
crypto ipsec transform-set ESP_AES_SHA_HMAC esp-aes esp-sha-hmac
crypto ipsec transform-set ESP_AES_MD5_HMAC esp-aes esp-md5-hmac
crypto ipsec transform-set ESP_AES256_SHA_HMAC esp-aes 256 esp-sha-hmac
!
crypto map Extranets 10 ipsec-isakmp
set peer 10.0.0.2
set transform-set ESP_3DES_MD5_HMAC
match address Remote_VPN
!
interface FastEthernet0
ip address 10.0.0.6 255.255.255.252
duplex auto
speed auto
crypto map Extranets
!
interface FastEthernet1
description Remote LAN
ip address 10.0.2.1 255.255.255.0
duplex auto
speed auto
!
interface Vlan1
no ip address
!
interface Async1
no ip address
encapsulation slip
!
ip route 10.0.0.0 255.255.255.252 10.0.0.5
ip route 10.0.1.0 255.255.255.0 10.0.0.2
!
no ip http server
no ip http secure-server
!
ip access-list extended Remote_VPN
permit ip any any
!
control-plane
!
line con 0
line 1
line aux 0
line vty 0 4
!
end
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 12:47 PM
Hello Ven,
Your problem is the acl 101 that is on the class-map Remote_VPN. The packets are going to first hit that acl, and since the class map is a match any, is only going to match the access list and let the packet in.
Remove the acl from the class map and you should have the desire expectations.
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 01:12 PM
Took out acl 101 and removed the match access-group 101 from the class-map and it still works.
!
class-map type inspect match-any Remote_VPN
match protocol http
match protocol kerberos
match protocol netbios-ns
match protocol dns
match protocol ldap
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 01:21 PM
Hi,
Please let a continuos ping and do the following command:
show policy-map type inspect zone-pair sessions
Send me the output.
Cheers.
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 01:26 PM
Here it is!
sdc-1811-LocalLab#show policy-map type inspect zone-pair sessions
Zone-pair: internet-to-dmz
Service-policy inspect : zbpf_policy
Class-map: Remote_VPN (match-any)
Match: protocol http
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol kerberos
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol netbios-ns
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol dns
0 packets, 0 bytes
30 second rate 0 bps
Match: protocol ldap
0 packets, 0 bytes
30 second rate 0 bps
Inspect
Class-map: class-default (match-any)
Match: any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 01:41 PM
Hi,
You are pinging to a host on the inside right?Class default should be dropped by default, please enter the following:
Policy-map type inspect zbpf_policy
class class-default
drop
If that does not solve the issue, do the following:
Class-map type inspect deny-all
match access-group 101
Policy-map type inspect zbpf_policy
Class deny-all
drop
If that does not solve it, please take a capture on the receiving host and gather the show arp of the router.
Cheers
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 01:46 PM
First one didn't work by itself. I'll add the second part... but I see you added the match access-group 101, but no access-list 101 exists.
If I create one, what should it look like?
Thanks!
Ven
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 01:50 PM
Hey,
Access-list 101 deny ip any any
Cheers,
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 02:03 PM
Mike:
Thanks for all the help... No joy so far.
Not sure I have a sniffer handy. I'll have to ask around.
Ven
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2011 02:07 PM
Sure thing is an extrange issue. You can download wireshark and start it, that should do it, then start the ping and gather the show arp from the router.
Cheers.
Mike.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2011 08:37 AM
Sorry about the delay. I was at a new site doing a wireless survey.
I missed a MAJOR part of this. Self zone. I was trying to ping the router interface... Not a device hanging off the router.
I went back to my original config and it worked just fine.
Now I just have to lock down the router with self-zone pairs.
Thanks for all your help!
Ven
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2011 04:47 PM
Hi,
I am glad, if you need further assistance let me know, I will be more than glad to help.
Have this question as marked so other people can follow the steps of troubleshooting we did.
Mike
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
