Terraform expands into the extensive Cisco IOS XE Programmability and Automation Ecosystem
IOS XE’s vast programmable feature set
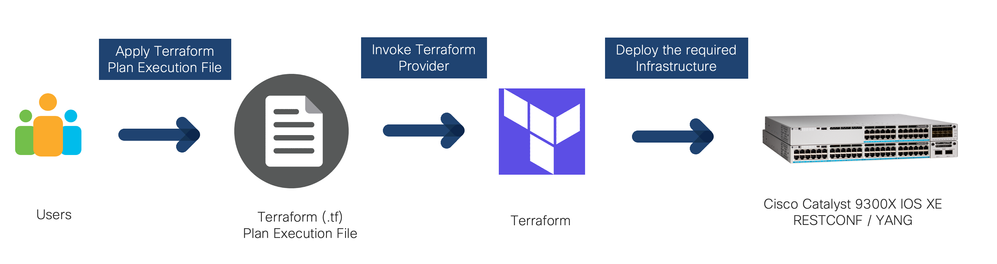
The Cisco IOS XE ecosystem is programmatically managed and supports a variety of tooling from Ansible to YANG Suite and with pyATS over NETCONF, RESTCONF, gNxI and even with legacy CLIs. With the addition of the new Cisco IOS XE Terraform provider, we add an additional tool into the IOS XE configuration management toolbox.
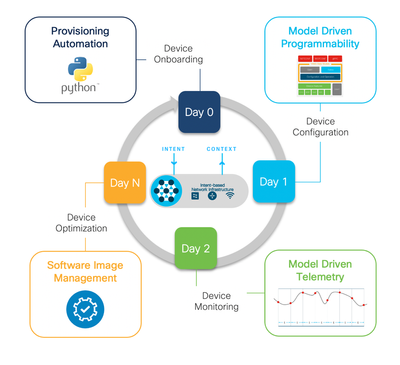
In the programmability lifecycle, we manage device onboarding, configuration, monitoring and optimization. In Day 0, we have device onboarding including Pre-boot Execution Environment (iPXE), Zero Touch Provisioning (ZTP), and VM automation. In Day 1, we configure devices using Network Configuration Protocol (NETCONF), RESTCONF, gNMI, YANG Data Models, OpenConfig, YANG Suite tooling, Ansible, pyATS, and now Terraform. In Day 2, we monitor devices using the TIG MDT container, YANG on-change support, gRPC dial-out with DNS and mutual TLS, and gNMI or NETCONF dial-in. Beyond Day 2, we optimize our devices using gNOI cert/os/reset.proto, Guest Shell with NETCONF, CentOS 8 with Python 3, Application Hosting with Docker, and CLI to YANG. These features and protocols knit programmability into Cisco IOS XE.
Introducing Terraform with IOS XE
Why Terraform? Terraform simplifies complex network configurations by orchestrating provisioning, configuration and state management in the cloud as well as on-prem in the campus enterprise network and the data center.
Why Terraform in the Campus? Terraform is an ideal solution for cloud-native customers, especially those already using this tooling in other aspects of their network to consolidate cloud-native provisioning with on-prem device configuration. Additionally, we can now use Terraform for other cloud services and infrastructure as well as use it with existing continuous integration/continuous deployment (CI/CD) tooling and pipelines.
Terraform is an Infrastructure as Code tooling that allows network operators to easily view operational data, configure devices and manage network resources. Since Terraform is cloud native, it works well with Cisco IOS XE cloud native solutions for routing, switching, and wireless platforms including the Cisco Catalyst 9000 Family switches, the Cisco Catalyst 8000V (virtual) router and the Cisco Wireless LAN Controller (WLC) 9800-CL (CL stands for “Cloud”). As well as easily managing cloud-native solutions, Terraform can also configure campus solutions. With Cisco IOS XE, we can automate with any tooling on any interface.
Secure Branch Connectivity
The relationship between Cisco and Terraform continues to grow. Cisco recently released Terraform support for Application Centric Infrastructure (ACI). We can Leverage Cisco Intersight Service for HashiCorp Terraform. Further, we can now integrate Terraform configurations with DevOps pipelines to manage the IOS XE features in a more flexible, consistent, and reliable way.
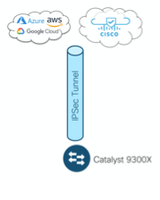
Terraform, a cloud-native tooling, can be used natively by all cloud providers such as Google Cloud Platform, Microsoft Azure, and AWS. For example, we can use Terraform to configure an IPsec crypto tunnel between a Cisco Catalyst 9300X and an AWS Virtual Private Cloud (VPC). We can also provision additional resources within the cloud and configure additional features on our Catalyst 9300X all at the same time.
Terraform Terminology
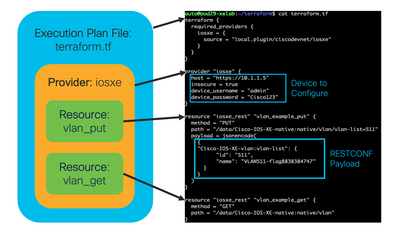
- An execution plan file defines the provider and resources. It is written in HashiCorp Configuration Language (HCL), similar to JSON, and stored with a .tf extension.
- A provider is a plugin to make a collection of resources accessible.
- A resource (or infrastructure resource) describes one or more infrastructure objects managed by Terraform. With the IOS XE Terraform provider, resources can be considered the same as a configurable feature.
Using the IOS XE Terraform Provider
- Enable RESTCONF on the device to prepare it for use with Terraform. The Terraform provider was built by abstracting RESTCONF & YANG into HashiCorp Configuration Language (HCL) to be easily used as a REST API. Therefore, RESTCONF is a prerequisite.
Device# conf t
Device(config)# restconf
- Install Terraform.
$ apt install terraform
- Clone the IOS XE Terraform Provider GitHub repository.
$ git clone git@github.com:CiscoDevNet/terraform-provider-iosxe.git
Terraform execution plan files are written in HCL, which is very similar to JSON. For each resource, a JSON mapping reformats the feature from CLI to JSON.
Explore examples of JSON mappings and feature configuration using the Cisco IOS XE Terraform provider on GitHub including features to add security, redundancy, and common protocols to your network.
Using a feature outside of the ones listed in the examples on GitHub? Fear not! All features supported by the REST API (more specifically RESTCONF & YANG) can also be extended and managed with Terraform by following these steps. This allows you to configure features using the IOS XE Terraform provider.
VLAN Management with Terraform
In this VLAN example, we start with no VLAN 511 configured on our Cisco IOS XE device. We explore the terraform.tf file, which has a resource to configure VLAN 511. We initialize terraform and then apply the changes to our device.
Within the Terraform execution plan file, we have a resource to configure VLAN 511 on a Cisco IOS XE device:
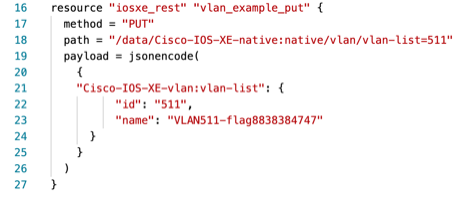
With resource in the Terraform execution plan file, we can now initialize Terraform using “terraform init”. After successfully initializing Terraform, we can deploy the changes in the Terraform execution plan file to the device using “terraform apply -auto-approve.”

Now, we have VLAN 511 successfully configured on our IOS XE device! Check out the full tutorial to configure a VLAN and other step-by-step tutorials showing how to use the IOS XE Terraform provider.
Where to go from Here
Terraform expands the Cisco IOS XE ecosystem to allow us to easily manage our network both in the cloud and on-prem. From configuring an IPsec tunnel between the public cloud and an IOS XE device, to enabling and configuring VMs, to provisioning using Cisco vManage and Cisco DNA Center, Terraform has your back. With Terraform entering the Cisco IOS XE realm, the possibilities are endless.
Ready to get started? Gain hands-on experience with Terraform through the Cisco DevNet sandbox and learning labs.
Resources
