EIGRP is a very interesting distance vector routing protocol that offers advanced options. It is preferably used in certain scenarios such as VPNs, DMVPN, etc.EIGRP exists in two modes of operation: c...

What’s new?
The next major software release for the Cisco C9000 switching portfolio is IOS XE 17.18.1. In this release, Cisco continues to bring forth new hardware and more software enhancements to IO...

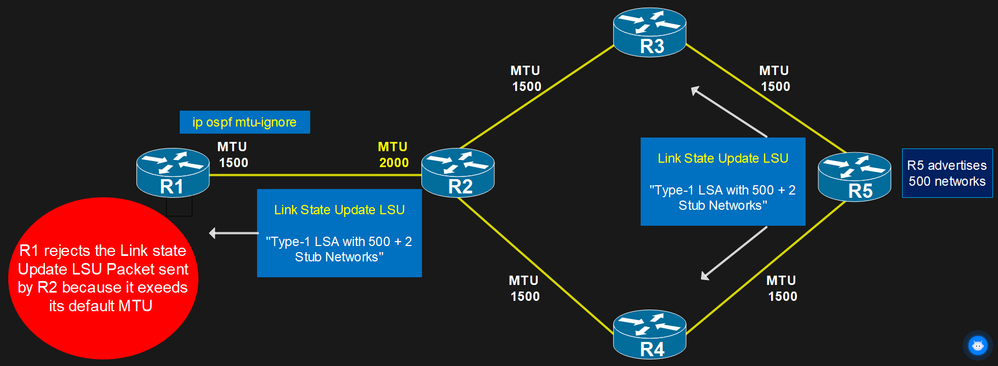
One of the most popular questions is: Why is the ip ospf mtu-ignore command considered dangerous?
An MTU mismatch between two OSPF routers causes the adjacency process to fail during the exchange of D...
Hi All,I'm not an expert in BGP, trying to solve an issue. Appreciate all the Inputs.

Tip to Factory reset Cisco Catalyst 9200L Switch (without password): Note: Don't forget to check the attached below screenshots. To factory reset a Cisco Catalyst 9200 series switch (e.g. when you can...

Today, I am going to share with you a small lab that illustrates a trick called "Errdisable recovery." Although this trick can be used in several cases, I will limit myself to its use in the context o...

Overall, speed, security, and performance data and analytics are critical, but larger and more mature Wi-Fi users prioritize AI-powered Ops (AIOps) functionality . Wi-Fi is a critically important tech...

In critical sectors like hospitals, financial institutions, airports etc., a routine reload, or a maintenance upgrade can have serious consequences. Applications may miss a heartbeat, triggering netw...

Your privileges on APIC will be reduced until you have updated your password. Keep getting this message on ACI Simulator

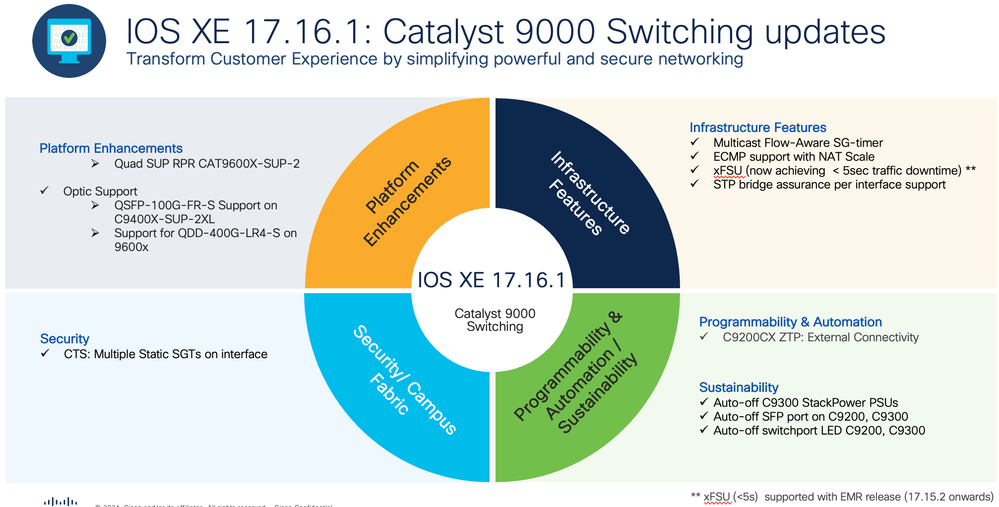
Cisco brings in its new software release IOS-XE 17.16.1, which offers a suite of new software features and enhancements to existing features for our Catalyst 9K portfolio. This update ensures a seamle...
Uploading a new IOS from a tftp server in rommon mode

The Spanning Tree Protocol (STP) family, which includes STP, RSTP (Rapid Spanning Tree Protocol), and MSTP (Multiple Spanning Tree Protocol), has been essential for loop protection in networks. Howeve...

n the design of the OSPF routing protocol, the number of routers in an area is widely discussed in deployments and forum, and according to recent studies and the power of modern routers, it is no long...

Cisco Umbrella is a cloud security platform that acts as a first line of defense against internet threats. It works by blocking malicious requests at the DNS layer before they reach a network or endpo...

In this software release, Cisco continues to bring forth more updates and enhancements to IOS XE. The key highlights for this Extended Maintenance Release (EMR) are related to new hardware capabilitie...