- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- How to use Group-Based Policies with 3rd Party RADIUS using Cisco DNA Center
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
09-25-2019
05:42 PM
- edited on
06-14-2023
05:46 AM
by
thomas
![]()
Overview
This configuration document provides general guidance on how to integrate an existing, non-Cisco RADIUS based solution with SD-Access so that it is possible to leverage the advanced segmentation capabilities of Cisco DNA Center 1.3.1. x FreeRADIUS is used as the RADIUS server in this document.
Note: This document applies to wired and wireless connections
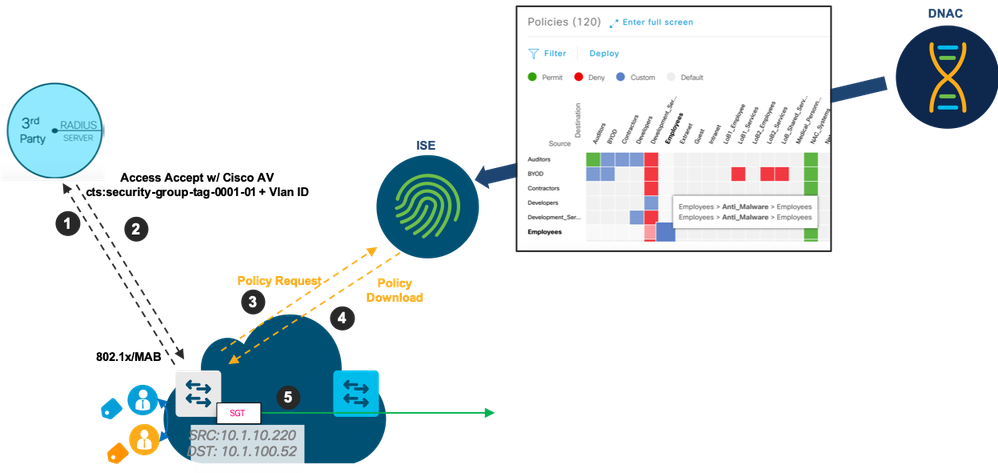
Connection Overview
- Users authenticate directly to the 3rd party RADIUS server
- RADIUS authorization returns VLAN and SGT
- Edge switch initiates a policy request if the policy associated with the newly connected SGT doesn't exist
- Edge switch downloads policies
- Edge switch enforces and/or traffic forwards traffic deeper into the network
Configuration Overview
The configuration objective is to configure the SD-Access edge to use the 3rd party RADIUS server for AAA authentication and authorization and use Cisco Identity Services Engine for group-based policy. This is achieved via the use of templates on Cisco DNA Center.
Cisco DNA Center
- Navigate to Design-->Network Settings--><Site Name>.
- Configure ISE as the AAA server
Note: Configure ISE here instead of the 3rd party server because Cisco DNA Center automates the TrustSec provisioning and add the fabric devices in ISE when the AAA server is ISE. No provisioning occurs when ISE is not specified. - Create a Cloud DayN template with the following commands (see Cisco DNA Center Templates for instructions on configuring a template.
aaa group server radius thirdparty server name thirdparty ip radius source-interface Loopback0 aaa authentication dot1x default group thirdparty aaa authorization network default group thirdparty aaa accounting identity default start-stopp broadcast group dnac-client-radius-group group thirdparty aaa accounting network default start-stop group dnac-client-radius-group group thirdparty aaa server radius dynamic_author client server-key 0 ip radius source-interface Loopback0 radius-server attribute 6 on-for-login-auth radius-server attribute 6 support-multiple radius-server attribute 8 include-in-access-req radius-server attribute 25 access-request include radius-server attribute 31 mac format ietf upper-case radius-server attribute 31 send nas-port-detail mac-only radius-server dead-criteria time 5 tries 3 radius-server deadtime 3 radius server thirdparty address ipv4 auth-port 1812 acct-port 1813 timeout 4 retransmit 3
- Provision the edge. Include the template configured above as part of the provisioning step. The resulting config would look similar to the following:
aaa group server radius dnac-client-radius-group server name dnac-radius_10.1.200.126 ip radius source-interface Loopback0 ! aaa group server radius thirdparty server name thirdparty ip radius source-interface Loopback0 ! aaa authentication login default local aaa authentication login dnac-cts-list group dnac-client-radius-group local aaa authentication enable default enable aaa authentication dot1x default group thirdparty aaa authorization exec default local aaa authorization network default group thirdparty aaa authorization network dnac-cts-list group dnac-client-radius-group aaa accounting update newinfo periodic 2880 aaa accounting identity default start-stop group dnac-client-radius-group ! aaa server radius dynamic-author client 10.1.200.126 server-key 7 073B32494D480A26474227 client 10.1.200.61 server-key 7 15261809076B380778631 ip radius source-interface Loopback0 radius-server attribute 6 on-for-login-auth radius-server attribute 6 support-multiple radius-server attribute 8 include-in-access-req radius-server attribute 25 access-request include radius-server attribute 31 mac format ietf upper-case radius-server attribute 31 send nas-port-detail mac-only radius-server dead-criteria time 5 tries 3 radius-server deadtime 3 radius server dnac-radius_10.1.200.126 address ipv4 10.1.200.126 auth-port 1812 acct-port 1813 timeout 4 retransmit 3 pac key 7 00300003071A18255F7160 radius server thirdparty address ipv4 10.1.200.61 auth-port 1812 acct-port 1813 timeout 4 retransmit 3 key 7 0330480E054E326F1E5935
FreeRADIUS
- Modify the /etc/freeradius/clients.conf file to add the Edge switch as a AAA client
- Modify the /etc/freeradius/users file to add the necessary attributes to pass back the VLAN and the SGT. For FEW, just pass back the SGT.
- Note: “Cisco-AVPair” is case-sensitive
- Note: The SGT value must be represented in Hex e.g. the Doctor_SGT = 18 so the value for the av-pair is 0012
- Note: The numbers trailing the SGT, eg. The “-00” in 0012-00, is important. Omitting this will result in an incorrect SGT assignment of “65535”
- Restart FreeRADIUS
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I think there maybe a couple of errors in the proposed template.
This line has an extra "p" in the start-stop command:
aaa accounting identity default start-stopp broadcast group dnac-client-radius-group group thirdparty
This line seems to be missing the "broadcast" keyword:
aaa accounting network default start-stop group dnac-client-radius-group group thirdparty
Proposed corrected configuration:
aaa accounting identity default start-stop broadcast group dnac-client-radius-group group thirdparty
aaa accounting network default start-stop broadcast group dnac-client-radius-group group thirdparty
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: