- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Cisco ISE configuration for onboarding hosts in Cisco SD-Access
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-20-2020 03:15 AM - edited 06-20-2020 11:47 AM
- Overview
- Authentication Methods in Cisco SD-Access fabric
- Wired Dot1X Authorization Profiles and Policies
- Authorization Profile for Employees
- Policy Set for Wired Dot1X
- Wireless Dot1X Authorization Profiles and Policies
- Wired Guest Authorization Profiles and Policies
- Authorization Profile for Wired Web Auth
- Authorization Profile for Wired Guest Access
- Policy Rules for Wired Guest Auth and Access
- Wireless Guest Authorization Profiles and Policies
- Design
- Create Guest Wireless SSID
- Update ISE Authorization Profile
- Provision WLC
- Add WLC to Fabric
- Assign IP Pool to Guest SSID
- Check WLAN status is Enabled
Cisco ISE configuration for onboarding hosts in Cisco SD-Access
Overview
This document will provide details of Cisco ISE configurations for customers who are onboarding wired and wireless users via 802.1x in the Cisco SD-Access solution.
This document also covers configuration in Cisco ISE for onboarding wired/wireless Guest users
in Cisco SD-Access fabric.
Authentication Methods in Cisco SD-Access fabric
Using Cisco DNAC, you can have multiple authentication methods:
Closed Authentication: This is the most restrictive authentication template. A host attempting to connect to the network will first be required to use dot1x authentication. If dot1x authentication fails, the host will be permitted to try to authentication using MAC Authentication Bypass (MAB). If MAB also fails, the host will have no access to the network.
Low Impact: Security is added by applying an ACL to the switch port, to allow very limited network access prior to authentication. After a host has been successfully authenticated, additional network access is granted.
No Authentication No Authentication deploys no additional configuration to the access ports. Hosts will not be required to use any authentication method to access the network. Access is simply granted when the port moves to the Up/Up status.
Open Authentication: A host is allowed network access without having to go through 802.1X authentication
Details regarding how to build the Cisco SD-Access fabric can be found here:
How to deploy Cisco SD-Access (SDA) Fabric from start to finish with Cisco DNAC 1.3.1
Cisco ISE configuration details for onboarding users in the Cisco SD-Access fabric via 802.1X are outlined below:
Wired Dot1X Authorization Profiles and Policies
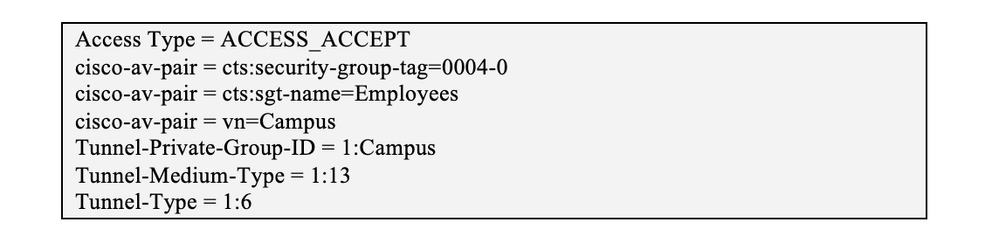
The authorization policy applies the VLAN and SGT assignment based on the authorization conditions/attributes. Below is one of the ways to push VLANs dynamically from ISE. You can use many other conditions to authorize as well from ISE. These policies will be specific to the authenticating user’s identity group.
After successful authentication, ISE will look at the User Identity Group the authenticated user is part of and assign the VLAN and SGT accordingly (e.g. Employees).
The authentication table checks who you are, and the authorization table gives you access to the right resources. If the user’s password is correct, authentication succeeds, and the authorization policy is then matched depending on the authorization policy conditions.
Upon successful match of authorization policy, the user is placed into the configured VLAN and assigned the configured SGT. This section explains how to create an authorization result for each user Identity Group. The authorization result is used in an authorization policy that informs the edge switch which VLAN and SGT to apply to the successfully authenticated endpoint/user.
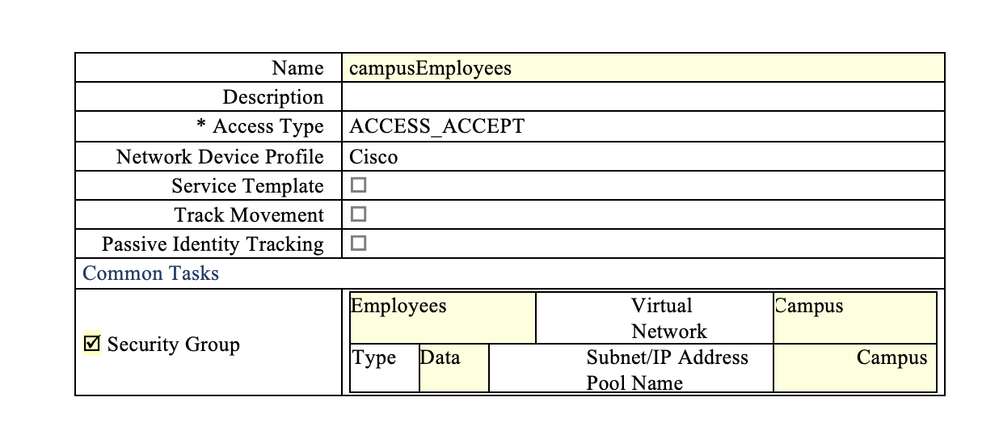
Authorization Profile for Employees
-
In ISE, click Authorization Profiles from the left-hand pane under Policy > Policy Elements > Results > Authorization.
-
Click Add from the right-hand pane and enter the values for the Authorization Profile as shown below.
More details regarding how to map ip pool from DNAC to name like above can be seen in the below link:
How to SDA Host Onboarding with ISE
Details about Cisco ISE Posturing can be found below
Cisco ISE Posture Prescriptive Deployment Guide
The resultant Attribute Details should appear at the bottom of the page as below:
-
Scroll to the bottom and click [ Submit ] to apply the changes.
You can create similar profiles for other users in the network
Policy Set for Wired Dot1X
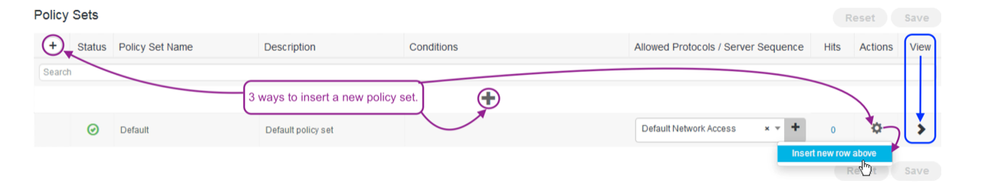
Navigate to Policy > Policy Sets.
-
Use one of the three ways shown above and add a new Policy Set.
-
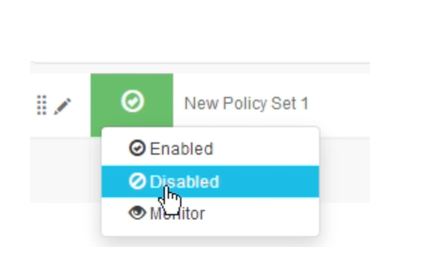
As a good practice, change the status to [ Disabled ], as this policy set is incomplete.
-
Update the policy set name to Wired1X.
-
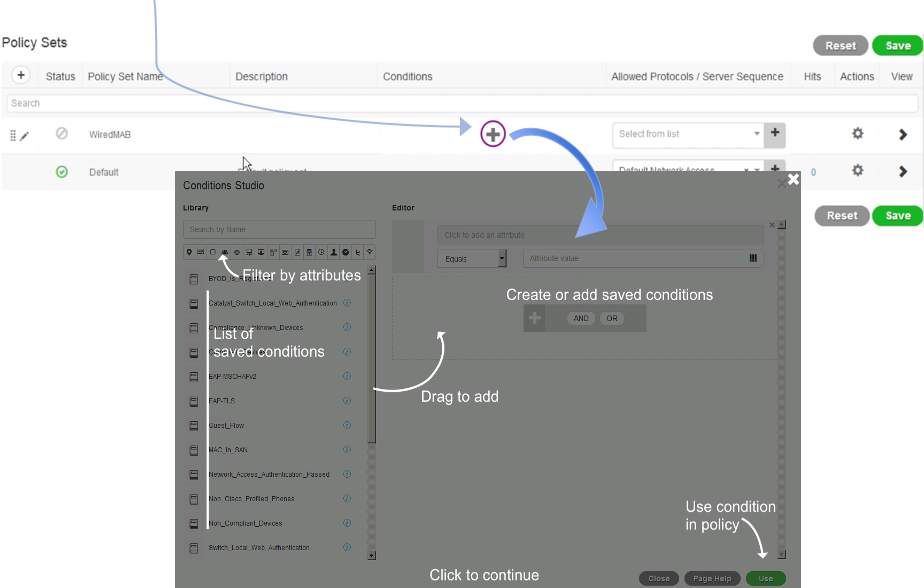
Click + under the Conditions column and bring up the Conditions Studio to add conditions
Inside the condition studio, the Library on the left has saved conditions for re-use. Scroll up and down to search for a condition visually or use the [ Search by Name] box on the top left of the screen to narrow down the list conditions. We can also hover over and click to filter on the category icons above the list of saved conditions to acquaint ourselves with the available categories.
-
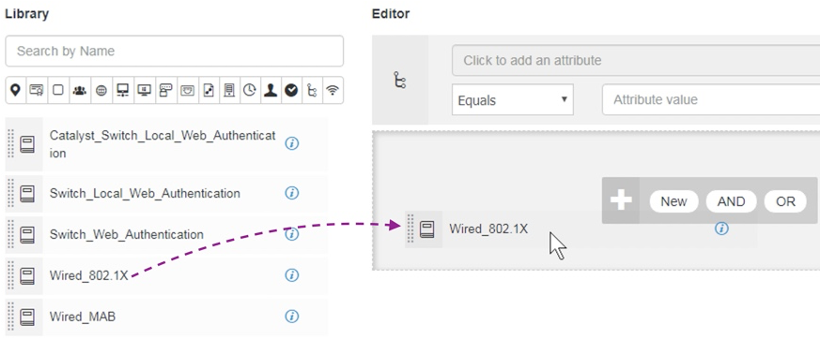
Locate it on the left side window, click and hold on the condition, drag to the right panel, and drop onto the block that has the + sign.
-
Scroll down the condition studio and click on the [ Use ] button at the bottom right of the screen.
-
After returning to the policy set list view. Click on [ Select from list ] drop down under the Allowed Protocols / Server Sequence and choose Default Network Access from the list. Click [ Save ].
The policy set should look similar to below:
Click the right arrow > to expand the policy set Wired1X. We will see the authentication, authorization and exception policies listed as shown aboveTo see the full Authorization Policy, collapse the Authentication Policy and expand the Authorization Policy in the Policy sets > Wired1X screen.
-
Next, we will insert a rule for Employees. Click + above the Default rule to insert a new one. Rename the rule to Employee.
-
Click + under the Conditions column and bring up the Conditions Studio to add a condition.
-
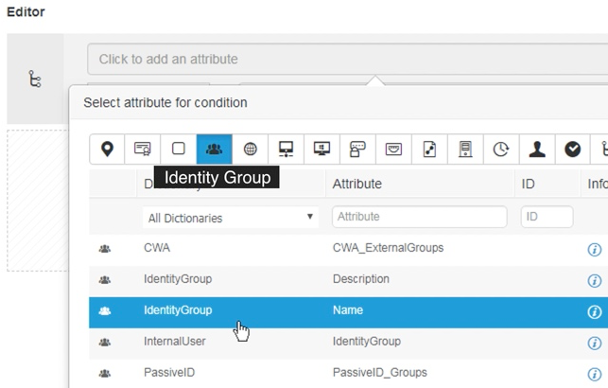
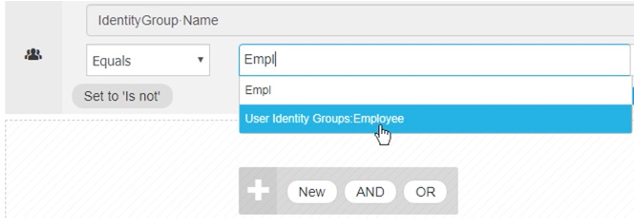
Under the Editor on the right pane, click on the box [ Click to add an attribute ].
-
Use the icon filter Identity Group to narrow down the attributes pertaining to ID groups. Then, select IdentityGroup:Name.
-
In the right-hand-side of EQUALS, type in the first few characters of Employee to find and select User Identity Groups:Employee.
-
Click [ Use ] to close the conditions studio and return to the policy set view.
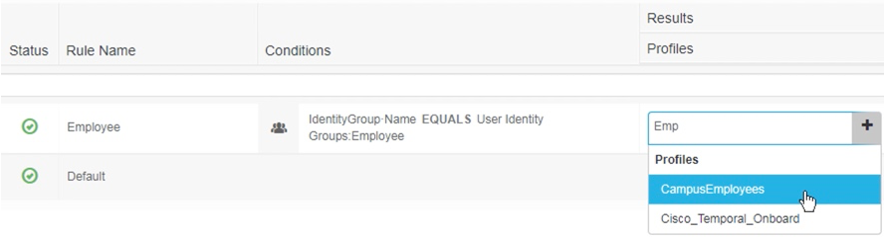
-
For the Results > Profiles of this rule, select CampusEmployees.
-
We are done with the authorization policy. Scroll up to the policy set name Wired1X and toggle the policy set status to Enabled. Then, click [ Save ].
The policies in ISE are enforced when the conditions are matched. The authenticated user/endpoint’s attributes will be matched against the beginning of the policies (rules) and continue down the list. Once a condition/attribute is matched, the associated authorization (result profile) and SGT (Security Group) is applied to the user/endpoint’s RADIUS session.
Wireless Dot1X Authorization Profiles and Policies
For Wireless, VLAN attribute is not essential. However if you want to create single Authorization profiles for both Wired/Wireless Users, you can reuse the Authorization profile used in Wired for Wireless as well.
This is one way of doing it because we are using separate policy set for wired/wireless authentication. You can also use same policy
Below configuration is showing creating separate Authorization policy for Wired/Wireless.
-
In ISE, go to Policy > Policy Sets
-
Duplicate above the policy set Wired1X as shown below.
-
In the duplicate, update the policy set name to Wireless1X, the conditions to Wireless_802.1X. Save the policy sets. After saving, click the view icon > to delve into the details of the policy set.
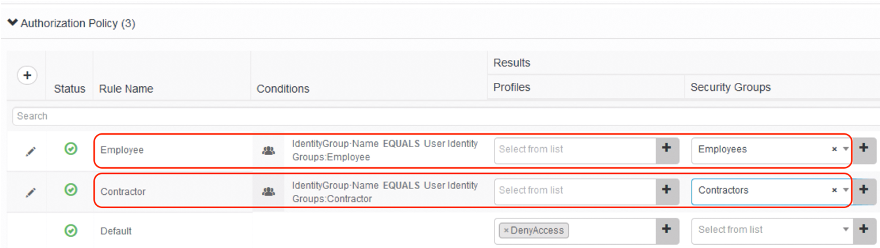
-
Expand on the last section Authorization Policy and update the results of the two rules Employee and Contractor by (a) removing the authorization profiles and then (b) adding security groups Employees and Contractors, respectively, as shown below.
-
Save once done.
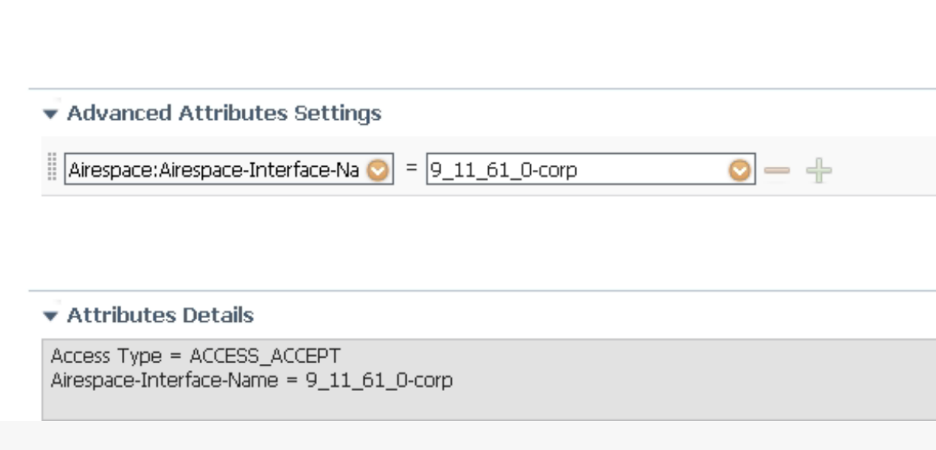
Note:
For Cat9800 controller running IOS-XE versions prior to 16.12.3, you need to create a separate authorization profile just for the 9800 and use the "airespace-interface-name" attribute to send the VLAN
Sample screenshot with airspace interface:
Wired Guest Authorization Profiles and Policies
Cisco ISE comes with policies and profiles for wireless guests. In this section, we will make adjustments to these pre-built elements for wired guests in SD-Access.
Authorization Profile for Wired Web Auth
-
In ISE, click Authorization Profiles from the left-hand pane under Policy > Policy Elements > Results > Authorization.
-
Locate the Authorization Profile Cisco_WebAuth. Select it and Duplicate.
-
In the edit page, update the name to sdaWiredWebAuth. Then, scroll down to the section Common Tasks, first locate VLAN and put Guest into the text box next to ID/Name. Then, locate Web Redirection (CWA, MDM, NSP, CPP), enable Static IP/Host name/FQDN, and put the ISE IP Address into the text input box, as shown below.
Static ip is needed only in case of Lab Environment where there is no DNS setup, we can use ISE IP address for redirection
-
Scroll to the bottom and click [ Submit ] to apply the changes.
Authorization Profile for Wired Guest Access
-
In the Standard Authorization Profiles pane in ISE, click Add and enter the values for the Authorization Profile as shown below.
The resultant Attribute Details should appear at the bottom of the page as the following:
-
Scroll to the bottom and click [ Submit ] to apply the changes.
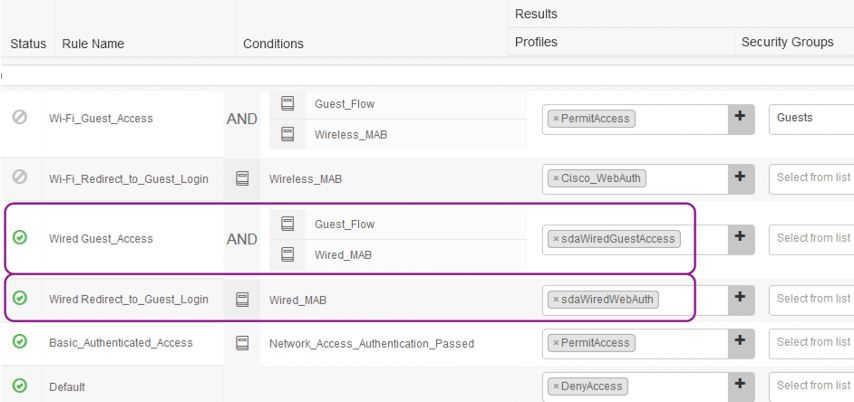
Policy Rules for Wired Guest Auth and Access
-
Navigate to Policy > Policy Sets. Then, click on > at the right end of the Default policy set to view the details.
-
Expand on the Authorization Policy section and scroll all the way down. Insert two rules before the one on Basic_Authenticated_Access as shown below and then Save.
Wireless Guest Authorization Profiles and Policies
There is a workflow for this from Cisco DNAC which pushes the configuration to Cisco ISE.
Design
Create Guest Wireless SSID
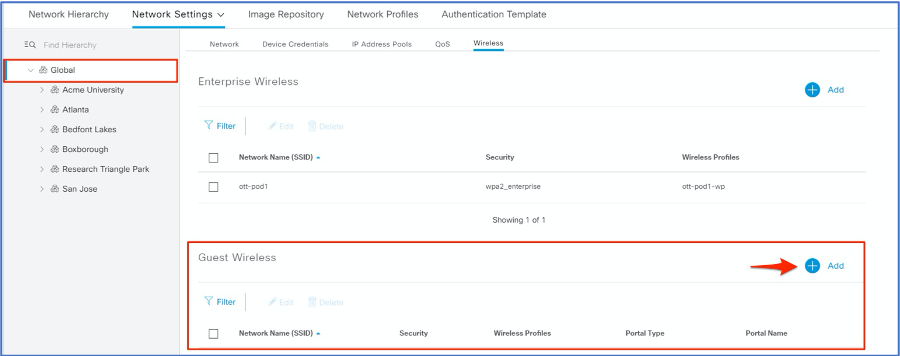
Navigate to DESIGN > Network Settings > Wireless. And, select Global in the Network Hierarchy.
-
Click Add to create a new Guest Wireless Network.
-
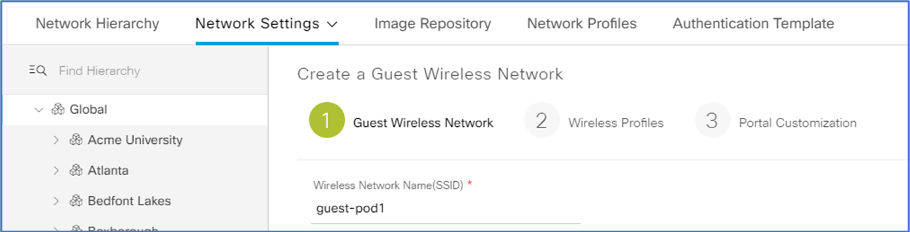
In (1), enter a Wireless Network Name (SSID).
-
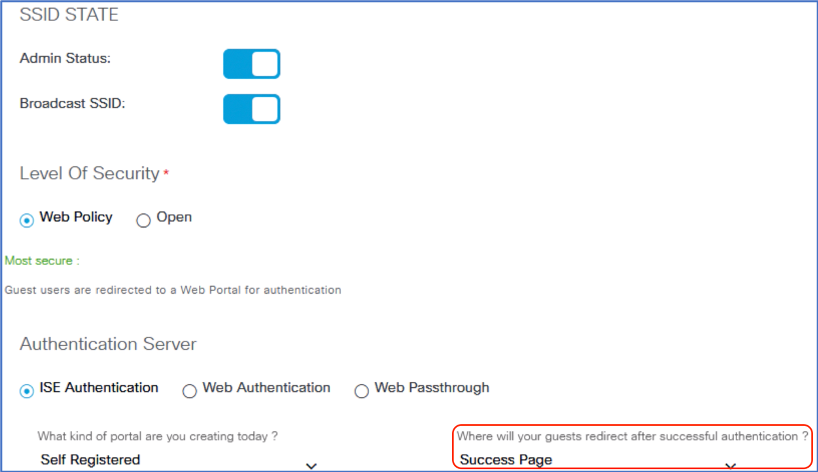
Leave the defaults setting for SSID State, Wireless Options, Level of Security and Authentication Server. Change from Original URL to Success Page at the option on where will your guests redirect after successful authentication? Click Next.
-
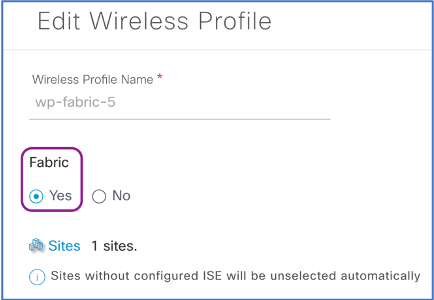
In (2) Wireless Profiles, select the wireless profile created for the fabric-enabled Enterprise Wireless.
-
In the Edit Wireless Profile slide-out, verify Yes for Fabric. Scroll down and Save.
-
Click Next in (2).
-
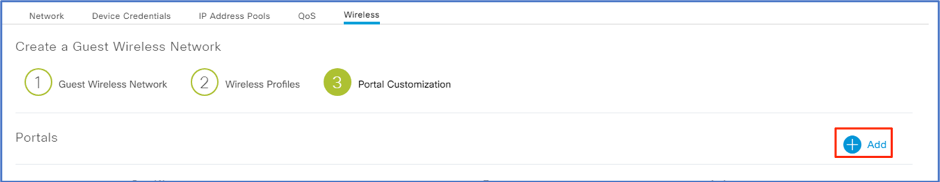
In (3) Portal Customization, click Add.
-
Give a descriptive Portal Name.
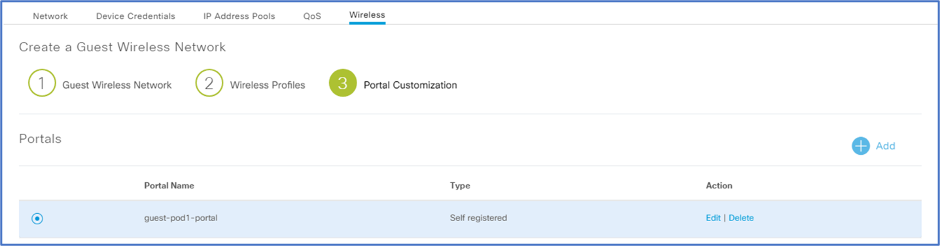
-
Click Save.
-
Click Finish.
Update ISE Authorization Profile
-
Similar Authorization profile is needed only in lab environment where there is no DNS for redirection, and we have to use static ip of ise similar to Wired Guest we created above
-
In ISE, click Authorization Profiles from the left-hand pane under Policy > Policy Elements > Results > Authorization.
-
Locate the Authorization Profile created for the Guest (e.g. dnacGuestPortalPod6_Profile). Select it and Edit.
-
In the edit page, scroll down to the section Common Tasks, locate Web Redirection (CWA, MDM, NSP, CPP), enable Static IP/Host name/FQDN, and put the ISE IP Address into the text input box, as shown below
-
Scroll to the bottom and click [ Save ] to apply the changes.
Provision WLC
-
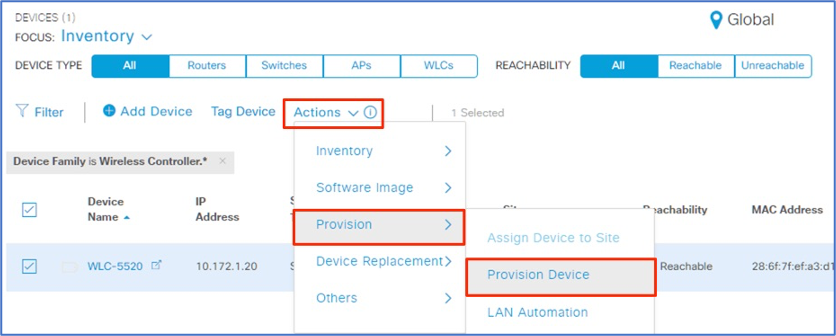
In Cisco DNA Center, go to Provision > Devices. Focus on Inventory.
-
Select WLCs as the device type and select WLC-5520.
-
Go to Actions > Provision and select Provision Device.
-
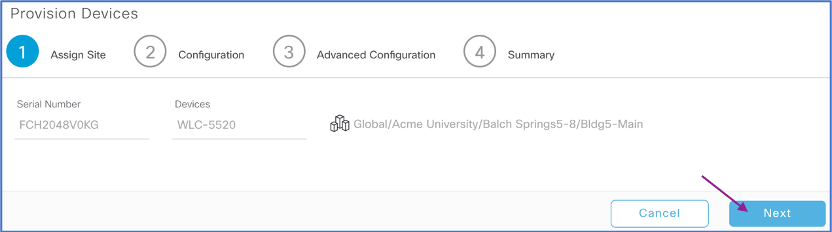
In (1) Assign Site, keep the current site and click Next.
In (2) Configuration, review and leave the Configuration as is and select Next.
-
In (3) Advanced Configuration, select Next
-
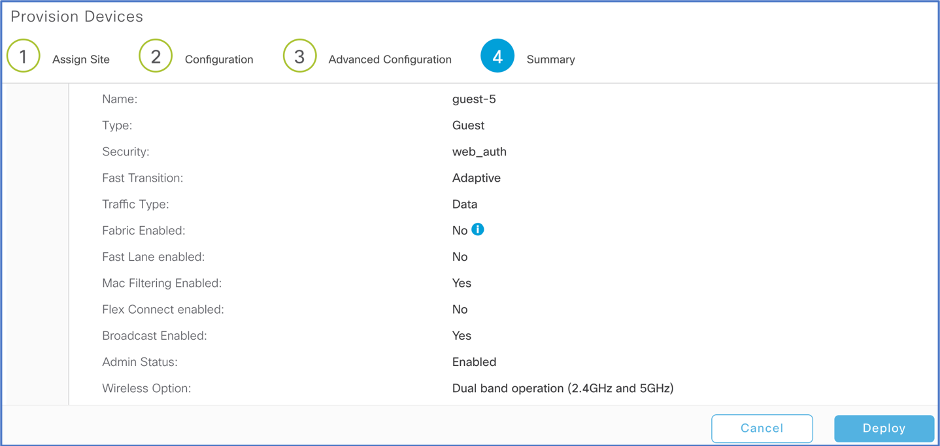
In (4) Summary, review and click Deploy.
-
Leave Now radio button checked and select Apply to start provisioning
-
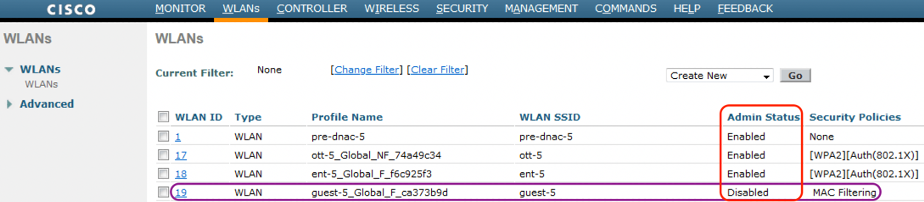
Go to WLC > WLANs. Verify that the SSID created in DNAC is listed and the status is disabled.
Add WLC to Fabric
This step is needed only if we did not provision WLC before.
-
Access Cisco DNA Center web UI
-
Go to PROVISION > Fabric
-
Select the main site from left panel.
-
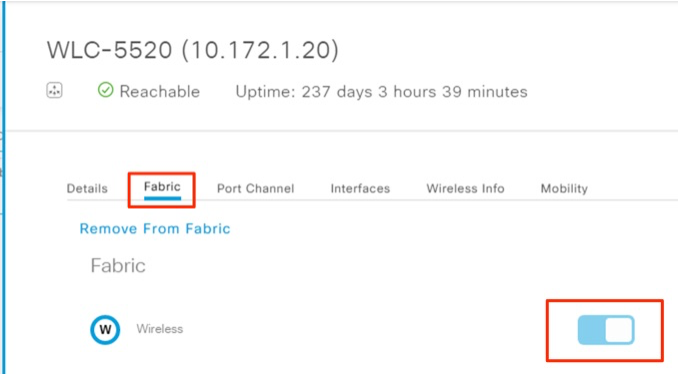
Under Fabric Infrastructure, select WLC-5520
-
Under Fabric, turn Wireless switch on and click Add.
Assign IP Pool to Guest SSID
-
Go to PROVISION > Fabric
-
Select fabric domain University
-
Select the main fabric site.
-
Go to Host Onboarding
-
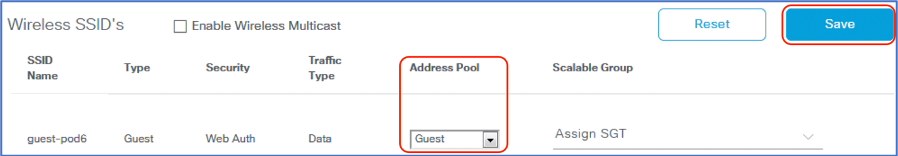
In Wireless SSID’s section, select Address Pool for Guest. Click Save and then Apply.
Check WLAN status is Enabled
-
Log in to WLC and then go to WLC > WLANs
-
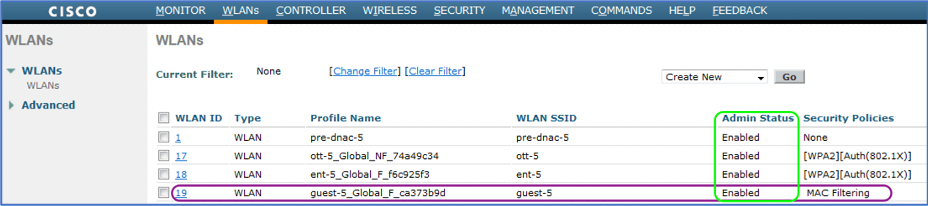
Check the guest SSID is now Enabled.
Note: The status is Enabled.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: