- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- SD-WAN Advanced Deployment version.F 2.1
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 01-03-2022 11:04 AM
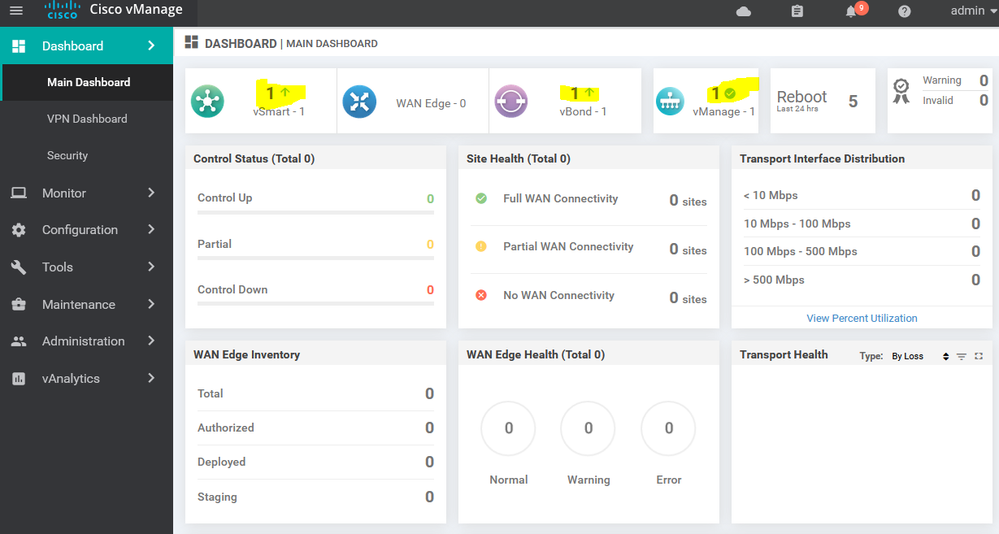
SD-WAN Advanced Deployment
What is SD-WAN?
SD-WAN is Software define wide area network and SD-WAN is key part of the technology of software-defined networking . SDN is a centralized approach to network management which abstracts the underlying network infrastructure away from its applications ,SD-WAN has more advantage such as automation, simplification of operations, provisioning, monitoring, Application Aware and smart troubleshooting.
Why SD-WAN solution ?
SD-WAN solution has major advantages but the most important of them is Cost &user experience let's imagine the connection with traditional wide area network (WAN) when users at the branch want to connect to applications hosted on servers in the data center through MPLS , look to cost & t-shoot , SD-WAN will reduce cost here because the solution Support for all typed of connections (4G, 5G, Broadband , MPLS that means you can select cheaper connection options for low-priority traffic and high cost for high-priority traffic.can help a branch router avoid loss, latency and jitter within the network, SD-WAN give you ease of management via your single pane of glass interface, Increasing bandwidth through the activate & backup links and dynamic load-balancing, Delivering faster cloud access by enabling direct internet access at the branch .As we are seeing today all business go with Software as a Service (SaaS) and Infrastructure as a Service (IaaS) across multiple clouds, IT departments are struggling with providing a satisfactory experience for business-critical applications, SD-WAN Delivering faster cloud access by enabling direct internet access .
How many planes in the Cisco SD-WAN solution ?
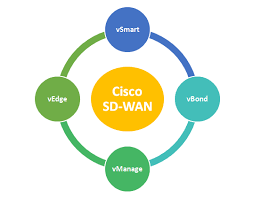
Cisco SD-WAN provides a clear separation between management plane, control plane, and data plane, Cisco SD-WAN solution contains four planes < Management plane , Control Plane , orchestration plane , Data plane > An important consequence of the software-defined networking principles is the separation of control plan and data plan
between the definition of network policies and the forwarding of traffic.This separation is key to the desired flexibility, breaking the network control problem into pieces, and making it easier to create and introduce new abstractions in networking,
simplifying network management and facilitating network evolution and innovation.
What is the components of cisco SD-WAN solution ?
The Cisco SD-WAN solution contains four key components responsible for each plane :
1-Cisco vManage :- Cisco V-manage is used to handle the management plane and represents the user interface of the solution.
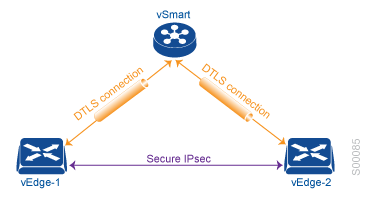
2-Cisco vSmart :- v-Smart is the brain of the solution and exists within the control plane, v-Smart is the component responsible for enforcing these policies centrally and exchange the routing information.
3-Cisco vBond :- v-Bond is the orchestration plane responsible for on boarding the device into the SD-WAN fabric and Zero-Touch Provisioning process as well as first-line to authentication, v-Bond is responsible Network Address Translation (NAT) traversal.
NOTE : Cisco SD-WAN is based on the zero-trust model. All of the components mutually authenticate each other, and all of the edge devices are authorized before they are allowed onto the network.
4- Edge routers :- Edge router is data plane and Edge routers are responsible for establishing the network fabric and forwarding traffic.
-------------------
- SD-Wan Policy :-
Viptela SD-WAN classified two types ( centralized policies or localized policies ) .
- The difference between ( centralized policies or localized policies )
Centralized policies : Those policies that are applied on the vSmart on the overlay network.
Localized policies : Those policies that are applied locally on the vEdge routers on the overlay network .
Centralized policies has two polices ( Control Policy and data Policy )
Localized Policy : Pushed from vManage directly to Edge devices via a NETCONF transaction – affects will happened for specific devices requiring policies.
Centralized Control policies :- Used to manipulate the propagation of routing information in the control plane including OMP, TLOC, VPN Services .
Centralized Data policies : Commonly used to accomplish (DIA) for specific applications, network service insertion, Also data plane manipulations such as packet Forwarding Error Correction (FEC) .
NOTE : In traditional wan , configurations are typically applied on a device thorough CLI but cisco SD-WAN is came with a new era of the network which's SDN and it has been designed to overcome this by implementing a centralized management plane that implement on all devices without any human error.
NOTE : Before Appalling any policy please be consider this all vEdges routers will sent the local site network to vSmart controller via OMP protocols , All vEdges will send all TLOC routes to vSmart controller via OMP , All vEdge Router will send all service Routes to all vSmart via OMP.
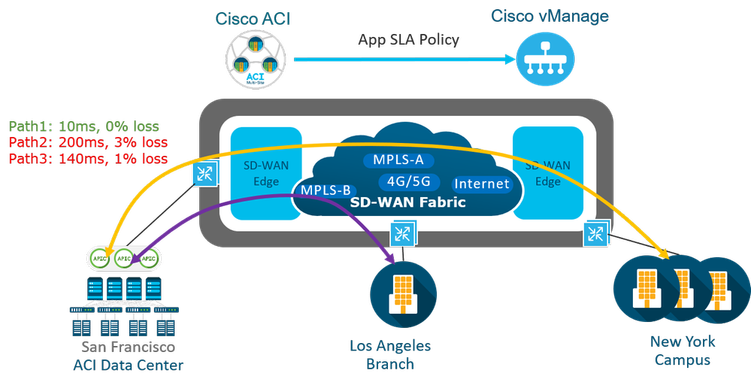
- Application Aware Routing
Application-Aware Routing is identify business critical traffic and specify the required SLA for that traffic classified . Viptela SD-WAN provides the ability to use multiple transports such as MPLS , BIZ-Internet, broadband , Etc... more than one method with high availability which 's will effect to the cost and operation . It provides the ability to use intelligent method through SLA detection for the application to used different transports based on the status .
Application-aware routing directs traffic based upon an application SLA LIST parameters and this defined application policies done though the vmanage and push to vSmart then to all SD-wan fabric Traffic is automatically sent to WAN links that have the important network characteristics and meet the SLA conditions to support these applications in production .
- SD-wan Security Features include IPS/IDS services
As we know the security is a critical part of today's networking infrastructure , Cisco Viptela SD-WAN align it self with this and from version 18.0 to latest version 20.6 the intrusion prevention/intrusion detection systems and URL filtering is available , and can apply this services for all the SD-WAN fabric .
- Unified communication Voice
Cisco Unified Communications requires that Cisco vManage be running Cisco SD-WAN Release 20.1. You can configure feature templates and voice policies to enable Cisco Unified Communications voice services for supported routers. These templates and policies configure parameters for FXO, FXS . When Cisco voice services are enabled, routers can process calls for various endpoints, including voice ports, POTS dial peers, SIP dial peers, and phone profiles in Cisco Unified Survivable Remote Site Telephony mode. Also voice policy defines how the system define and manipulates calls for various endpoint types. Endpoints include voice ports, POTS dial peers, SIP dial peers, and Survivable Remote Site Telephony .
- Integration with Cisco umbrella
The security, availability, visibility, and performance of the IT sector are the key foundation of a solid business and service environment.
- what you will do if the attacker pivots and enter your network infrastructure to get your sensitive data, attackers need to register with your domain to start his attack, all of this will happen once you respond to the incident.
NOTE: You can get the Cisco umbrella solution in your enterprise within 10 minutes .
- Integration With cisco DNAC :-
Cisco DNA enables a blend of typical routing Lisp , BGP, DNS, etc. and security MACsec, ACLs, etc. capabilities for routing-only deployments for any organization. The network is managed by either Cisco DNA Center or vManage. Each is a single, centralized management console to monitor and manage the entire network , Cisco DNA can manage the WAN and security part and SD-WAN to manage the WAN side and Applications which's based on the cloud .
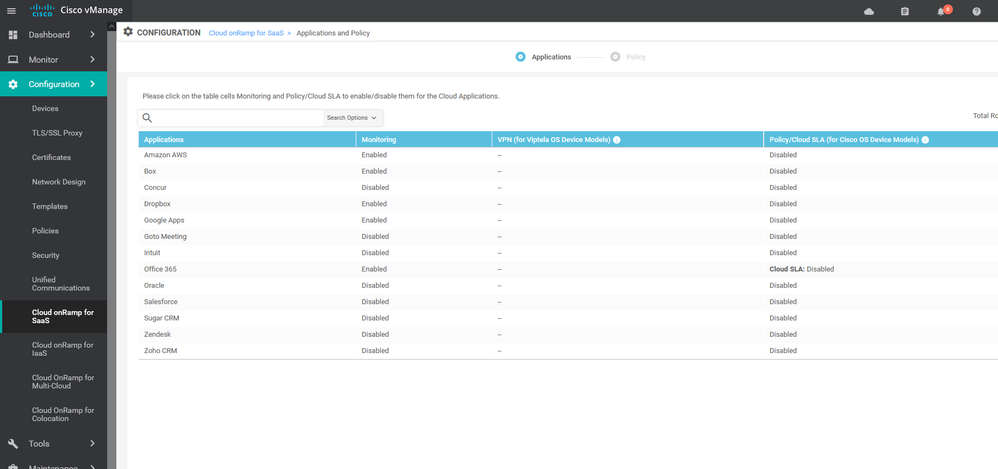
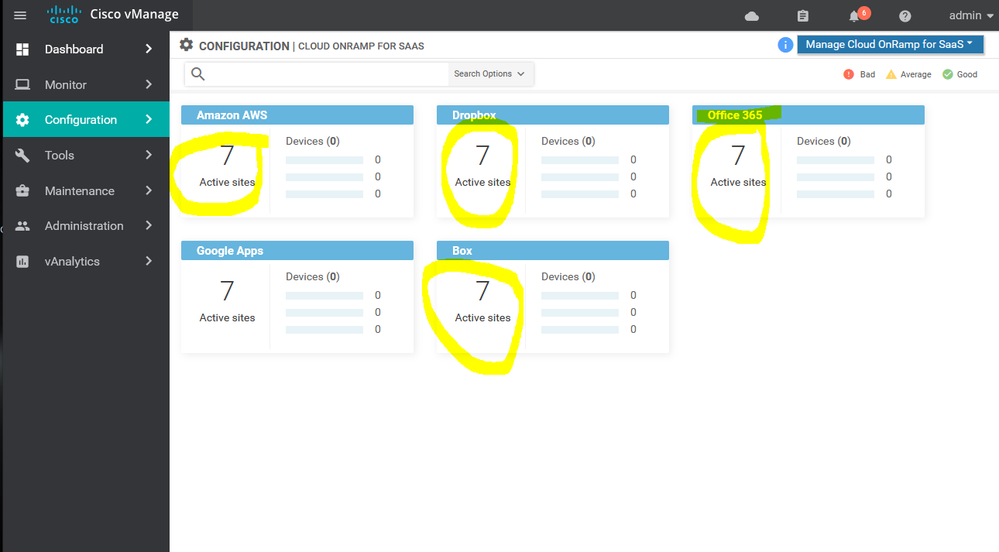
- cloud onRamp for Saas & laas :-
Cloud OnRamp for SaaS optimizes the performance of Software as a Service (SaaS) cloud applications based on network loss and latency SLA . Cloud OnRamp for SaaS provides clear visibility of the performance of individual applications and automatically chooses the best path for each one even MPLS , BIZ-Internet , 4 G Etc...
Although Cloud onRamp addresses both IaaS and SaaS providers, it's operate for the two types of cloud. With IaaS providers, such as AWS and Azure , Cloud OnRamp for SaaS calculates a value called the Viptela Quality of Experience , you also enable Cloud OnRamp for SaaS on the gateway site , viptela support some of the application now such as Microsoft Office 365 , oracle , sales forces , Zoho , Etc...
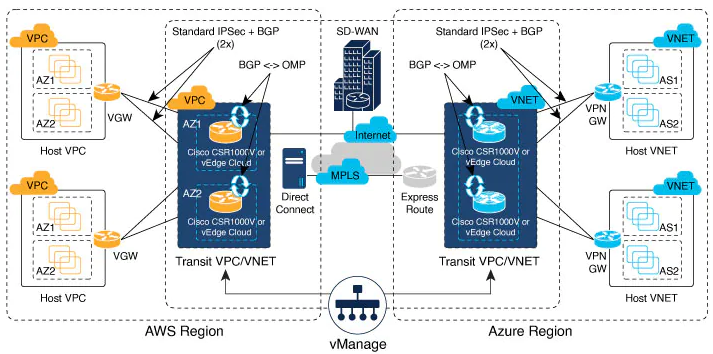
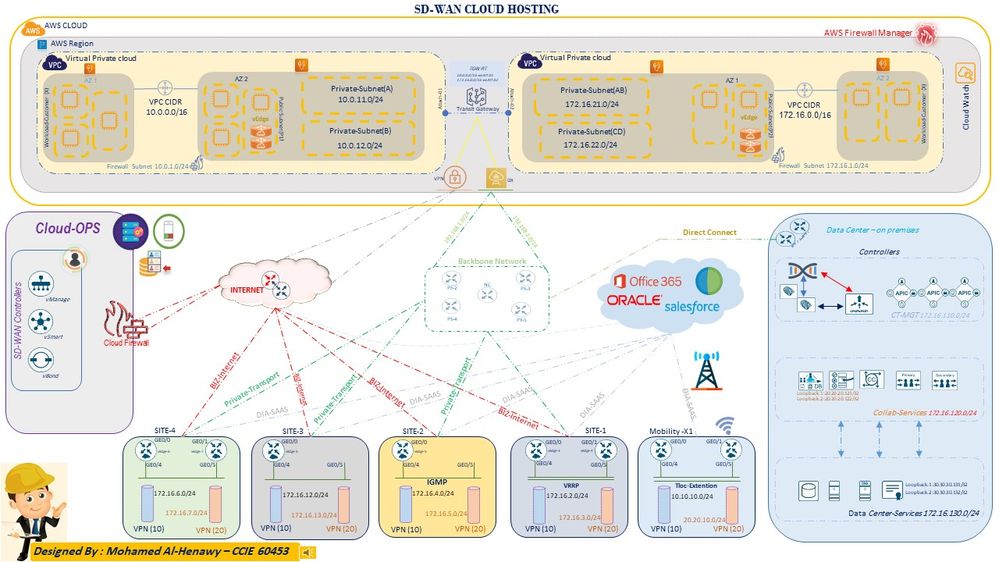
Cloud OnRamp for IaaS you can read more helpful details here :
The Cloud onRamp for IaaS works in conjunction with AWS virtual private clouds (VPCs) and Azure virtual networks (VNets). The following image provides a high level overview of multi-cloud onRamp for IaaS.
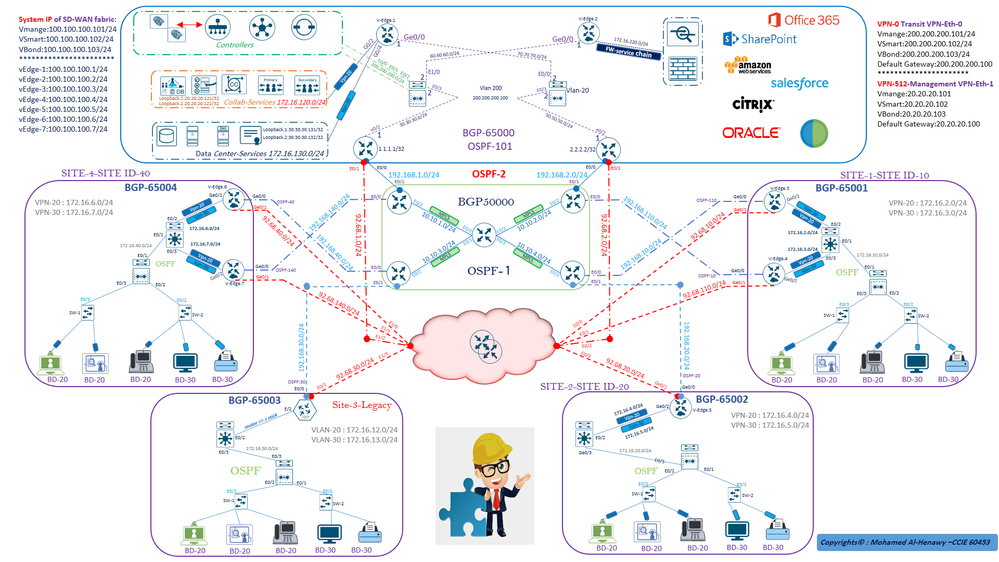
******* LAB TOPOLOGY *******
** Initial Configuration for Devices & SD-WAN Controllers **
DC-sw-1
hostname -DC-1
!
aaa new-model
!
clock timezone EET 2 0
!
ip cef
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
interface Ethernet0/2
!
interface Ethernet0/3
no switchport
ip address 30.30.30.2 255.255.255.0
duplex auto
!
interface Ethernet1/0
no switchport
ip address 60.60.60.2 255.255.255.0
duplex auto
!
interface Ethernet2/2
switchport trunk encapsulation dot1q
switchport mode trunk
duplex auto
!
interface Vlan200
ip address 200.200.200.101 255.255.255.0
standby version 2
standby 200 ip 200.200.200.100
standby 200 timers 1 3
standby 200 preempt
standby 200 authentication Cisco
!
router ospf 101
redistribute connected subnets
redistribute static subnets
network 11.11.11.8 0.0.0.3 area 0
network 30.30.30.0 0.0.0.255 area 0
network 60.60.60.0 0.0.0.255 area 0
network 200.200.200.0 0.0.0.255 area 0
!
ip forward-protocol nd
!
ip http server
ip http secure-server
DC-sw-2
hostname DC-2
!
boot-start-marker
boot-end-marker
!
aaa new-model
clock timezone EET 2 0
!
ip cef
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
interface Ethernet0/0
no switchport
ip address 70.70.70.2 255.255.255.0
duplex auto
!
interface Ethernet0/3
no switchport
ip address 50.50.50.2 255.255.255.0
duplex auto
!
interface Ethernet2/2
switchport trunk encapsulation dot1q
switchport mode trunk
duplex auto
!
interface Ethernet5/2
switchport access vlan 200
!
interface Vlan200
ip address 200.200.200.102 255.255.255.0
standby version 2
standby 200 ip 200.200.200.100
standby 200 timers 1 3
standby 200 preempt
standby 200 authentication Cisco
!
router ospf 101
redistribute connected subnets
redistribute static subnets
network 11.11.11.8 0.0.0.3 area 0
network 50.50.50.0 0.0.0.255 area 0
network 70.70.70.0 0.0.0.255 area 0
network 200.200.200.0 0.0.0.255 area 0
!
ip forward-protocol nd
!
ip http server
ip http secure-server
hostname DC-ED-1
!
boot-start-marker
boot-end-marker
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip cef
!
multilink bundle-name authenticated
!
cts logging verbose
!
redundancy
!
interface Ethernet0/0
ip address 192.168.1.2 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.1.2 255.255.255.0
!
interface Ethernet0/2
ip address 30.30.30.1 255.255.255.0
!
router ospf 101
network 30.30.30.0 0.0.0.255 area 0
!
router ospf 2
redistribute connected subnets
redistribute static subnets
redistribute bgp 65000 subnets
network 192.168.1.0 0.0.0.255 area 0
!
router bgp 65000
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 192.168.1.1 remote-as 50000
!
address-family ipv4
network 192.168.1.0
redistribute connected
redistribute static
redistribute ospf 2
neighbor 192.168.1.1 activate
exit-address-family
!
ip forward-protocol nd
ip http server
ip http secure-server
hostname DC-ED-2
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
!
cts logging verbose
!
redundancy
!
interface Ethernet0/0
ip address 192.168.2.2 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.2.2 255.255.255.0
!
interface Ethernet0/2
ip address 50.50.50.1 255.255.255.0
!
router ospf 101
network 50.50.50.0 0.0.0.255 area 0
!
router ospf 2
redistribute bgp 65000 subnets
network 192.168.2.0 0.0.0.255 area 0
!
router bgp 65000
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 192.168.2.1 remote-as 50000
!
address-family ipv4
network 192.168.2.0
redistribute connected
redistribute static
redistribute ospf 2
neighbor 192.168.2.1 activate
exit-address-family
!
ip forward-protocol nd
ip http server
ip http secure-server
!
control-plane
hostname SP-C
!
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Ethernet0/0
ip address 10.10.1.1 255.255.255.0
!
interface Ethernet0/1
ip address 10.10.3.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.2.1 255.255.255.0
!
interface Ethernet0/3
ip address 10.10.4.1 255.255.255.0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 1.1.1.1
redistribute connected subnets
redistribute static subnets
network 1.1.1.1 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 1.1.1.1
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor SP-CORE peer-group
neighbor SP-CORE remote-as 50000
neighbor SP-CORE log-neighbor-changes
neighbor SP-CORE update-source Loopback0
neighbor 2.2.2.2 peer-group SP-CORE
neighbor 3.3.3.3 peer-group SP-CORE
neighbor 4.4.4.4 peer-group SP-CORE
neighbor 5.5.5.5 peer-group SP-CORE
!
address-family ipv4
network 1.1.1.1 mask 255.255.255.255
redistribute connected
redistribute static
redistribute ospf 1
neighbor SP-CORE send-community both
neighbor SP-CORE route-reflector-client
neighbor SP-CORE next-hop-self
neighbor 2.2.2.2 activate
neighbor 3.3.3.3 activate
neighbor 4.4.4.4 activate
neighbor 5.5.5.5 activate
exit-address-family
!
address-family vpnv4
neighbor SP-CORE send-community both
neighbor SP-CORE route-reflector-client
neighbor SP-CORE next-hop-self
neighbor 2.2.2.2 activate
neighbor 3.3.3.3 activate
neighbor 4.4.4.4 activate
neighbor 5.5.5.5 activate
exit-address-family
!
ip forward-protocol nd
!
ip http server
ip http secure-server
control-plane
hostname SP-PE-2
!
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf DC-1
rd 1:1
route-target export 1:1
route-target import 1:1
route-target import 1:7
route-target import 2:2
route-target import 2:4
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip vrf S4-V7
rd 1:7
route-target export 1:7
route-target import 1:7
route-target import 1:1
route-target import 2:2
route-target import 2:4
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S4-V7
ip address 192.168.140.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding DC-1
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.1.2 255.255.255.0
!
router ospf 2 vrf DC-1
redistribute bgp 50000 subnets
network 192.168.1.0 0.0.0.255 area 0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 2.2.2.2
redistribute bgp 50000 subnets
network 2.2.2.2 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 2.2.2.2
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 50000
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 2.2.2.2 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf DC-1
network 192.168.1.0
redistribute connected
redistribute static
redistribute ospf 2
neighbor 192.168.1.2 remote-as 65000
neighbor 192.168.1.2 activate
exit-address-family
!
address-family ipv4 vrf S4-V7
network 192.168.140.0
redistribute connected
redistribute static
neighbor 192.168.140.2 remote-as 65004
neighbor 192.168.140.2 activate
exit-address-family
!
ip forward-protocol nd
!
ip http server
ip http secure-server
!
control-plane
hostname SP-PE-3
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf DC-2
rd 2:2
route-target export 2:2
route-target import 2:2
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip vrf S1-V4
rd 2:4
route-target export 2:4
route-target import 2:4
route-target import 1:7
route-target import 1:1
route-target import 2:2
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S1-V4
ip address 192.168.110.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding DC-2
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.2.2 255.255.255.0
!
router ospf 2 vrf DC-2
redistribute bgp 50000 subnets
network 192.168.2.0 0.0.0.255 area 0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 3.3.3.3
redistribute bgp 50000 subnets
network 3.3.3.3 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 3.3.3.3
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 50000
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 3.3.3.3 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf DC-2
network 192.168.2.0
redistribute connected
redistribute static
redistribute ospf 2
neighbor 192.168.2.2 remote-as 65000
neighbor 192.168.2.2 activate
exit-address-family
!
address-family ipv4 vrf S1-V4
network 192.168.110.0
redistribute connected
redistribute static
neighbor 192.168.110.2 remote-as 65001
neighbor 192.168.110.2 activate
exit-address-family
!
ip forward-protocol nd
ip http server
ip http secure-server
control-plane
hostname SP-PE-4
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf S3-V1
rd 4:1
route-target export 4:1
route-target import 4:1
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip vrf S4-V6
rd 4:6
route-target export 4:6
route-target import 4:6
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:1
route-target import 5:3
route-target import 5:1
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S4-V6
ip address 192.168.40.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding S3-V1
ip address 192.168.30.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.3.2 255.255.255.0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 4.4.4.4
network 4.4.4.4 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 4.4.4.4
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 50000
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 4.4.4.4 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf S3-V1
network 192.168.30.0
redistribute connected
redistribute static
neighbor 192.168.30.2 remote-as 65003
neighbor 192.168.30.2 activate
exit-address-family
!
address-family ipv4 vrf S4-V6
network 192.168.40.0
redistribute connected
redistribute static
neighbor 192.168.40.2 remote-as 65004
neighbor 192.168.40.2 activate
exit-address-family
!
ip forward-protocol nd
!
ip http server
ip http secure-server
control-plane
hostname SP-PE-5
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf S1-V3
rd 5:3
route-target export 5:3
route-target import 5:3
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:1
route-target import 4:6
route-target import 5:1
!
ip vrf S2-V1
rd 5:1
route-target export 5:1
route-target import 5:1
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:1
route-target import 4:6
route-target import 5:3
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
!
interface Loopback0
ip address 5.5.5.5 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S1-V3
ip address 192.168.10.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding S2-V1
ip address 192.168.20.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.4.2 255.255.255.0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 5.5.5.5
network 5.5.5.5 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 5.5.5.5
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 50000
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 5.5.5.5 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf S1-V3
network 192.168.10.0
redistribute connected
redistribute static
neighbor 192.168.10.2 remote-as 65001
neighbor 192.168.10.2 activate
exit-address-family
!
address-family ipv4 vrf S2-V1
network 192.168.20.0
redistribute connected
redistribute static
neighbor 192.168.20.2 remote-as 65002
neighbor 192.168.20.2 activate
exit-address-family
!
ip forward-protocol nd
!
ip http secure-server
control-plane
!
hostname Public-Internet
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
!
cts logging verbose
!
redundancy
!
interface Ethernet0/0
ip address 92.68.10.1 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.110.1 255.255.255.0
!
interface Ethernet0/2
ip address 92.68.2.1 255.255.255.0
!
interface Ethernet0/3
ip address 92.68.20.1 255.255.255.0
!
interface Ethernet1/0
ip address 92.68.40.1 255.255.255.0
!
interface Ethernet1/1
ip address 92.68.140.1 255.255.255.0
!
interface Ethernet1/2
ip address 92.68.1.1 255.255.255.0
!
interface Ethernet1/3
ip address 92.68.30.1 255.255.255.0
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
ip route 200.200.200.0 255.255.255.0 92.68.1.2 10
ip route 200.200.200.0 255.255.255.0 92.68.2.2 20
control-plane
!
---------------------------------------------------------------------------------------------------------
Public Internet Verification :
DC-ED-1(config)#do pin www.google.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 114/126/135 ms
------------------------------------------
DC-ED-2(config)#do pin www.google.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 105/114/120 ms
------------------------------------------
Public-Internet(config)#do ping www.google.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 105/115/122 ms
Public-Internet(config)#
------------------------------------------
MPLS Verification :
SP-C(config)#do show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 2.2.2.2/32 5428 Et0/0 10.10.1.2
17 Pop Label 3.3.3.3/32 6608 Et0/2 10.10.2.2
18 Pop Label 4.4.4.4/32 1770 Et0/1 10.10.3.2
19 Pop Label 5.5.5.5/32 2360 Et0/3 10.10.4.2
SP-C(config)#do show mpls ldp neighbor
Peer LDP Ident: 2.2.2.2:0; Local LDP Ident 1.1.1.1:0
TCP connection: 2.2.2.2.38221 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1689/1688; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/0, Src IP addr: 10.10.1.2
Addresses bound to peer LDP Ident:
10.10.1.2 2.2.2.2
Peer LDP Ident: 3.3.3.3:0; Local LDP Ident 1.1.1.1:0
TCP connection: 3.3.3.3.30480 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1683/1688; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.2.2
Addresses bound to peer LDP Ident:
10.10.2.2 3.3.3.3
Peer LDP Ident: 4.4.4.4:0; Local LDP Ident 1.1.1.1:0
TCP connection: 4.4.4.4.49818 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1686/1691; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/1, Src IP addr: 10.10.3.2
Addresses bound to peer LDP Ident:
10.10.3.2 4.4.4.4
Peer LDP Ident: 5.5.5.5:0; Local LDP Ident 1.1.1.1:0
TCP connection: 5.5.5.5.34188 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1690/1693; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/3, Src IP addr: 10.10.4.2
Addresses bound to peer LDP Ident:
10.10.4.2 5.5.5.5
------------------------------------------
SP-PE-2#show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.1.1
17 Pop Label 10.10.2.0/24 0 Et0/2 10.10.1.1
18 Pop Label 10.10.3.0/24 0 Et0/2 10.10.1.1
19 Pop Label 10.10.4.0/24 0 Et0/2 10.10.1.1
20 17 3.3.3.3/32 0 Et0/2 10.10.1.1
21 18 4.4.4.4/32 0 Et0/2 10.10.1.1
22 19 5.5.5.5/32 0 Et0/2 10.10.1.1
23 No Label 192.168.1.0/24[V] \
3990 aggregate/DC-1
24 No Label 192.168.140.0/24[V] \
570 aggregate/S4-V7
25 No Label 30.30.30.0/24[V] 570 Et0/1 192.168.1.2
26 No Label 92.68.1.0/24[V] 0 Et0/1 192.168.1.2
SP-PE-2#show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 2.2.2.2:0
TCP connection: 1.1.1.1.646 - 2.2.2.2.38221
State: Oper; Msgs sent/rcvd: 1690/1691; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.1.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------
SP-PE-3(config)#do show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.2.1
17 Pop Label 10.10.1.0/24 0 Et0/2 10.10.2.1
18 Pop Label 10.10.3.0/24 0 Et0/2 10.10.2.1
19 Pop Label 10.10.4.0/24 0 Et0/2 10.10.2.1
20 16 2.2.2.2/32 0 Et0/2 10.10.2.1
21 18 4.4.4.4/32 0 Et0/2 10.10.2.1
22 19 5.5.5.5/32 0 Et0/2 10.10.2.1
23 No Label 192.168.2.0/24[V] \
3420 aggregate/DC-2
24 No Label 192.168.110.0/24[V] \
570 aggregate/S1-V4
25 No Label 50.50.50.0/24[V] 2394 Et0/1 192.168.2.2
26 No Label 92.68.2.0/24[V] 0 Et0/1 192.168.2.2
SP-PE-3(config)#do show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 3.3.3.3:0
TCP connection: 1.1.1.1.646 - 3.3.3.3.30480
State: Oper; Msgs sent/rcvd: 1691/1686; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.2.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------
SP-PE-4#sho mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.3.1
17 Pop Label 10.10.1.0/24 0 Et0/2 10.10.3.1
18 Pop Label 10.10.2.0/24 0 Et0/2 10.10.3.1
19 Pop Label 10.10.4.0/24 0 Et0/2 10.10.3.1
20 16 2.2.2.2/32 0 Et0/2 10.10.3.1
21 17 3.3.3.3/32 0 Et0/2 10.10.3.1
22 19 5.5.5.5/32 0 Et0/2 10.10.3.1
23 No Label 192.168.30.0/24[V] \
1140 aggregate/S3-V1
24 No Label 192.168.40.0/24[V] \
570 aggregate/S4-V6
SP-PE-4#show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 4.4.4.4:0
TCP connection: 1.1.1.1.646 - 4.4.4.4.49818
State: Oper; Msgs sent/rcvd: 1695/1690; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.3.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------
SP-PE-5#show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.4.1
17 Pop Label 10.10.1.0/24 0 Et0/2 10.10.4.1
18 Pop Label 10.10.2.0/24 0 Et0/2 10.10.4.1
19 Pop Label 10.10.3.0/24 0 Et0/2 10.10.4.1
20 16 2.2.2.2/32 0 Et0/2 10.10.4.1
21 17 3.3.3.3/32 0 Et0/2 10.10.4.1
22 18 4.4.4.4/32 0 Et0/2 10.10.4.1
23 No Label 192.168.10.0/24[V] \
1140 aggregate/S1-V3
24 No Label 192.168.20.0/24[V] \
1140 aggregate/S2-V1
SP-PE-5#show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 5.5.5.5:0
TCP connection: 1.1.1.1.646 - 5.5.5.5.34188
State: Oper; Msgs sent/rcvd: 1699/1696; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.4.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------------------------------------------------
BGP Verification :
SP-C(config)#do show ip bgp vpnv4 all summary
Neighbor V AS Msg Rcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2.2.2.2 4 50000 230 234 13 0 0 03:16:52 4
3.3.3.3 4 50000 230 234 13 0 0 03:16:52 4
4.4.4.4 4 50000 227 237 13 0 0 03:16:52 2
5.5.5.5 4 50000 228 236 13 0 0 03:16:52 2
------------------------------------------
SP-PE-2(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1107 1102 59 0 0 16:29:01 8
192.168.1.2 4 65000 1138 1152 59 0 0 17:09:28 3
192.168.140.2 4 65004 0 0 1 0 0 19:09:28 3
------------------------------------------
SP-PE-3(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1105 1111 59 0 0 16:32:19 8
192.168.2.2 4 65000 1131 1147 59 0 0 17:03:38 3
192.168.110.2 4 65001 0 0 1 0
------------------------------------------
SP-PE-4(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1114 1102 67 0 0 16:33:40 10
192.168.30.2 4 65003 0 0 1 0 0 never Idle
192.168.40.2 4 65004 0 0 1 0
------------------------------------------
SP-PE-5(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1112 1107 69 0 0 16:34:27 10
192.168.10.2 4 65001 0 0 1 0 0 never Active
192.168.20.2 4 65002 0 0 1 0
------------------------------------------------------------------------------------
**Viptela Controllers initial configuration**
NOTE : All Controllers Work with version ((((viptela 20.3.4))))
{Vmanage initial configuration }
configure
system
host-name vmanage
system-ip 100.100.100.101
site-id 1
admin-tech-on-failure
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$cUCfm1swmEQhJ1zJ$pnOPy.FKMGCxzM.FPeiEh0RNQXP5SXXBgSn3X.qPC39vZnsOsBpfXpDKd/NyLimCwc6txSIMzax9wNI3OCxfk1
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
vpn 0
interface eth0
ip address 200.200.200.101/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth1
ip dhcp-client
no shutdown
!
ip route 0.0.0.0/0 192.168.205.1
!
------------------------------------------------------------------------------------
{Vsmart initial configuration }
configure
system
host-name vsmart
system-ip 100.100.100.102
site-id 1
admin-tech-on-failure
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$heVRjPJAGcTR/AX5$TPN9s2iG1ogb7.3OtfeWCKieIx90KMuet2Vzg2Lr4c1g/sLziUAgQF20UgpWfMOL6AfH3Ek8MBtv4lVZe3RUa0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
!
vpn 0
interface eth0
ip address 200.200.200.102/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
!
------------------------------------------------------------------------------------
{Vbond initial configuration }
system
host-name vbond
system-ip 100.100.100.103
site-id 1
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103 local
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$GcfTQKxQdG5jHL75$WwWDC6KW6zWUVhKDxgWpBo/EjGL8dyw A7/irYodz4ne5xYt1lgT.8gu.vkR2ngkIcNs/7JVDs2XV99UWrG0Ly1
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 200.200.200.103/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
------------------------------------------------------------------------------------
Then We will access to vmanage as GUI https://192.168.205.145/welcome.html
Username : admin
Password : admin
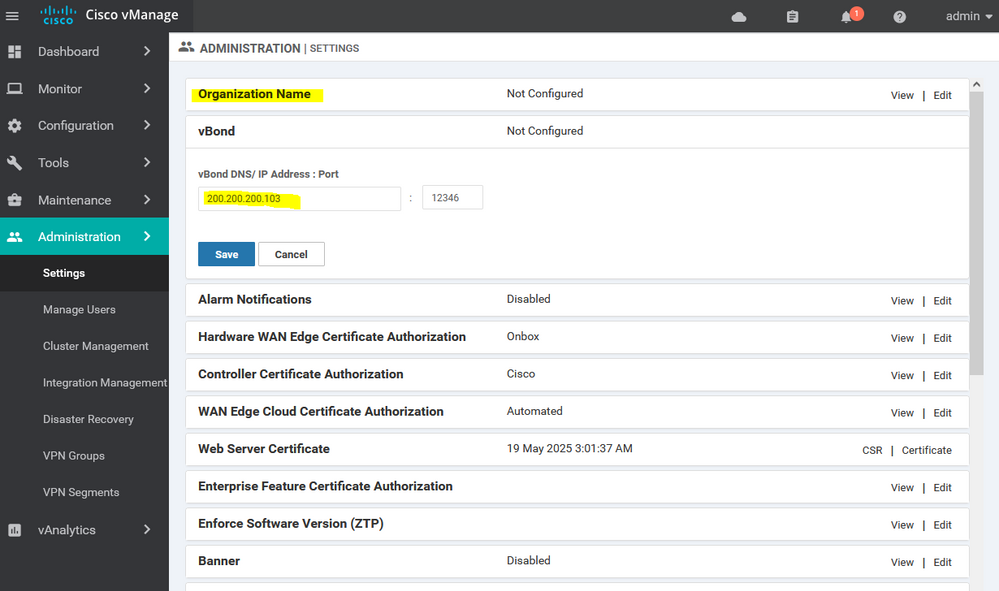
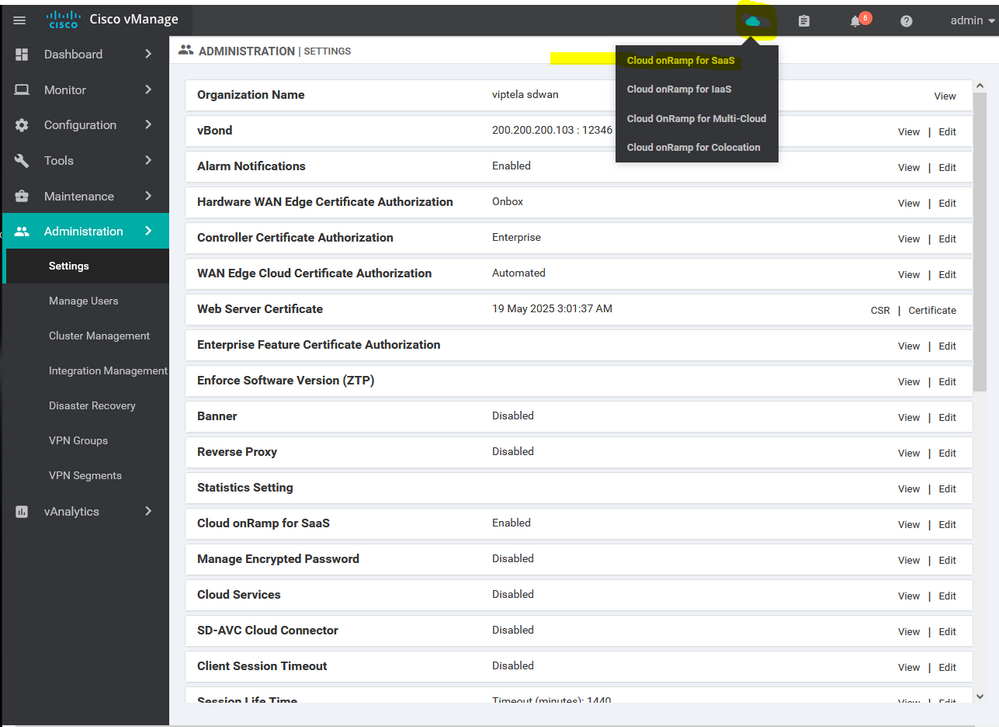
Navigate to Administrator > Settings. Verify that Organization Name is correctly displayed.( Organization Name is very important point so take care )
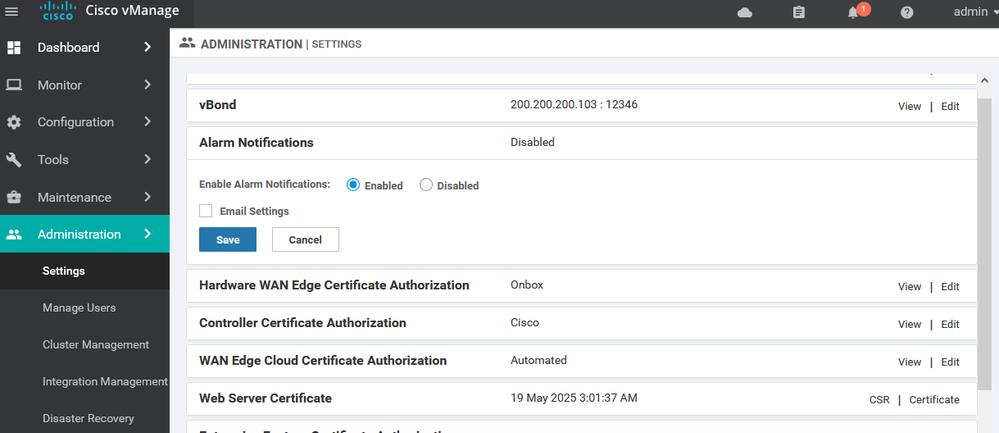
Edit the vBond settings and enter vBond Public IP address 200.200.200.103
Enable the alarm notification Through Mail
Add Smart account of my organization
Generate the Root CA certificate
vmanage# vshell
vmanage:~$ openssl genrsa -out ROOTCA.key 2048
Generating RSA private key, 2048 bit long modulus
......
...............
e is 65537 (0x10001)
---------------------------------------------------
To create a Root CA cert named ROOTCA.pem
openssl req -x509 -new -nodes -key ROOTCA.key -sha256 -days 2000 \
-subj "/C=cisco sdwan/CN=cisco sdwan" \
-out ROOTCA.pem
---------------------------------------------------
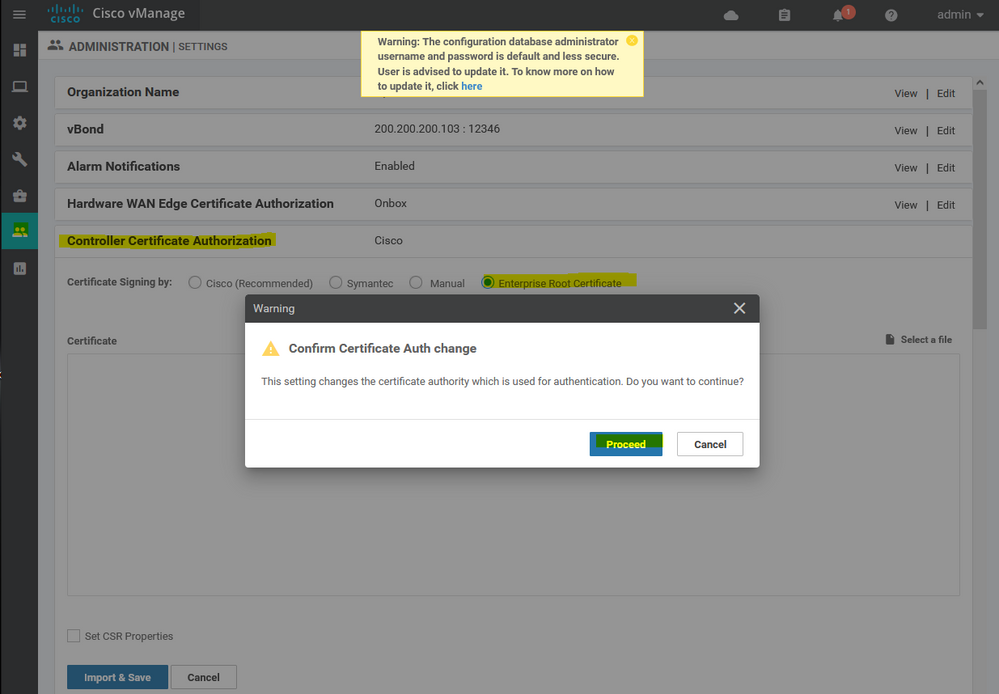
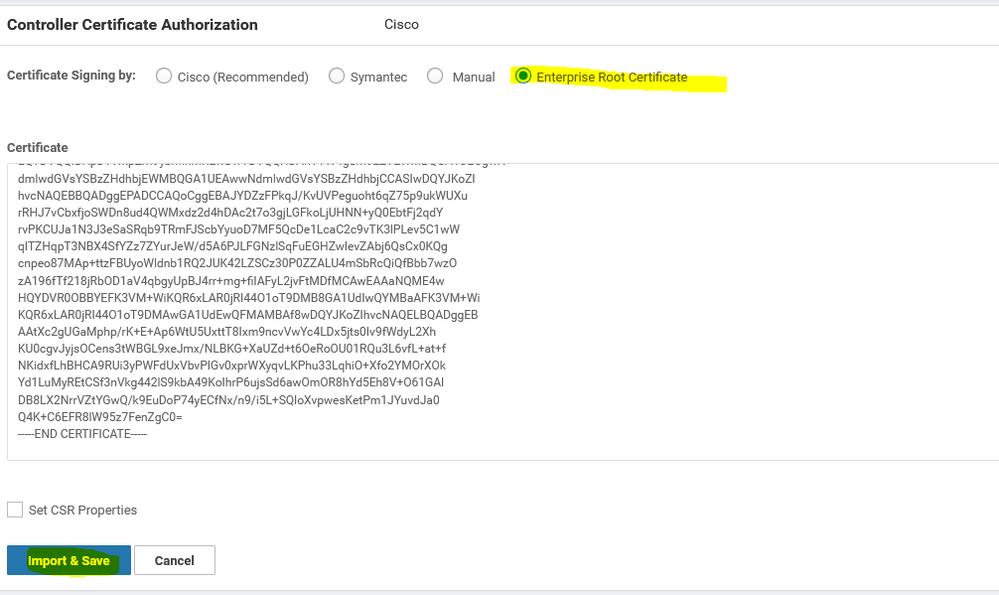
Viptela Sdwan have more than one option for the certificate options include ( Cisco , Symantec , Manual approach , Enterprise certificate ) here we are going to Change the Controller Certificate Authorization to use Enterprise Root Certificate
vmanage:~$ ls
ROOTCA.key ROOTCA.pem archive_id_rsa.pub
vmanage:~$ cat ROOTCA.pem
-----Get the certificate and take it copy past to the Enterprise Root Certificate -----
To create a CSR for the vManage. Navigate to the certificates section Administrator - Certificate - controllers - vmanage - setting -- Generate CSR
Then Cat vmanage.crt -- Copy
install certificate -- Past -- install
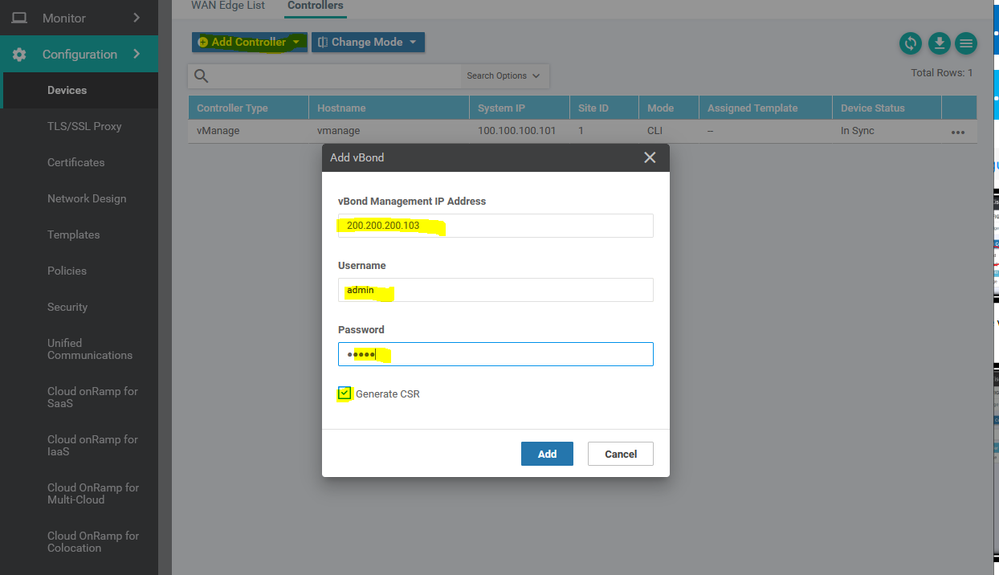
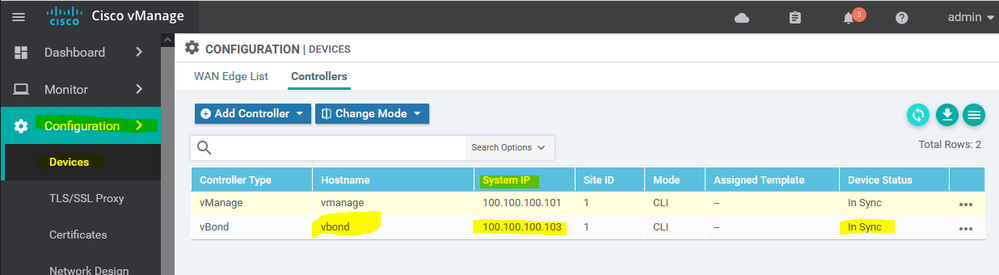
Add the vbond and vsmart to the vmanage
Configuration -- Devices -- Controllers -- Add -- vbond
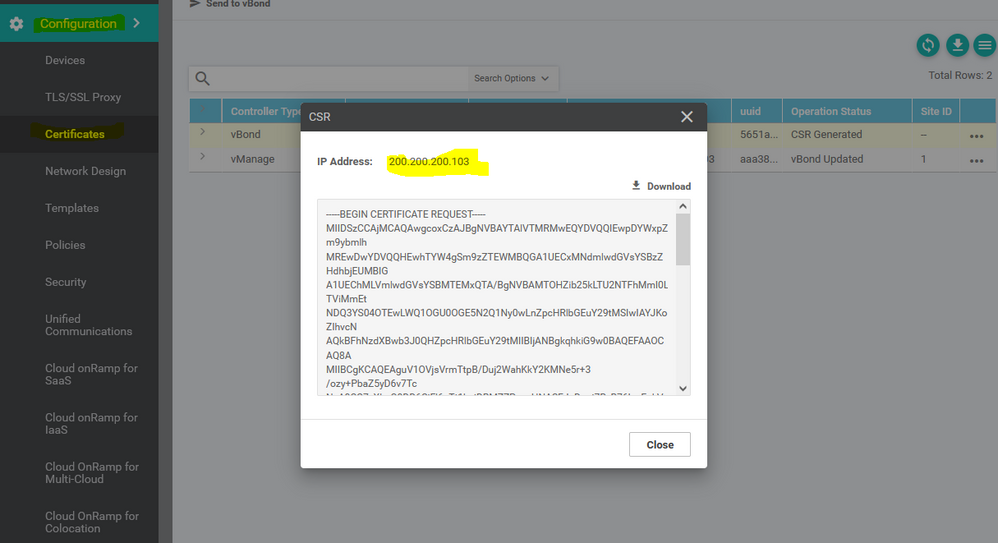
Then get copy from the vbond CSR to past on the vmanage vmanage:~$ vim vbond.csr
vmanage:~$ cat vbond.crt --- get copy and pat on the vmanage instillation certificate
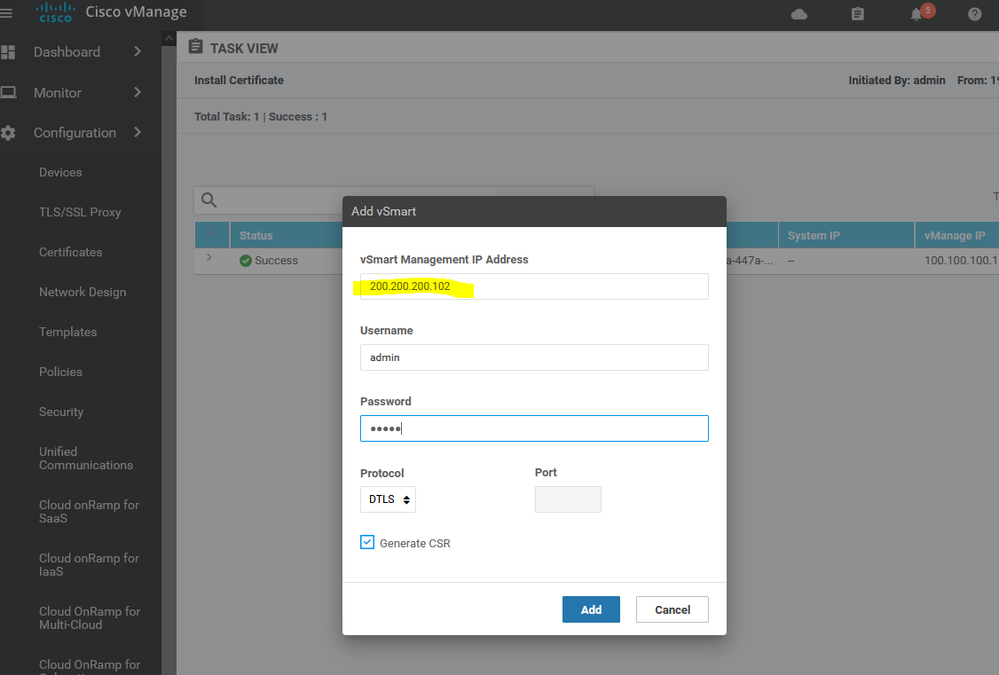
Add Vsmart
vmanage# show control connections
0 vsmart dtls 100.100.100.102 100.100.100.102 1 1 200.200.200.102 12346 200.200.200.102 12346 cisco sdwan default up 0:00:27:18
0 vbond dtls 100.100.100.103 100.100.100.103 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:43
1 vbond dtls 0.0.0.0 - 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:43
2 vbond dtls 0.0.0.0 - 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:43
3 vbond dtls 0.0.0.0 - 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:45
vmanage#
vmanage# show control connections
PEER PEER PEER
PEER PEER PEER CONFIGURED SITE DOMAIN PEER PRIV PEER PUB
INDEX TYPE PROT SYSTEM IP SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZATION REMOTE COLOR STATE UPTIME
----------------------------------------------------------
0 vsmart dtls 100.100.100.102 100.100.100.102 1 1 200.200.200.102 12346 200.200.200.102 12346 cisco sdwan default up 0:00:27:32
0 vbond dtls 100.100.100.103 100.100.100.103 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:56
1 vbond dtls 0.0.0.0 - 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:57
2 vbond dtls 0.0.0.0 - 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:56
3 vbond dtls 0.0.0.0 - 0 0 200.200.200.103 12346 200.200.200.103 12346 cisco sdwan default up 0:00:49:59
---------------------------------------------------------
vEdges and traditional Site initial configurations
---------------------------------------------------------
vEdge (1)
system
host-name vedge1
system-ip 100.100.100.1
site-id 1
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$Nty8xQQcKl5s1yEU$t924Ps3198o2CiH0qnUgVvt6nwC9hw0ssH8G.X2dJaRU2qNg3lM25Vo.uKLKdLY/kFqx/e6Zk05LgntaV4DK.0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 70.70.70.1/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 70.70.70.2
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
vEdge (2)
system
host-name vedge2
system-ip 100.100.100.2
site-id 1
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$iS7UFUrpnpqn1.7T$VlgGKfs/pBU/Rnr6m7IMayWIPvOYuPuXUgLeUKFPrD4K9uNcjSvUmQdwxaMHG3UMRso8JkybCi9MydwPph8O70
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 60.60.60.1/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 60.60.60.2
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
vEdge (3)
system
host-name vedge3
system-ip 100.100.100.3
site-id 10
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$RnNIz7mLuLdtBTsj$8UvJFDadZ75GrxNaO2T.C6fm4uwkvDijvWdCJOInjw67O67S07yMBA2SpJJdUNFX1g0aoyCzGh7pJJ/p66Ste0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
redistribute static
redistribute connected
area 0
interface ge0/0
exit
exit
!
!
interface ge0/0
ip address 192.168.10.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.10.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
vEdge (4)
system
host-name vedge4
system-ip 100.100.100.4
site-id 10
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$kOQs8Nwnot.2zuvD$tHIMM3KHw5M9cdtNcN6FhOVNv8TvhHC stxYTS8dnnDL5MVIr0/JH.llJb11ic8pdhyfMatmo1tBHDk0mjdBb6/
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
area 0
interface ge0/0
exit
exit
!
!
interface ge0/0
ip address 192.168.110.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.110.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
vEdge (5)
vedge5# show running-config
system
host-name vedge5
system-ip 100.100.100.5
site-id 20
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$pNxenR.ErpM0H/1t$JZJX0gygSVf/GVQvQ/r5sPJzEqehHllPhtuwYxR0ud9Q52nyxl8cDSd8RUOpp.uiku67ALMSFkm6PMPE0qJCg0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
area 0
interface ge0/0
exit
exit
!
!
interface ge0/0
ip address 192.168.20.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.20.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
vEdge (6)
system
host-name vedge6
system-ip 100.100.100.6
site-id 40
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$aR8Zc0KH3Z6n4i/7$eY97oYSxLA9tGLkmPGbqhqPIuYWVT4SH1rfDbZeBWZaWsAWkVVMjVllt/ot02H4dsFxkR0i8p28PF10.Wq2TI0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
area 0
interface ge0/0
exit
exit
!
!
interface ge0/0
ip address 192.168.40.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.40.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
vEdge (7)
system
host-name vedge7
system-ip 100.100.100.7
site-id 40
admin-tech-on-failure
no route-consistency-check
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$FCfqkJyF4OxFw13o$q6v7jAkIPruzD94zjkrrYLAjtxIQ2PtiwaP2Z9qibkzwHBpU9Pxzi7uWRcNkyIC7eOf4C9swHFc5C8dXDxh.1.
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
area 0
interface ge0/0
exit
exit
!
!
interface ge0/0
ip address 192.168.140.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.140.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
---------------------------------------------------------
Traditional Site (3)
clock timezone EET 2 0
!
mmi polling-interval 60
!
ip cef
!
multilink bundle-name authenticated
redundancy
!
interface Ethernet0/0
ip address 192.168.30.2 255.255.255.0
no shut
!
router ospf 30
redistribute connected subnets
redistribute static subnets
network 192.168.30.0 0.0.0.255 area 0
!
ip forward-protocol nd
!
ip http server
!
ip http secure-server
---------------------------------------------------------
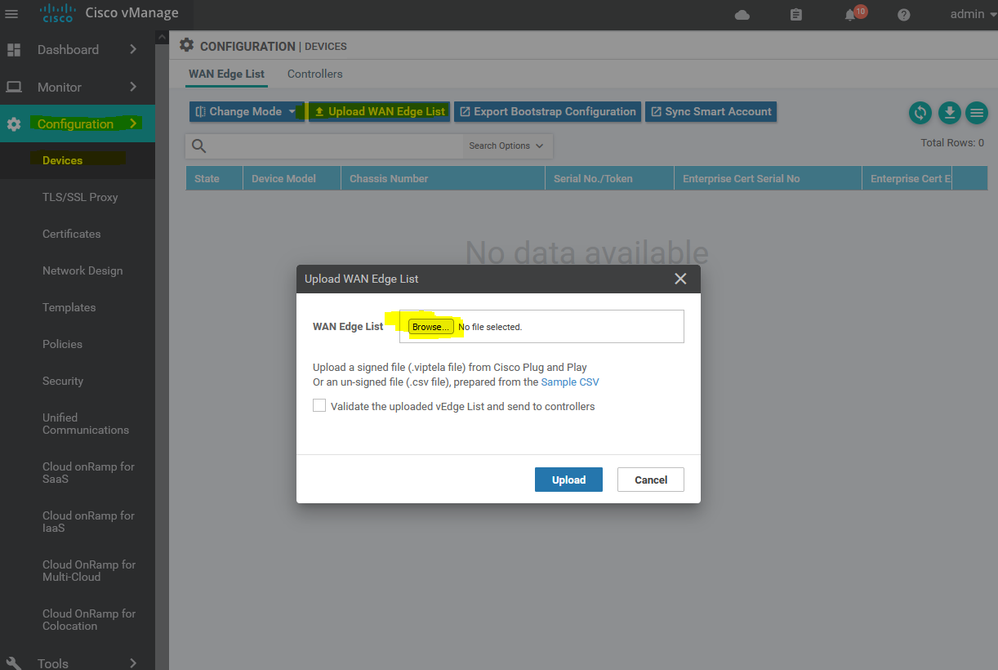
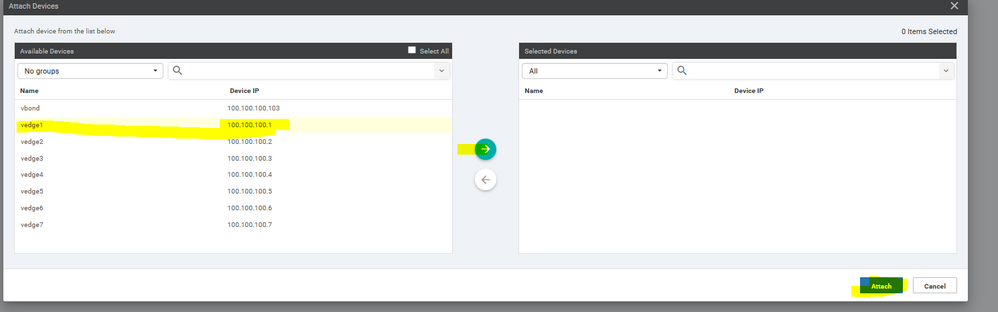
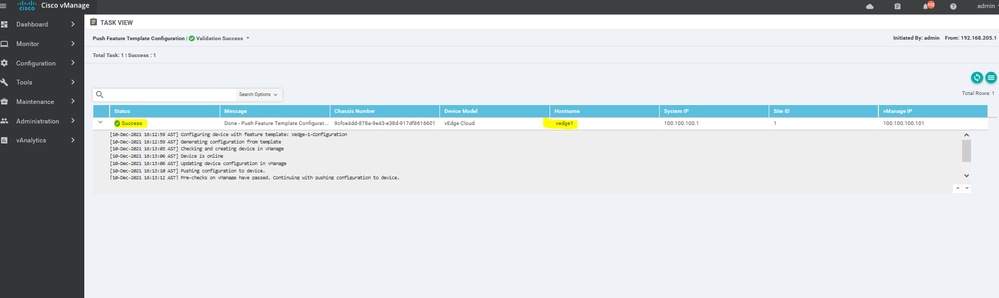
Start the process to upload the WAN Edge List serials and validate them through Check box
◘ Validate the uploaded vEdge List and send to controllers
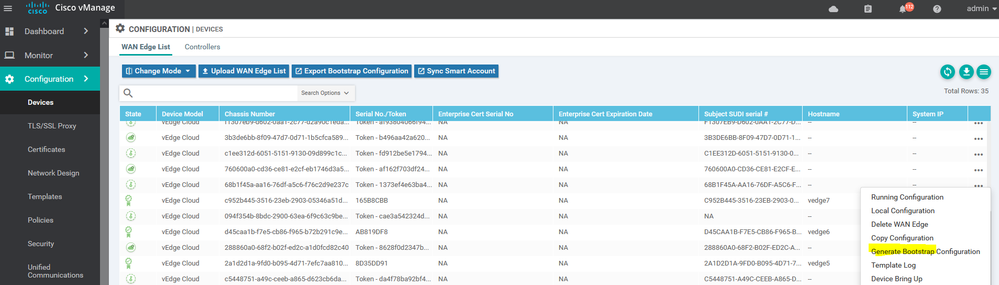
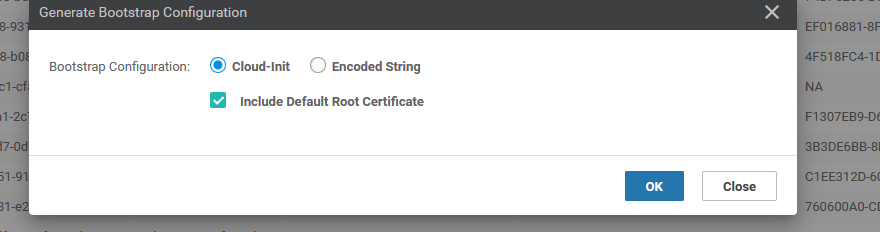
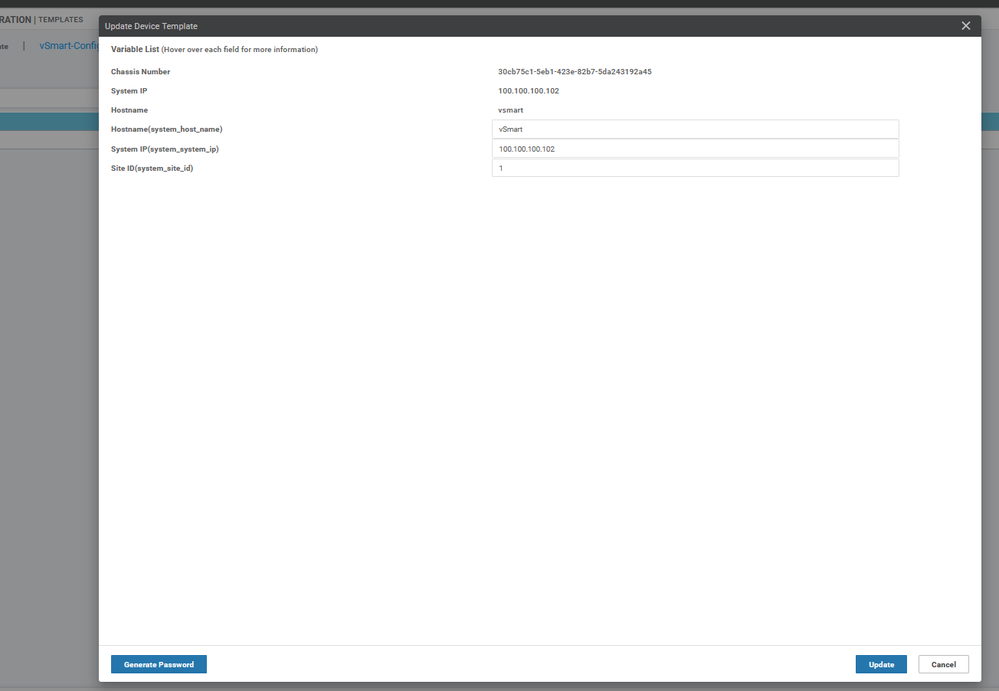
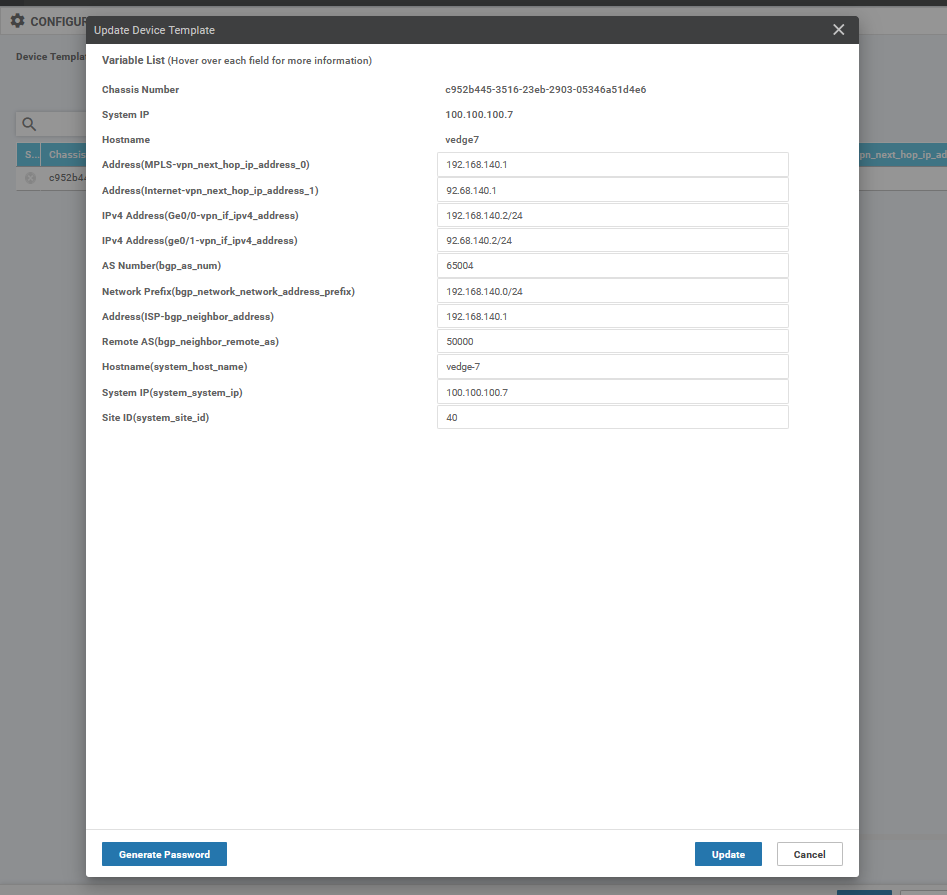
To add a virtual edge you need to generate a bootstrap file generating Chassis UUID and OTP Token
# request vedge-cloud activate chassis (UUID) token (OTP)
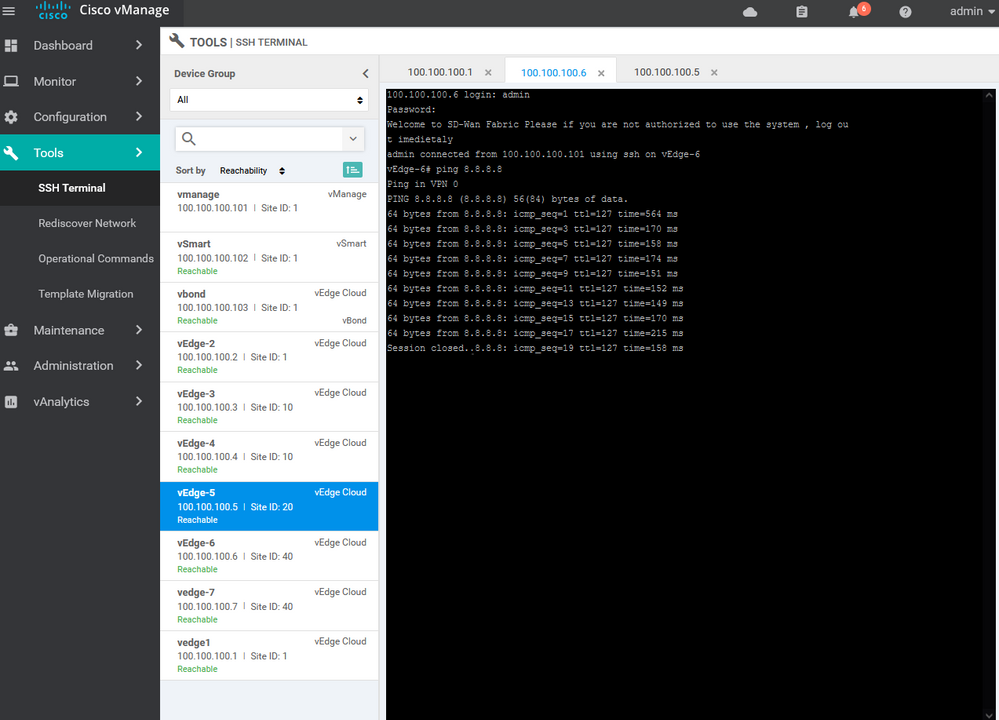
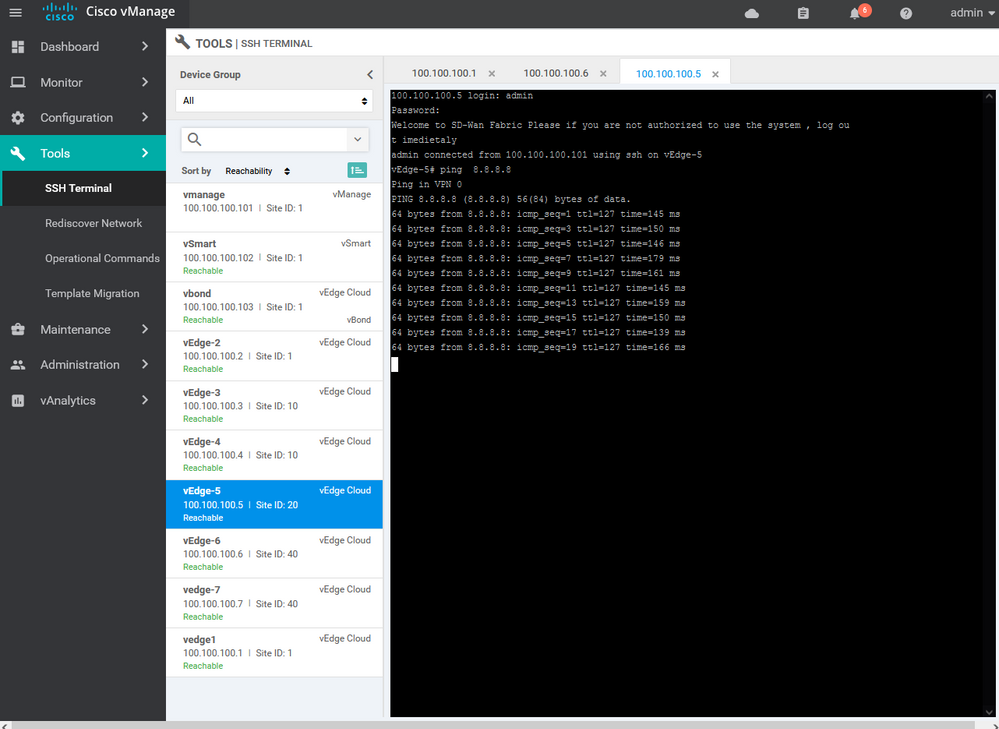
Example for verification :
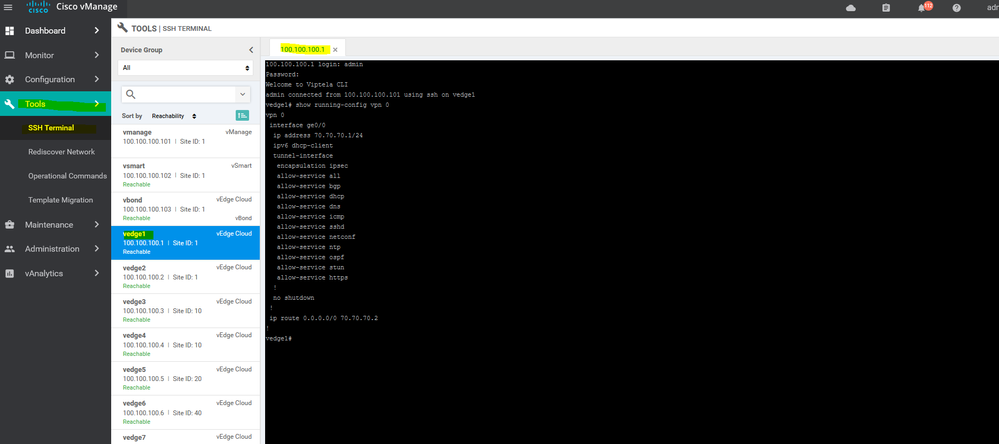
vedge7# show certificate serial
Chassis number: c952b445-3516-23eb-2903-00346C51d4e6 serial number: 165B8AAA
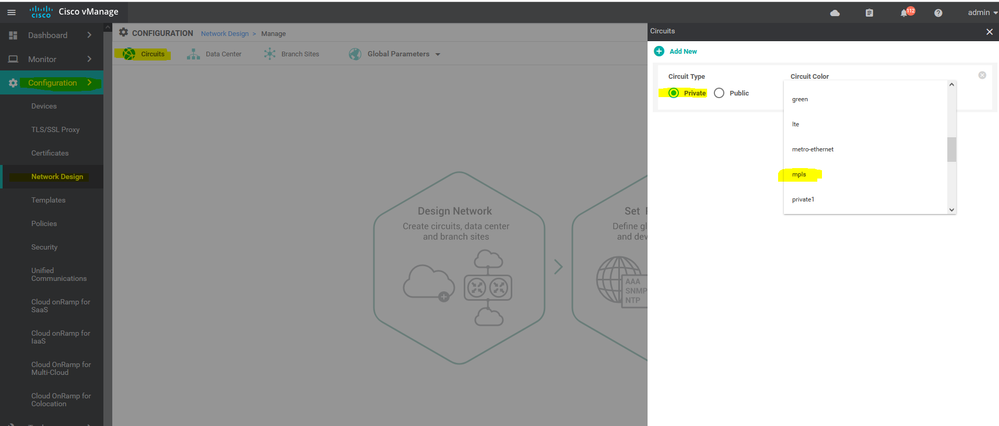
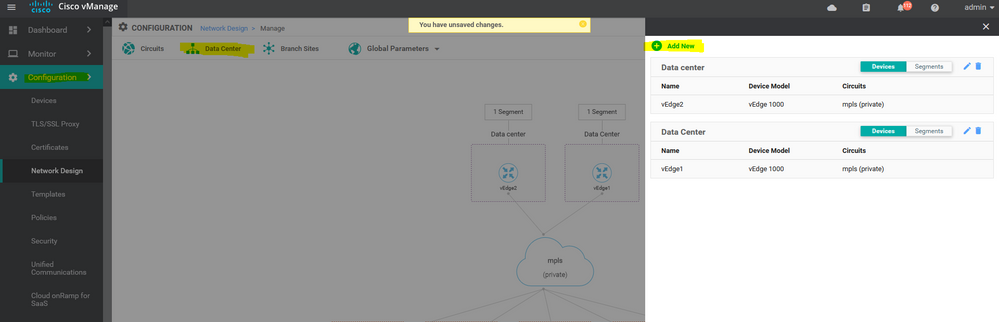
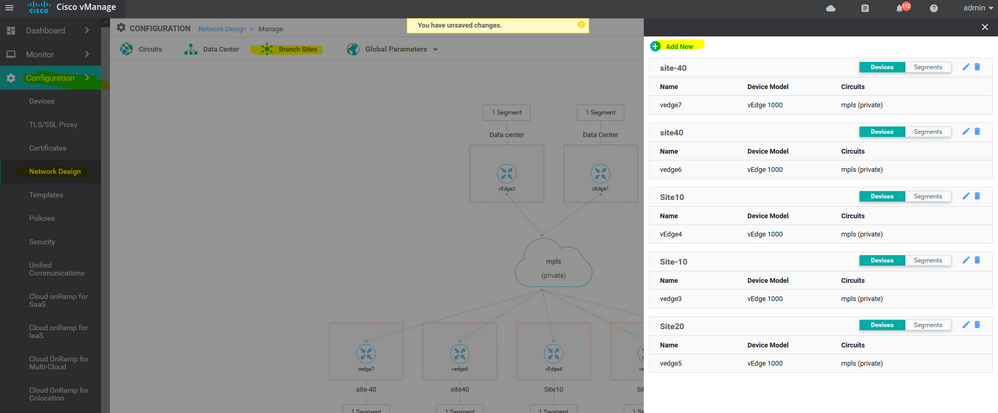
- Design the Network ||
Use the Network Design Feature to create and manage an overlay network topology. you can add circuits, data centers, and branch sites to a network topology, configure LAN, WAN, and management options for elements in the topology.
Start configuration for vEdges through Vmanage :
- Feature Template—Create feature templates for configuring features that you want to run on a Viptela device
- Device template consists of a number of feature templates. Each feature template defines the configuration for a particular Cisco SD-WAN software feature .
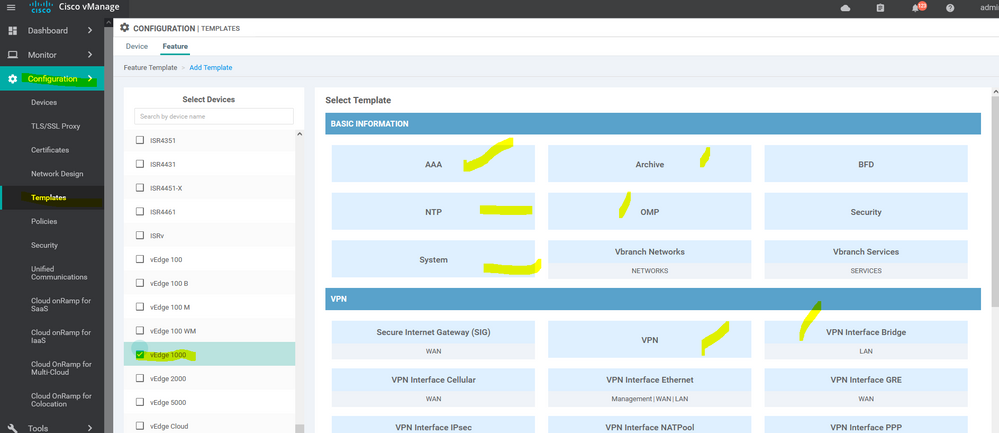
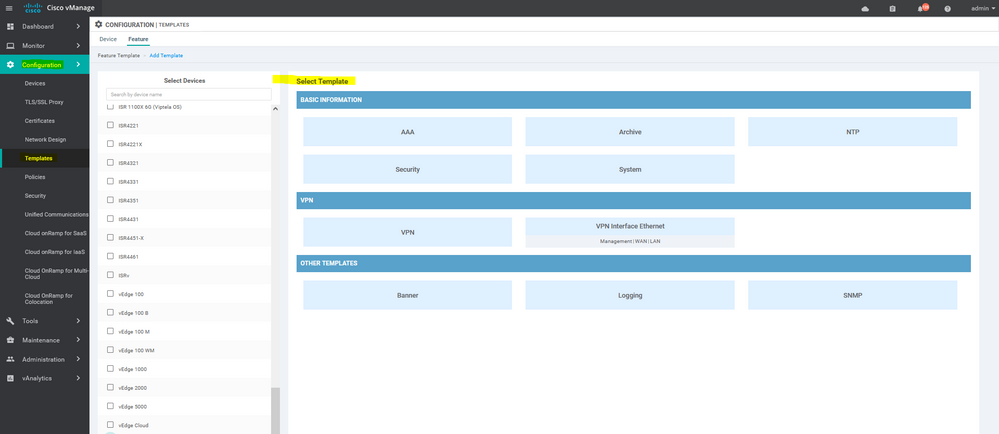
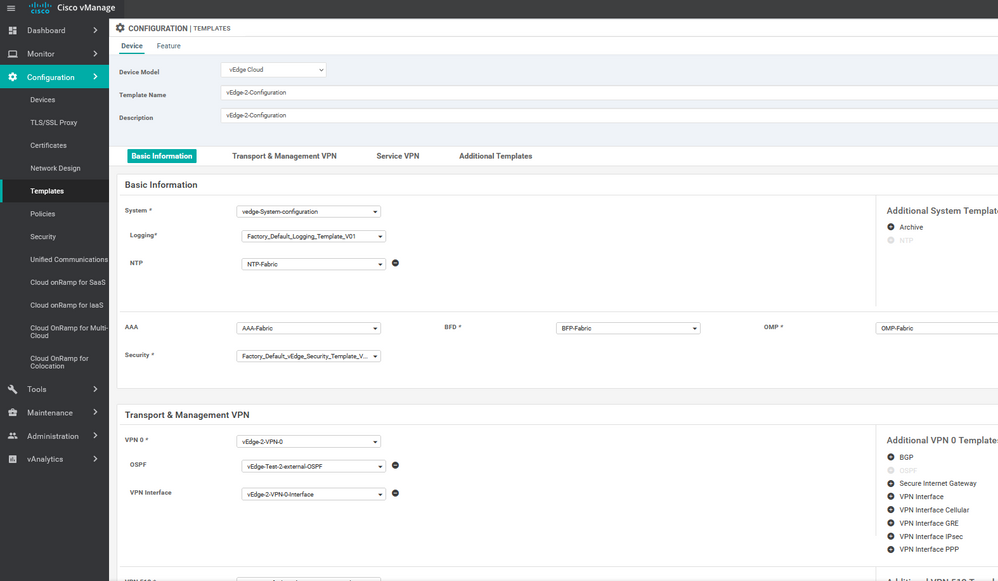
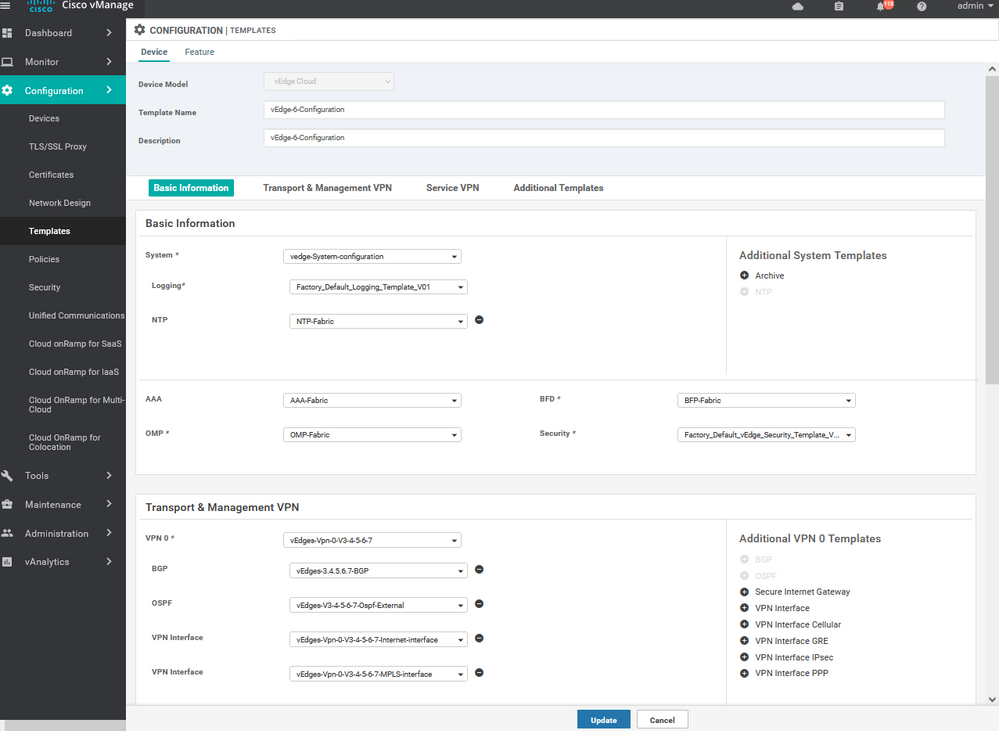
Navigate to the vManage Configuration > Templates. Select Feature Tab. And press Add template then choose the device type then select the template .
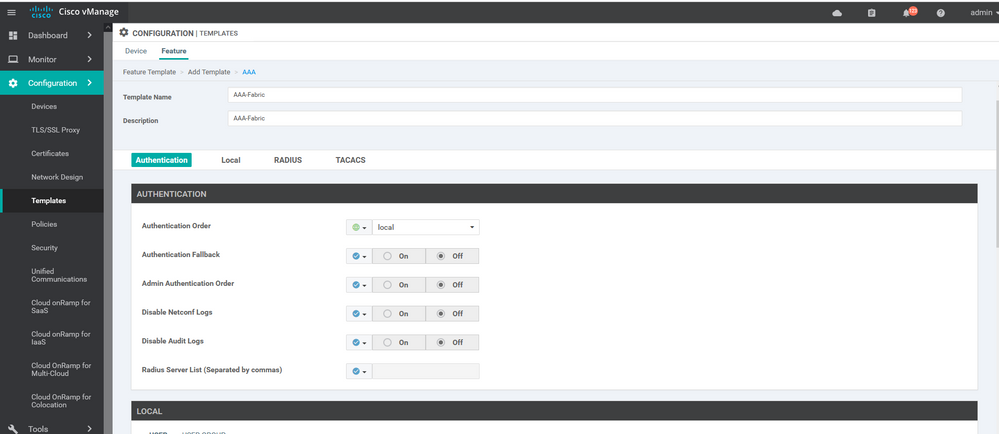
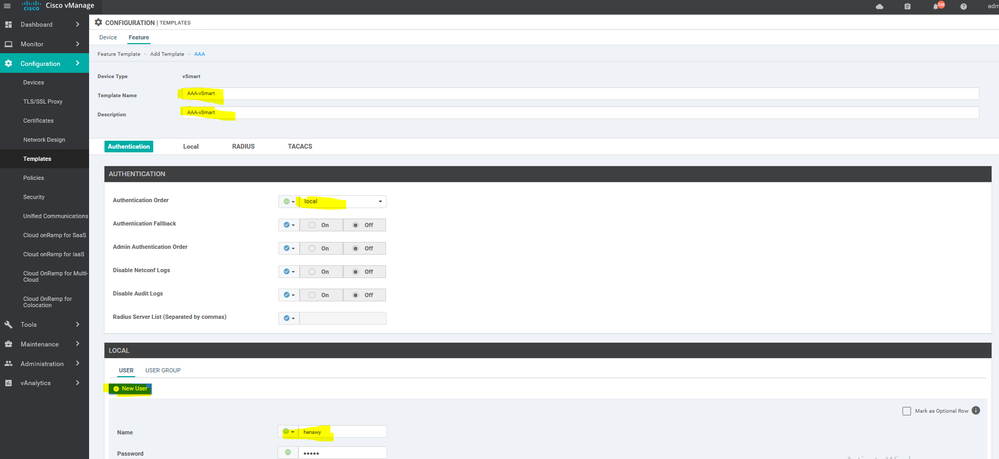
To create AAA feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic Information > AAA
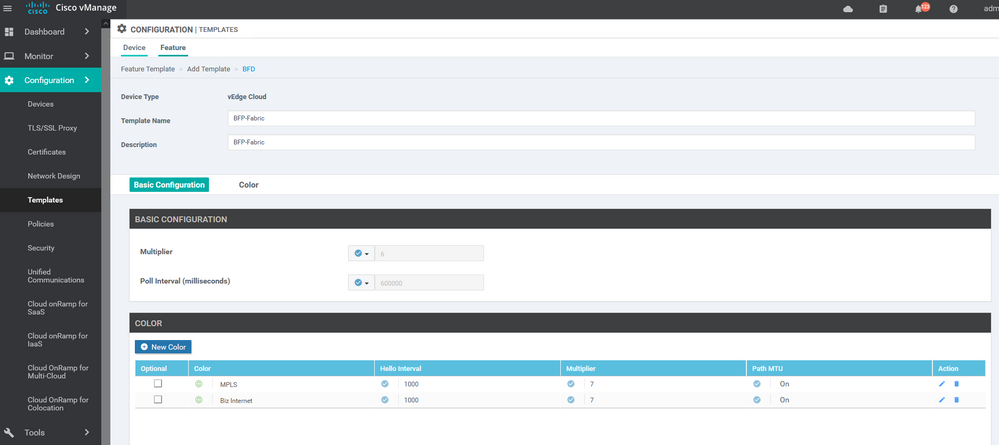
To create BFD feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic Information > BFD
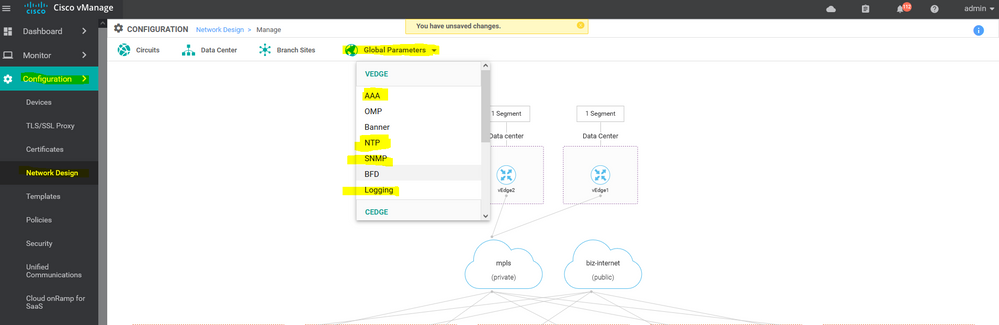
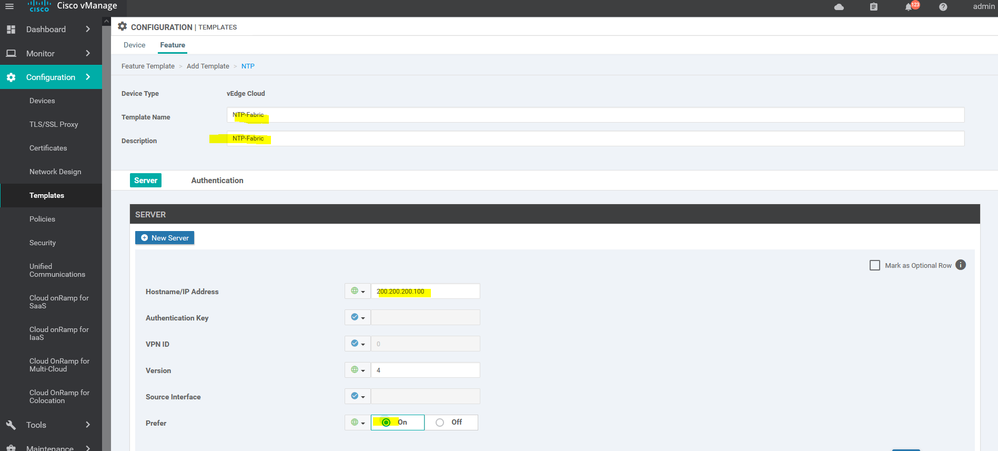
To create NTP feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic Information > NTP
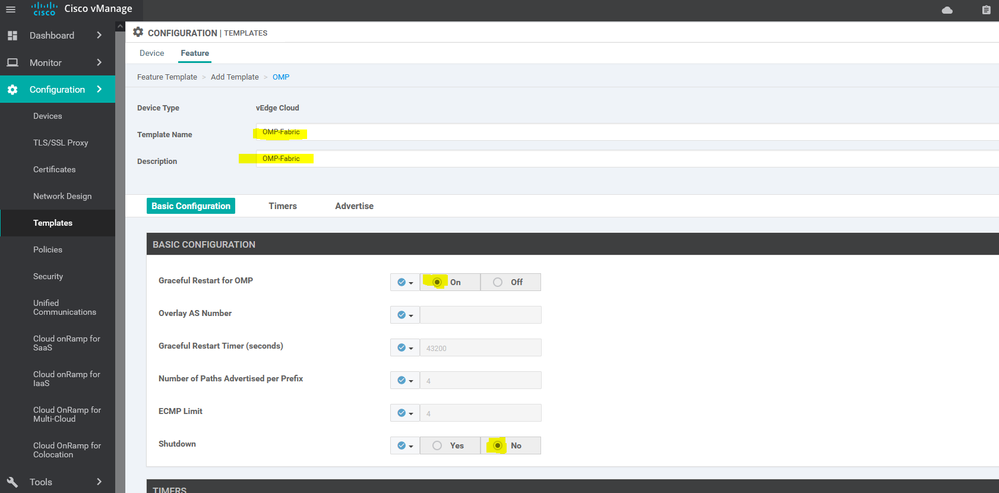
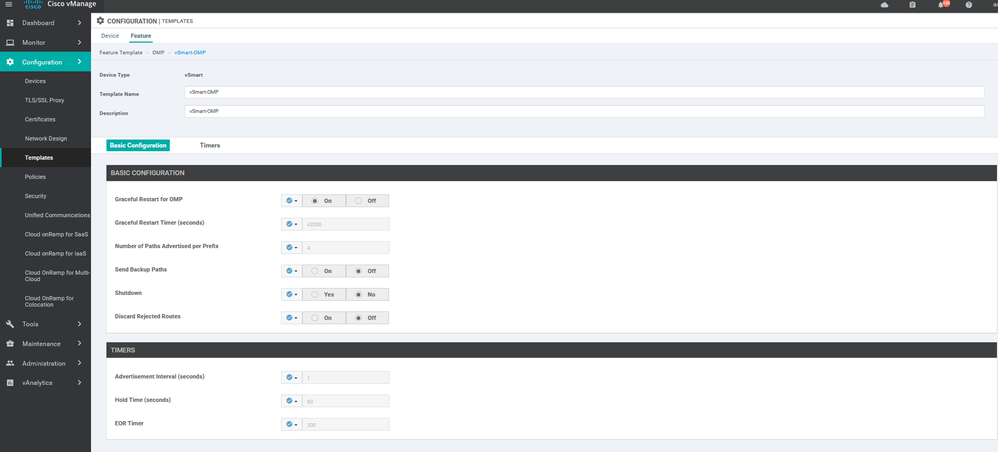
To create OMP feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic Information > OMP
To create vedge system feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic Information > system
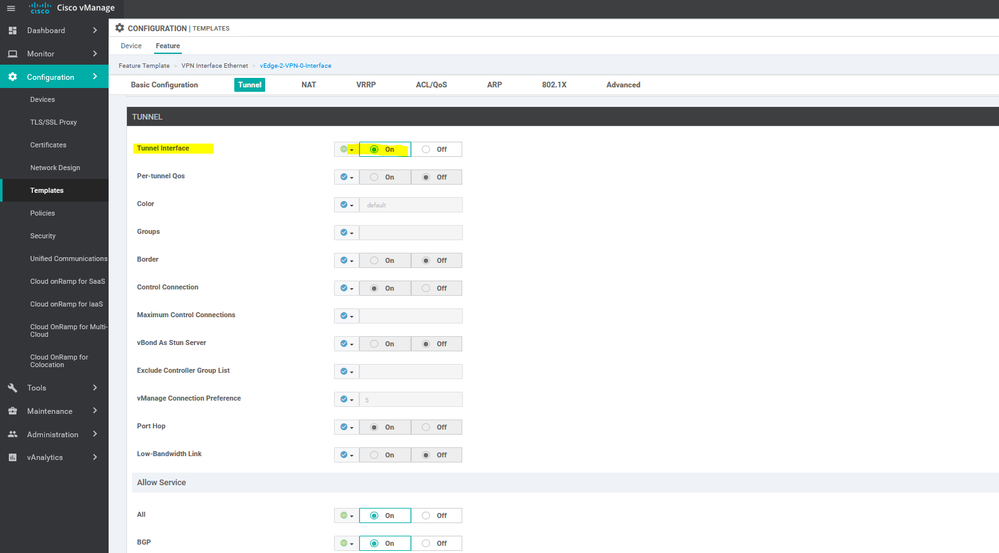
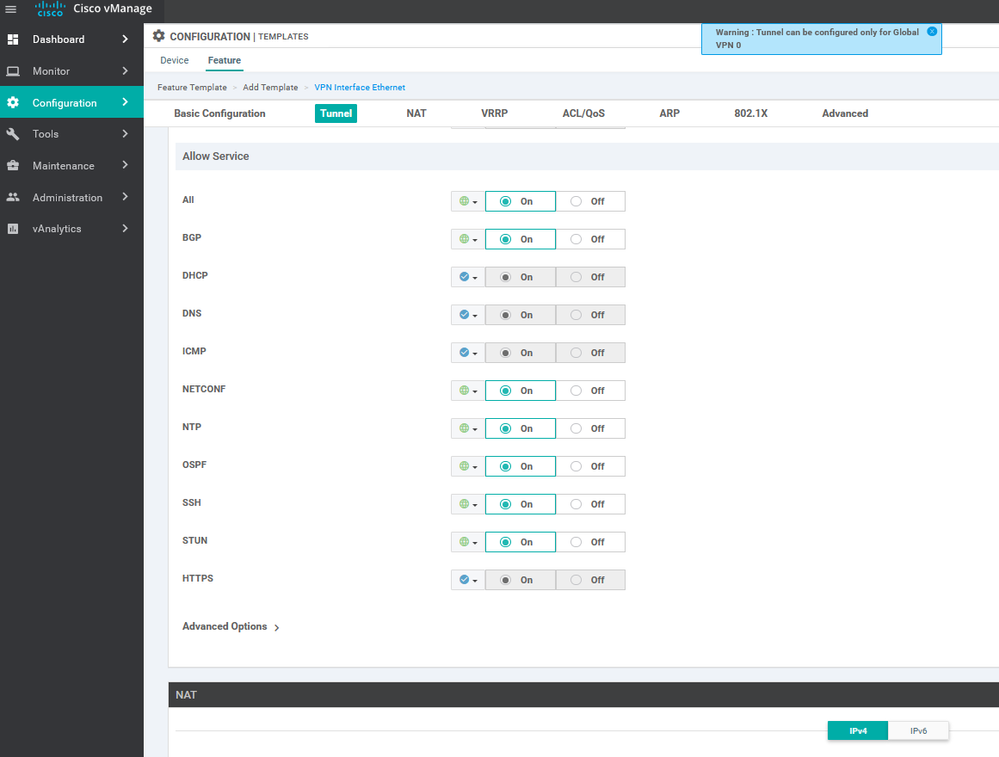
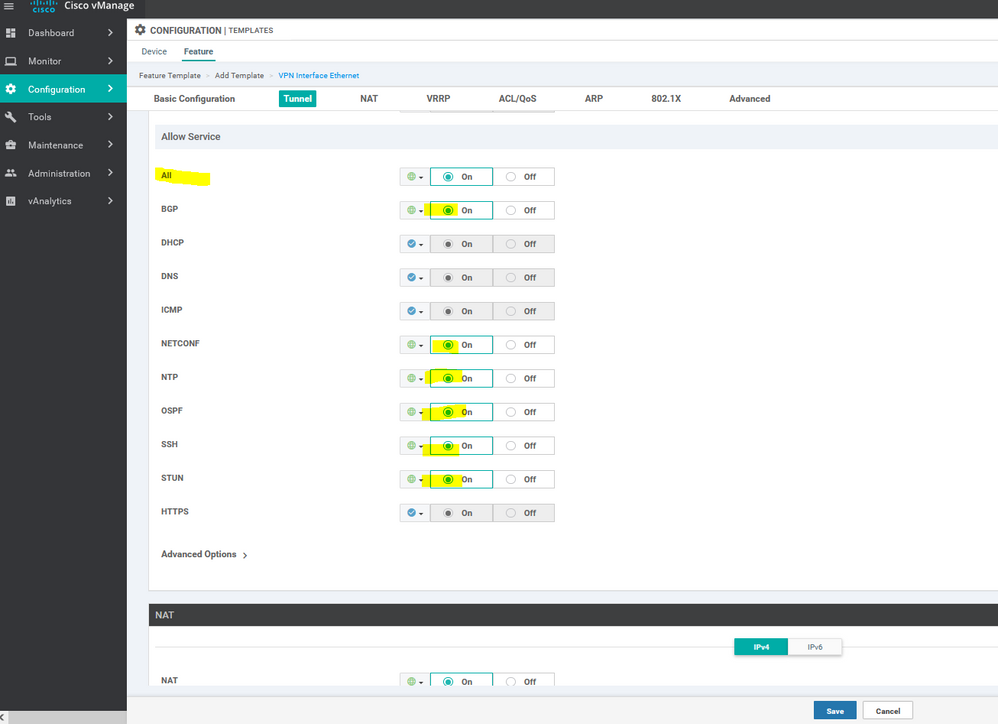
IMPORTANT NOTE : Port hopping is assigned a random port number. After a fixed the service is assigned to a random port and so on, so it is called hopping. This mechanism makes its difficult to attack and retain connection to a particular service .
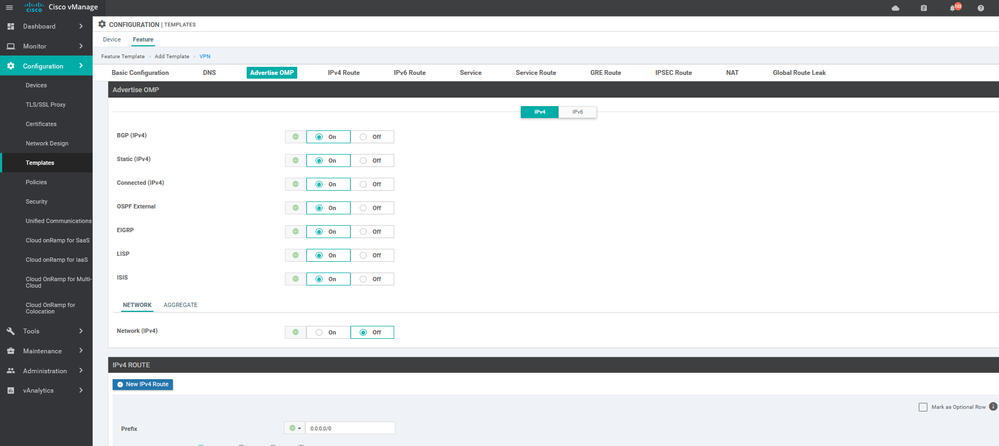
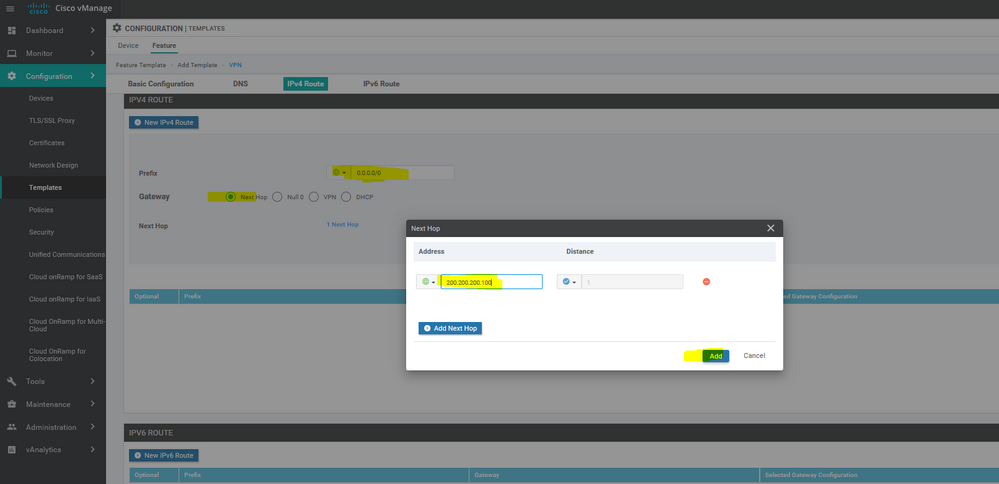
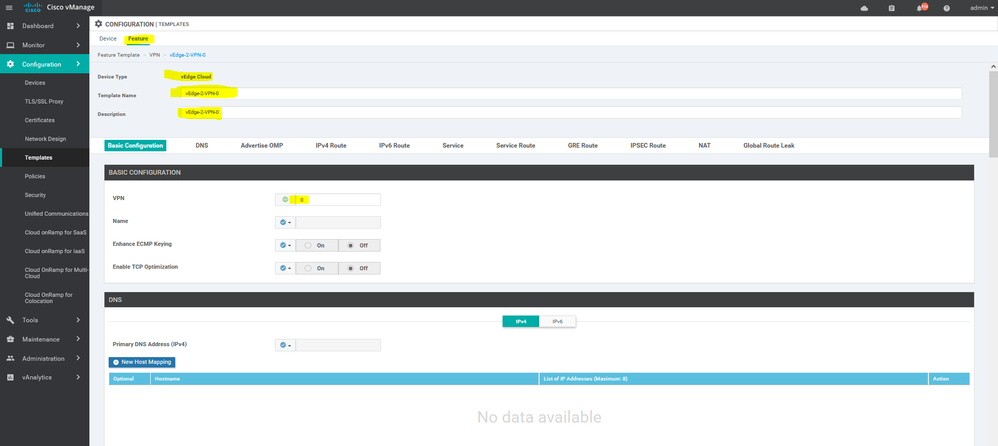
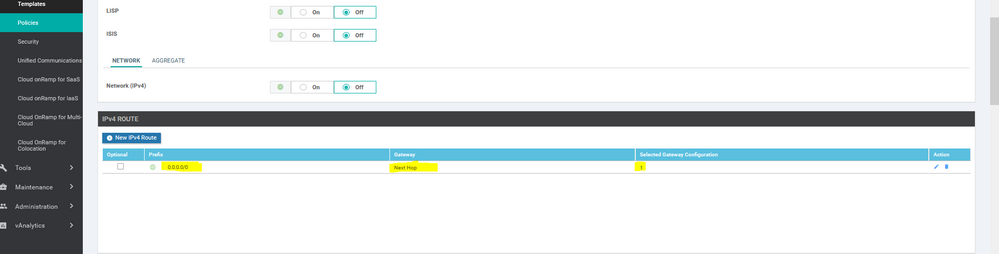
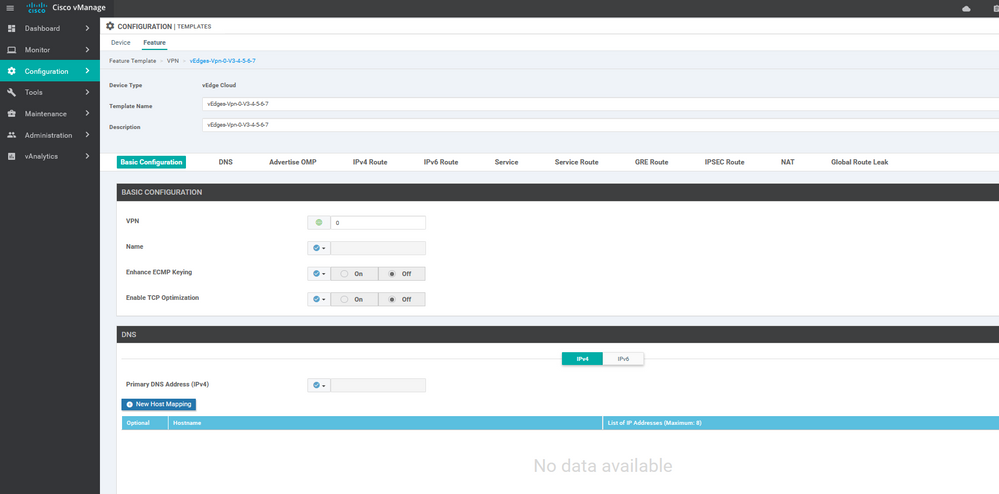
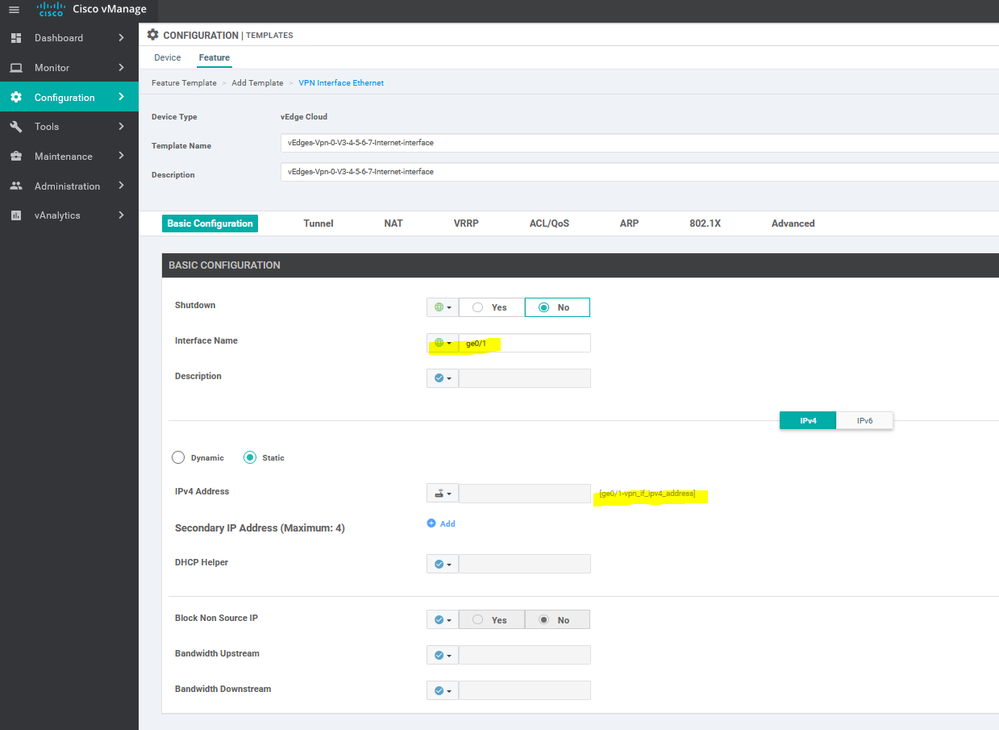
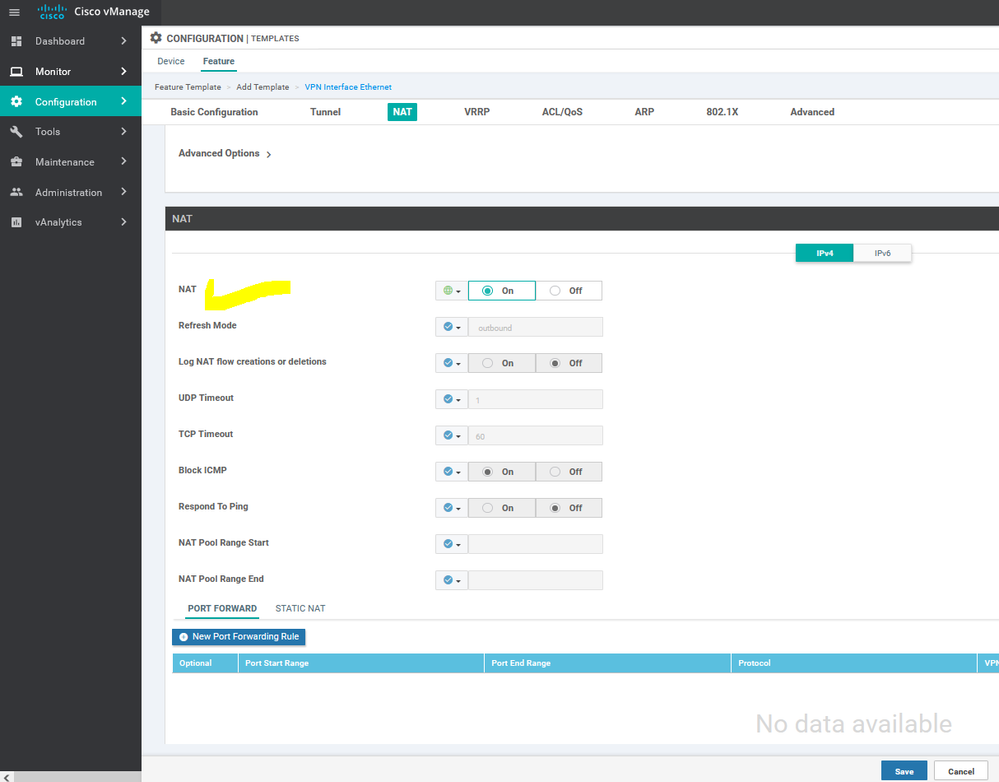
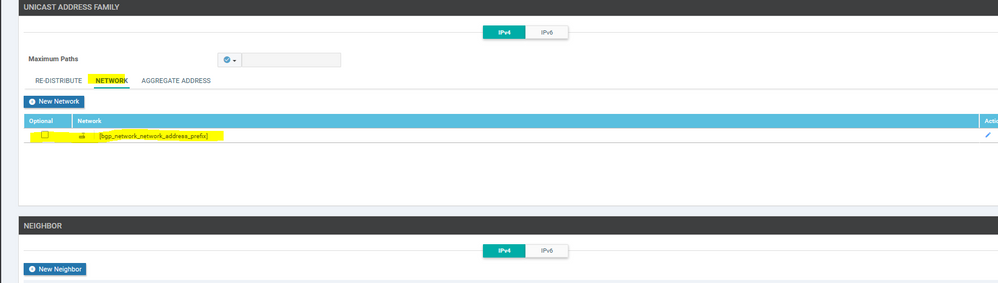
To create VPN feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> VPN> VPN
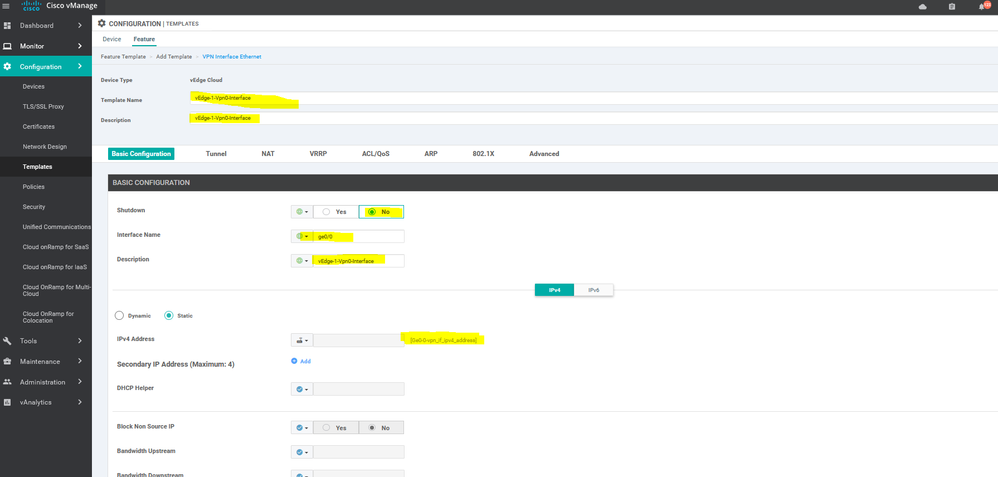
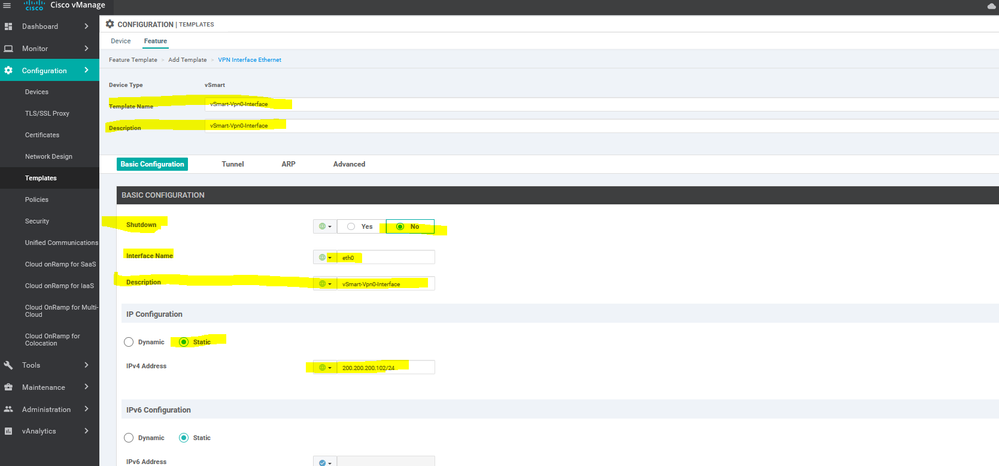
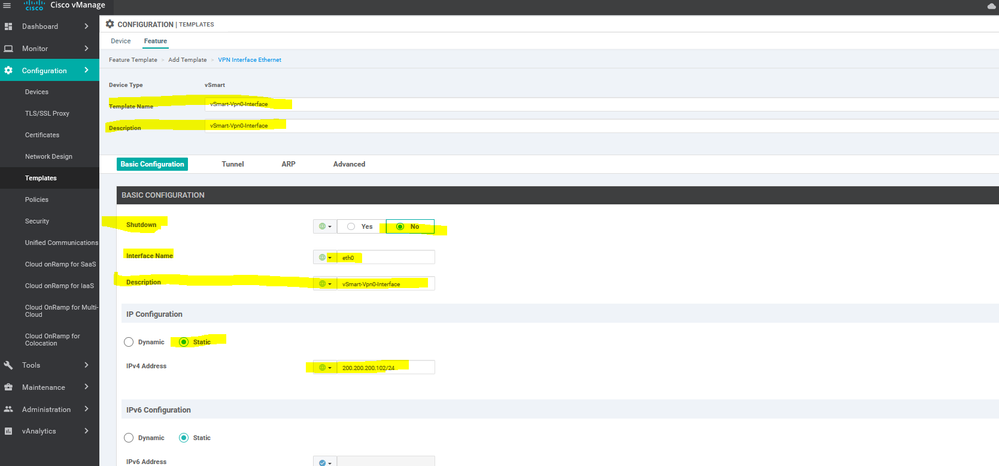
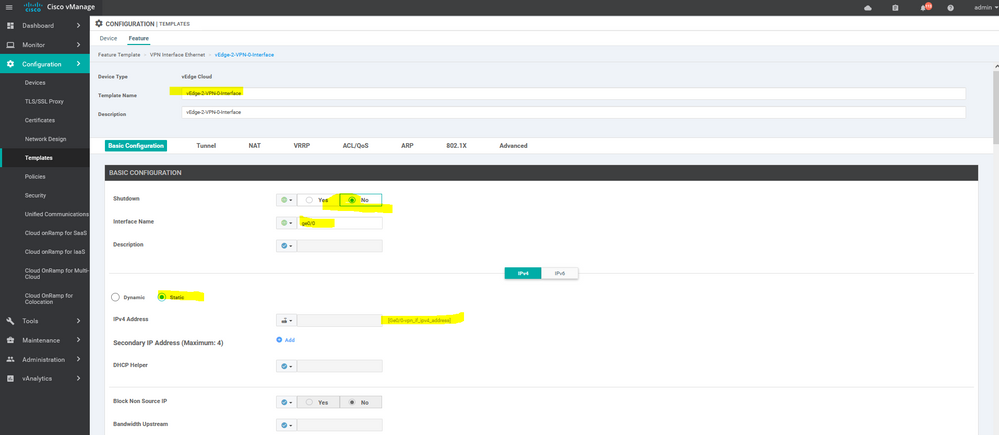
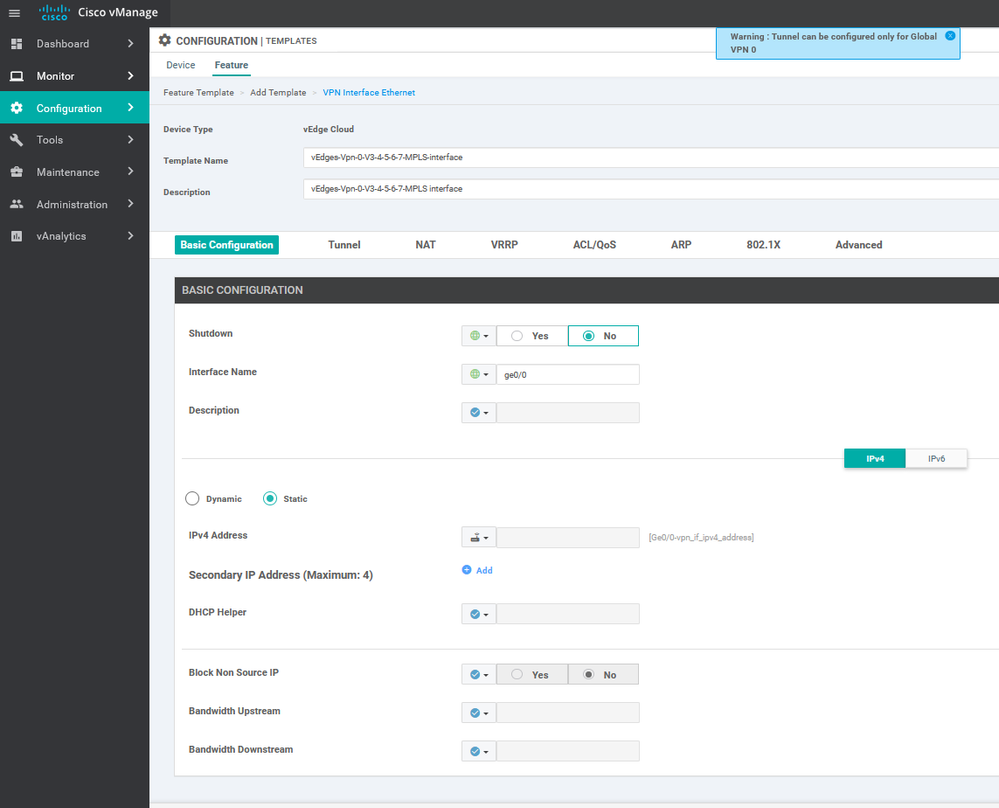
To create INTERFACE VPN feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> VPN> VPN VPN Interface Ethernet
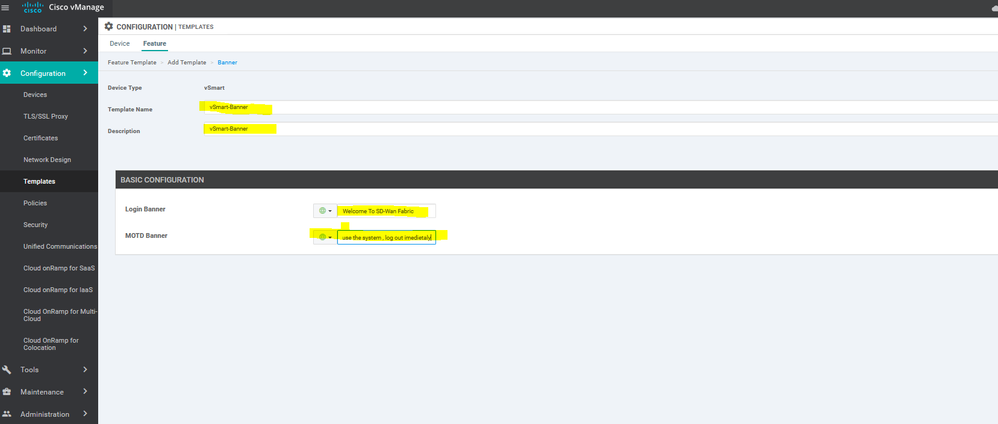
To create Banner feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Banner
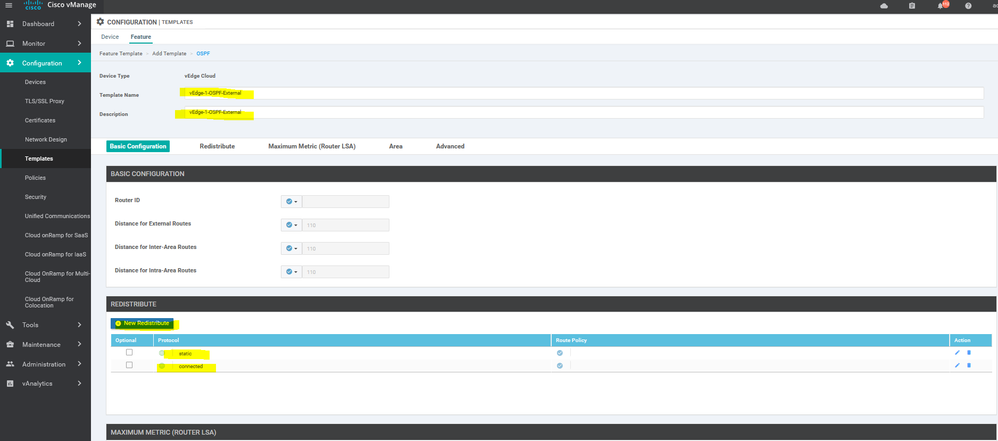
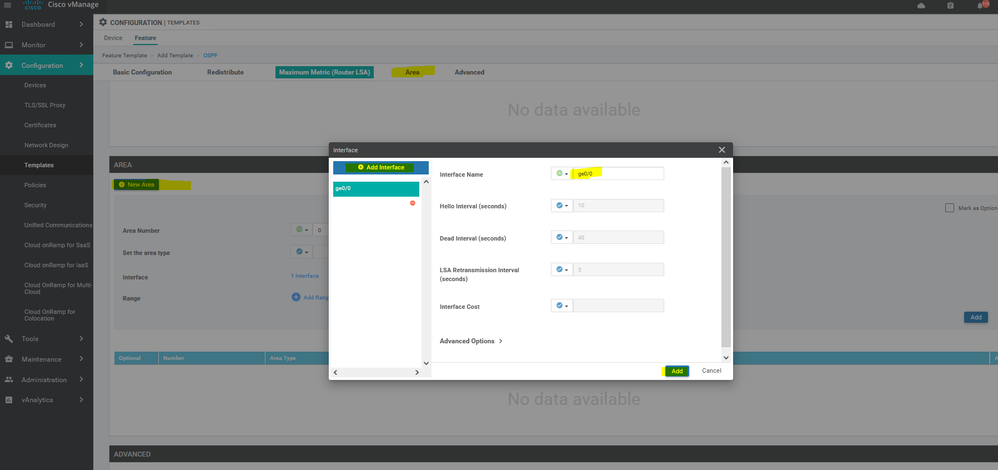
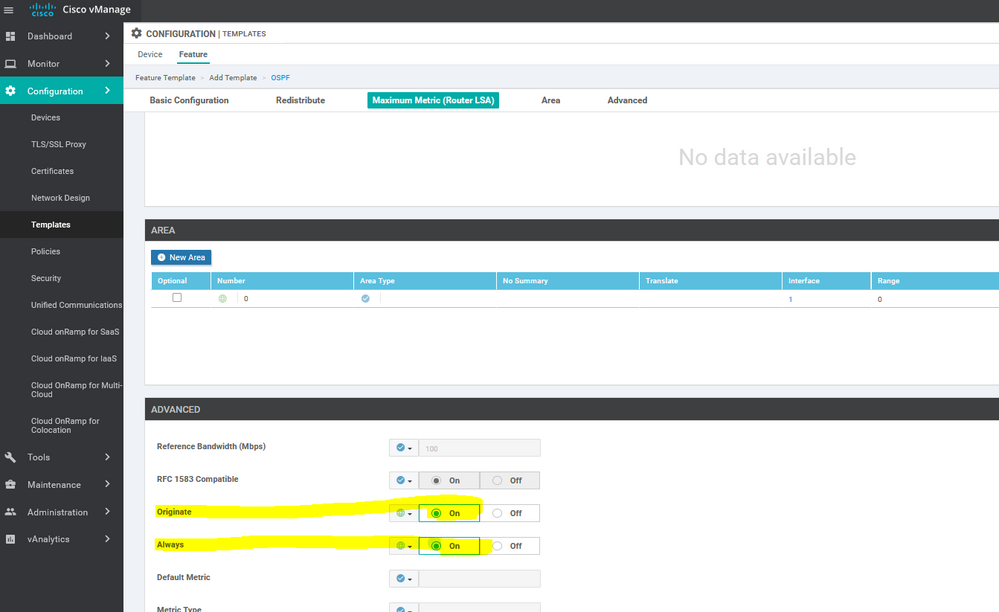
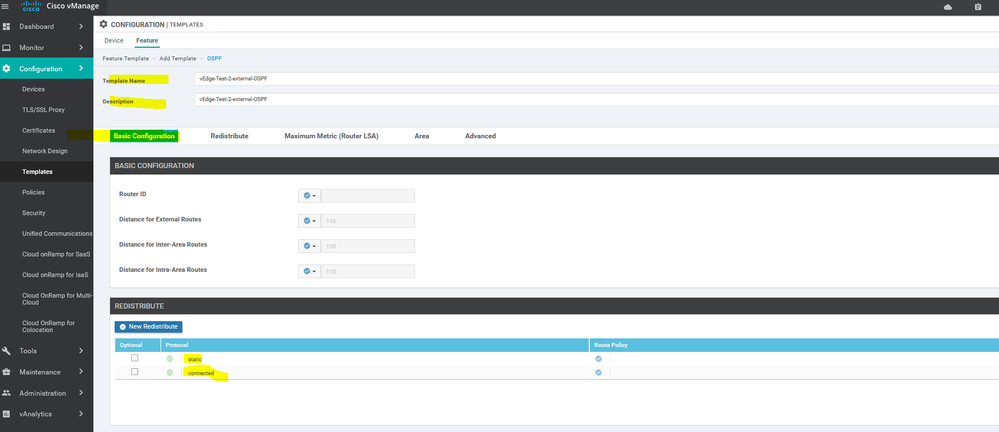
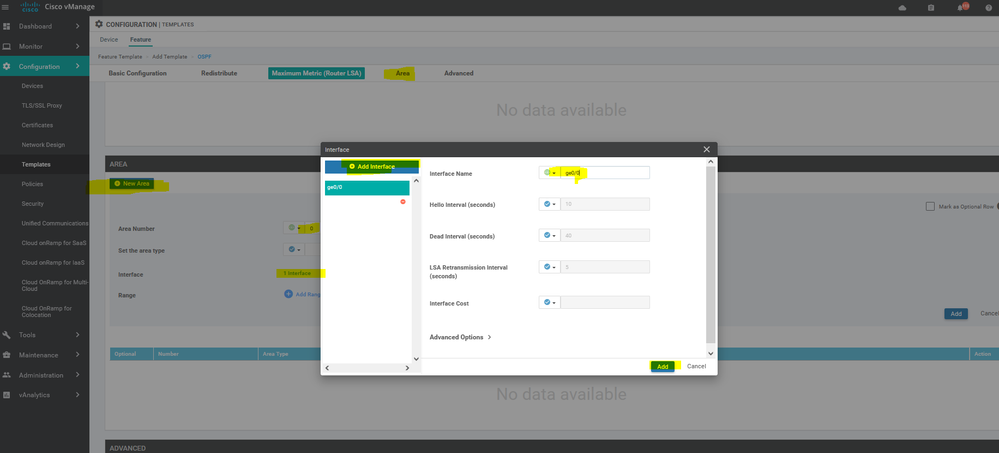
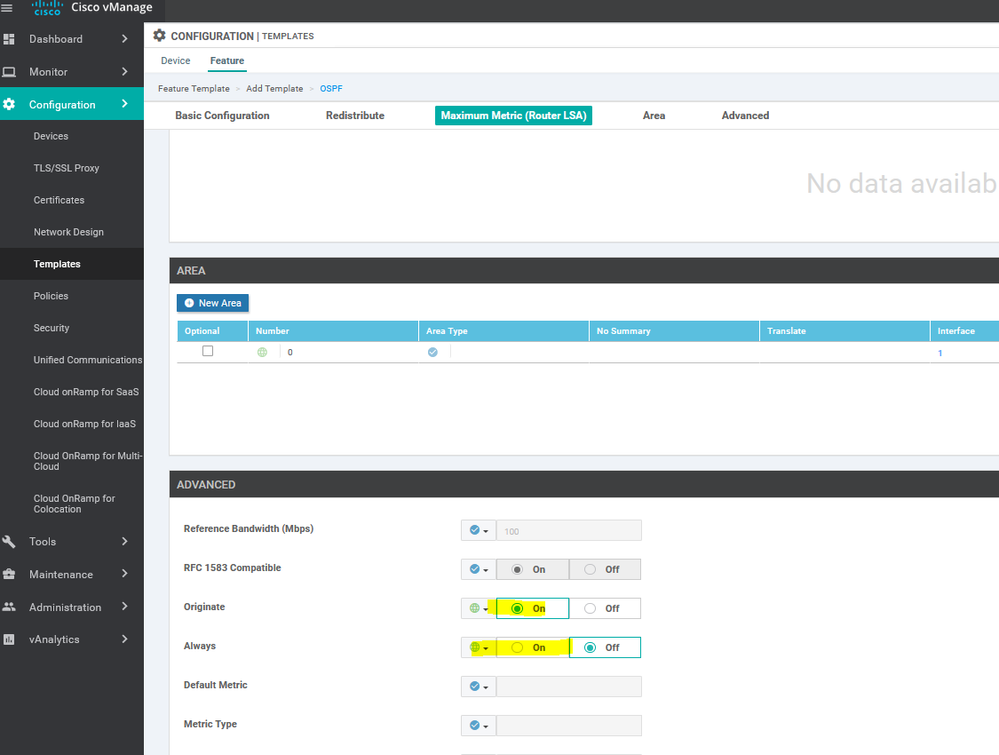
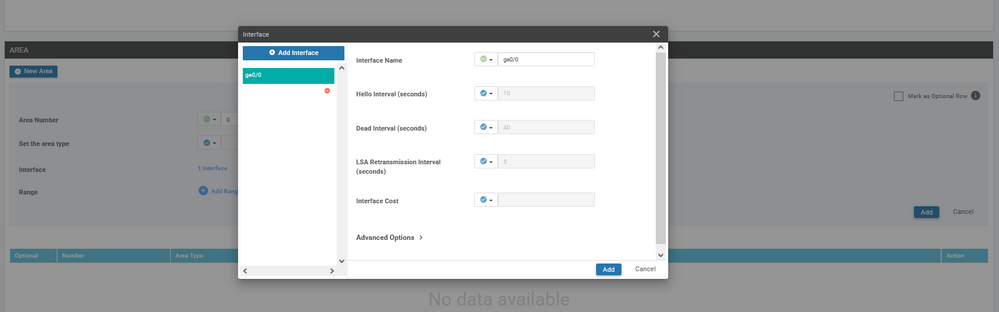
To create OSPF feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Other template > OSPF
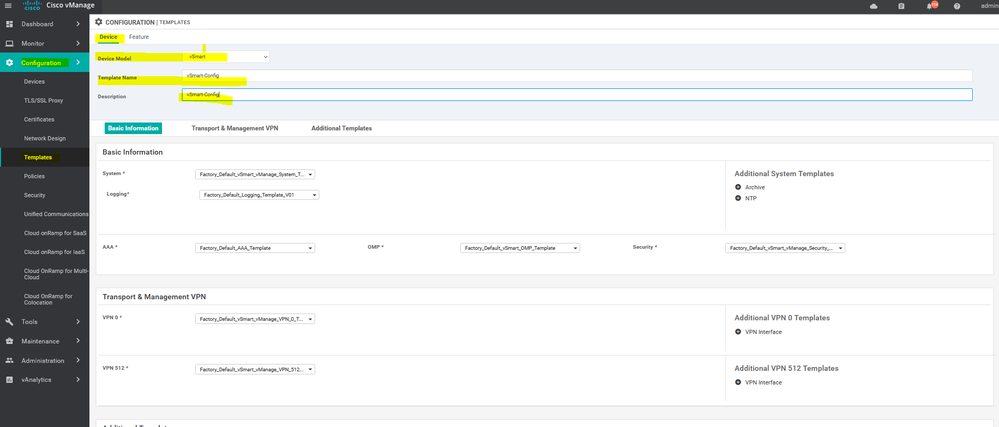
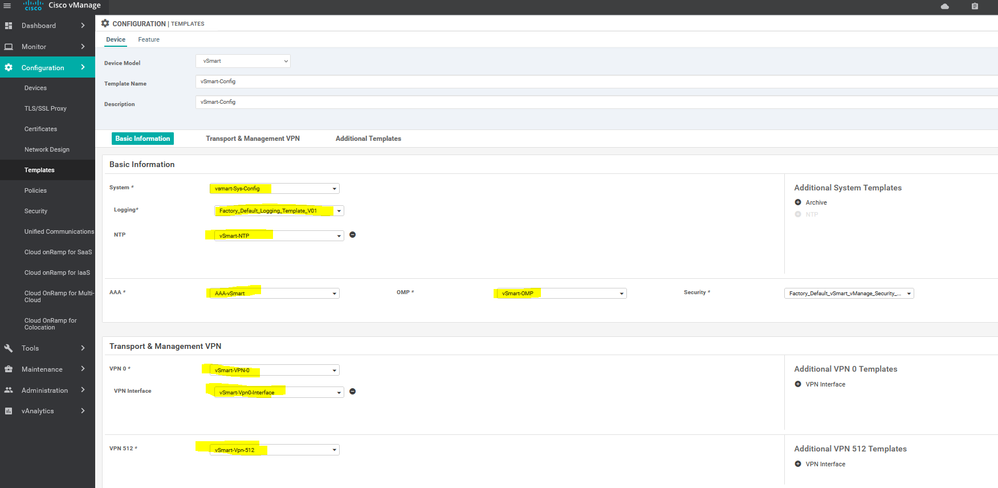
Create vSmart Template :-
To create vSmart AAA feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic template > AAA
To create vSmart NTP feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic template > NTP
To create vSmart system feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic template > system
To create vSmart OMP feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Basic template > OMP
To create vSmart VPN 0 feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> VPN template > VPN
To create vSmart interface VPN 0 feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> VPN template > interface VPN
To create vSmart Banner feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> Others template > Banner
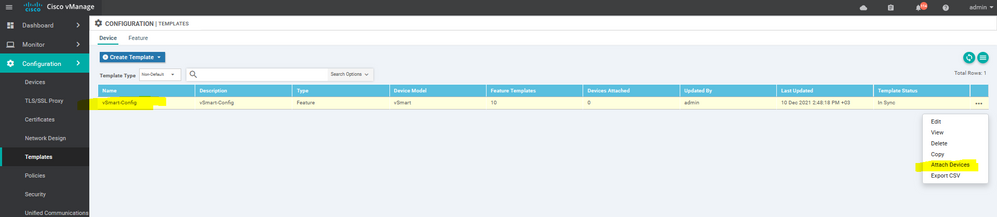
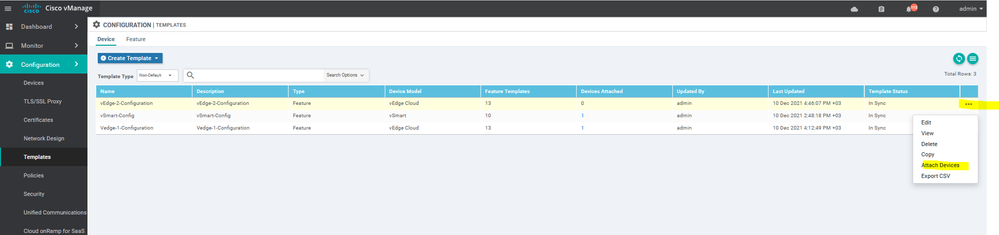
Create the Device Templet for the vSmart :
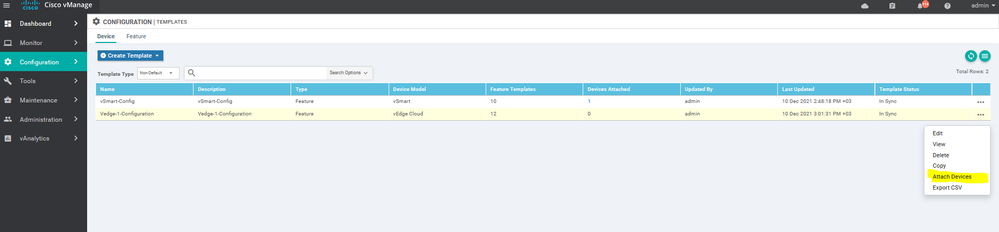
To create vSmart device template, go to Configuration > Templates and select the Device tab , Select the Add device button> choose the vsmart > name > description then start choose the Feature
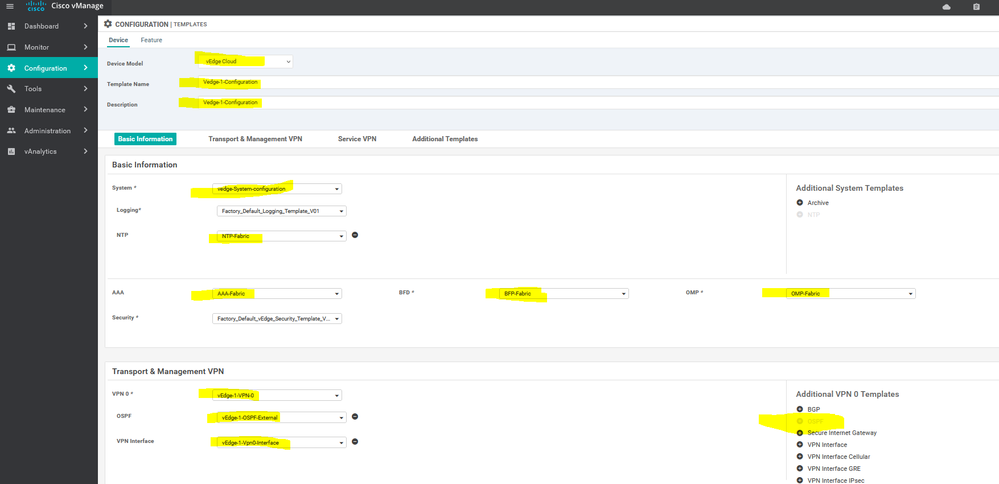
Create the Device Templet for the vEdge 1 :
To create vEdge device template, go to Configuration > Templates and select the Device tab , Select the Add device button> choose the vEdge cloud > name > description then start choose the Feature
Create the Templet for the vEdge 2 :
To create vEdge Vpn0 feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> vpn >vpn
To create vEdge interface Vpn0 feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> vpn > interface vpn
To create vEdge OSPF feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> other > OSPF
Create the Device Templet for the vEdge 2 :
To create vEdge2 Device template, go to Configuration > Templates and select the device tab , Select the Add device Template button> choose the vEdge cloud > name > description then start choose the Feature
Create the Templet for the vEdge 3-4-5-6-7 :
To create vEdge Vpn0 feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> vpn >vpn
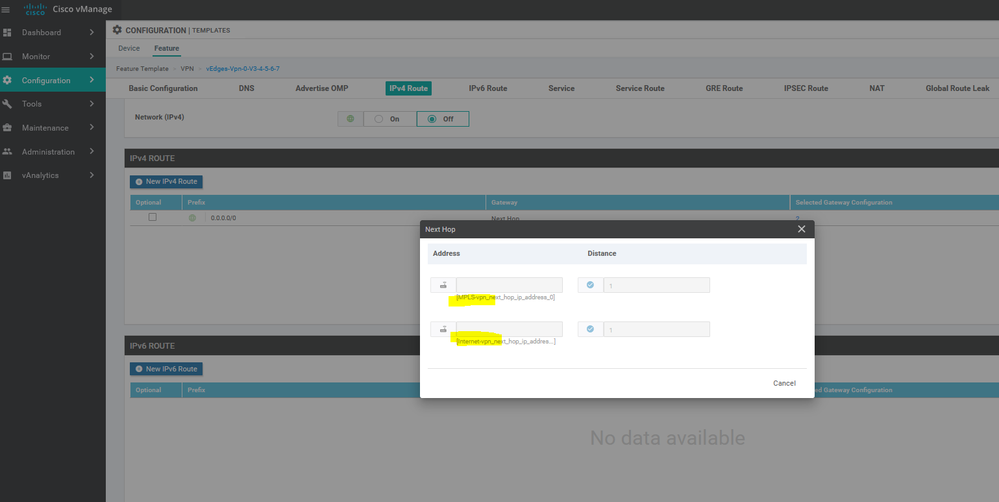
To create vEdge Vpn0 MPLS & internet interface feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> vpn >vpn interface Ethernet
To create vEdge OSPF feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> other >OSPF
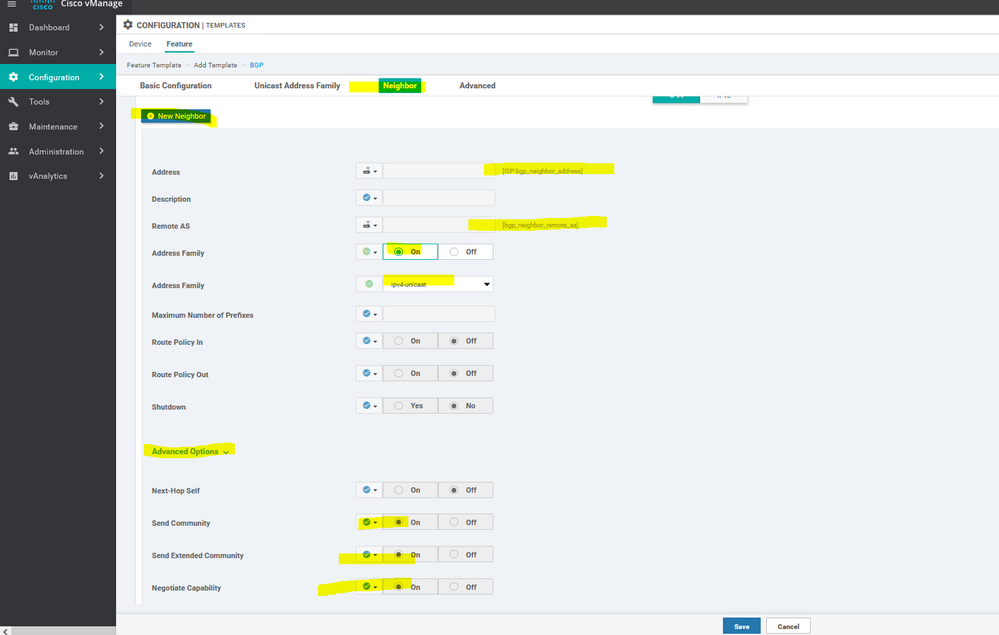
To create vEdge BGP feature template, go to Configuration > Templates and select the Feature tab , Select the Add Template button> other > BGP
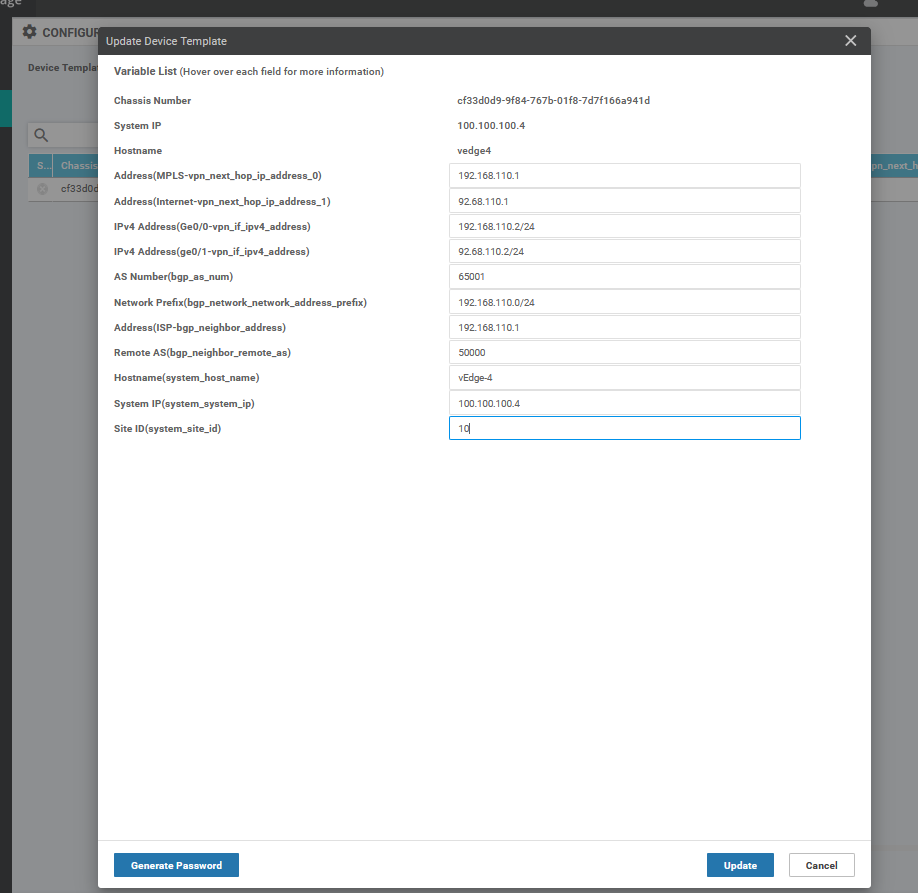
Create the Device Templet for the vEdge 3 :
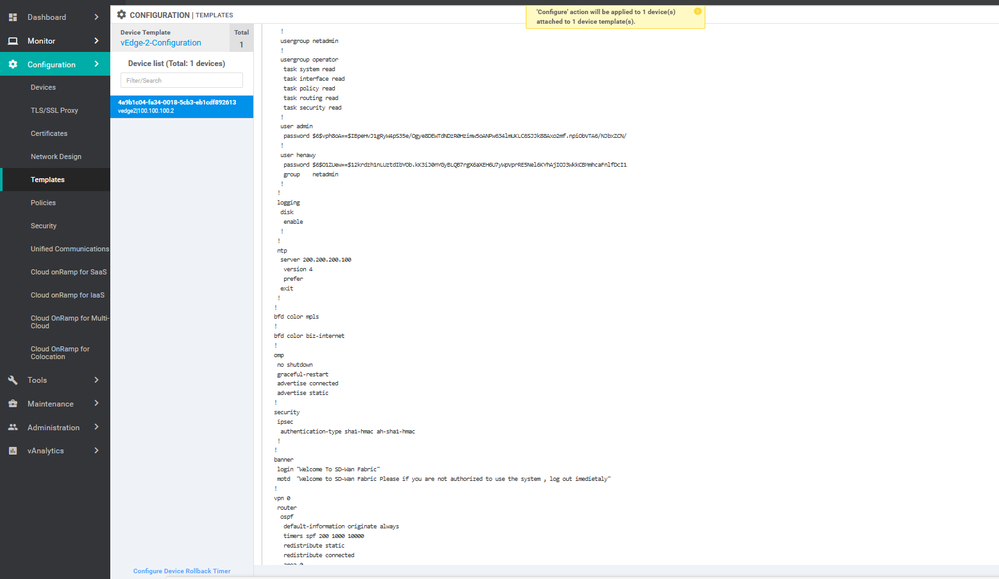
To create vEdges Device template, go to Configuration > Templates and select the device tab , Select the Add device Template button> choose the vEdge cloud > name > description then start choose the Feature
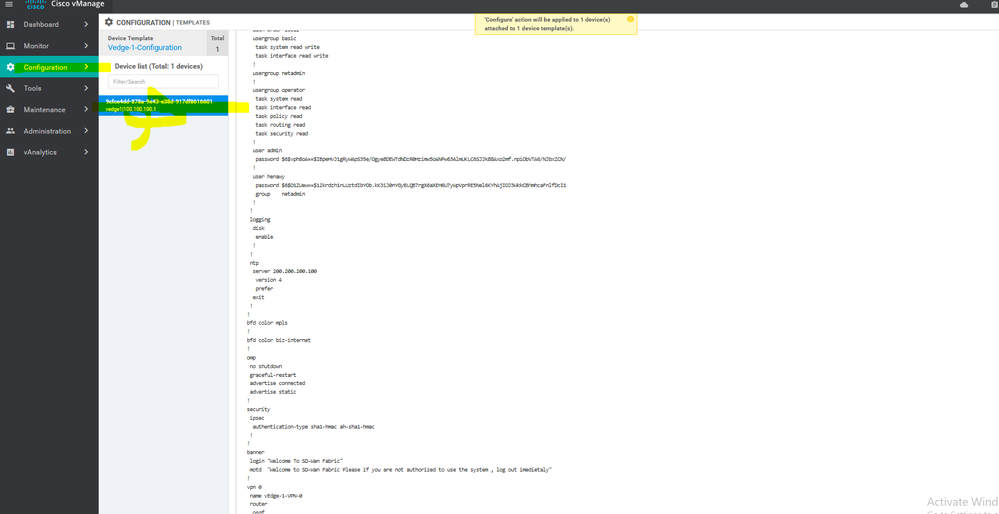
CLI configuration
system
device-model vedge-cloud
host-name vEdge-3
system-ip 100.100.100.3
domain-id 1
site-id 10
admin-tech-on-failure
no route-consistency-check
sp-organization-name "cico sdwan"
organization-name "cisco sdwan"
clock timezone Asia/Riyadh
console-baud-rate 9600
vbond 200.200.200.103 port 12346
aaa
auth-order local
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
user admin
password $6$vph8oA==$IBpeHvJ1gRyW4pS35e/Ogye8DEWTdNDzR0Hzimw5oANPw634lmUKLC6SJJk88Axo2mf.npiObVTA6/NJbxZCN/
!
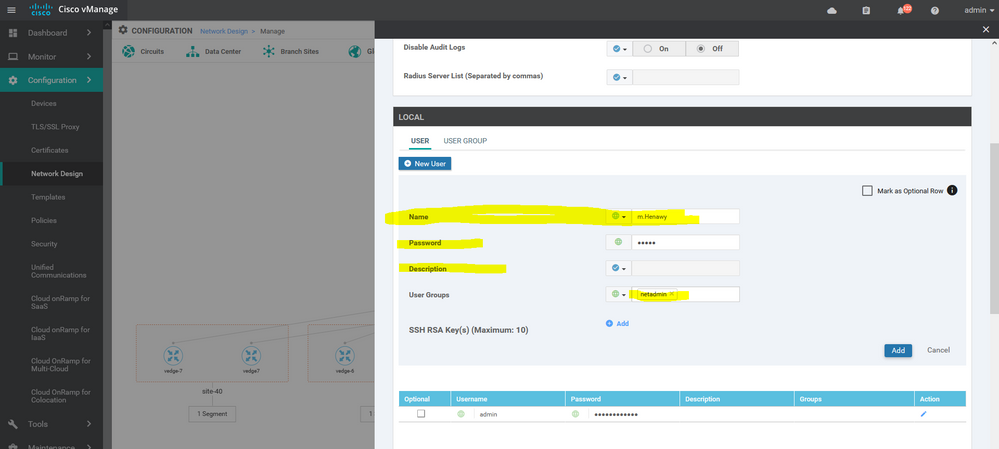
user m.henawy
password $6$O1ZUew==$12krdzh1nLUztdIbYOb.kK3iJ0nYGyBLQB7rgX6aXEH6U7yWpVprRE5Nel6KYhAjIOJ3WkkCBMmhcaFnlfDcI1
group netadmin
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
bfd color mpls
!
bfd color biz-internet
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type sha1-hmac ah-sha1-hmac
!
!
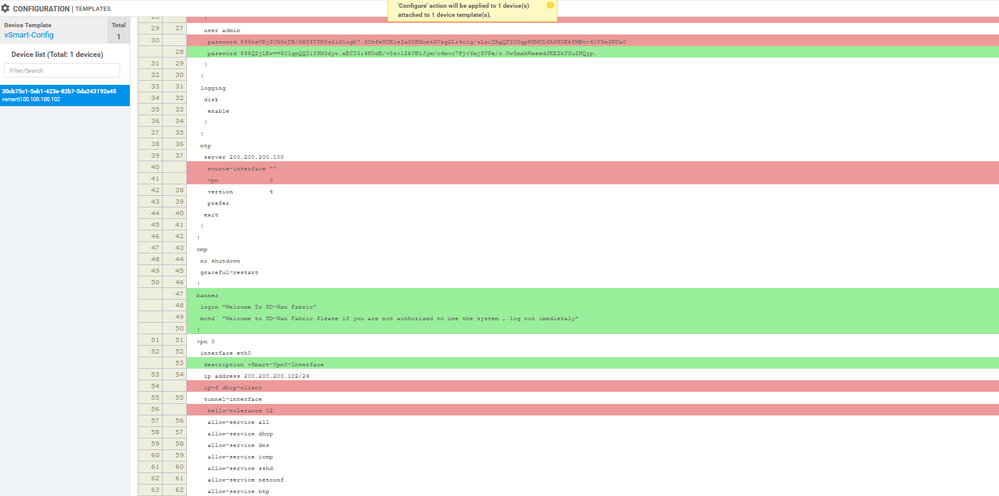
banner
login "Welcome To SD-Wan Fabric"
motd "Welcome to SD-Wan Fabric Please if you are not authorized to use the system , log out imedietaly"
!
vpn 0
router
ospf
default-information originate always
timers spf 200 1000 10000
redistribute static
redistribute connected
area 0
interface ge0/0
exit
exit
!
bgp 65001
no shutdown
address-family ipv4-unicast
network 192.168.10.0/24
redistribute static
redistribute connected
redistribute ospf
!
neighbor 192.168.10.1
no shutdown
remote-as 50000
address-family ipv4-unicast
!
!
!
!
interface ge0/0
ip address 192.168.10.2/24
tunnel-interface
encapsulation ipsec
color mpls restrict
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
interface ge0/1
ip address 92.68.10.2/24
nat
!
tunnel-interface
encapsulation ipsec
color biz-internet
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 92.68.10.1
ip route 0.0.0.0/0 192.168.10.1
!
vpn 512
interface eth0
no shutdown
!
!
!
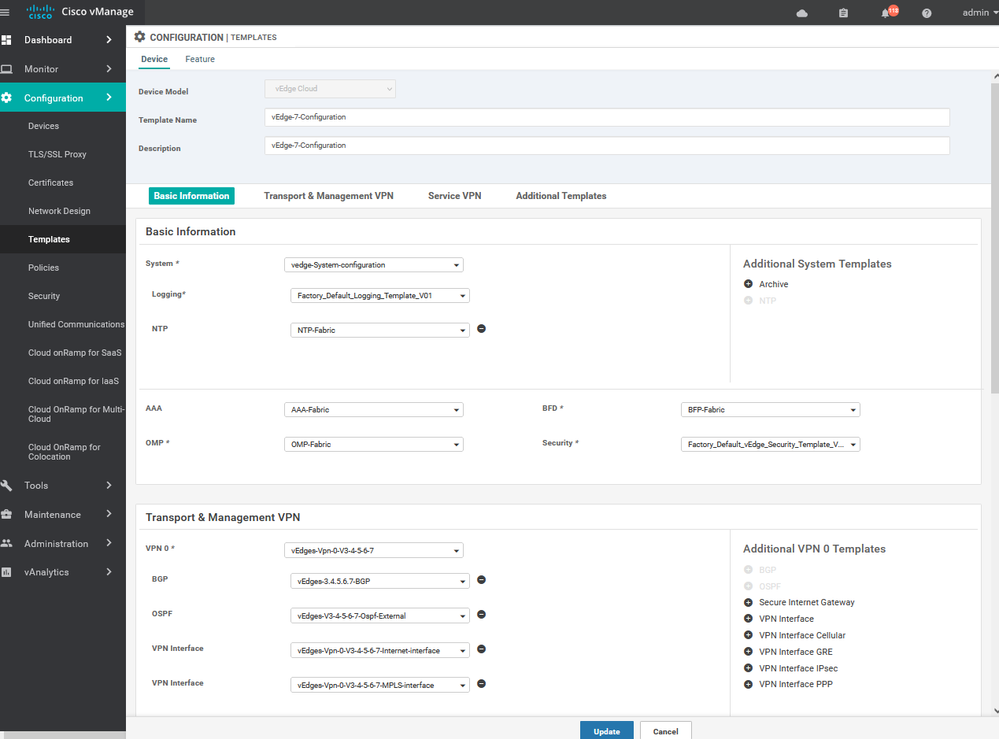
Create the Device Templet for the vEdge 4 :
To create vEdges Device template, go to Configuration > Templates and select the device tab , Select the Add device Template button> choose the vEdge cloud > name > description then start choose the Feature
Create the Device Templet for the vEdge 5-6-7 :
To create vEdges Device template, go to Configuration > Templates and select the device tab , Select the Add device Template button> choose the vEdge cloud > name > description then start choose the Feature
!
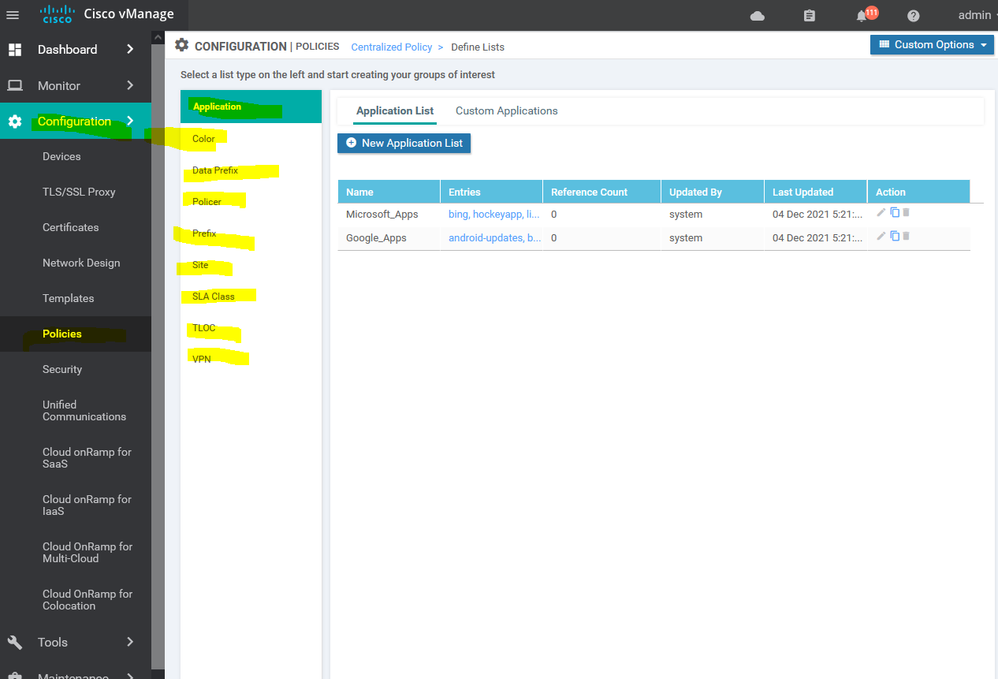
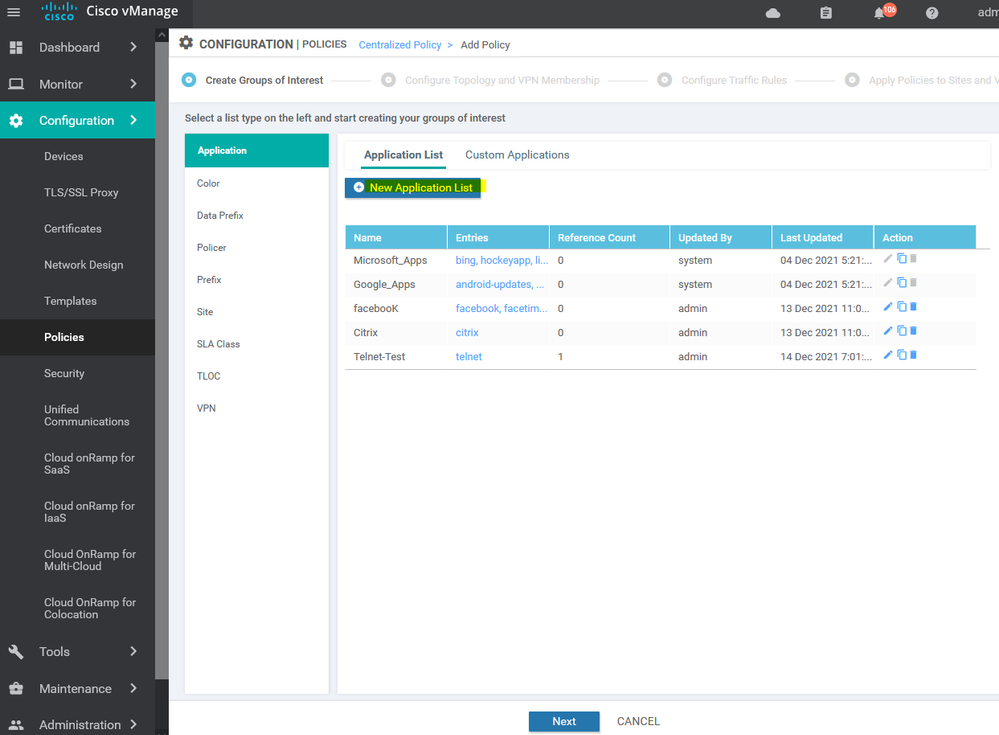
To create Policy we need some elements such as Site list , App list , VPN list , ETC...
To create list Configuration > Policy > Customize options > Centralized policy > List > select from the list APP, VPN, Site Etc...
To create list Configuration > Policy > Customize options > Centralized policy > List > select
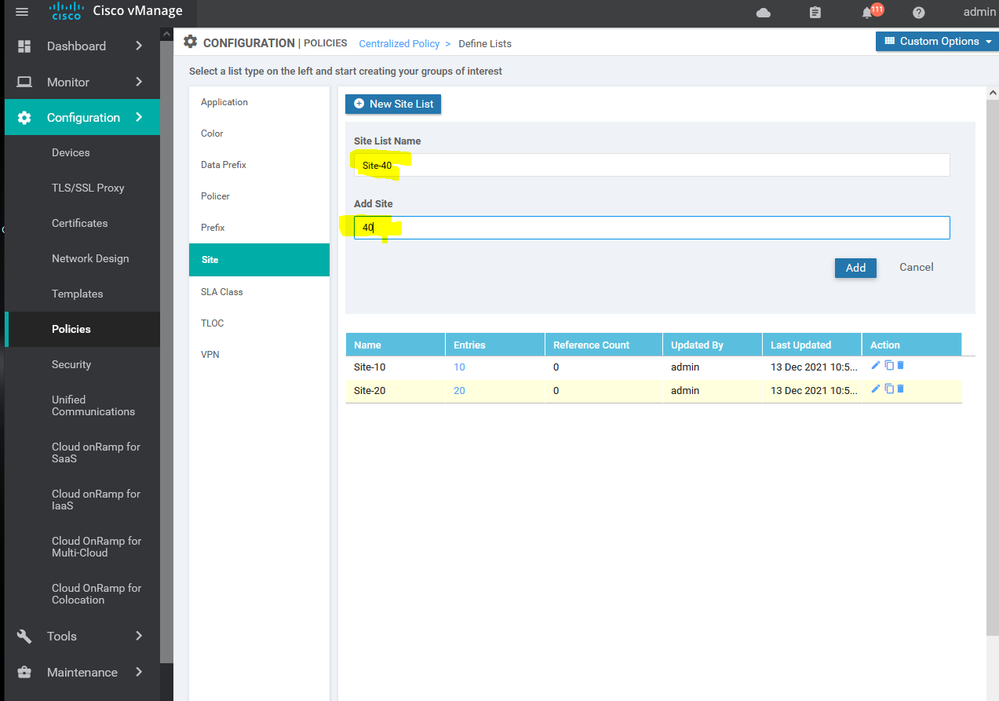
To create site list Configuration > Policy > Customize options > Centralized policy > List > site
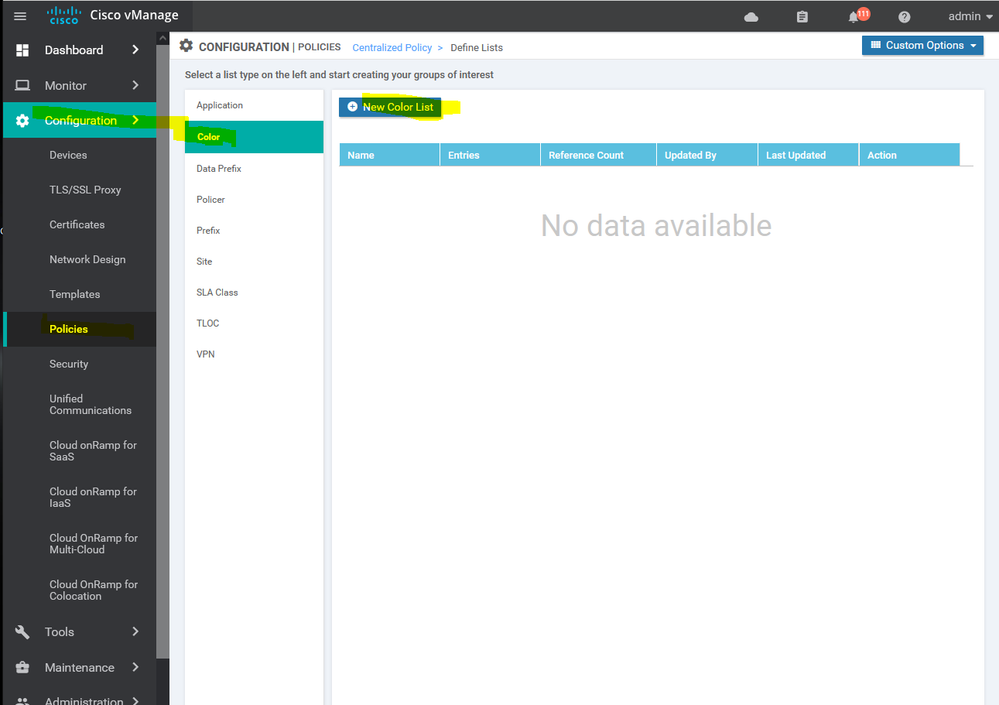
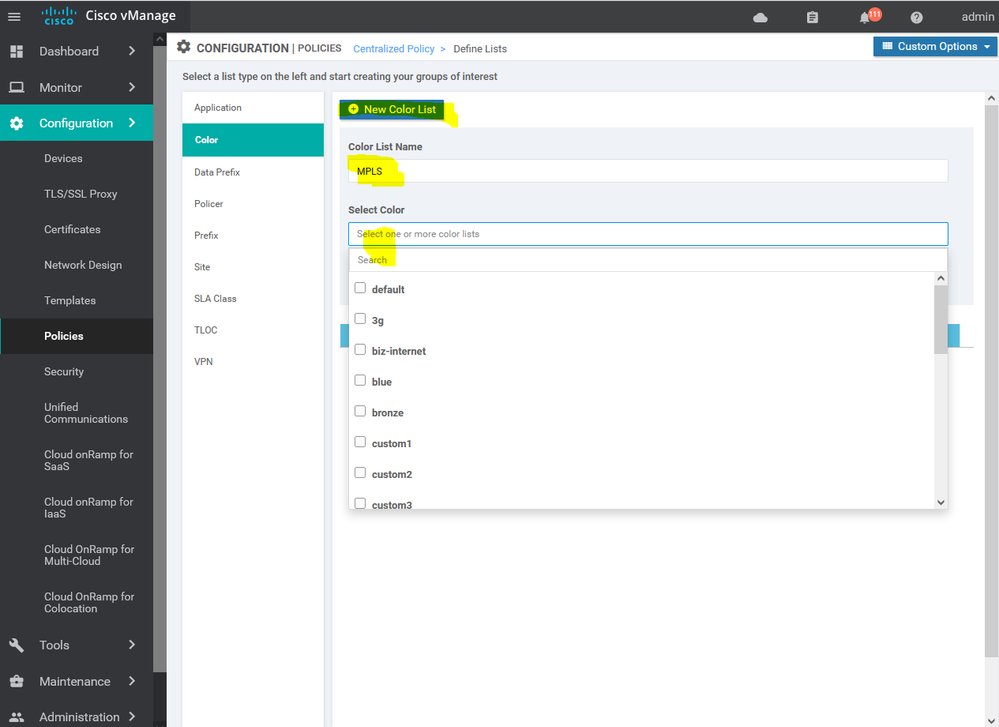
To create Color list Configuration > Policy > Customize options > Centralized policy > List > select color
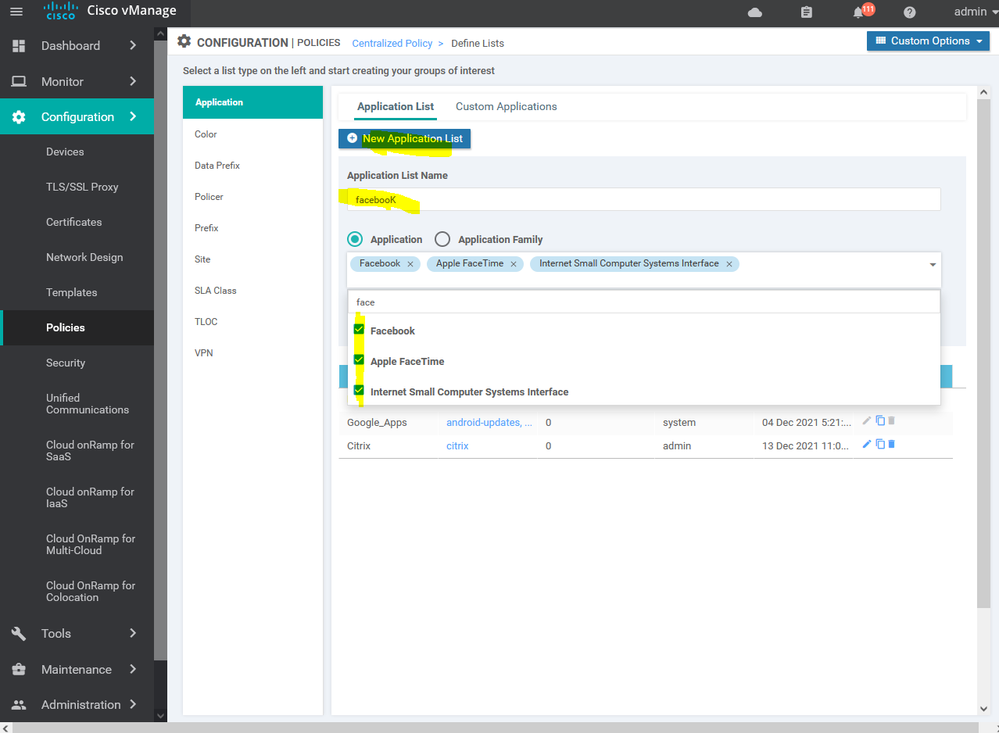
To create list of application Configuration > Policy > Customize options > Centralized policy > List > select application
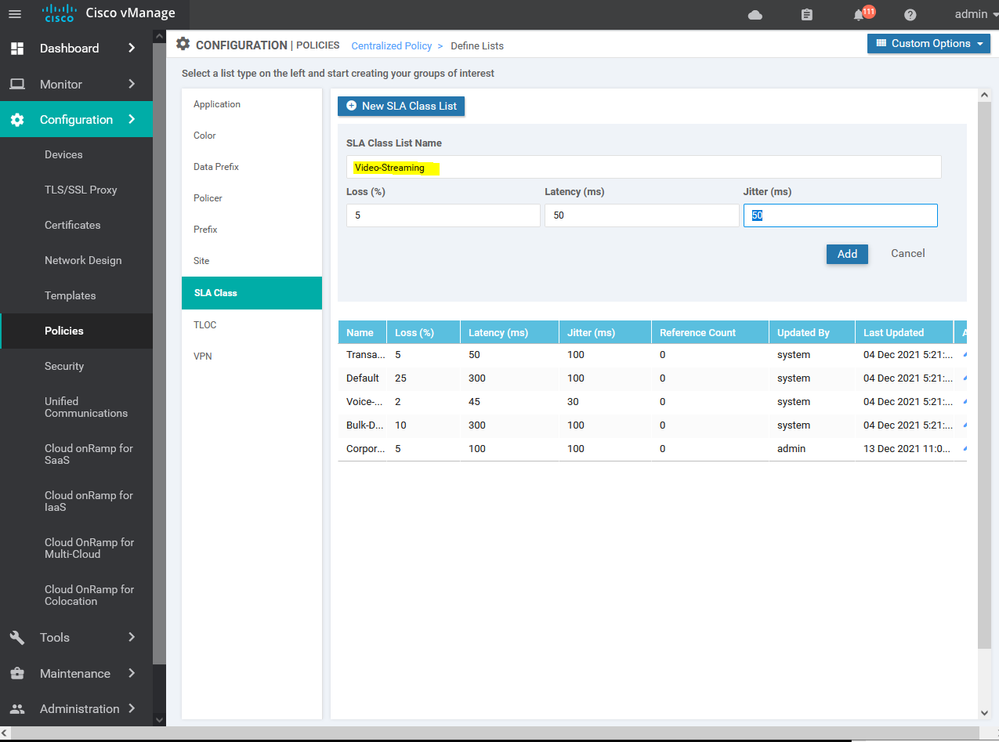
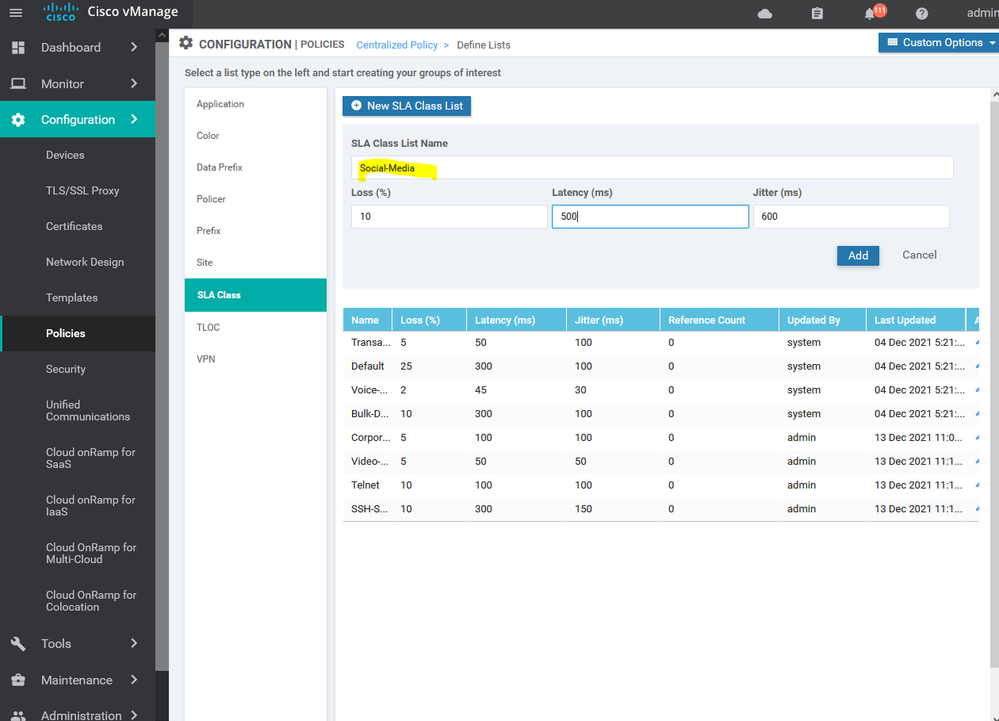
To create list of the Service level agreement SLA Configuration > Policy > Customize options > Centralized policy > List > SLA
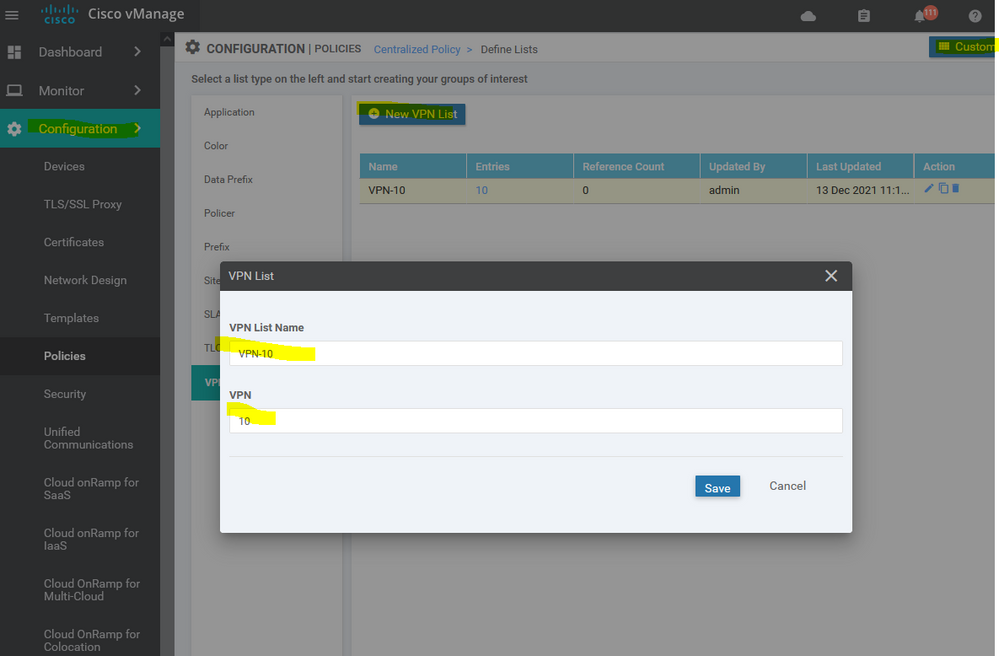
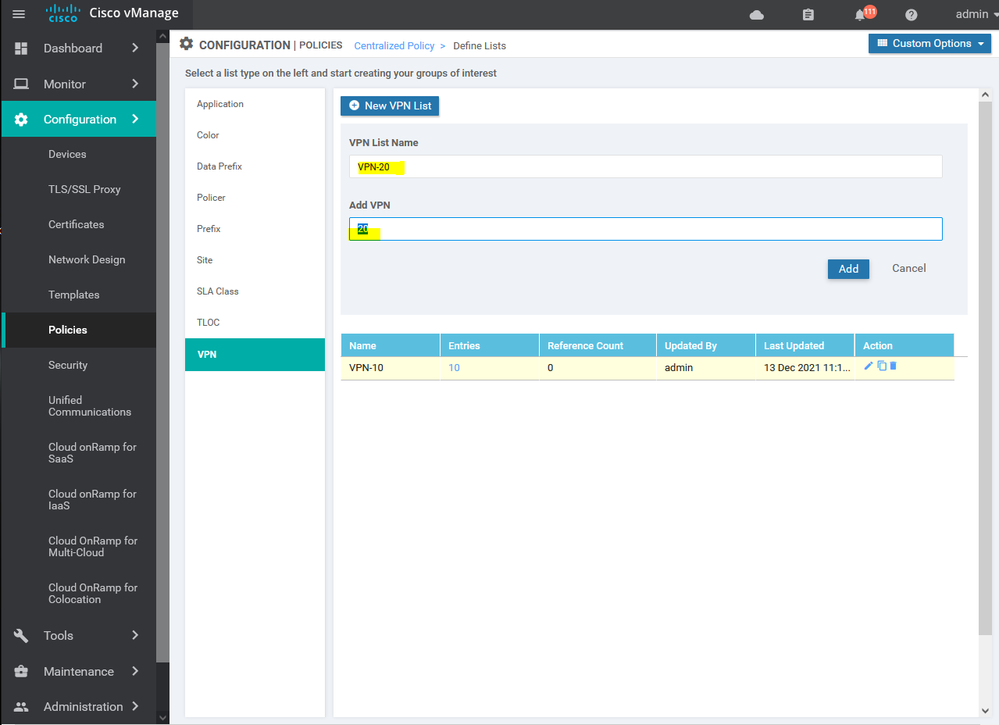
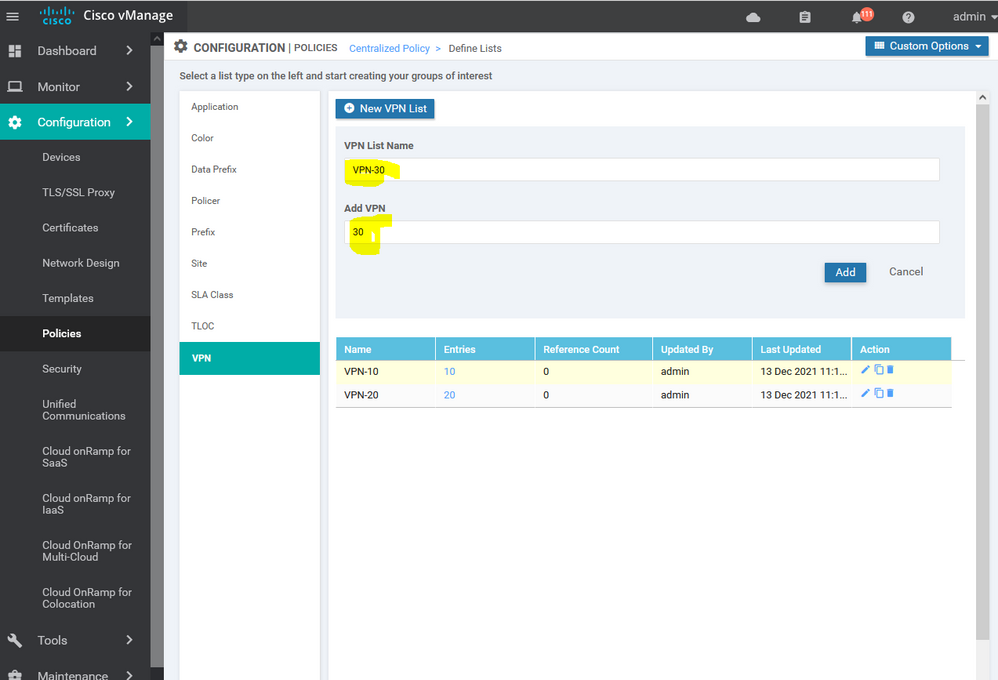
To create list of VPN Configuration > Policy > Customize options > Centralized policy > List > select VPN
To create Policy and add all of the lists and elements of the policy Configuration > Policy > Customize options > Centralized policy > ADD
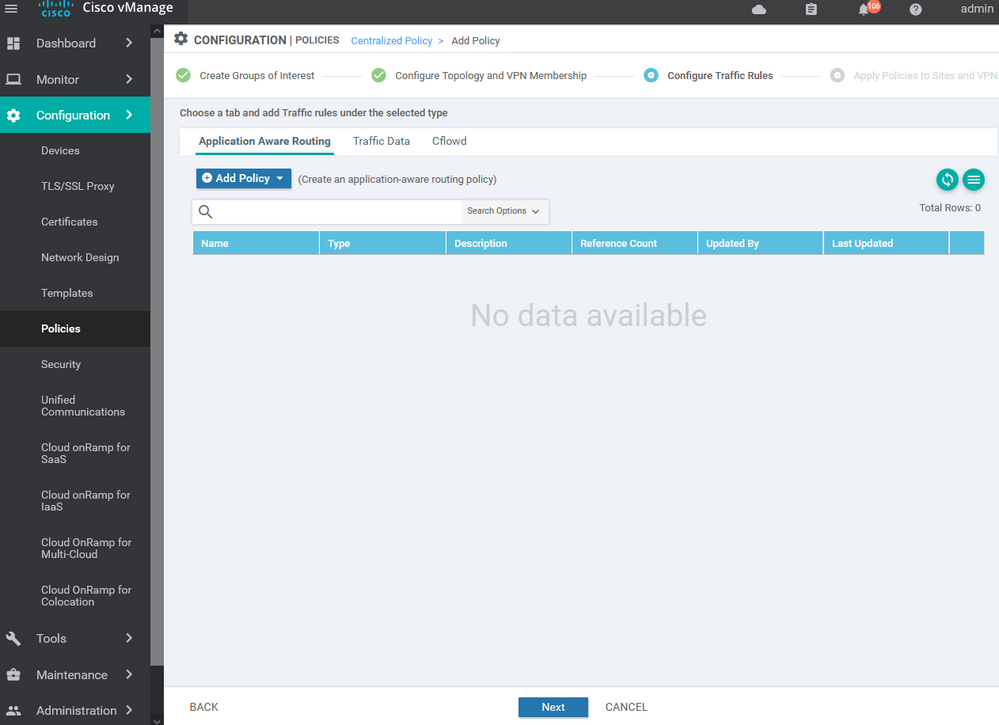
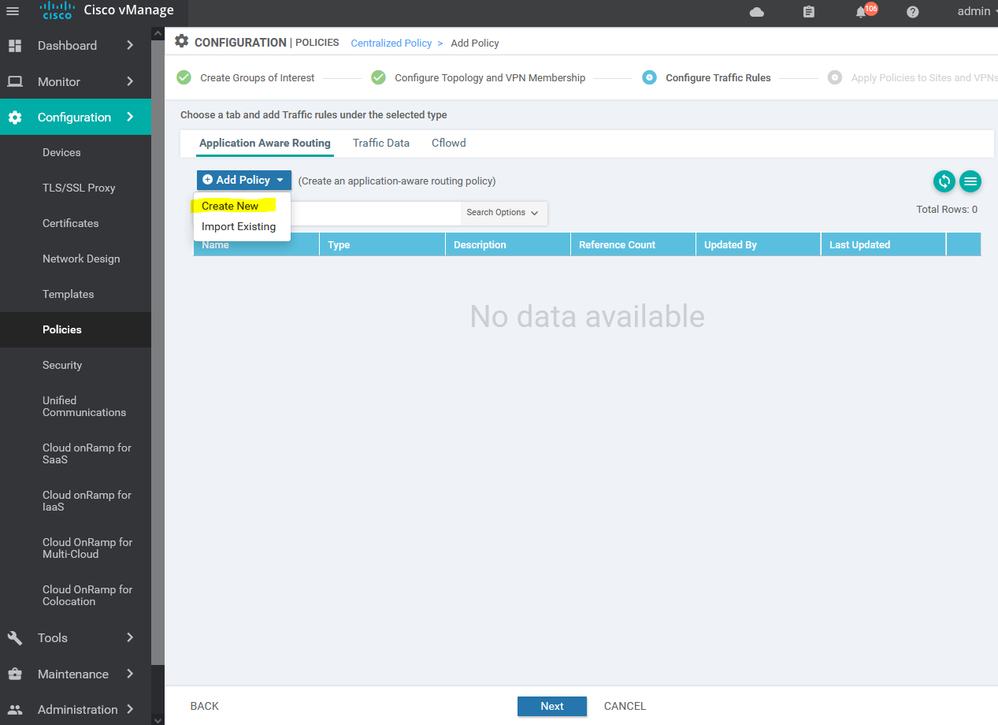
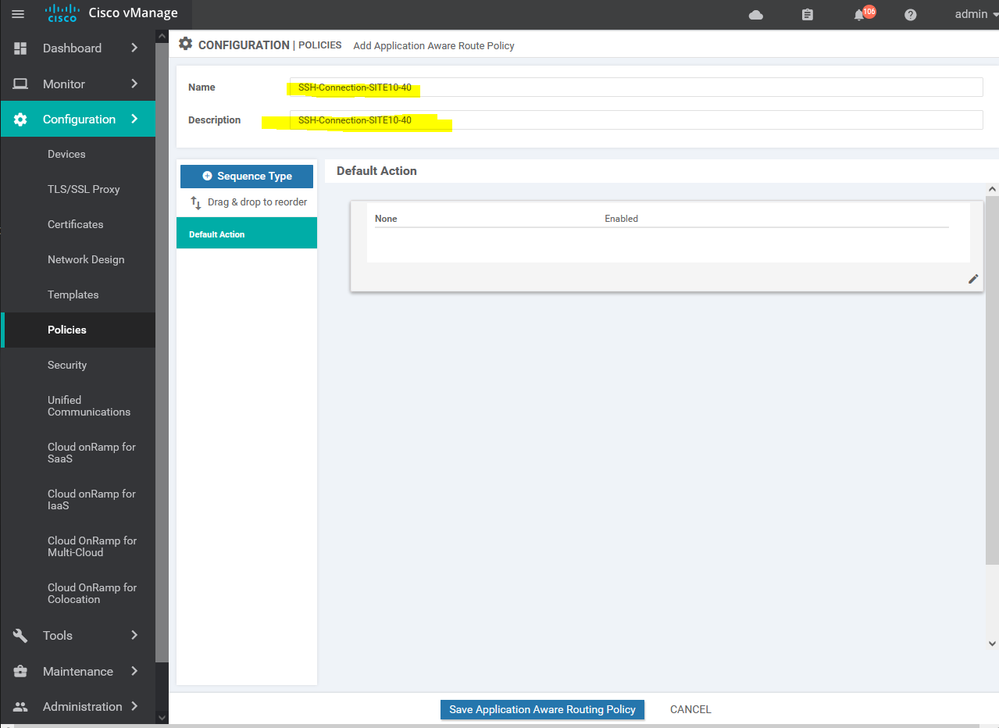
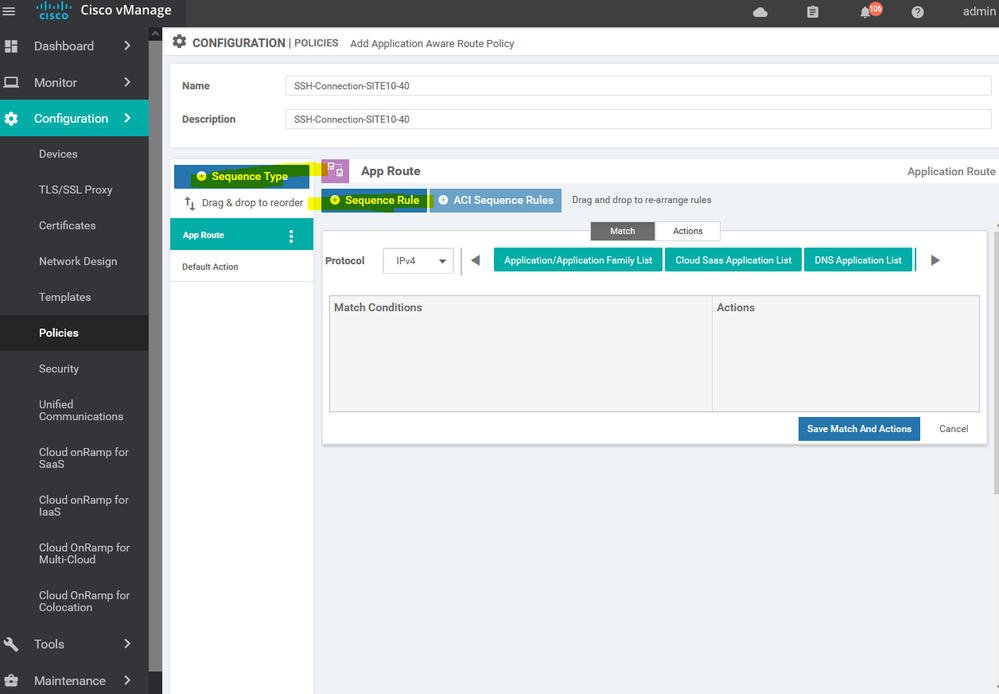
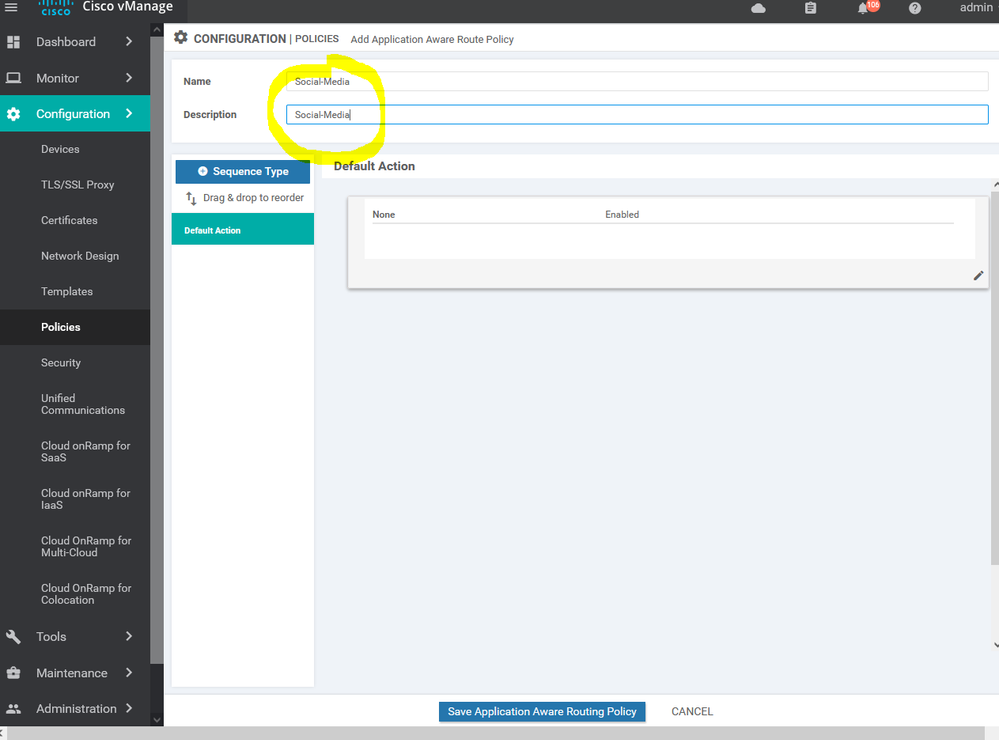
To create new application aware routing Configuration > Policy > Customize options > Centralized policy > ADD new policy > next > next > application aware routing > add policy > create new
NOTE : the default App route is allowed in version 20
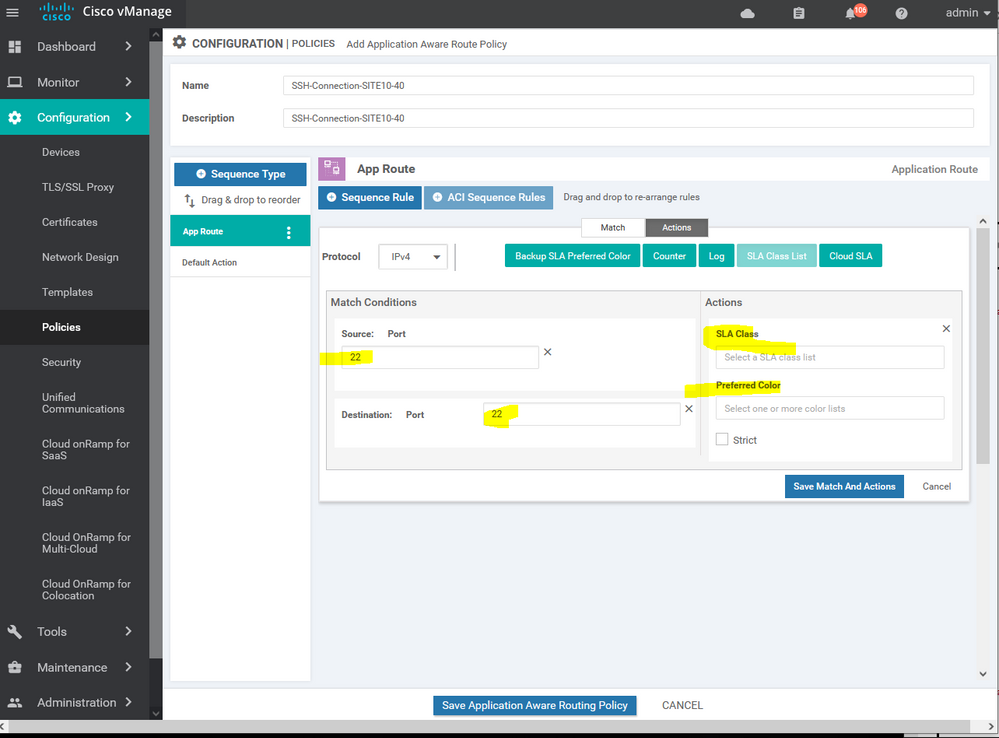
Here we using the SSH SLA which's including the percentage of the latency and jitter , ETc...
Here we using the MPLS for the SSH services and BIZ-Internet as a secondary if the MPLS is down
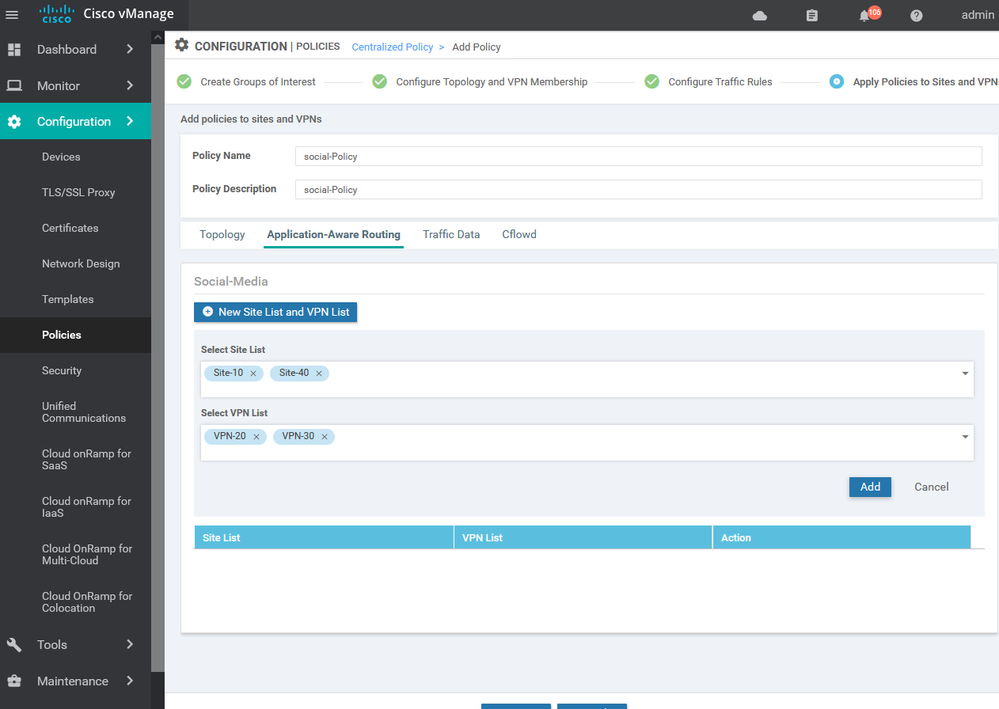
after creating the APPAR import the site list and vpn services list
To activate the policy press ... and choose activate .
NOTE : only one centralize policy can run in the real time .
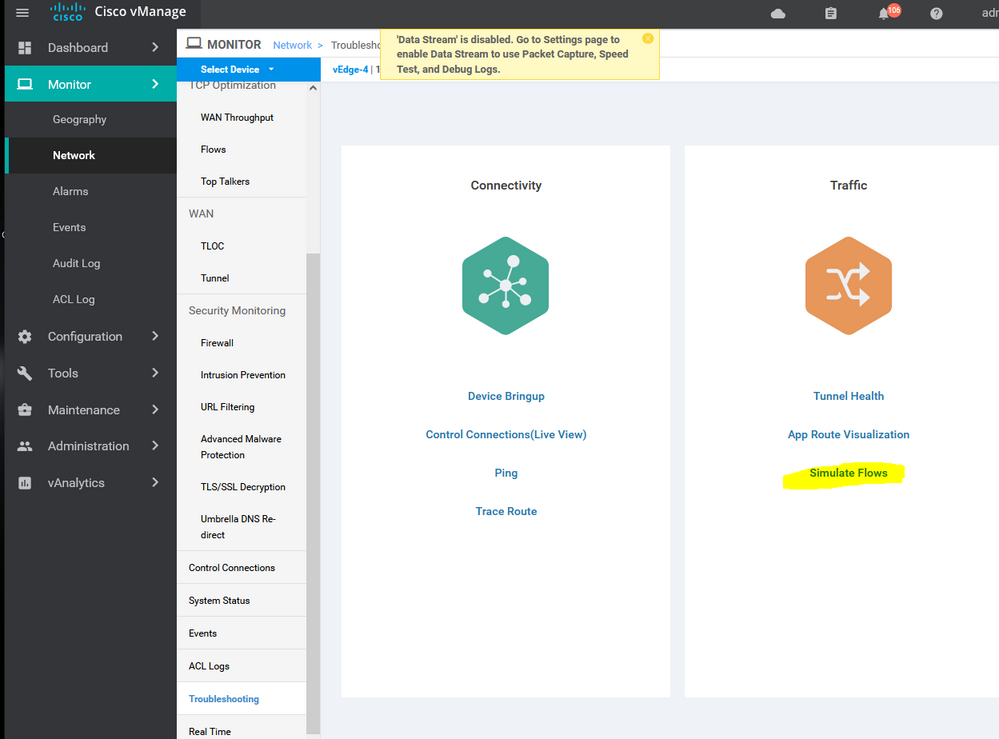
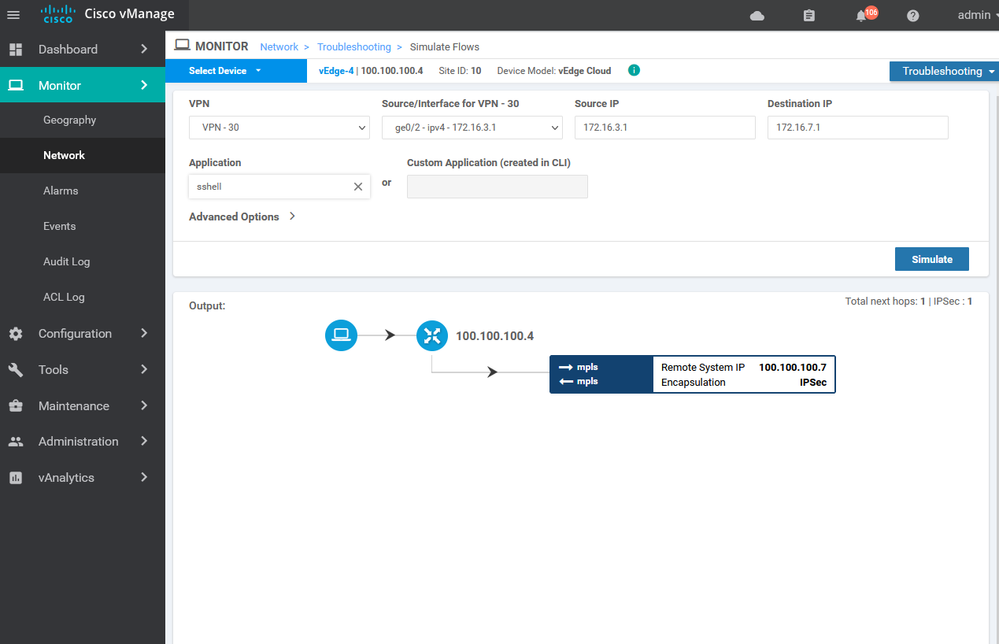
Verification :
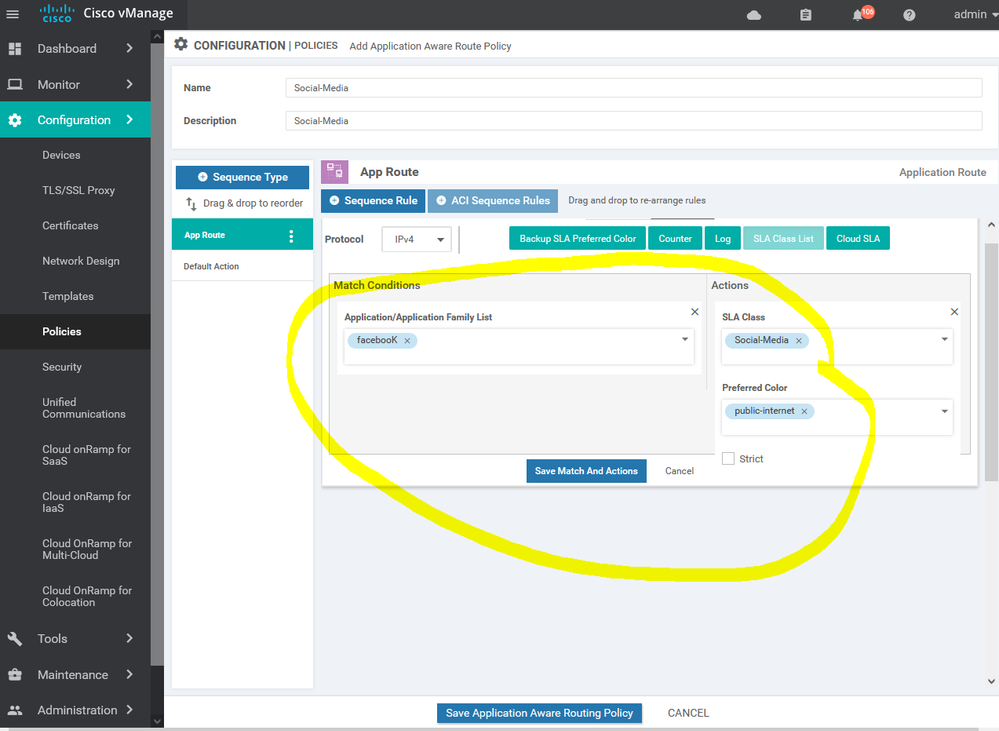
Create new Application aware routing for social media : -
Choose the internet as the primary transit with specific SLA for each application : -
Choose the VPN services which will apply this policy for it .
Viptela SD-WAN Security policy IPS/IDS services
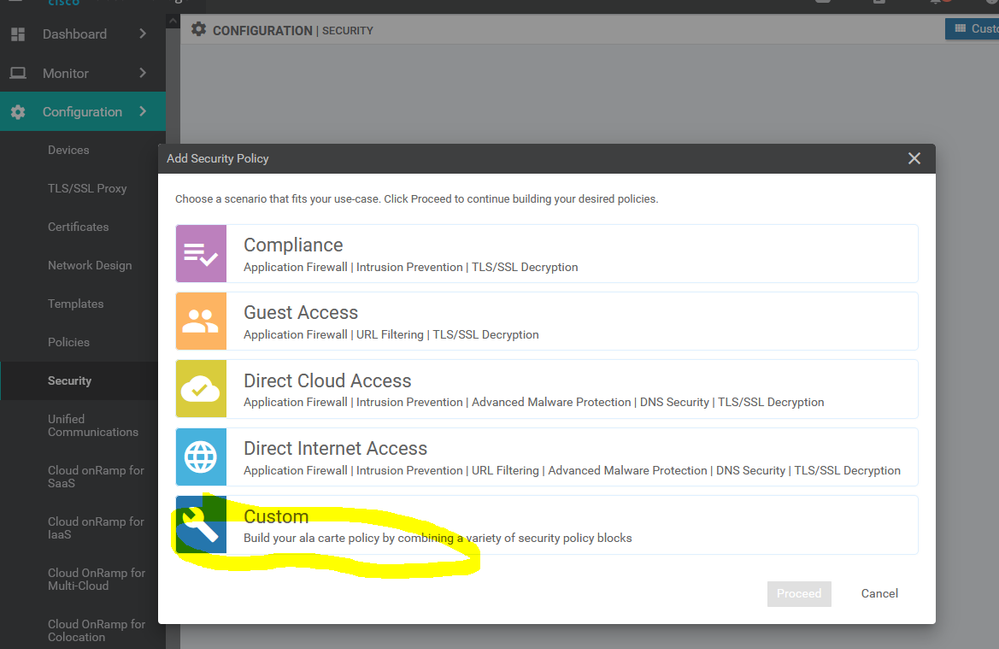
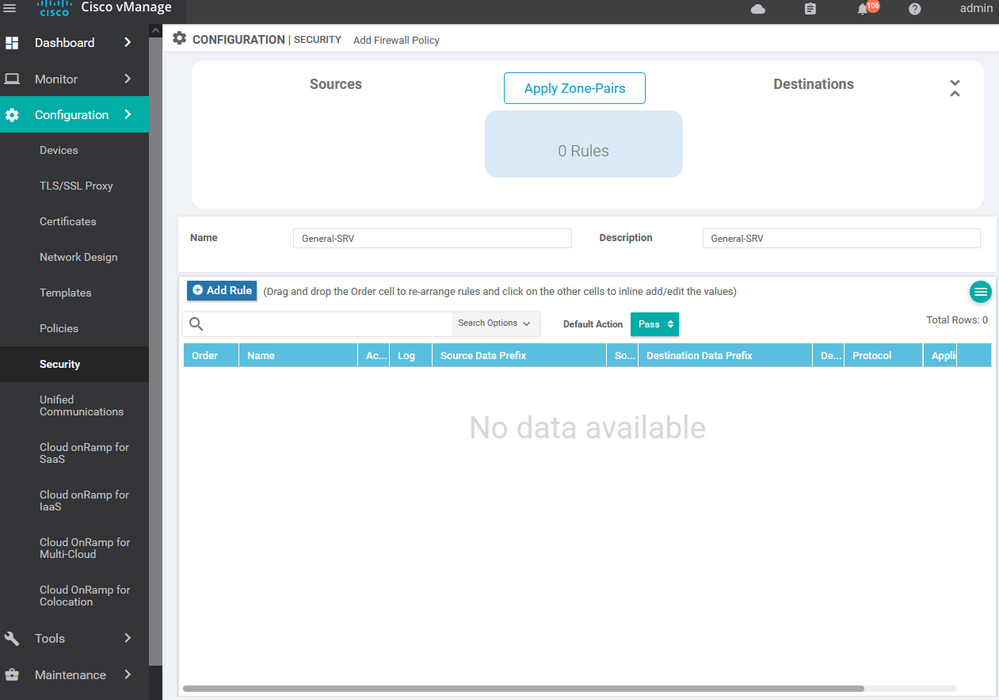
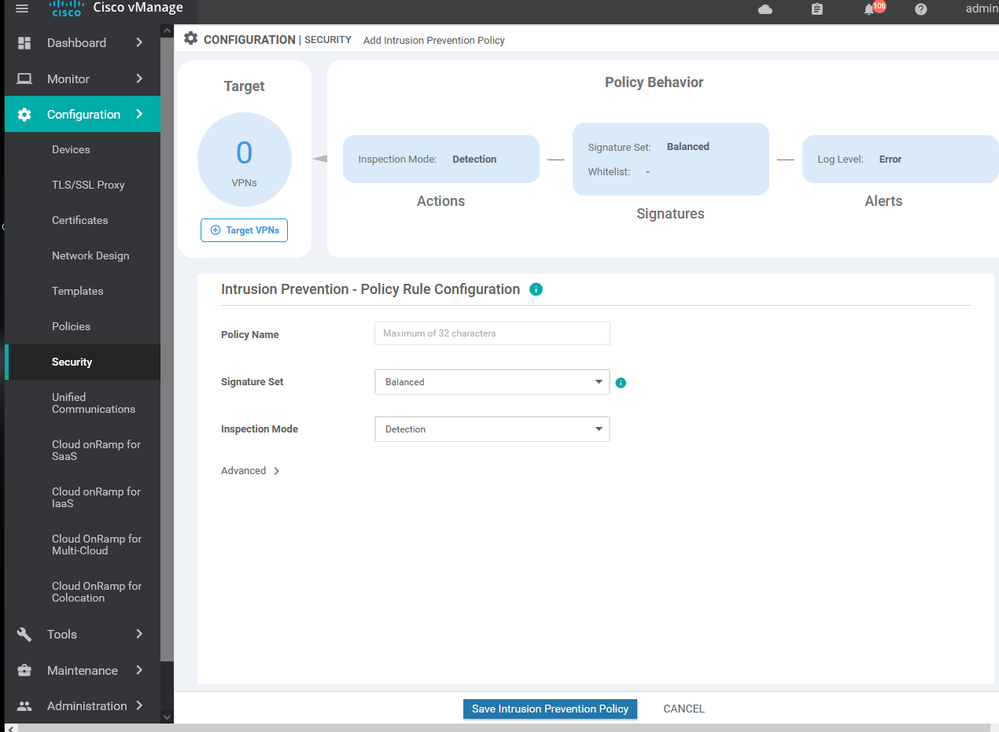
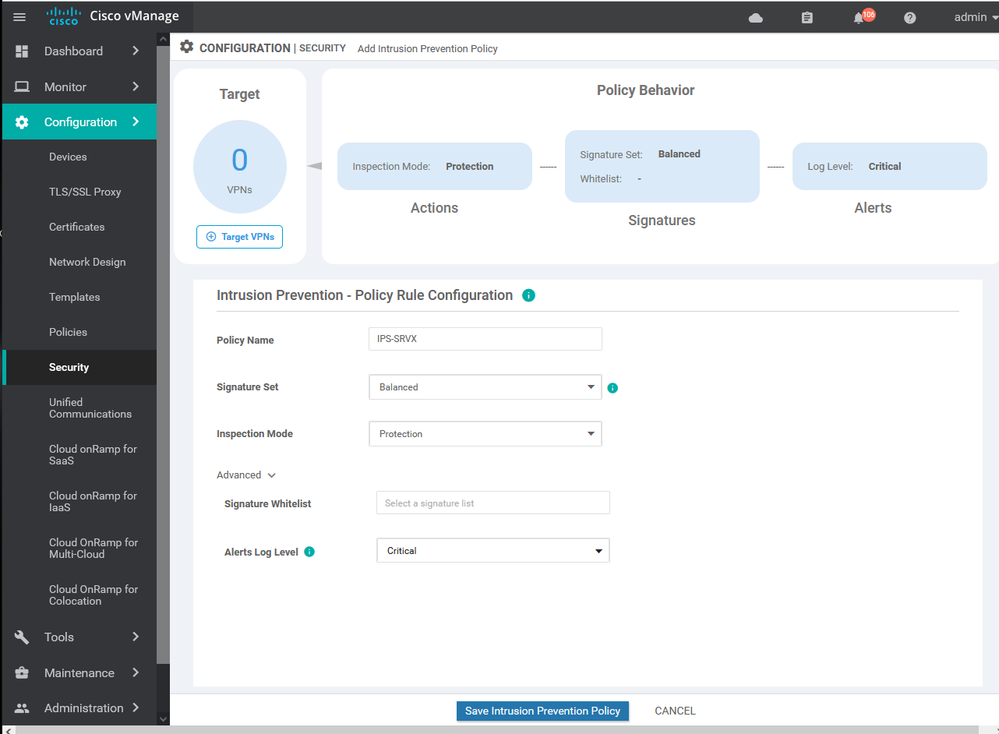
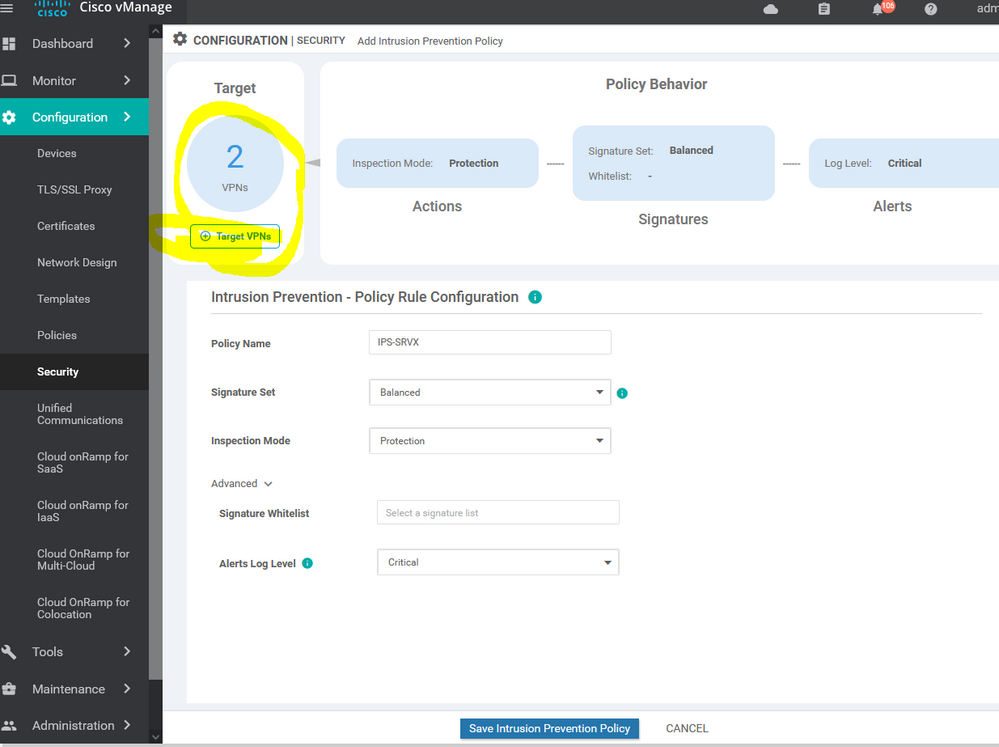
To create IPS/ IDS Services Configuration > Security > Add security policy > Custom >
To create IPS/ IDS Services Configuration > Security > Add security policy > Custom > create new
To create IPS/ IDS Services Configuration > Security > Add security policy > Custom > create new > Add role
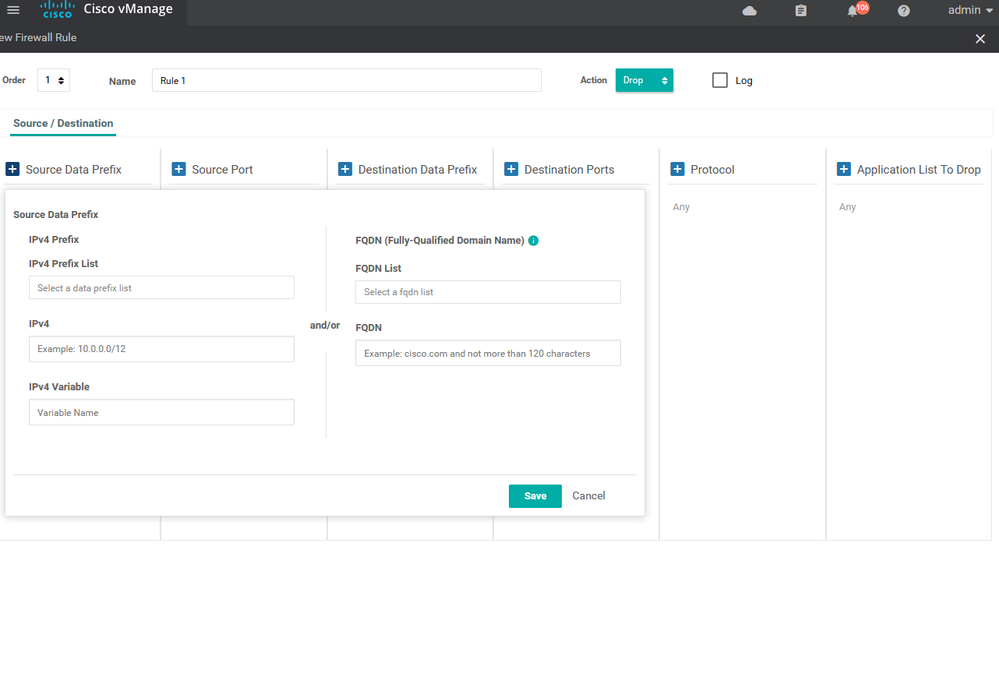
To create IPS/ IDS Services Configuration > Security > Add security policy > Custom > create new > Add role > choose source and destination and port and protocols
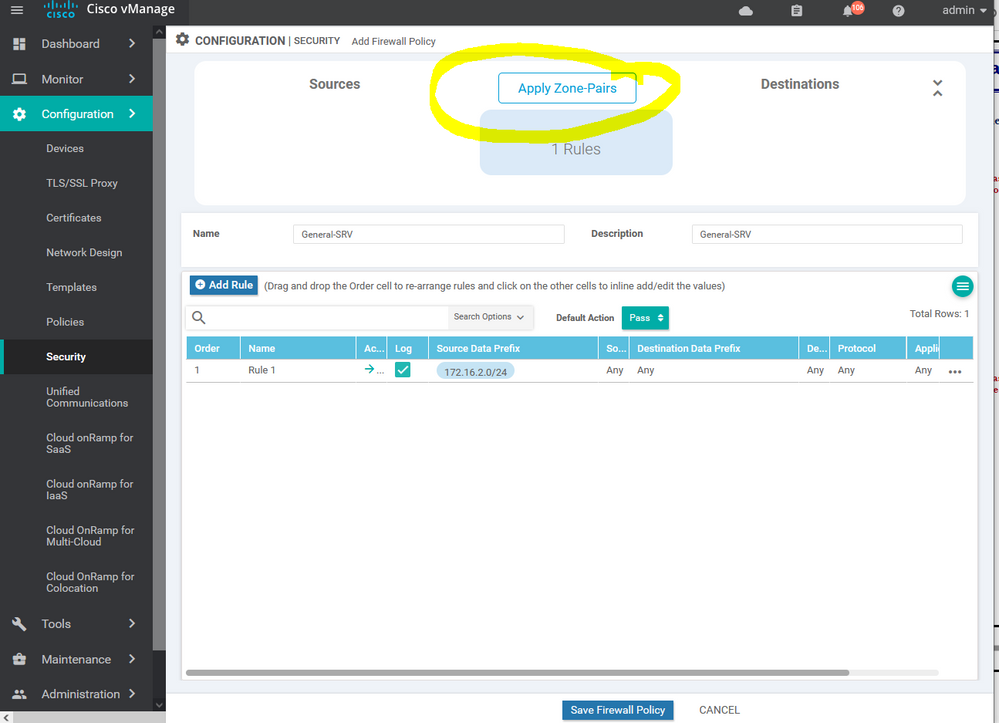
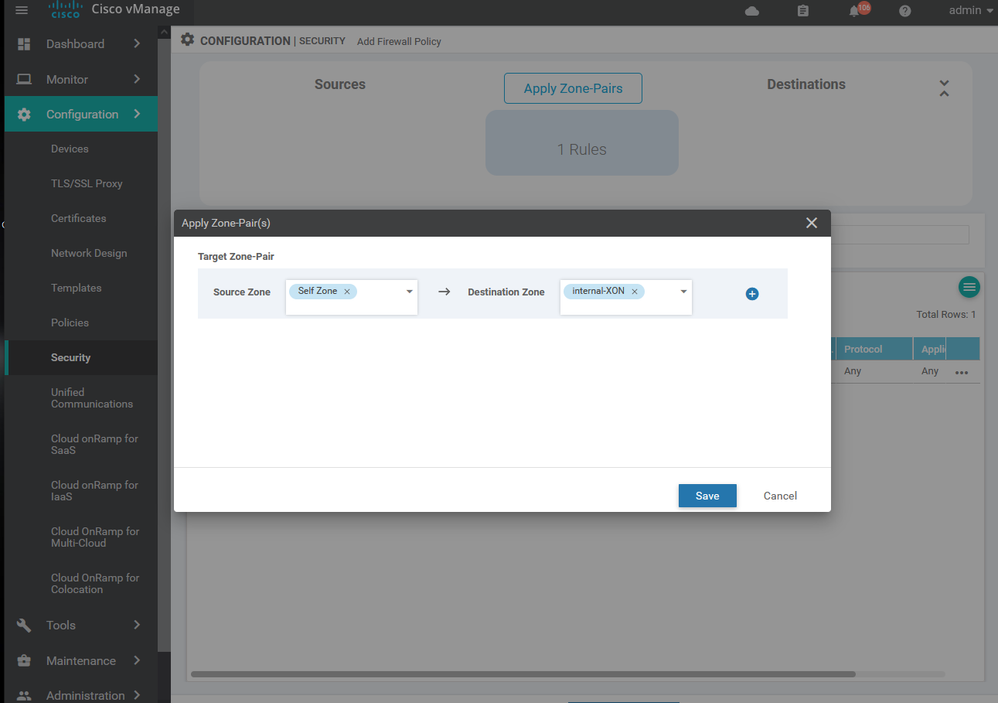
To create IPS/ IDS Services Configuration > Security > Add security policy > Custom > create new > Add role > choose source and destination and port and protocols> then apply to specific zone .
policy intrusion-prevention IPS-IDS security-level security inspection-mode detection log-level alert target-vpns 30 20 10 ! url-filtering URL-F-TX web-category-action allow web-categories travel uncategorized unconfirmed-spam-sources violence weapons block-threshold trustworthy block text Access to the requested page has been denied. Please contact your Network Administrator alert categories-reputation blacklist whitelist target-vpns 30 20 10 ! advanced-malware-protection AMP-TX file-reputation-cloud-server cloud-isr-asn.apjc.amp.cisco.com file-reputation-est-server cloud-isr-est.apjc.amp.cisco.com file-reputation-alert critical target-vpns matchAllVpn ! ! failure-mode open
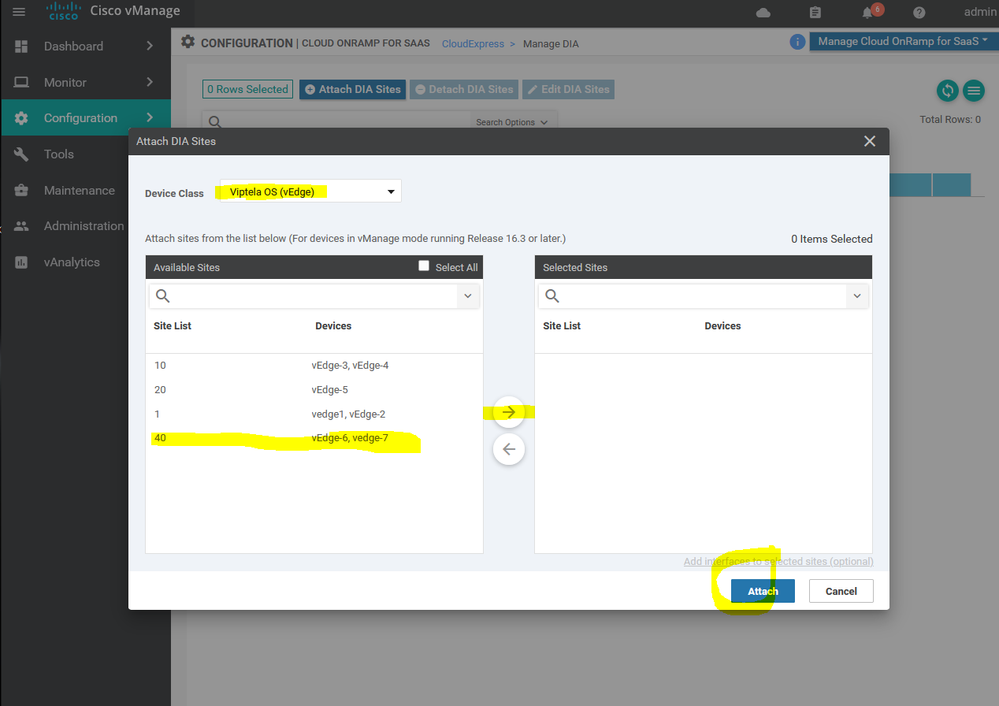
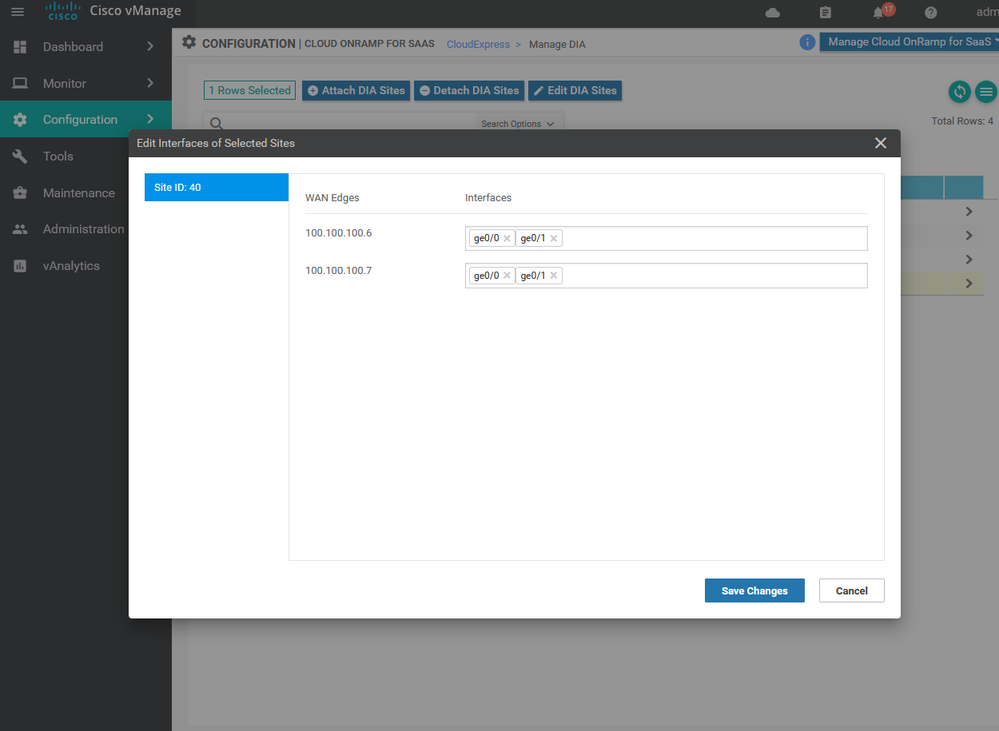
Cloud onRamp
To respect copyrights This note copy from cisco live document
vManage mode: Sites to be configured for Cloud onRamp for SaaS need to be in vManage mode as opposed to command-line interface (CLI) mode, meaning that the vManage GUI will control the configuration of the vEdge router as opposed to a user using the CLI to modify the configuration directly on a vEdge device. You need to apply a device template to the vEdge router from the vManage GUI in order to put it in vManage mode. Cisco vEdge software version: The minimum Cisco vEdge software version is 16.3.0 to configure DIA sites and 17.1.0 to configure gateway sites, but you should use the latest recommended maintenance release.
DIA or gateway sites only Network Address Translation (NAT) configuration: In order for SaaS traffic to be able to exit
the site locally (for both DIA and gateway sites), NAT configuration is required under each VPN 0 physical interface attached to the Internet or Internet path. This requirement is necessary for the interface to be a candidate for local exit, regardless of any other NAT configured for the site. Enabling NAT, by default, causes translation of the source IP address of a site user to
the outside IP address of the vEdge router when it uses the interface as a local exit to the SaaS applications.
DNS server configuration: Configure DNS server addresses in VPN 0 so the vEdge router can resolve the SaaS application hostnames and initiate performance statistics to those SaaS servers, as well as intercept DNS queries to the configured SaaS applications and act as a DNS proxy for those users. The DNS server addresses that you specify need to be able to resolve
the SaaS Fully Qualified Domain Names (FQDNs) and need to be reachable from VPN 0 or the local Internet exit.
Default route for local exit: This guide assumes that the SD-WAN overlay is already operational. If so, you must have at least one default route defined under VPN 0 to allow the tunnel to connect to the remote sites and data centers through one or more of the physical interfaces. You can either statically define the configuration of this default route or obtain it via Dynamic Host Configuration Protocol (DHCP). For DIA and gateway sites, this default route gives the next-hop information for the direct Internet exits when the Cloud onRamp for SaaS feature is configured.
Let's Confirm the internet connection is working for the branches and data center
To enable the Cloud onRamp for SaaS feature, you must first enable it globally. Then the SaaS applications that will be used and monitored will be defined. After that, the various sites will be enabled (DIA, gateway, and client sites). You must complete the first two procedures before you can enable the sites; you can enable them in any order and in any combination.
If you define only DIA sites, then site users will use their local exits until the SaaS applications become unreachable or performance becomes unacceptable; at that point, the SaaS traffic will fall back to normal routing and follow the default route for Internet access. If you define client sites, you must also define gateway sites so that the client-site traffic will
have performance-monitored sites to use for Internet exits; otherwise this traffic will follow the normal default routed path.
If you define both gateway and DIA sites, the site users at a DIA site could use either the local exit or the gateway site for Internet access, depending on the performance of the application and path.
to Configure cloud onRamp for saas > administrator > setting > cloud onRamp for saas > enable > then Cloud icon > cloud onRamp for saas > add new application and policy
To Add site for cloud onRamp for saas > administrator > setting > cloud onRamp for saas > enable > then Cloud icon > cloud onRamp for saas > add client sites
To configure DIA sites, select Manage Cloud onRamp for Saas >Direct Internet Access (DIA) Sites in the drop- Add site
Adjust the DIA for the Site 4
***** I hope that has been informative for you and thank you *****
Mohamed Alhenawy
CCIE#60453
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
NEW POST !!!!
Stay Tune for all the series , Coming Sooon
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi mr. Mohammed
we have SD-WAN Project , we deploy on-prem controllers , when we use MPLS as underlay IP every thing is goes fine and we can onboarding cEdges and joined the vManage.
But when we moved to Internet we its not worked at all.
we try to many options using public IP addresses and Natting but Unfortunately Noting work.
can you please help in this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes for sure but could you please share the whole design also I wanna know the model of the devices and version .
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: