- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- SSH Configuration On Cisco IOS XR
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-15-2013 11:30 AM - edited 03-01-2019 04:55 PM
Introduction:
Secure Shell (SSH) is a useful protocol or application for establishing secure sessions with the router. A router configured with SSH server allows a secure connection to the router similar to Telnet. The Telnet application has limited security. SSH provides stronger encryption and deploys public-key cryptography for added confidentiality.
IOS XR supports two versions of SSH:
- SSH version 1 uses Rivest, Shamire, and Adelman (RSA) keys.
- SSH version 2 uses the Digital Signature Algorithm (DSA).
There are two modes you can configure:
SSH Server:
The SSH server feature enables an SSH client to make a secure, encrypted connection to router. This connection provides functionality that is similar to that of an inbound Telnet connection.
SSH Client:
The SSH client feature is an application running over the SSH protocol to provide device authentication and encryption. The SSH client enables router to make a secure, encrypted connection to another router or to any other device running the SSH server. This connection provides functionality that is similar to that of an outbound Telnet connection except that the connection is encrypted.
Configuration Example:
In this example we will configure Router1 in server mode using SSHv2:
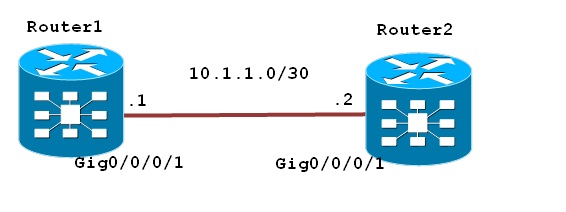
In IOS XR if you don’t configure domain name default domain name that the software uses to complete unqualified host names.
Enabling SSH on IOS XR requires the "Hfr-k9sec security" PIE to be installed on the router.
If this PIE is not present, it needs to be installed; you can refer Upgrading and Managing Cisco IOS XR Software on Cisco ASR 9000 Series Routers document
In addition to installing the k9sec PIE, IOS XR requires RSA or DSA keys to be generated on the router before SSH runs in server mode.
To verify the existence of k9sec pie use "show install active | include k9" command as shown below:
RP/0/0/CPU0:Router1(admin)#sh install active | in k9
Wed May 15 17:59:25.164 UTC
disk0:hfr-k9sec-3.6.0
RP/0/0/CPU0:Router1(admin)#
Then generate DSA key pairs using following command:
RP/0/0/CPU0:Router1#crypto key generate dsa
Wed May 15 18:16:43.712 UTC
The name for the keys will be: the_default
Choose the size of your DSA key modulus. Modulus size can be 512, 768, or 1024 bits. Choosing a key modulus
How many bits in the modulus [1024]: 1024
Generating DSA keys ...
Done w/ crypto generate keypair
[OK]
RP/0/0/CPU0:Router1#
Then enable SSHv2:
If you don’t enable server configuration on XR devices you will not able to get SSH access of device, you will get following message:
RP/0/0/CPU0:Router2#ssh 10.1.1.1
%Error in connect v4 - Connection refused
RP/0/0/CPU0:Router2#
Now let’s enable SSHv2 on Router1:
RP/0/0/CPU0:Router1(config)#ssh server v2
RP/0/0/CPU0:Router1(config)#commit
Verification:
1) SSH from Router2 to Router1
RP/0/0/CPU0:Router2#ssh 10.1.1.1
Password:
RP/0/0/CPU0:Router1#
2) You can also verify SSH session detail on the router:
RP/0/0/CPU0:Router1#sh ssh session details
Wed May 15 18:31:11.993 UTC
SSH version : Cisco-2.0
id key-exchange pubkey incipher outcipher inmac outmac
-------------------------------------------------------------------
Incoming Session
0 diffie-hellman ssh-dss 3des-cbc 3des-cbc hmac-md5 hmac-md5
Outgoing connection
RP/0/0/CPU0:Router1#
3) The output of show tcp brief shows the TCP port 22 sessions that identifies the incoming SSH connection.
RP/0/0/CPU0:Router1#sh tcp brief
Wed May 15 18:32:16.959 UTC
PCB VRF-ID Recv-Q Send-Q Local Address Foreign Address State
0x1012d904 0x60000000 0 0 :::22 :::0 LISTEN
0x10129ed0 0x00000000 0 0 :::22 :::0 LISTEN
0x1012e1bc 0x60000000 0 0 10.1.1.1:22 10.1.1.2:62153 ESTAB
0x1012d764 0x60000000 0 0 0.0.0.0:22 0.0.0.0:0 LISTEN
0x10125348 0x00000000 0 0 0.0.0.0:22 0.0.0.0:0 LISTEN
RP/0/0/CPU0:Router1#
You can also configure SSH client on router as shown below:
RP/0/0/CPU0:Router2(config)#ssh client ?
dscp DSCP value for ssh client sessions
knownhost Enable the host pubkey check by local database
source-interface Source interface for ssh client sessions
vrf Source interface VRF for ssh client sessions
If you want to enable SSH on VRF just include "vrf" word after ssh command as shown below :
"ssh server [vrf vrf-name]"
"ssh client [vrf vrf-name]"
Related Information:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does anyone know where the RSA keys are stored in IOS-XR?
In IOS it's nvram:private-config. In IOS-XR there is a file nvram:cepki_key_db, but it's not clear if this is the one.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
RSA keys work just fine with SSHv2, it appears both this document and the official documentation are outdated.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You are correct, ssh v1 may only support RSA, but SSH V2 supports both RSA and DSA. I will get the documentation corrected.
RP/0/0/CPU0:PE4#sh ssh sess det
Thu Apr 14 22:34:37.390 CEST
SSH version : Cisco-2.0
id key-exchange pubkey incipher outcipher inmac outmac
-------------------------------------------------------------------
Incoming Session
0 diffie-hellman ssh-rsa 3des-cbc 3des-cbc hmac-md5 hmac-md5
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
On an XE device, the key generation uses the host name and domain name information.
So that, if you change the host name or domain name after key generation, it is recommended that you generate new keys.
Is this also the case with IOS-XR?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
When setting the number of concurrent cli sessions on Cisco ISE
GUI(v3.1), the command max-ssh-sessions is absent from the
running/startup config (cli), to which it should be replicated.
In previous versions of ISE (2.7) it is still visibly contained
in the configuration. is it a BUG?
Is there a way to access this (now hidden) parameter from the
cli or to make it visible in the configuration file?
This would be required, as we are using an external script to
check this value for compliance purposes.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

