- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- Re: CCDA design question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2018 03:53 PM - edited 03-03-2019 08:58 AM
Hello,
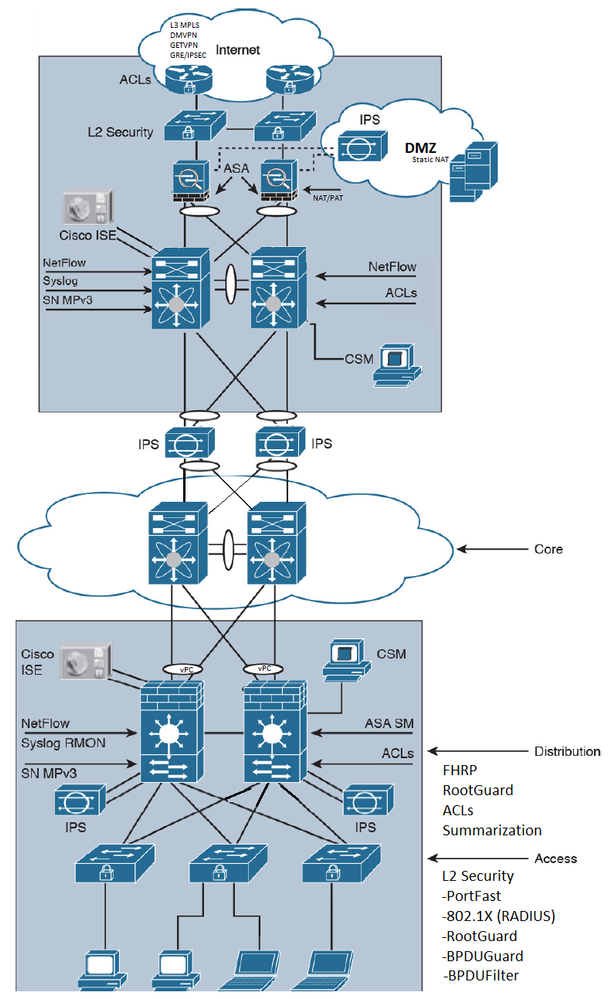
Currently as a CCNA R/S, CCNA Sec holder I am attempting my CCDA and over my 700 pages of reading have culminated to the creation of an image. I was wondering if my image is correct as it relates to a potential CCDA network environment. If I have missed anything please let me know so I can grow in my design knowledge. See below for questions i'm looking for clarification on.
- This represents the campus and enterprise modules, is the DMZ labeled correctly? If so why does the DMZ get an IPS, maybe this is a very budget less design, or traffic intense network?
- Are Distribution and Access layer protocols correctly placed?
- Are L2 protocols correctly listed and has anything been missed?
- I also have a data center to consider not included in the image, the image in the book shows it connecting to the "Core" would this be considered the data centers core and theirs really a WAN circuit or VPN module in the Enterprise Edge connecting to back to the DC?
- Am I missing anything?
Thanks again for your time, I appreciate it
Solved! Go to Solution.
- Labels:
-
Other Networking
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2018 01:46 PM
Hello
-
This represents the campus and enterprise modules, is the DMZ labeled correctly? If so why does the DMZ get an IPS, maybe this is a very budget less design, or traffic intense network?
The IPS/IDS appliances are supposed to be placed behind your firewall, so that the traffic analyzed would be filtered by rules in the firewall beforehand. The DMZ zone is an external-facing part of the network where you interact with other organizations/partners/businesses. It is typically composed of an Internal zone, commonly called iDMZ, and an External zone, called eDMZ. Within the DMZ zone, iDMZ is a trusted domain within the DMZ, and eDMZ the untrusted domain. These deployments are commonly addressed with Virtual Firewalls providing segmentation between both parts of the DMZ. As the firewalls are filtering the traffic between zones, it would make sense to deploy an IPS/IDS system behind them. This certainly depends on your requirements and how specific they are. I have seen it in the iDMZ to protect your devices in the trusted zone you are placing within the DMZ. In the external DMZ, everything is simply denied unless otherwise.
-
Are Distribution and Access layer protocols correctly placed?
I would add Port Security in the access layer to limit the amount of MAC addresses per port in user-facing ports.
-
Are L2 protocols correctly listed and has anything been missed?
read above :) - Although, Maybe MACSec :D but that would not be at the access layer.
-
I also have a data center to consider not included in the image, the image in the book shows it connecting to the "Core" would this be considered the data centers core and theirs really a WAN circuit or VPN module in the Enterprise Edge connecting to back to the DC?
The DC can have its own edge module to manage external connectivity, or it can use the edge module placed in the enterprise design. It depends on its requirements, like a centralized model (traffic being delivered directly to the DC from external locations). Having its own edge module would be the safest option, as the failure domain would not be shared (edge module) and therefore its stability would not compromised.
-
Am I missing anything?
I dont think you are, please write your comments if you have more thoughts :D
Hope that helps
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2018 01:46 PM
Hello
-
This represents the campus and enterprise modules, is the DMZ labeled correctly? If so why does the DMZ get an IPS, maybe this is a very budget less design, or traffic intense network?
The IPS/IDS appliances are supposed to be placed behind your firewall, so that the traffic analyzed would be filtered by rules in the firewall beforehand. The DMZ zone is an external-facing part of the network where you interact with other organizations/partners/businesses. It is typically composed of an Internal zone, commonly called iDMZ, and an External zone, called eDMZ. Within the DMZ zone, iDMZ is a trusted domain within the DMZ, and eDMZ the untrusted domain. These deployments are commonly addressed with Virtual Firewalls providing segmentation between both parts of the DMZ. As the firewalls are filtering the traffic between zones, it would make sense to deploy an IPS/IDS system behind them. This certainly depends on your requirements and how specific they are. I have seen it in the iDMZ to protect your devices in the trusted zone you are placing within the DMZ. In the external DMZ, everything is simply denied unless otherwise.
-
Are Distribution and Access layer protocols correctly placed?
I would add Port Security in the access layer to limit the amount of MAC addresses per port in user-facing ports.
-
Are L2 protocols correctly listed and has anything been missed?
read above :) - Although, Maybe MACSec :D but that would not be at the access layer.
-
I also have a data center to consider not included in the image, the image in the book shows it connecting to the "Core" would this be considered the data centers core and theirs really a WAN circuit or VPN module in the Enterprise Edge connecting to back to the DC?
The DC can have its own edge module to manage external connectivity, or it can use the edge module placed in the enterprise design. It depends on its requirements, like a centralized model (traffic being delivered directly to the DC from external locations). Having its own edge module would be the safest option, as the failure domain would not be shared (edge module) and therefore its stability would not compromised.
-
Am I missing anything?
I dont think you are, please write your comments if you have more thoughts :D
Hope that helps
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 03:22 AM - edited 03-28-2019 12:51 AM
The Cisco CCDA® certification is for network design engineers, technicians, and support engineers, who require a basic understanding of network design fundamentals. The CCDA curriculum focuses on but is not limited to designing basic campus, data center, security, voice, and wireless networks.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide