So, as part of my lab I have a site to site vpn tunnel between two sites. One of them is a cloud hosted bare metal ESX server. After adding it to my vCenter I realized I couldn't view the remote consoles of any of the VMs. Looking at the firewall logs everything is permitted. However, looking at the packet captures I see:
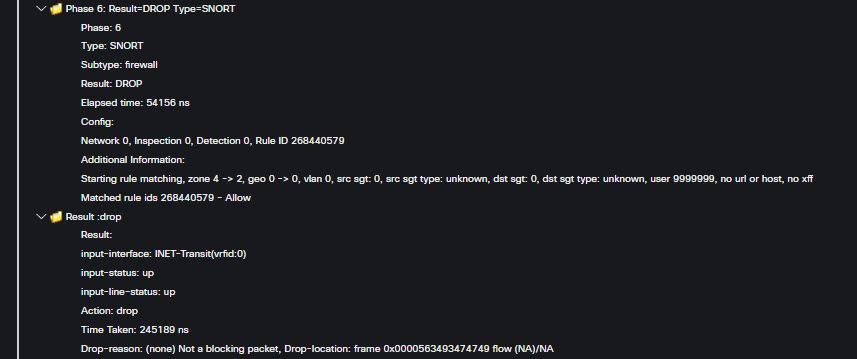
Looking at the ASP capture I see:
60: 16:56:52.678889 802.1Q vlan#70 P0 192.168.69.240.48304 > 192.168.59.2.902: P 270723155:270723422(267) ack 3792805314 win 119 Drop-reason: (snort-block) Packet is blocked as requested by snort, Drop-location: frame 0x0000563493474749 flow (NA)/NA
Where do I go to see data about what snort rule I'm hitting? I've always thought its odd there is nothing in the FMC GUI about snort to see what is going on and pretty misleading that I've got to do packet captures and all to identify what snort is doing unless I'm totally missing something. Hopefully I am but I'd like to better understand how I find out what it thinks this traffic is that is blocking it. Obviously yes, I can put in a fastpath rule and it fixes it. I'm just curious how I dig deeper and see what is actually going on here.